
400 Million Twitter Users Data Allegedly Breached for Extortion
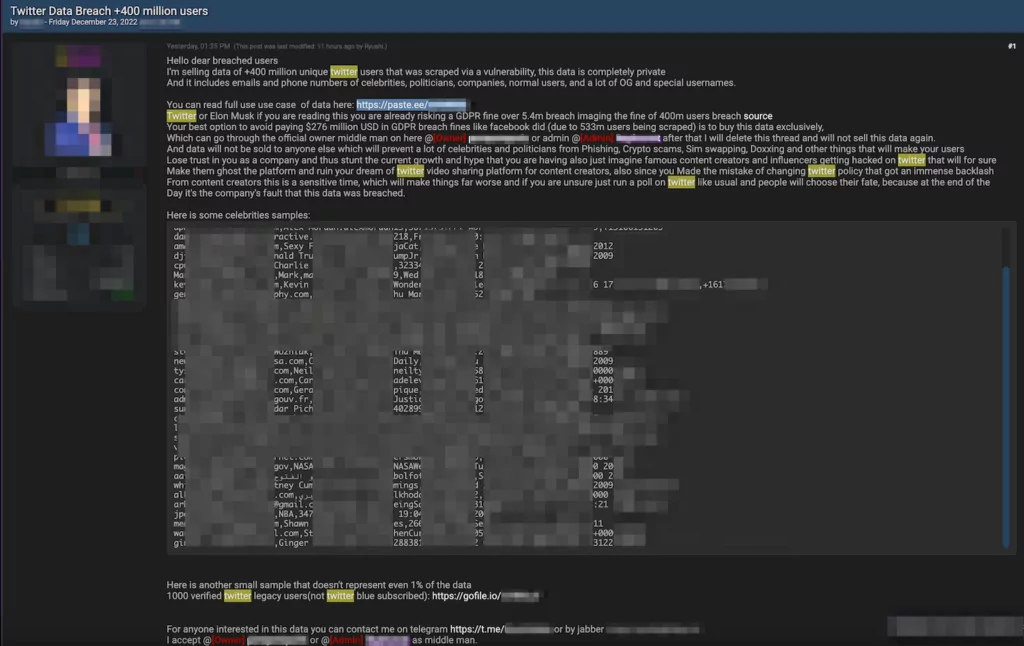
On December 23, 2022, a threat actor shared a post on a dark web forum monitored by SOCRadar, claiming to possess 400 million Twitter user data. While sharing some samples, the adversary states that Elon Musk, CEO of Twitter, should purchase the data before anyone else to avoid GDPR fines.
What Happened?
A threat actor claimed he scraped Twitter user data by exploiting a vulnerability. The cybercriminal shared some sample data allegedly belonging to celebrities from different countries and occupations. The sample directly shared in the post includes the personal data of 37 individuals. The threat actor also shared a link to the data of another 1,000 users.
As an extortion tactic, the threat actor mentioned Elon Musk and called him to purchase the data exclusively to avoid GDPR fines. The adversary even gave the example of the Facebook data breach and the fine. In April 2021, another threat actor scraped 533 million Facebook user data by exploiting a vulnerability. Meta, the parent company of Facebook, was fined €235 million (approx. $275 million) by the Irish Data Protection Commission on November 28, 2022. The similarity between the Facebook data breach incident and this extortion post raises questions about the authenticity of the data possessed by the threat actor.
What Was the Data Breach on Twitter About?
The sample data includes email address, name, username, number of followers, the creation date of the account, and phone number.
SOCRadar analysts investigated the sample data. Some information, such as name, username, number of followers, and account creation date, is already public and can be scraped from Twitter using automated tools. In this sample set, only personally identifiable information (PII) data that might have been scraped using a vulnerability are email addresses and phone numbers. Some of the email addresses are company email addresses, which are already shared in the bio of Twitter accounts. The phone number information for some accounts needs to be included. The threat actor scraped public Twitter data and combined it with other breach information.
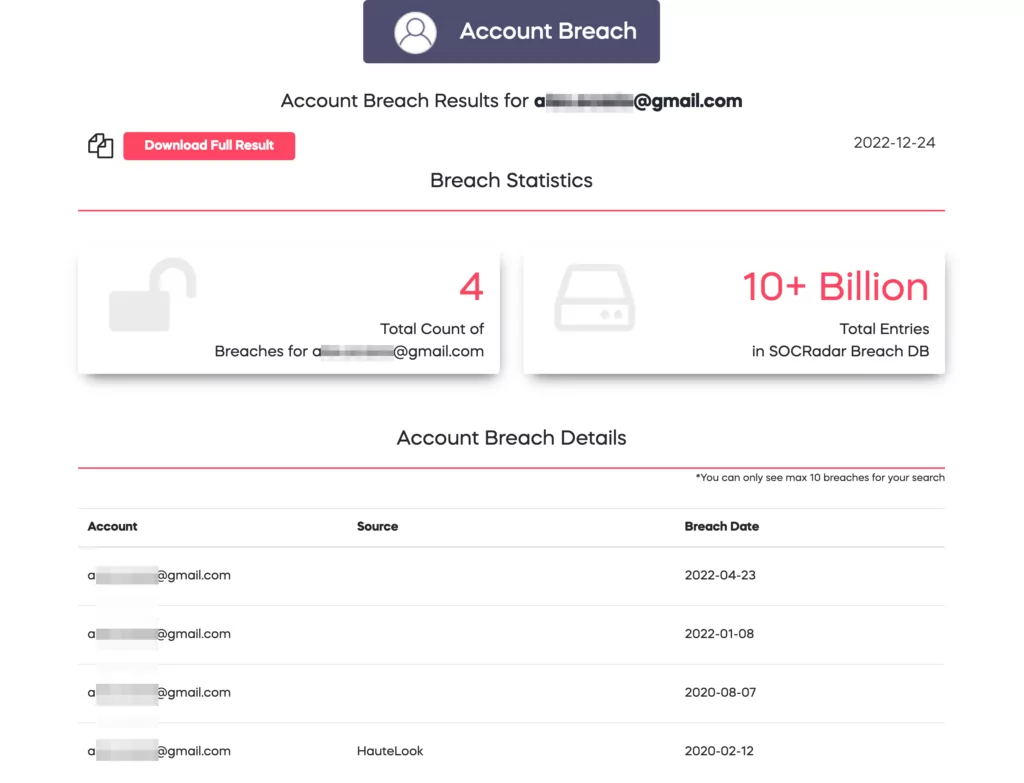
SOCRadar analysts searched the email addresses with SOCRadar’s Free Account Breach service. The results show that most of the email addresses in the sample were already breached in previous data breaches.
What are the Risks of Breached Data?
Since the data includes email addresses and phone numbers, hackers can use the information for social engineering attacks to take over the Twitter account. Then, the Twitter account can be used for phishing, such as the infamous Elon Musk Crypto scams on Twitter in 2021.
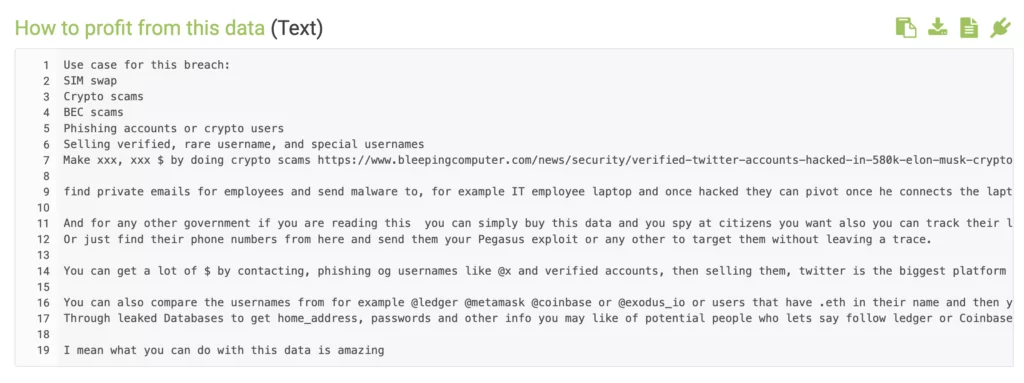
The threat actor also created a text about how to profit from the data and shared it with the post. For the use cases, the adversary “recommends”;
- SIM swap,
- Crypto scams,
- BEC scams,
- Phishing accounts,
- Selling usernames, and
- Creating a crypto scam
Who is the Threat Actor Behind the Alleged Twitter Breach?
The threat actor is new in the dark web forum where the post is shared. He joined the forum in December 2022 and has only posted a few times since joining. Only a little information is available at this point about the threat actor. His financial motivations and the suspicion around the authenticity of the data might indicate that he is a scammer.
How to Prevent Data Breaches and the Impacts of Data Breaches?
Most threat actors try to exploit vulnerabilities, especially Remote Code Execution (RCE) vulnerabilities on commonly used products. SOCRadar researchers monitor trends in the dark web, and it is evident that using vulnerabilities is one of the top methods for data breaches. Organizations should regularly monitor their external attack surface for possible vulnerabilities and use vulnerability intelligence to apply patches proactively.
The breached credentials or credentials publicly available in code repositories (e.g., Github) are also used by threat actors to gain access to the systems. For credential stuffing attacks, cybercriminals use automation tools and find the proper credential to log in to the target systems in a concise amount of time. While looking for anomalies in the system, organizations should proactively monitor leaked credentials and credentials publicly available in code repositories and even public buckets (either owned or third-party). Tools such as SOCRadar’s Cloud Security Module can automate organizations’ processes.
Would you like to learn if your organization’s credentials are shared in the dark web or public cloud buckets? SOCRadar’s Free Edition can provide the information in seconds.



































