
Zero-Day Security Flaw Exploited in PrestaShop Websites
Attackers discovered a way to exploit a vulnerability in PrestaShop servers. The actively exploited zero-day, CVE-2022-36408, allows attackers to execute arbitrary code in an SQL injection attempt and possibly steal customer payment information.
Nearly 300,000 online retailers use PrestaShop, which is positioned as the top open-source e-commerce system in Europe and Latin America.
Which PrestaShop Versions Affected?
Versions 1.6.0.10 and later are affected by this SQL injection vulnerability. If PrestaShop versions 1.7.8.2 and later are running modules susceptible to SQL injection, such as the Wishlist 2.0.0 to 2.1.0 module, they may be affected by the attack as well.
How Does the Attack Happen?
The attack targets shops that are already exposed to SQL injection. According to PrestaShop’s investigation, the attacks start with the attacker sending a POST request to the vulnerable endpoint, followed by a GET request to the homepage with no parameters. This causes the creation of a web shell file with the name blm[.]php in the shop’s root directory. The attackers frequently used this web shell to inject fake payment pages. Finally, the attacker sends a GET request to the newly created file, granting them the ability to execute arbitrary commands. Attackers erase their tracks after the attack, so the shop owners can’t follow up.
Exploits could be used against stores still using out-of-date software and software modules. PrestaShop released version 1.7.8.7 specifically to defend against code injection attacks. This latest PrestaShop version and modules are considered safe.
Is There Any Patch or Mitigation?
The first thing to do is to confirm that your shop and all of your modules are updated to the most recent version.
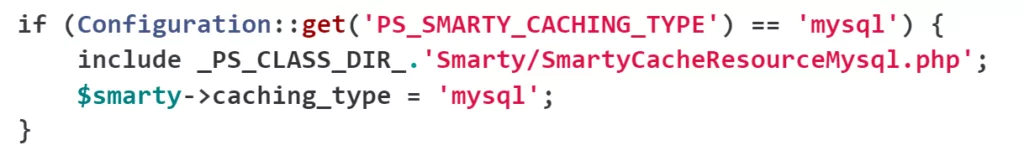
A potential attack method mentioned in the PrestaShop security advisory is the use of MySQL Smarty cache storage features. This function is disabled by default because it is rarely used, but an attacker could turn it on remotely. So, it is recommended to physically disable this feature if it’s not needed.
To do that, find the file config/smarty.config.inc.php on your PrestaShop installation and delete lines 43–46 (for PrestaShop 1.7) or 40–43 (for PrestaShop 1.6) as follows:
Check the attack pattern shared on the advisory to understand if you are affected or not.




































