Attack Surface Management
Gain visibility into your ever-growing attack surface.
You do not want your security posture to be poor when things dynamically change in your organization’s digital environment. Track your digital assets in real time and know your attack surface and protect them from cyber attacks.
Thanks to SOCRadar’s EASM advanced continuous monitoring algorithms, you gain enhanced visibility and context for your current and future attack surface without manually providing your asset inventory.
Get continuous visibility into vulnerable software, exposed sensitive information, third-party software, expired SSL certificates, DNS records, undiscovered cloud assets, and more with SOCRadar external attack surface management.
Explore SOCRadar’s External Attack Surface Management and meet with the easiest way to take a proactive stance against malicious activities.
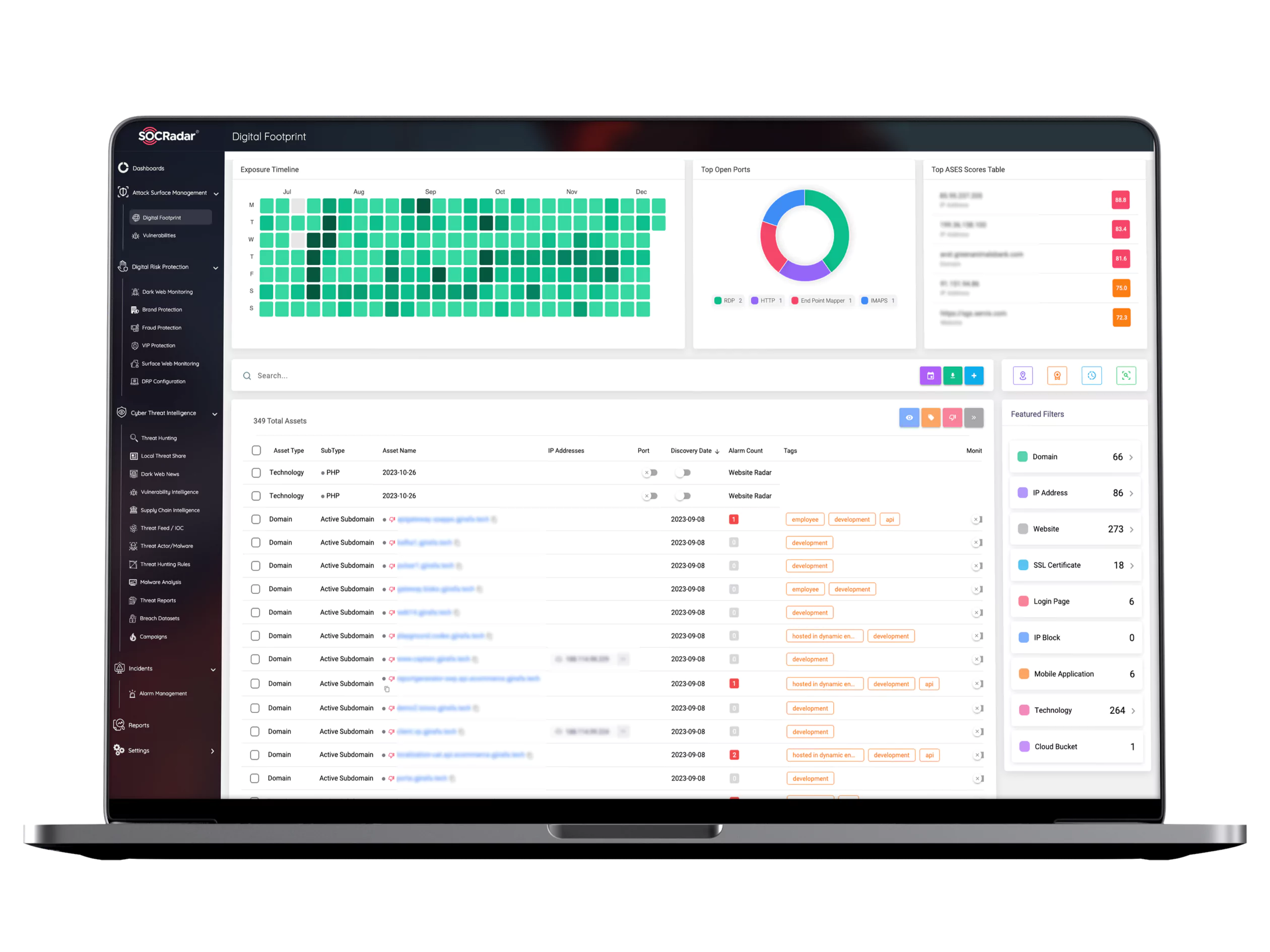
See What Hackers See in Your Digital Footprint
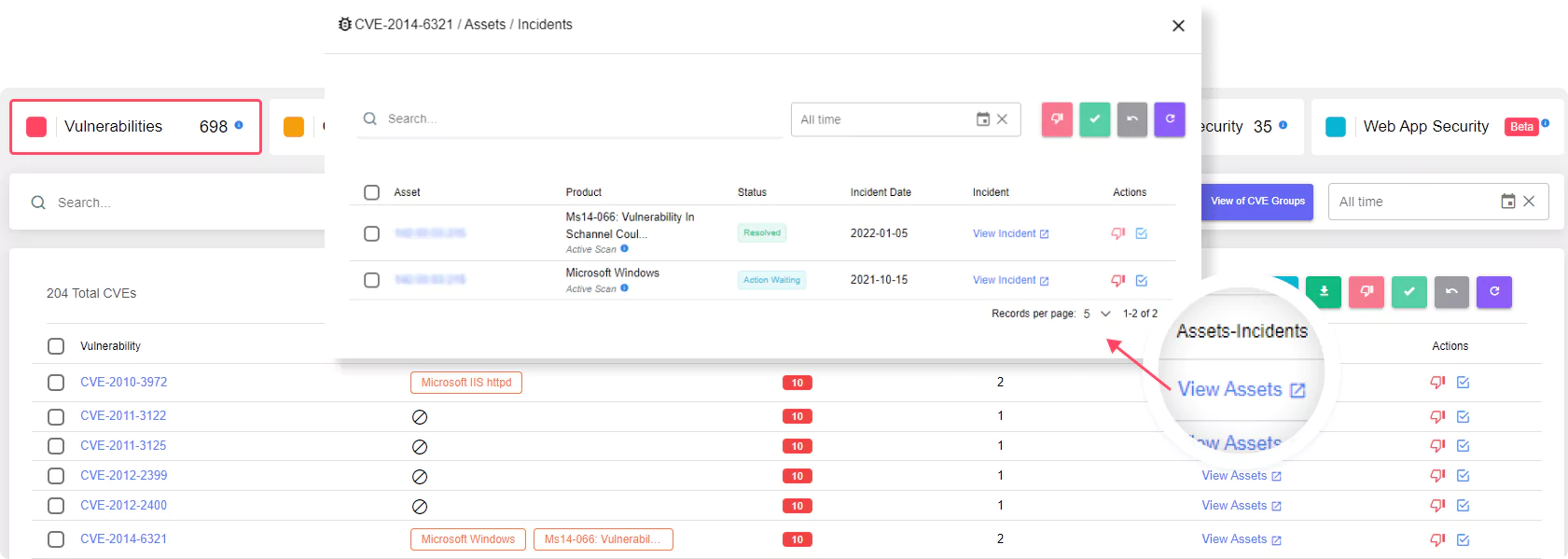
Discover your external-facing digital assets
Maintain an accurate, continuously updated and complete view of your external attack surface.
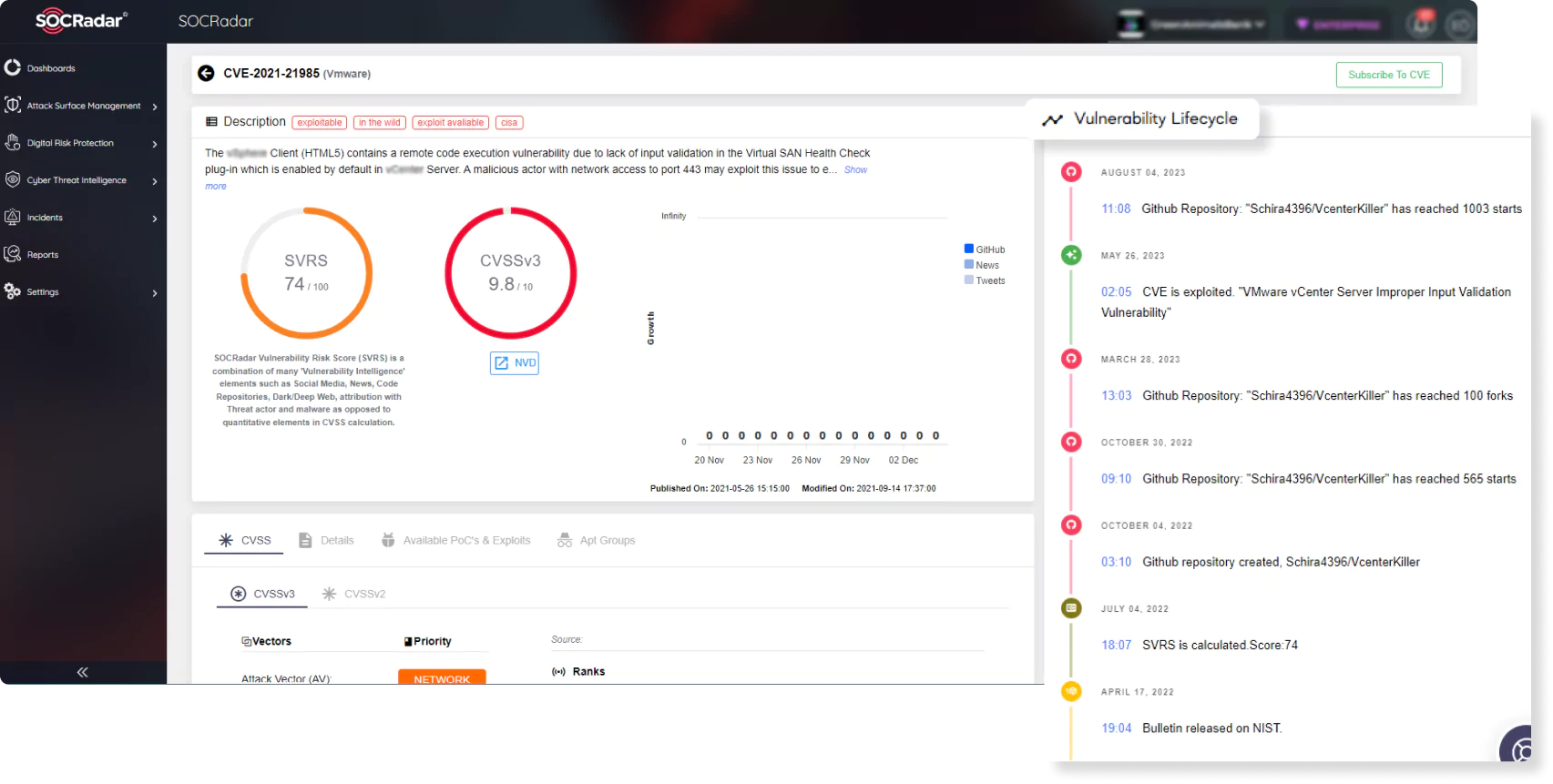
Identify hacker-exposed vulnerability risk
Get alert when a critical vulnerability is cross-referenced to your exposed software assets.
Level up your infrastructure monitoring capabilities
Spot threats early by keeping track of your public-facing DNS, Web and SSL infrastructures.
A key benefit of our service is the detection of Shadow IT – the unknown, unmanaged, and often unsecured elements in your network.
By bringing these hidden aspects to light, we enable your organization to preemptively address vulnerabilities, maintain stringent compliance, and uphold the integrity of your operations.
Join forces with us and experience a transformative approach to cybersecurity.
Every organization leaves a unique footprint – a trail of digital interactions, assets, and vulnerabilities in the digital world.
Your digital footprint is more than just a trace; it’s a critical aspect of your cybersecurity profile.
We thoroughly explore and secure each component of your digital footprint, identifying exposed assets and hidden vulnerabilities in various platforms, including external databases and cloud services.
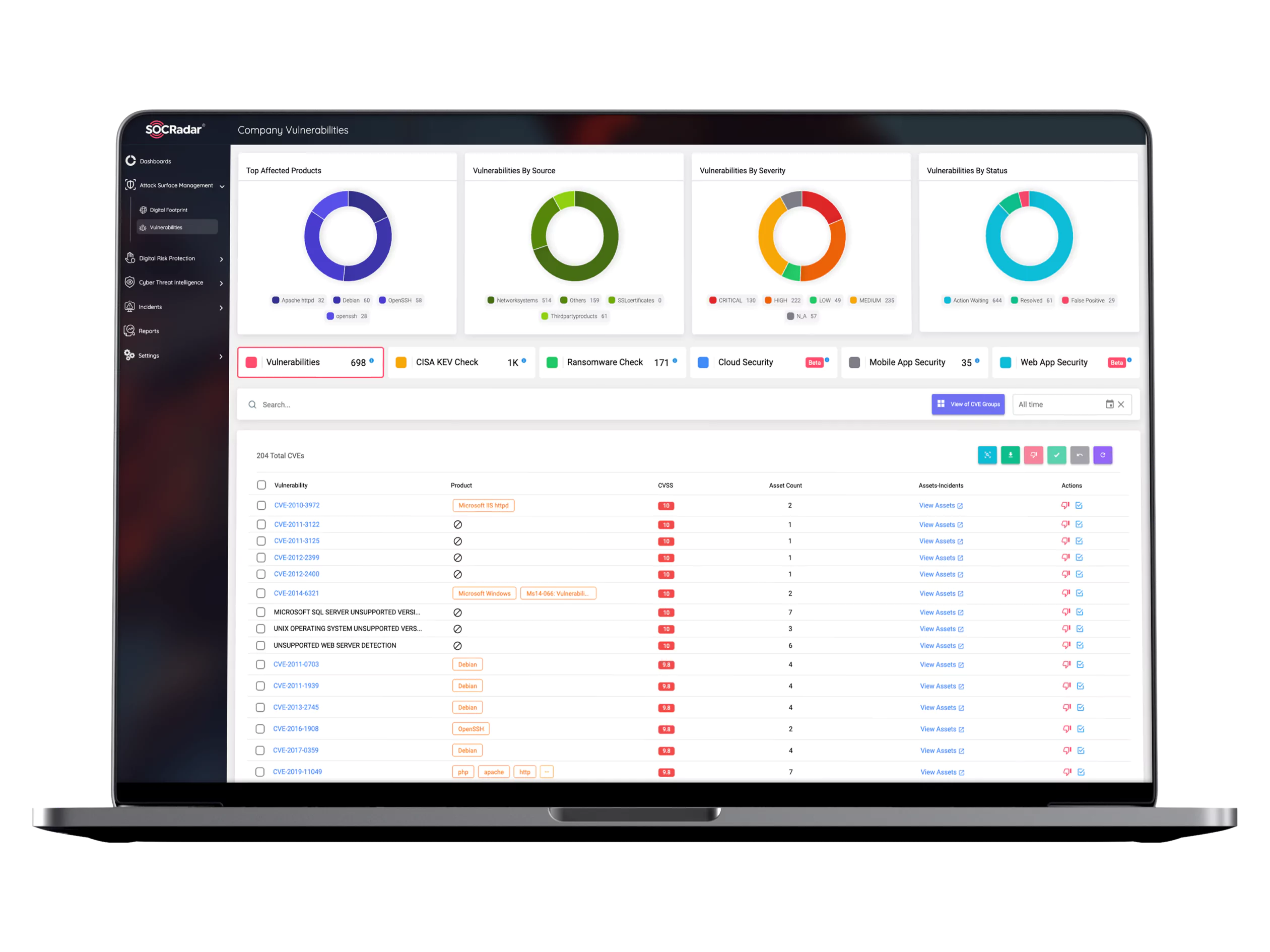
Features of SOCRadar External Attack Surface Management
Attack Surface Management
SOCRadar’s External Attack Surface Management (EASM) services help users gain additional visibility and context regarding the severity of unknown external-facing digital assets in an automated manner.
Our EASM solution provides security teams with direct visibility into all internet-facing technological assets in use and assets attributed to IP, DNS, Domain, and cryptographic infrastructure through advanced internet-wide monitoring algorithms.


The attack surface is the point or vector through which an attacker enters the environment and is merely a list of all possible ways in which the attacker can enter a device or network and extract data. In other words, the attack interfaces can be described as a collection of different points where unauthorized users could infiltrate an IT environment. There are a number of points from which attackers could attempt to penetrate the environment, such as access to the network, access from a remote location, or access via a network connection.
The attack surface can be categorized into 4 groups. All attack surfaces can be at least one of these 4 groups.
Attack surface refers to any asset such as domain infrastructure, website services, cloud technologies, etc. that is open to the Internet and can be exploited by the attacker. It can be described as the network interface of an organization, its network infrastructure, and resources. The attack surface includes:
- Known Assets: Known assets are the assets that are registered and managed by companies, such as websites, servers, etc.
- Unknown Assets: Unknown assets are domains that have been opened and not closed for marketing purposes forgotten by the security team, or some sensitive data that the development team forgot in repositories constitute unknown entities.
- Impersonating Assets: Malicious infrastructures such as fake domains and malicious social media accounts seem like belonging to companies but are created by attackers.
- 3rd Party Assets: The attack surface does not end up only targeting companies’ own assets and companies. 3rd party JavaScripts on the websites used by the companies or hosting servers used to locate their assets are part of the attack surface in the ecosystems of the companies where data is exchanged.
Good attack surface management products monitor all systems around the clock for newly discovered new security vulnerabilities. Real-time visibility is critical to detecting the impact of an attack on the attack surface of a range of networks, software, protocols, and services that run online in an enterprise. Given the number and complexity of network and software protocols and services in an online business, it can be difficult to identify which parts of your attacks are the source of breaches and intrusions. Identifying injury risks, which is dynamic and highly complex, is characterized by several complex areas to be explored, such as network infrastructure, network security, data security, and network management.
An organization’s external attack surface includes all the digital assets that are accessible from the internet. This can include websites, email servers, cloud storage and services, web applications, APIs, Internet of Things (IoT) devices, and more.
To manage the attack surface, it is necessary to first identify all assets open to the Internet. The digital footprint is important because companies have many assets that they do not know or forget, as well as assets they know and manage. For instance, some promotional pages opened for marketing purposes may have been forgotten to shut down or not notified to the security team. Any assets that are forgotten or not configured for security threats could be harmful to companies. Because attackers always prefer to attack companies over unmanaged assets.
EASM involves several key steps: asset discovery to identify all external-facing digital assets; vulnerability assessment to identify potential security weaknesses; risk assessment to prioritize threats based on their potential impact; remediation to address identified vulnerabilities; and continuous monitoring and reporting to keep the attack surface assessment up-to-date.
No, EASM is an ongoing process. The external attack surface changes as an organization’s digital footprint evolves and new vulnerabilities are discovered. This necessitates regular monitoring, updates, and adjustments to EASM strategies.
While EASM significantly reduces the risk of cyber attacks, no cybersecurity measure can guarantee complete security. Cyber threats evolve constantly, and new vulnerabilities can be discovered at any time. However, EASM, combined with other cybersecurity practices such as intrusion detection systems, security awareness training, and incident response planning, can offer a robust defense against most threats.
Organizations can reduce their external attack surface by regularly conducting vulnerability assessments and penetration testing, timely patching and updating software, employing strong access control measures, securing APIs, encrypting data, and utilizing other cybersecurity best practices.