
7 Important Life Lessons from 19th of March Attacks in Turkey
On the 19th of March 2021, a couple of the major companies in Turkey were hit by a cyber-attack. SOCRadar analysts have been determined that the domain names of the companies, acquired through the company named “Atak Domain” (atakdomain.com), redirected the fake propaganda page. They emphasized that all domain name owners who receive service from Atak Domain are affected.
What is Domain Hijacking?
Domain hijacking or domain theft is the alteration by misuse of privileges of domain hosting and registrant software systems of a domain name without the consent of its original domain registration owner.
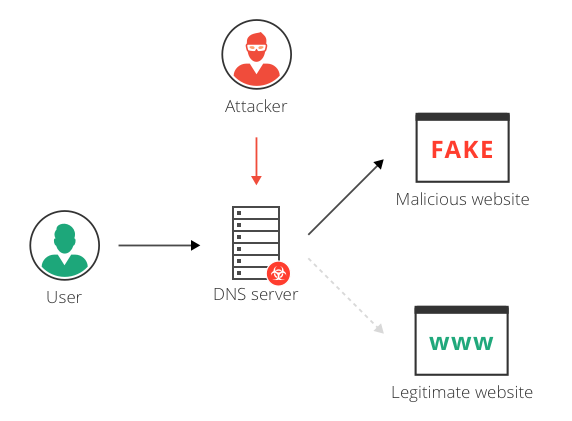
This may devastate the original domain name holder not only financially but also as regards readership and/or audience for non-profit or innovative web addresses. Because they may derive business revenue from a domain host or business website via the email accounts of that domain. The hijacker may use a domain name, after the successful hijacking, to enable other illegal activities such as phishing if a site is replaced by a site that records private information such as log-in passwords, spam, and/or even malware, which causes losses and unlawful gain to a third party.
How Domain Hijack Attacks Can be Prevented?
There are certain steps that a domain-name owner can take to reduce the exposure to domain name hijacking.
- Use strong email passwords and enable two-factor authentication if available.
- Disable POP if your email provider is able to use a different protocol.
- Tick the setting “always use HTTPS” under email options.
- Frequently check the “unusual activity” flag if provided by your email service.
- Use a two-step (two-factor) authentication if available.
- Make sure to renew your domain registration in a timely manner with timely payments and register them for at least five years
- Use a domain-name registrar that offers enhanced transfer protection, i.e., “domain locking” and even consider paying for registry locking.
- Make sure your WHOIS information is up-to-date and really points to you and you only.
- If you have 2500 or more domain names consider buying your own registrar.
- Monitor the DNS constantly
What is DNS Monitoring?
Many attack vectors are leveraged by attackers and organizations address these threats using multiple layers of perimeter security. These include next-generation firewalls, secure web gateways, sandboxing, intrusion prevention systems, anti-virus, EDR, and more. Yet despite these safeguards, bad actors continue to find ways by exploiting gaps outside of your perimeter. Over the last few years, a large number of organizations have been affected by DNS record manipulation (DNS Hijacking) including telecoms, ISP providers, and infrastructure providers. In addition to global-scale mass scanning of SSL certificates related to your domain.
When were the Attacks Took Place?
The attack took place on Friday, March 19, 2021, at 18:00, which is the end of business hours. It is obvious that the adversaries specifically choose after work hours to attack.
What kind of Attack was it?
The attack was done using a very old method called “domain hijacking”. In this method, there is an attack against the registrar company where the target companies registered their domain names. By entering the domain name management panel, DNS records are directed to a different site where it is shown as hacked. Although there is no change in the original website, the visitors see the indexed (message left) page because the DNS requests are directed to the IP address requested by the attackers.
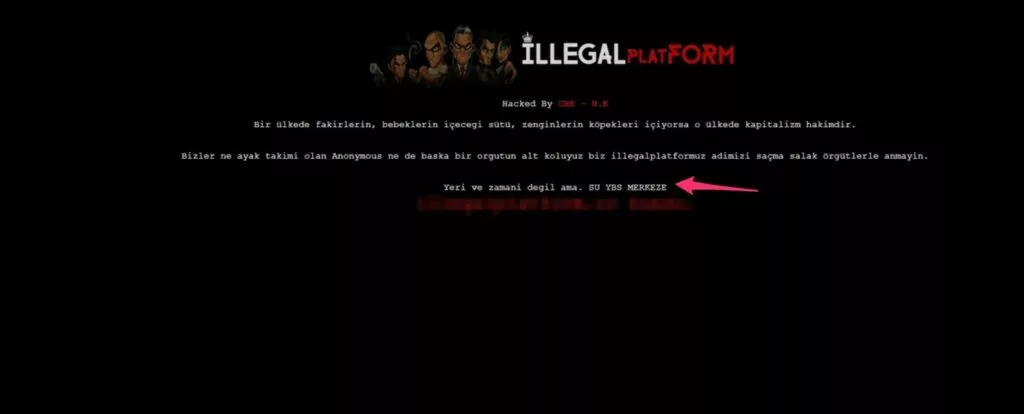
What was the Effect of the Attack?
The effect of the attack lasted around 4 hours. Meanwhile, many users could not reach the relevant sites and could not benefit from the services provided.
No data loss or disclosure of the relevant companies was experienced during the attack.
What Could Be Done with a More Advanced Attack Method?
- By directing the mail record (MX), incoming and outgoing e-mails to the employees of the company could be read.
- The data of visitors and users who entered credit card information or other information on the home page could be collected by making a fake page.
- Social media accounts of the relevant company could be seized by the email reset method.
Who Were the Attackers and How the Attack Carried Out?
The attacker is one of the most common profiles in Turkish forums. With the data obtained from SOCRadar® ThreatHose, there are some correspondences about how to get account information with brute-force and sharing some config files belonging to the domain company allegedly hacked (access to the domain management panel) on similar forum pages in December. It is understood here that this event is actually the last phase of the attacks covering a period of 2-3 months.
How did SOCRadar Detect the Attacks?
SOCRadar has the capacity to monitor auto-discovered DNS records with an interval of 10 minutes and generates real-time email alerts if there’s any change in A, AAAA, CNAME, NS, MX records.
SOCRadar Cyber Intelligence Platform detected this incident at 18:04 and notified the relevant companies using e-mail, telephone, and instant messaging channels.
How SOCRadar can Detect Similar Attacks?
SOCRadar can detect similar attacks very quickly with the following methods;
- Tracking the NS (Name Server) record changes of the domain
- Tracking the A record change of the domain
- Tracking the change of Whois information
- Tracking changes of website content and header information
- Automatic monitoring of deep web environments and alarms for company domains
External attack surface management also plays an important role in the prevention of such attacks.
What’s External Attack Surface Management?
External Attack Surface Management (ASM) is the process of discovering, listing, classifying, analyzing, prioritizing, and monitoring all information that can be collected on the internet and informing your organization about sensitive data by searching external digital assets.
A useful ASM follows your entire digital footprint over the Internet, discovering and collecting the information that relates to your company. But that could be either too much information or not useful information. That’s why instead of sharing this information with your company, it gets analyzed and classified first. After this step, the information is prioritized based on its sensitivity. Finally, monitoring is the last step.
In short, attacks surface is everything that attackers can and will discover as they research the threat landscape for vulnerable organizations.
Why is External Attack Surface Management Important?
To manage this dynamic attack interface, organizations must ensure that they have the right security controls to reduce the number of vulnerabilities in the attack surface that attackers can exploit. This can be done by using cybersecurity tools to minimize the places where organizations are vulnerable to cyber-attacks.
However, it is not impossible to put into perspective the enormous scale of an organization’s target area; it simply requires looking at it in a new way. Attack surfaces can be further reduced by proactively mapping the digital footprint, monitoring online channels for attack indicators, quickly defusing identified threats, and protecting customers, employees, and networks. To keep your organization safe, it is important to understand the way your infrastructure is exposed and vulnerable to attacks, and then prioritize activities that help reduce it. Once you understand what a cyber-attack is and what it involves, as well as how extensive your own is, security experts can begin to narrow down the types of attacks your infrastructure is exposed to.
ASM combines advanced Internet data intelligence and analysis to speed up investigations, understand the attack surface, and take action against digital threats. Continuous security monitoring is a level of attack area management concerning trusted digital assets of third parties. ASM tools provide insight and visibility into these assets to discover and monitor everything related to your organization on the Internet to bring the enormous scale of your attack surface into focus.
This real-time visibility is critical to the risk of violating the attack surface, which is dynamic and highly complex as it is a key component of any organization’s security strategy
What are the Similar Cases?
Basketball superstar Mark Madsen unknowingly bought a “stolen” (or hijacked) URL by way of eBay auctions rather than the more common auction sites such as Snapnames
Former Lakers and Timberwolf Mark Madsen once bought an eBay web domain in excess of $100,000. The person who sold it to him turns out that he has bought it unlawfully, and now he’s at the clink. Daniel Goncalves in December pleaded guilty to stealing the P2P.com domain name and selling it for $111,000 at the eBay web auction. He was sentenced to restitution. After an inquiry from the State Police Cyber Crimes Unit, Goncalves was indicted in 2009. He admitted unauthorized access to and transfer of his account on an account owned by P2P.com.
Lenovo and Google websites hijacked by DNS attacks
Lenovo’s main page and Google’s site for Vietnam briefly redirected people to another website. Both Google and Lenovo were victims of “domain hijacking,” a type of attack against the DNS.
In Lenovo’s case, Lenovo’s hackers have transferred the registration of their domain name to Cloudflare. Name servers advise a machine which IP address to view. CloudFlare’s servers then redirected people trying to go to lenovo.com to two IP addresses hosted in the Netherlands by the company Digital Ocean.
Google’s site for Vietnam briefly redirected people to another website. Like Lenovo, Google also had its google.com.vn domain name registered with Webnic.
In 2021, Perl’s domain was briefly hijacked, causing a relatively major issue with CPAN
People who visit perl.com have been redirected to perldotcom.perl.org. The Register spotted it on Afternic.com (part of GoDaddy) for $190,000 shortly after the hijack of the Perl.com domain. Soon after, the listing was drawn.
Users who might have selected Perl.com as their CPAN mirror are advised to update their mirror in CPAN.pm
What Lessons Can You Learn from the Attack?
- We are as safe as the weakest link of the chain. No matter how much we invest in security.
- Registrar companies usually are not taken into account when performing security audits of supplier/3rd party companies. But in reality, they should be placed at the top of the list.
- In similar cases, the durations of DNS records should be kept as short as possible in order to be able to recover quickly
- “Registrar lock” or “Client Transfer Prohibited” feature must be activated in Whois records.
- Registrar companies that do not offer multiple authentication services should not be preferred.
- DNS server and whois information changes should be monitored by a service in order to be notified of similar attacks as quickly as possible.
- Conducting crisis management exercises and having incident management and response procedures ready can be lifesaving in such incidents.
Cover image by Freepik



































