
0-Day Sale, Swiss and US Data Leaks, Indian and Saudi Arabian Services’ Access Sales
In the unceasing vigilance of the digital realm, the SOCRadar Dark Web Team has uncovered yet another series of alarming incidents this week.
From a new 0-day exploit threatening major corporations to data leaks affecting Swiss citizens and American doctors, and unauthorized access sales targeting Indian websites and a Saudi Arabian academic services provider, these discoveries unveil a chilling world of cyber threats.
Find out if your data has been exposed.
New 0-Day is on Sale
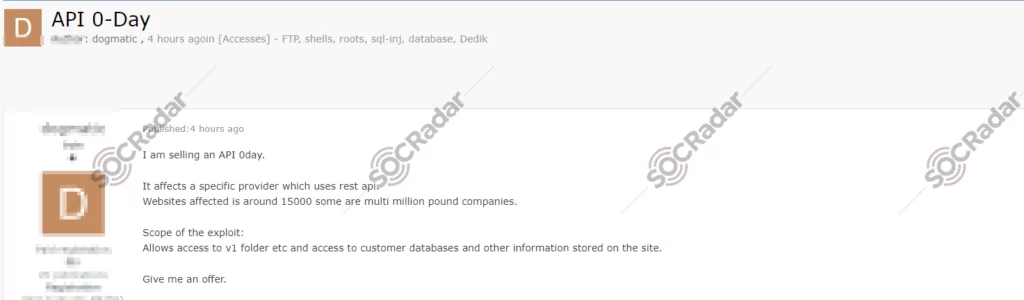
The SOCRadar Dark Web Team detected a post where a threat actor claims to have a new 0-day exploit for sale targeting a specific API used by various websites, including some significant corporations. The threat actor suggests that this exploit allows unauthorized access to the initial version of the API accessed through v1 endpoint and potentially exposes customer databases and other sensitive information stored on the affected sites. The exact number of affected websites is around 15,000, some of which are described as multi-million-pound companies.
Data of Swiss Citizens are Leaked
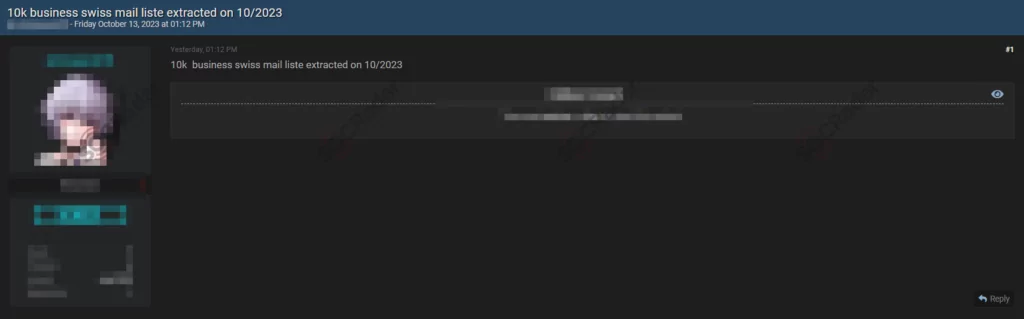
The SOCRadar Dark Web Team has detected a post in a hacker forum that a threat actor claims to have leaked data of Swiss citizens. The threat actor claims a list of 10,000 business Swiss email addresses extracted in October 2023.
Data of American Doctors are Leaked
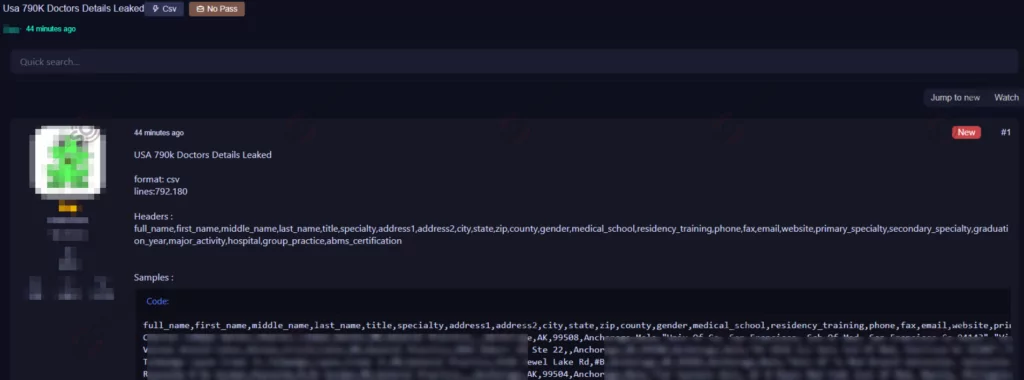
The SOCRadar Dark Web Team detected a post where a threat actor claims to have leaked data belonging to American doctors. The alleged data leak includes information on doctors in the United States and is provided in CSV format with over 792,000 lines of data. The suspected data fields in this leak encompass various details, including full names, titles, specialties, contact information (address, phone, fax, e-mail, website), medical school information, graduation year, and more.
Unauthorized Accesses Sale is Detected for Several Indian Websites
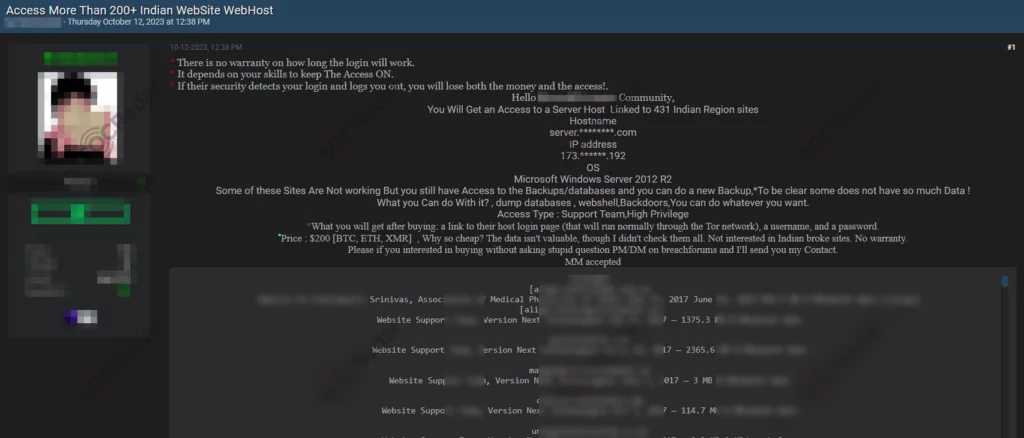
The SOCRadar Dark Web Team has identified a post where a threat actor claims to be selling unauthorized access to several Indian websites. The actor is offering access to a server linked to 431 Indian region sites, with details such as the server hostname, IP address, and operating system provided. This unauthorized access is described as having high privileges and is intended for various malicious activities, including dumping databases, creating webshells, installing backdoors, and other illegal actions.
Unauthorized CRM Access Sale is Detected for a Saudi Arabian Academic Services
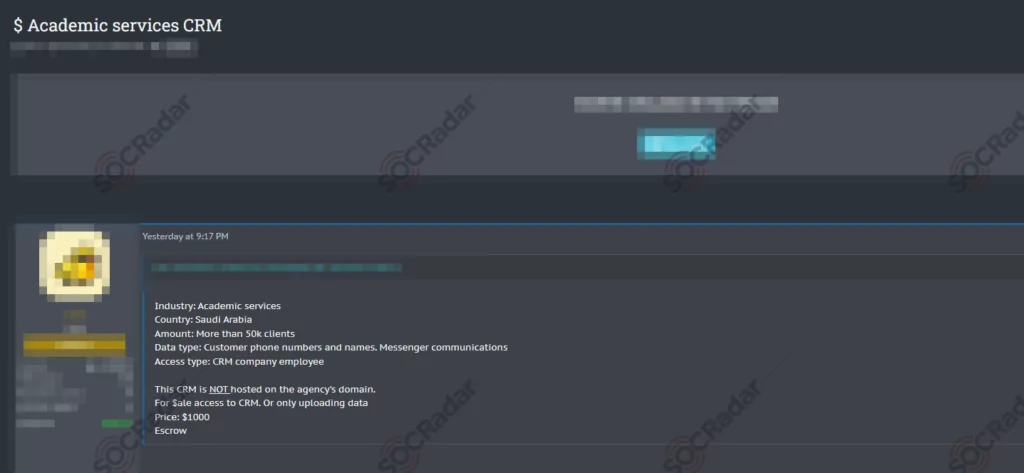
The SOCRadar Dark Web Team has detected a post in a hacker forum that a threat actor claims to possess unauthorized access to a Customer Relationship Management (CRM) system affiliated with an academic services provider in Saudi Arabia. This breach exposes sensitive information, including customer names, phone numbers, and messenger communications, concerning more than 50,000 clients. The method of access is attributed to an employee within the CRM company; notably, the CRM is not hosted on the service provider’s domain. The threat actor offers this illicit access for sale at a price of $1,000, with the option of using an escrow service for the transaction.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.



































