
10 Things You Need to Know About CSM (Continuous Security Monitoring) for SOC Environments
Defense teams are switching from preventative ideology to early detection and rapid reaction in order to confront attackers. Security teams will quickly catch and interrupt criminals and remove risks before they destroy the infrastructure of an organization. Teams need the right level of exposure to gather actionable intelligence in order to execute this approach, without drowning in too many details.
What is a Security Operations Center (SOC)?
A Security Operations Center (SOC) has a data security team that monitors and analyzes the security position of an entity on a continuous basis. SOC team aims, by means of a technological approach combination and a solid collection of processes, to detect, analyze and respond to cybersecurity events. Security operation centers typically have security analysts, engineers, and security operations managers.
SOC monitor and analyze network, server, endpoint, database, device, web site, and other systems behavior in the search for the anomaly that may indicate an incident in security or compromise. The SOC is responsible for ensuring the proper identification, analysis, defense, investigation, and reporting of possible security incidents.
How a SOC Works?(SOC)?
The SOC team is responsible for the continuing organizational aspect of enterprise information management rather as being based on evolving a security policy, the construction of security architecture, or the implementation of protection measures. SOC personnel mostly consist of security analysts working together to monitor, analyze, respond, report on and deter incidents involving cybersecurity. Any SOCs can also provide specialized forensic analysis, cryptanalysis, and reverse engineering, and incident analysis.
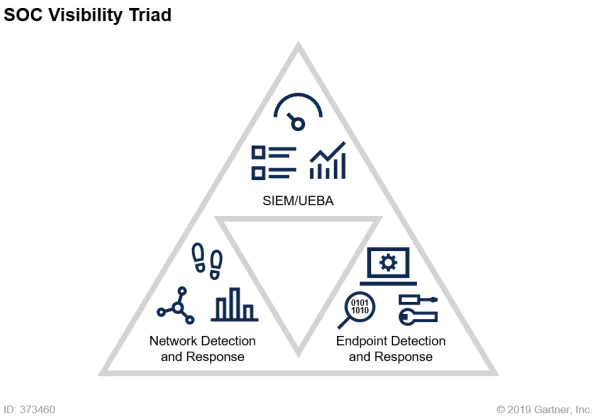
Gaining comprehensive visibility into the SOC Visibility Triad of security operations makes all the difference in enabling a security team to catch attacks early on.
The SOC Visibility Triad model leverages data from three core pillars:
- Logs/user and entity behavior through security information and event management (SIEM)
- Network traffic through network detection and response (NDR)
- Endpoint detection and response (EDR)
What is Continuous Security Monitoring?
The Continuous Security Monitoring (CSM) methodology automates the monitoring of security records, vulnerabilities, and other cyber risks, with the objective of supporting corporate decisions on risk management.
What are the Goals of Continuous Security Monitoring?
Increased visibility and accountability of the network activities, especially suspicious network activities, that may mean a security breach and reducing the risk of cyber-attacks with early warning systems (EWS) that cause rapid reactions are the objective of ongoing monitoring. The organizations incorporate continuous monitoring software solutions.
Continuous monitoring can also play a role in monitoring the operational performance of applications. A machine analysis tool can help SOC analysts track problems with program functionality and detect their origin before this problem leads to unplanned downtime and lost revenue.
SOC teams may also use continuous monitoring as a means of tracking user behavior, especially in the minutes and hours following a new application update. Continuous monitoring tools may help SOC teams assess the positive or negative impact that an upgrade has on consumer behavior and customer experiences overall.
Finally, continuous monitoring aims to provide SOC teams and helps improve organizational, security, enterprise efficiency, near-immediate feedback, and insight into performance around the network.
How to Implement CSM and Improve your Organization’s Security Posture?
Cyber Threat Intelligence Platforms create robust and versatile solutions that enable IT organizations to effectively monitor network traffic, detect anomalies or suspicious patterns of activity and develop actionable insights.
In five fundamental stages, the implementation of a continuous security monitoring solution is described as;
- System Definition: SOC team must determine the scope of its continuous monitoring deployment. Which systems are under the purview of the IT organization? Which systems should be subject to continuous monitoring?
- Risk Assessment:SOC team should conduct a risk assessment of each asset it wishes to secure, categorizing assets based on the risk and potential impact of a data breach. Higher-risk assets will require more rigorous security controls, while low-risk assets may require none at all and could even serve as a “honeypot” – a decoy system that hackers might target before they find something important.
- Choosing and Implementing Security Control Applications:Once a risk assessment has been completed, the SOC team should determine what types of security controls will be applied to each IT asset. Security controls can include things like passwords and other forms of authentication, firewalls, antivirus software, intrusion detection systems (IDS), and encryption measures.
- Software Tool Configuration:As the SOC team coordinates the desired security controls to protect key informational assets, it can begin to configure a CSM tool to start capturing data from those security control applications. CSM incorporates a feature called log aggregation that collects log files from applications deployed on the network, including the security applications that are in place to protect information assets. These log files contain information about all events that take place within the application, including the detection of security threats and the measurement of key operational metrics.
- Ongoing Assessment:Collecting data from throughout the IT infrastructure is not the ultimate goal of continuous monitoring. With millions of data points generated and centralized each day through log aggregation, information must be assessed on an ongoing basis to determine whether there are any security, operational, or business issues that require attention from a human analyst. Many organizations today are leveraging big data analytics technologies, including artificial intelligence and machine learning, to analyze large volumes of log data and detect trends, patterns, or outliers that indicate abnormal network activity.
What are the Benefits of CSM?
The main benefits associated with continuous monitoring are:
- Increase Visibility and Transparency of Network
- Enable Rapid Incident Response
- Reduce System Downtime
- Drive Business Performance
What are the 10 Things You Need to Know About CSM?
- CSM enables SOC to collect, analyze and report the defensive backfield of their organizations.
- CSM facilitates the auditing of IT infrastructure and asset details since measurements are held by the program in a repository.
- CSM is recognized and supported by numerous organizations and vendors. For example, organizations can use NIST’s reference architecture to implement and maintain their CSM process.
- CSM enables the organization to exchange data and records of continuous monitoring with those responsible for supervision.
- CSM provides real-time threat intelligence to SOCs and management that can be implemented according to the policy and requirements of the organization.
- CSM can address the vast majority of risks to your IT infrastructure by focusing on asset, configuration, and vulnerability management.
- CSM strengthens a security culture that empowers employees to make informed decision-making and act in the interest of the organization and its customers
- CSM enables improvements to the security practices of management to be enforced effectively and smoothly.
- CSM provides an automated mechanism that can significantly enhance the security of the company.
- 10. CSM enhances the SOC teams’ understanding of its IT infrastructure by remedying any flaws and vulnerabilities that can be identified through the CSM processes.
What is SOCRadar CMS?
Reduce downtime and move from reactive to proactive monitoring.
SOCRadar offers a 24x7x365 continuous security monitoring for its clients. Continuous monitoring is designed to monitor a client’s network for potential threats and respond to those threats as quickly as possible.
Auto-discovery: Discover all of your active and inactive websites with login pages automatically.
Realtime Hack alert: Early spot hacking issues like web defacement by continuous monitoring of all of your websites.
Monitor for vulnerabilities: Auto-discover underlying technologies and CMSs to check for vulnerabilities.
Detect cryptographic issues: Monitor all of your websites for valid and vulnerability-free SSL/TLS certificates.
Detect firewall/IPS misconfigurations: Get alerted< if your existing perimeter security, IPS appliances are not active or not configured properly.
Monitor deeper web structure: Identify anomalies and changes by monitoring DOM structures, header, cookies, JavaScript, and CSS links continually.
Downtime notifications: Be notified instantly when your websites return an error code.
Discover SOCRadar® Community Edition for free
With SOCRadar® Community Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
References
Cover image by Veresproduction from Freepik



































