
20 SOCRadar Notifications That Will Make You Feel Safer
SOCRadar presents its detections through the alarm mechanism and adds new alarms to the system every day to provide safer conditions. In addition, up-to-date notifications are provided for you to follow the spotlight actively.
In this article, we will explain the alarms and notifications included in the SOCRadar in 2021 and how you can use them.
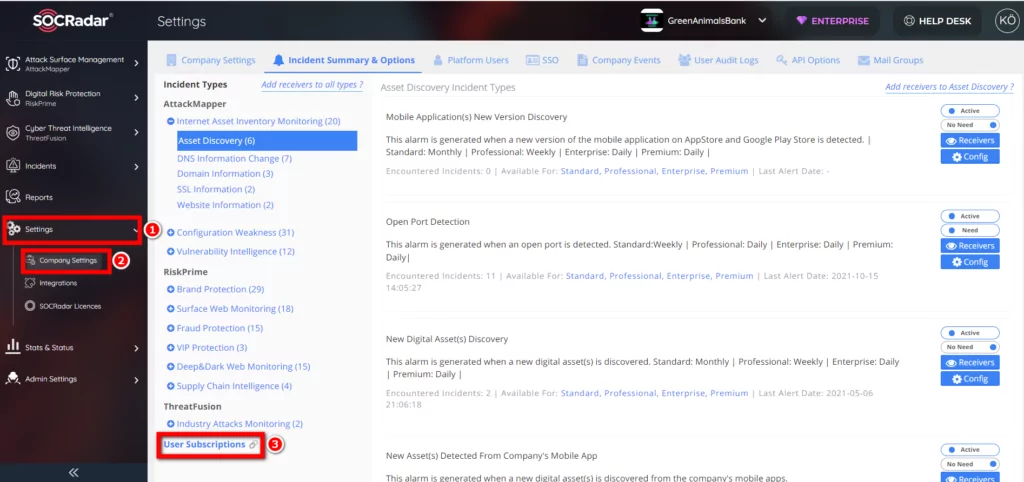
You can access all SOCRadar alarms from Settings >> Company Settings >> Incident Summary & Options.
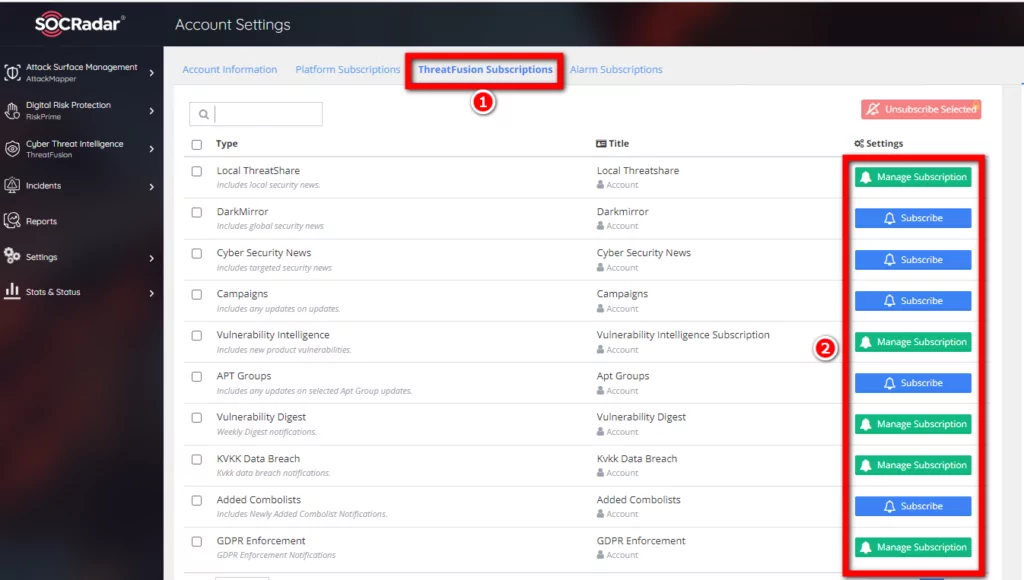
You can access all SOCRadar notations from the Account >> Subscription field.
Attack Surface Management
Newly added alarms within the scope of Internet Asset Inventory Mounting:
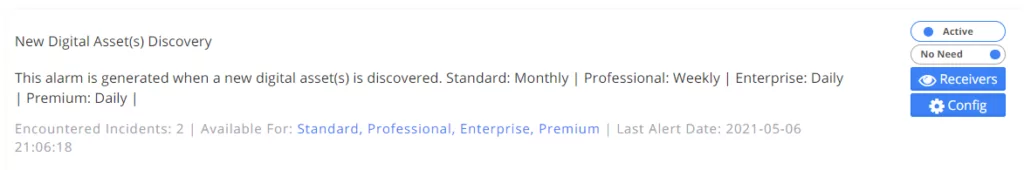
1. New Digital Asset(s) Discovery
This alarm performs asset discovery according to the relevant frequency and occurs when new digital assets are discovered.
2. Development Environment Detection /API Endpoint Detected
Subdomains detected by SOCRadar are tagged within the framework of specific keywords, and information is sent to those who have a possible development inventory or API endpoint.

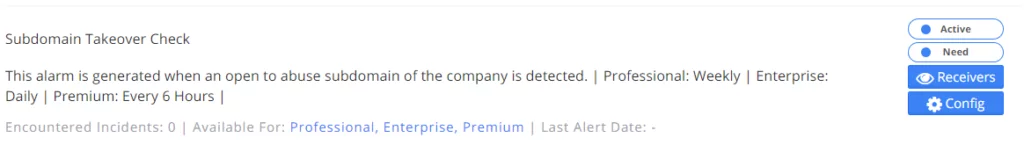
3. Subdomain Takeover Check
There is a scenario open to subdomain takeover among company-owned subdomains if it goes to a third-party service provider and this page is not accessible. This alarm is generated if the third-party provider is vulnerable to takeover.
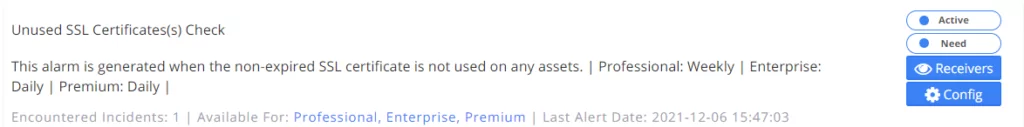
4. Check Unused SSL Certificates(s)
This alarm is generated when an unexpired SSL certificate is not used on any entity.
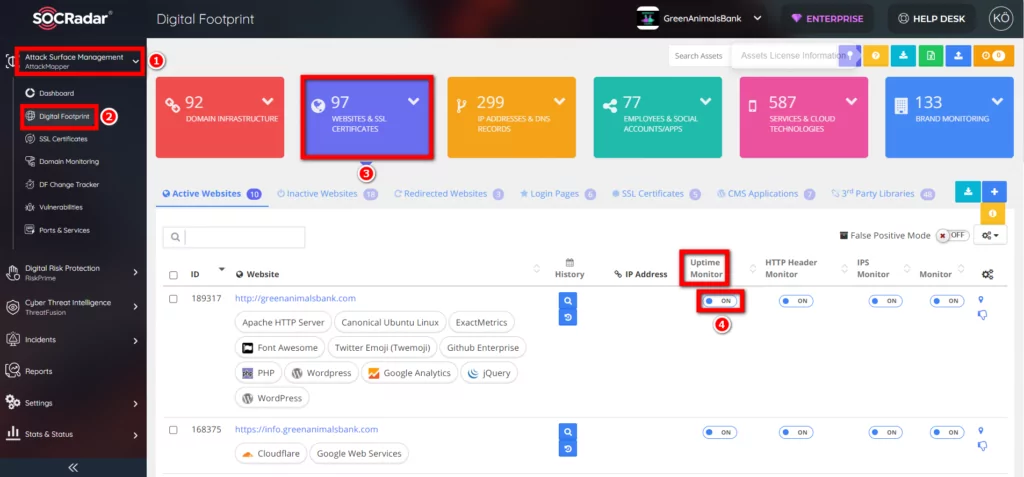
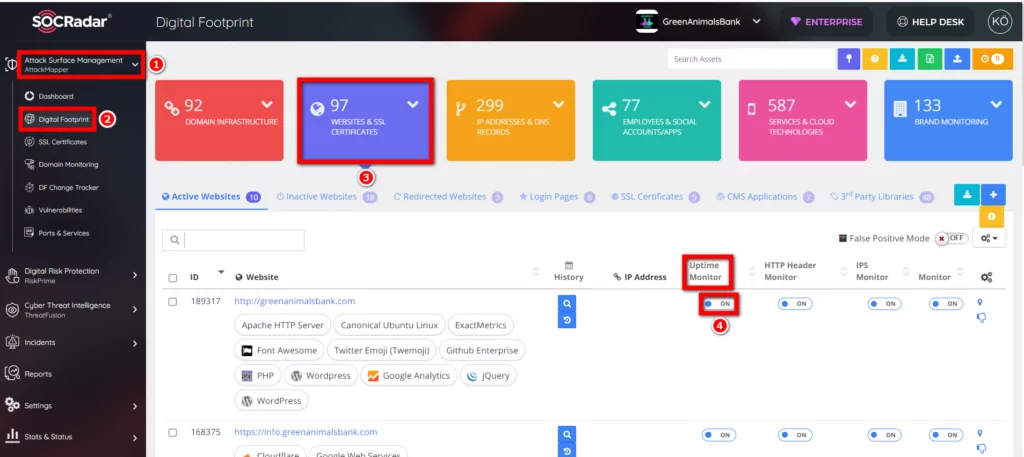
5. Website Uptime Monitor
If the website cannot be reached for about 3 minutes, an alarm occurs with the relevant error code.
In order to activate the alarm-related job, AttackMapper >> Digital Footprint >> Websites&SSL Certificates >> Uptime Monitor >> ON must be done.
Configuration Weakness
6. Cookie Monitor
This alarm occurs if it cannot find the HttpOnly, Secure, SameSite flags in the cookie in the Response Header.
In order for the alarm to be triggered, AttackMapper >> Digital Footprint >> Websites&SSL Certificates >> HTTP Header Monitor >> ON must be set.
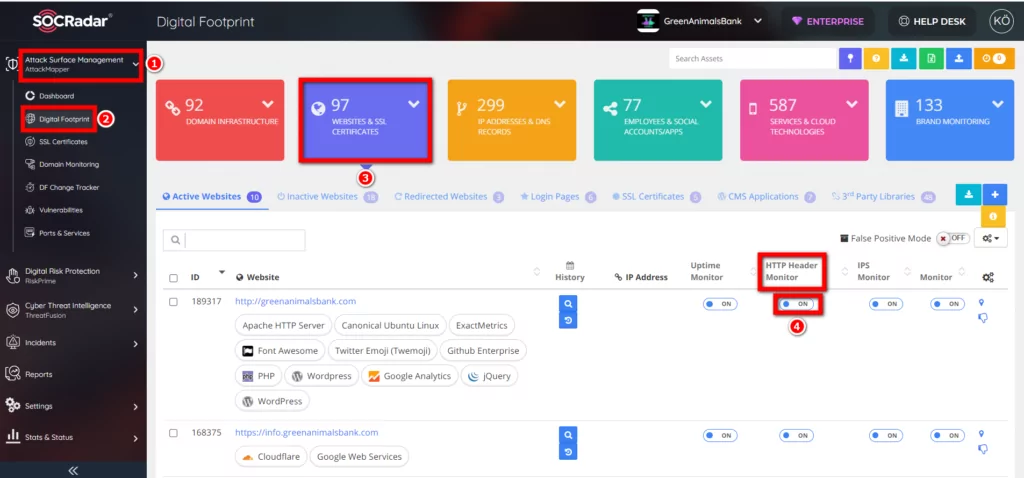
7. Security Header Monitor
This alarm provides security header control over the response header. Occurs if there are no security headers, such as X-Frame Options.
In order for the alarm to be triggered, AttackMapper >> Digital Footprint >> Websites&SSL Certificates >> HTTP Header Monitor >> ON must be set.
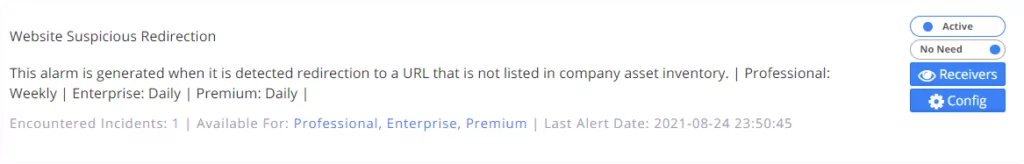
8. Website Suspicious Redirection
If there is a direction other than company assets, an alarm is generated by SOCRadar.
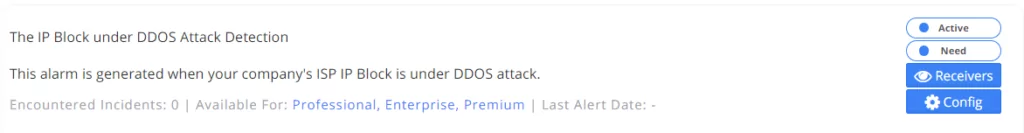
9. The IP Block under DDOS Attack Detection
The DDoS watch service is actively monitored, and an alarm is generated for informational purposes if the company’s ISP IP block(s) are present between ongoing attacks in this service.
10. Company Azure Blob Visibility Monitor / Company GitHub Repository Visibility Monitor / Company Bitbucket Repository Visibility Monitor
An alarm occurs when the company’s “Private Azure Blob,” “Private Github Repo,” and “Private Bitbucket Repo,” which are added to the SOCRadar digital inventory, are converted to public.
To trigger the alarm:
AttackMapper >> Digital Footprint >> Brand Monitoring >> Employess & Social Accounts / Apps >> Source Code Repositories & Storage >> (+) Repo / bitbucket / blob should be added.
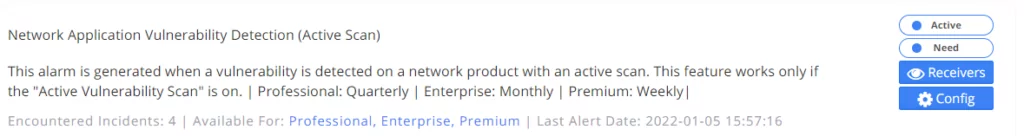
11. Network Application Vulnerability Detection (Active Scan) / Third-Party Library Vulnerability Detection (Active Scan):
If active scanning is approved by the company, the vulnerability active scanning feature is turned on, and the IPs in the system are scanned. An alarm is generated for vulnerabilities with CVS score information above 7.2.
If active scanning is approved;
Check whether the Company Settings >> Active Vulnerability Scan feature is “Active.”
Brand Protection
Newly added alarms under Supply Chain Intelligence:
You can monitor your suppliers with whom you exchange data through SOCRadar within the framework of the intelligence concept, and you can generate alarms in the following areas.
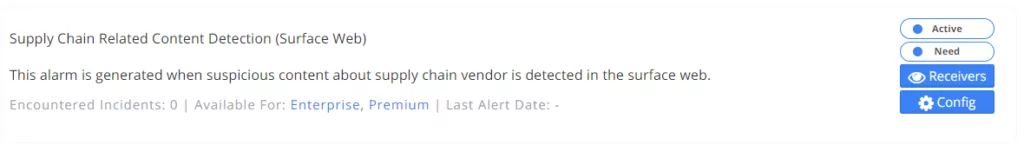
12. Supply Chain Related Content Detection (Dark Web/Surface Web)
This alarm occurs when risky/suspicious content is detected on dark web environments (hacker forums, black markets) or surface web environments (GitHub, Trello) about your suppliers you follow.
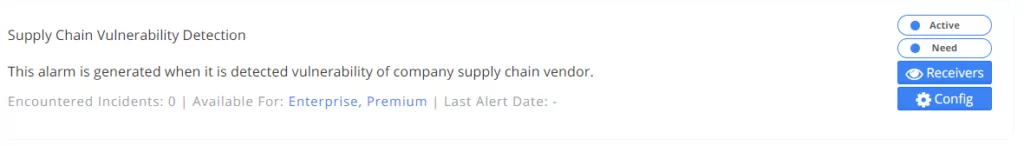
13. Supply Chain Vulnerability Detection
The IP information of the main domain of the supplier you follow is queried in passive scan sources. If the vulnerability information is reached, it is triggered as an alarm.
14. Supply Chain Detection on GDPR Enforcement Tracker
By monitoring the GDPR Enforcement Tracker website by SOCRadar, an alarm is sent when the supplier’s name is found among the companies penalized by the authorities penalizing within the scope of GDPR.
Newly added alarms under Brand Protection:
15. Company Name Detection (GDPR Enforcement Tracker)
SOCRadar monitors the GDPR Enforcement Tracker website and sent as an alarm when the company name is found among the companies that penalized the authorities punishing under the GDPR.
Newly added alarms within the scope of Deep&Dark Web Monitoring:
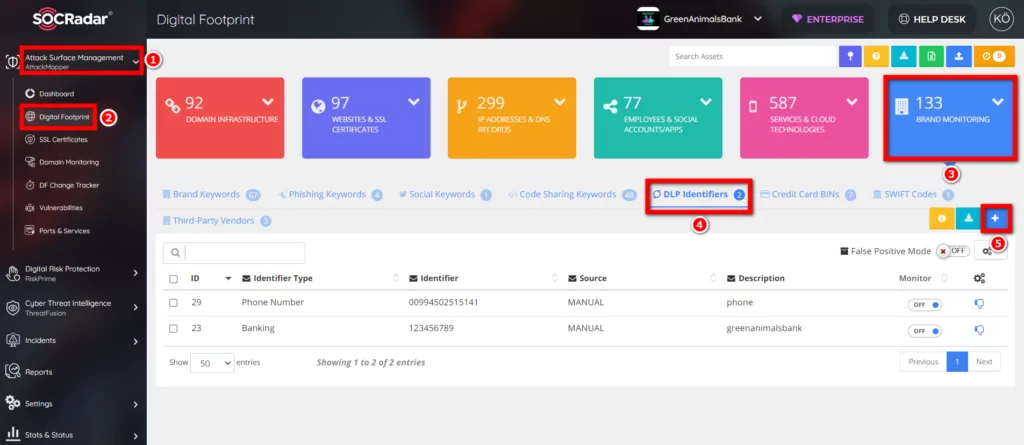
16. Sensitive DLP Identifier Detection
An alarm will occur if some sensitive information of the company is searched on Darkweb/Deepweb and hacker forums and any data sharing regarding this information is found. Some company information must be entered in the DLP Identifier field described below for this alarm to occur. This information can be a company’s credit card, phone number, or personal information (Social Security Number, etc.).
For data entry to the relevant field: AttackMapper >> Digital Footprint >> Brand Monitoring >> DLP Identifiers >> The information requested to be searched in Darkweb / Deepweb must be entered using the (+) button.
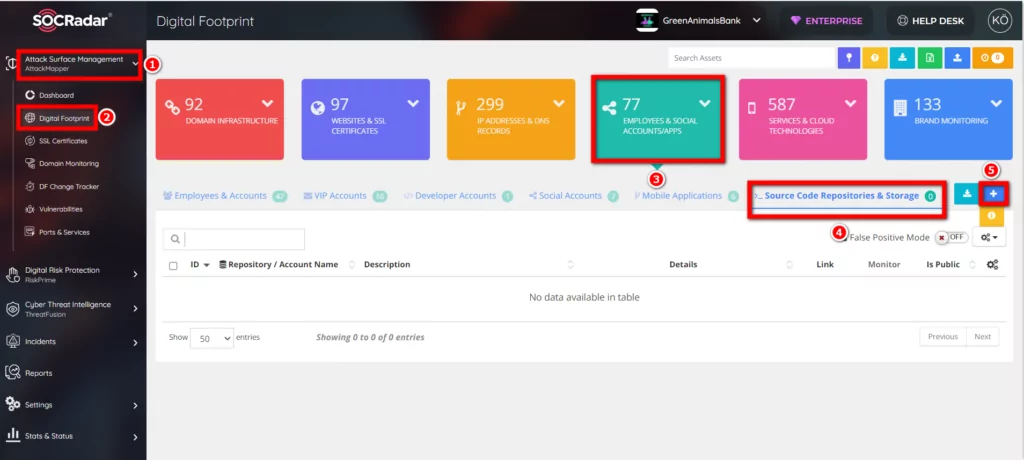
17. Sensitive Data Detection (Company Public Git Repository/Company Public Bitbucket Repository)
SOCRadar is constantly looking for code repository leaks. SOCRadar generates an alarm when it detects a critical keyword with your company name. With this newly opened alarm, a supportive control is provided to the existing code leak alarm.
The company’s open source GitHub or Bitbucket repository is examined in detail, and this alarm occurs when a critical keyword is detected.
The company’s repo/bucket should be added to the digital inventory to ensure relevant control.
Repo / bitbucket is added from AttackMapper >> Digital Footprint >> Brand Monitoring >> Employess & Social Accounts / Apps >> Source Code Repositories & Storage >> (+) button.
Cyber Threat Intelligence
Newly added alarms under Industry Attacks Monitoring:
18. Industry-Specific Activity
An alarm is generated when threat actor activity is detected targeting the industry in which the company operates.

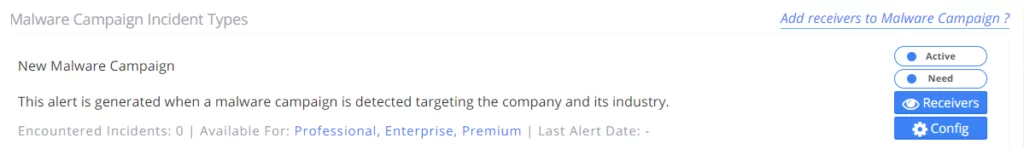
19. New Malware Campaign
An alarm is generated when a malware campaign is detected targeting the company, industry, or region.
Newly added notifications under Incidents >> Notifications:
20. GDPR Notification
SOCRadar monitors the GDPR Enforcement Tracker website and sends notifications about the penal authorities and the penalized company under the GDPR.
If you do not want to receive this notification:
You can “Unsubscribe” from the Account field >> Subscriptions >> GDPR Enforcement field.
On the same screen, you can subscribe or unsubscribe from “Platform Subscritions” / “Threat Fuisons Subscriptions” / “Alarm Subscriptions” tabs from Settings >> Company Settings >> Incident Summary&Options >> User Subscriptions.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Get free access.


































