
How to Prevent Attacks by APT Groups Using SOCRadar
What is an APT Group?
The advanced persistent threat (APT) is a stealthy method to gain access to your company’s data. It requires a high degree of secrecy, skill, and patience – which is why the most dangerous cybercriminals use this method against both high-profile targets and small businesses.
According to the Cloud Adoption Practices & Priorities Survey Report, 53% of IT professionals see Advanced Persistent Threat (APT) attacks as one of their organizations’ top security challenges.
Surprisingly, according to the Ponemon Institute, only 68% of IT administrators know what an APT is. If you don’t know your enemy, you cannot defeat them. APT groups are one of the most dangerous adversaries trying to infiltrate your organization.
A cyber attack against a company with an advanced security system is time-consuming, expensive, and requires specialized knowledge and tools. Multi-stage and well-planned attacks targeting a specific company are called APTs.
To carry out such attacks, hackers form criminal groups known as APT groups. These groups differ from other cybercriminals in that they tend to adapt to defenses and maintain their presence in a system for months or even years.
Most hacking attacks are fast-damaging, but APTs take a different, more strategic, and stealthy approach. Attackers come through traditional malware such as Trojans or phishing but then cover their tracks as they sneak around and place attack tools on the network.
- Advances by APT groups are more sophisticated than hacking.
- APT groups include talented members with highly technical backgrounds.
- The motivation behind hacker groups is usually financial or political, while the reason behind the groups can be strategic.
- APT groups are generally subsidized, government-sponsored groups that have much better and more advanced equipment. There have also been large-scale attacks against specific non-government-sponsored targets lately.
There Are Many Recent APT Attacks
The attack, which exploits the software vulnerability while downloading the update of SolarWinds program Orion, will likely overshadow it as the most costly one. More than a thousand SolarWinds customers exposed to the first phase of the Sunburst malware are undergoing threat assessment to determine if they are among the primary targets of attackers.
Microsoft has identified more than 40 customers at the actual target compromised with complex TTP in addition to existing TTP (Tactical, Technical, Procedural).
SUPERNOVA is another less developed threat actor that spreads backdoor vulnerabilities. According to the investigations, the US and UK stated that Russia was behind the attack on the 15th of April. In addition, Russian security companies are included in the sanction lists.

On the 21st of July, France’s National Agency for Information Systems Security (ANSSI) issued (1) an alert to warn organizations that a threat group tracked as APT31 is abusing compromised routers in its recent attacks.
According to ANSSI, this “massive offensive campaign” continues and has affected many organizations in France. The agency shared IOCs to help organizations detect potential attacks.
“Our investigations show that the threat actor uses a network of compromised home routers as operational relay boxes to perform stealth reconnaissance as well as attacks.” ANSSI said. APT31 is an APT group, also known as Zirconium, Judgment Panda, and Red Keres, with ties to the Government of China.
APT31 is one of three threat groups that the UK government has officially attributed last week to Microsoft Exchange server attacks affiliated with the Chinese Government. Besides the UK, the US, New Zealand, Canada, Australia, European Union, NATO and Japan also claim that the group in question is behind these attacks.
In 2020, British officials stated that APT31 targeted government institutions, political figures, contractors, and service providers in European countries, including the Finnish parliament.
A security researcher highlighted that the approximately 160 IP addresses shared by ANSSI are primarily associated with Asia, Latin America, and Africa. About a third of the devices are located in Russia.
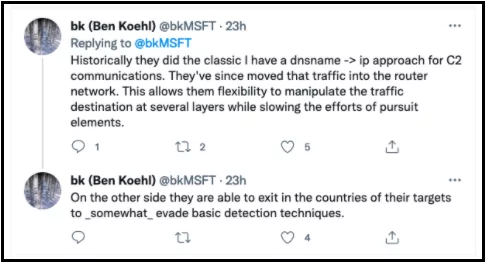
Ben Koehl, the Chief Threat Analyst at Microsoft’s Threat Intelligence Center, stated that ZIRCONIUM has been detected to run multiple router networks to facilitate these actions, and it prevents tracking thanks to its layered structure.
What are the ways to avoid APT attacks?
- Provide basic cybersecurity training to your staff and make them aware of cybersecurity policies. By tightening access controls and providing 2FA logins, you protect the system against possible leaks.
- If your organization has Operational Technology (OT) or critical infrastructure, ensure that it is disconnected from the corporate network or unauthorized connections are not allowed.
- Provide your SOC team with advanced Threat Intelligence (TI) access and active monitoring of threat actors.
- Use attack-surface security solutions that detect potential threats and zero-day vulnerabilities at an early stage.
- Use endpoint solutions that detect activities that may be indicative of a targeted attack.
- Reduce the number of vulnerabilities that APT attackers can exploit by keeping security patches up to date.
- Close the gaps in your network by establishing a multi-layered security infrastructure within your organization.
- With your structure consisting of Firewall, WAF, IPS, and SIEM, in addition to the anomalies to be experienced in the system, review access requests and login processes faster and detect anomalies.
- Identify the organizations’ most valuable assets. In this way, the organization can protect its most attractive goals in many ways.
- Create a “whitelist”. Determining which domains and applications access a network further limits the APT attack surface.
How Can You Track APT Groups Using SOCRadar?
Actively monitor APT groups
Threat actors and APT groups often use a variety of tools and tactics to achieve their goals. Understanding and tracking attackers provide insights into existing TTP that may be far more important than easily replaceable IOCs.
Through automated data collection, classification, and AI-powered analysis of hundreds of sources across the surface, deep and dark web, SOCRadar monitors the activities of APT groups in a MITRE ATT&CK-compliant structure. It enables organizations to identify the use cases to more effectively detect and prevent malicious activity.
With the SOCRadar Threat Actor monitoring module, you can gain essential insights into the activities of government-sponsored APT groups to stay up-to-date on new and emerging tools used to run their global operations.
Accelerate threat hunting, research, and analysis
Combining SOCRadar’s unique technology with a human analyst perspective leads to in-depth and actionable threat intelligence profiles of current and future threats. With SOCRadar threat analysis, you can get a service to analyze malware actively used by APT groups.
Protect from potential APT group attacks with threat feeds.
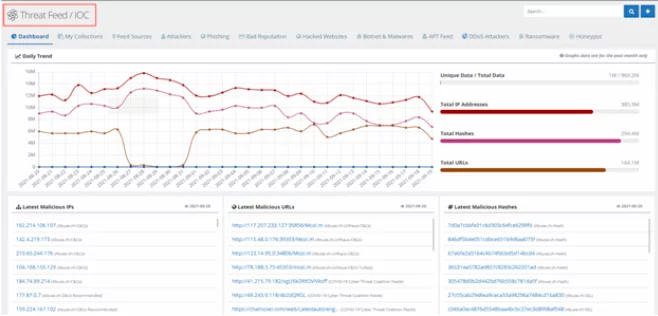
SOCRadar’s Threat Feed and IoC Management module help cybersecurity teams investigate cyber threats with data backed up and enriched by easy-to-use dashboards. Cybersecurity professionals can customize feeds, stay up-to-date on the latest threats, search for danger indicators (IOCs), and integrate them into the company systems.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Try for free



































