Around 50 Ransomware Attacks Targeting Financial Institutions
The Q3 Finance Industry Threat Landscape Report prepared by SOCRadar analysts has been published this week. The report includes a detailed analysis of the cybersecurity threats that most impact the financial industry globally.
One of the most prominent topics in the report was the ransomware attacks, which have been discussed frequently. In this blog post, you’ll find a summary of where ransomware is mentioned in the report. Then, besides ransomware groups, we will talk about another critical cyber security threat, APT groups.
You can read the full report by clicking here.
Deep Web Radar for Financial Institutions
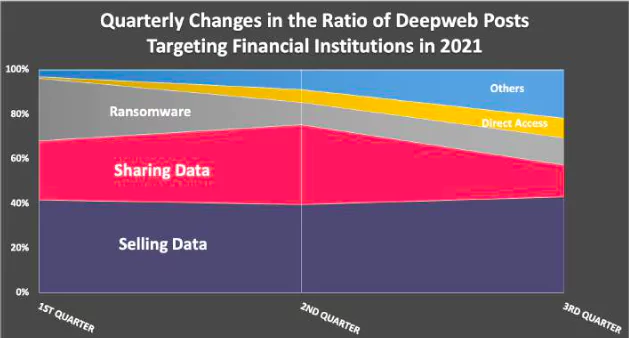
Ransomware groups, still a significant threat to financial institutions, target companies in other industries (especially manufacturing) more in the third quarter compared with the first quarter.
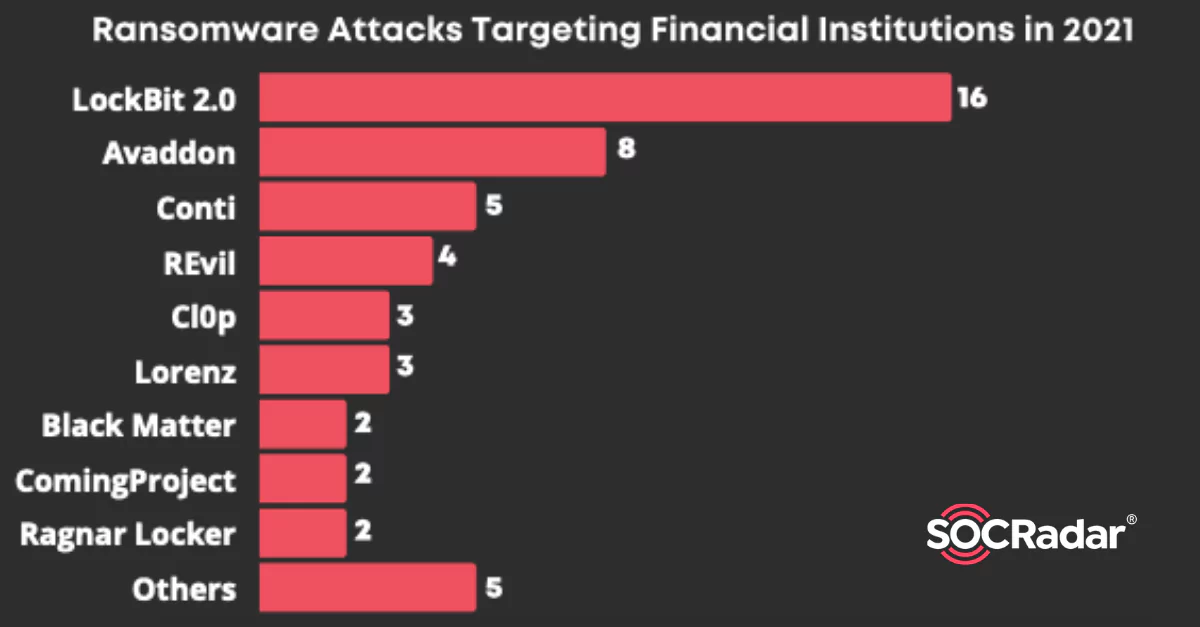
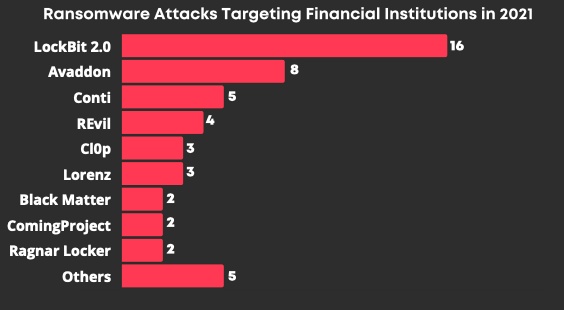
Various ransomware groups targeted financial institutions in 2021. Lockbit 2.0, Avaddon, Conti, ReVIL, and Cl0p are the head runners. Ransomware groups target fifty financial organizations around the globe.
Most Concerning Threat Actor: LockBit 2.0
Many significant ransomware gangs’ online presence tends to be limited to affiliate recruitment and their private networks. Over the years, LockBit ransomware operations have been active online, with gang representatives promoting the operation and supporting hacker forums. Like most Ransomware, the LockBit Group maintains forums on topics known as underground web boards to advertise their products.
LockBit is a new ransomware family that exploits widely available protocols and tools such as SMB and PowerShell. Lockbit Ransomware group launched its operations in September 2019, and LockBit Ransomware is recruited by penetrating networks of encrypted devices. In these operations, ransomware services threaten actors to be recruited by breaking through networks of encryption devices.
LockBit 2.0 is the most concerning ransomware threat actor for financial institutions. This group hit Two-third of ransomware victims in finance in the third quarter of 2021.
Techniques, Tactics, and Procedures (TTPs) of LockBit 2.0
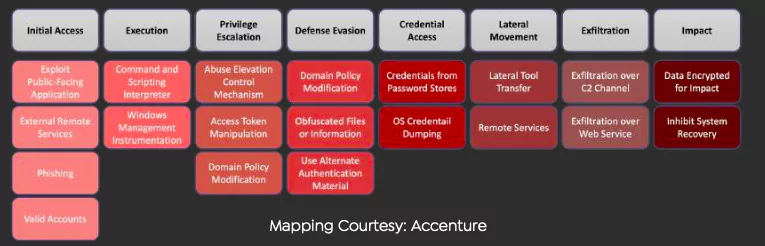
The new variant of LockBit 2.0 ransomware can encrypt Windows domains with Active Directory Group Policies. It automates the interaction and subsequent encryption of Windows domains with Active Directory group policies.
It adds a novel approach to interact with Active Directory to spread rogue malware to local domains by creating an updated global policy that disables antivirus, making it easier for new malware operators to engage in operations. The below diagram shows the TTPs of the Lockbit 2.0 ransomware group mapped to MITRE’s ATT&CK Framework.
State-Sponsored APT Groups Against Finance Industry
In addition to ransomware attacks, the report also included APT group attacks in the financial sector.
State-sponsored Advanced Persistent Groups (APTs) and financially motivated threat actors are more organized groups in cyberspace targeting several industries, including finance, with sophisticated attacks.
SOCRadar has listed significant threat groups that are active in 2021 and target financial institutions directly or indirectly.
Both ransomware and APT groups pose a significant threat to financial institutions. Threat actors tracking and grasping their TTPs are an essential arsenal for security teams of such institutions.
SOCRadar provides the actionable and timely intelligence context you need to manage the risks in the era of transformation.
Darknet and Deep Web Monitoring: SOCRadar’s fusion of its unique dark web Recon technology with the human analyst eye achieves further to provide in-depth insights into financially-targeted APT groups and threat landscape.