
22 Years Old Vulnerability in SQLite Allows Arbitrary Code Execution
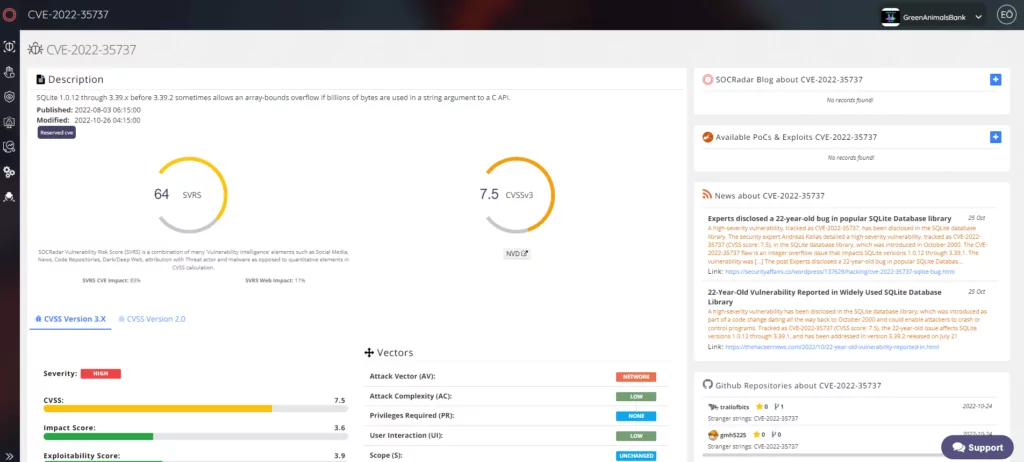
CVE-2022-35737 is a vulnerability caused by the “Improper Validation of Array Index.” The vulnerability has a CVSS score of 7.5 and affects applications that use the SQLite library API.
CVE-2022-35737 emerged in SQLite version 1.0.12 in October 2000. Attackers can exploit it on 64-bit systems. Versions 1.0.12 – 3.39.x and before 3.39.2 are vulnerable to CVE-2022-35737.
According to SQLite’s description of the vulnerability, it can only come up when “very long string inputs (greater than 2 billion bytes in length) are provided as arguments to a few specific C-language interfaces”.
Conditions for Exploiting the Vulnerability
To exploit the vulnerability, an attacker must pass large strings as inputs to the SQLite implementations of the printf functions (sqlite3_str_vappendf) and include the format specifiers “%q,” “%Q,” or “%w” in the format string.
A denial-of-service (DoS) status is caused within the program due to vulnerability. If the format string includes the special character “!”, arbitrary code execution is also possible, as confirmed in cases where the library is compiled without stack canaries.
SQLite Released a Security Patch
SQLite release 3.39.2 was made available in late July to fix the issue. Check the release log for details.
There are no reported exploits in the wild related to this vulnerability. Trail of Bits published a proof-of-concept exploit codes (see GitHub) and public disclosure of the vulnerability.
SQLite has not recommended any workarounds. The best practice is to apply the update.


































