How to Detect Phishing Attacks?
1-What is a Phishing Attack?
Phishing is a cyberattack that collects sensitive information such as login credentials, credit card numbers, bank account numbers, or other financial information by pretending to be a real website or email. Personal information such as identity security numbers, phone numbers, and social media account information are also common targets for identity theft cybercriminals.
A phishing attack deceives victims by creating a sense of urgency combined with social engineering. When the victim opens a phishing email or text message and clicks on the malicious link, they are redirected to a fake website that matches the real site.
Commonly used phishing attacks are cloning financial institutions, emails from colleagues, government agencies, social media sites, and online payment processors.
Although phishing is one of the oldest cybercrime, it remains a significant cyber threat for many organizations. This is due to its widespread use and advanced phishing campaigns. Phishers are collecting more and more information about their targets to increase the effectiveness of phishing messages.
What is the Purpose of Phishing Attacks?
Generally, at least one of the following is the goal of phishing attacks:
- Collection of sensitive information:
- Sending suspicious emails is intended to trick the victim into disclosing login credentials or disclosing personally identifiable information.
- The classic phishing scam is to send millions of emails tailored to look like a big bank, and the victim clicks on the link and logs into the fake web page to gain access to the victim’s bank account.
- Malware download: Phishers attach malware or ransomware to email.
While there are many types of Phishing Attacks, all phishing attacks rely on some form of disguise. Generally, the type of phishing attack used will depend on how the phisher chooses his/her target(s). A phishing attempt sent to millions of potential targets will be tailored to a popular brand like Microsoft, PayPal, or Facebook. In contrast, a spear-phishing attack would be hyper-targeted to a specific organization or person.
Common symptoms of a phishing attempt include:
- Use of subdomains, misspelled URLs (typosquatting), or other questionable URLs
- The threat actor is Gmail, Outlook, Yandex, etc. instead of a corporate email. He/She is using a free email provider and the link of the domain name in the email content does not directly match the link of the original domain name.
- The message is designed to evoke a sense of fear or urgency.
- The message includes a request to verify personal information such as your bank login or social media password.
- The Message contains serious typos and/or grammatical errors.
- The email contains an unexpected or unusual attachment that could be malware or ransomware
- You know the sender’s name but do not normally contact them, especially if the email is unrelated to your job responsibilities
- The URL in the email does not match the URL of the site it uses for social engineering.
- The forwarded message sounds too good to be true like you’ve won a contest you’ve never entered.
- Provides feeds to your system by keeping a list of known/detected phishing web pages.
2-Recent Phishing Attacks
Hackers Perform Phishing Attack to Seize Sony Company Data
A major security breach occurred at Sony with a series of spear-phishing emails sent to Sony employees. Threat actors sent malicious emails to employees who they identified by searching Sony’s names and titles on LinkedIn, posing as company employees. After all, more than 100 terabytes of data including records such as financial records, customer data, etc. were captured. This phishing attack caused Sony more than $100 million in financial damage.
In February 2016, analytics firm Novetta issued a joint investigative report on the attack. The report, published in collaboration with Invincea, Trend Micro, PunchCyber, RiskIQ, Kaspersky Lab, Symantec, AlienVault, Carbon Black, ThreatConnect, and Volexity, concluded that a well-resourced organization had committed the intrusion, and that “we strongly believe that the SPE attack was not the work of insiders or hacktivists“. The analysis said that the same group is engaged in military espionage campaigns. So it was evaluated that it was made by a state-supported group, although it is not known exactly which group it was.
The U.S. Department of Justice has accused three North Korean computer programmers (Park Jin Hyok, Jon Chang Hyok, and Kim Il) of trying to extort and steal more than $1.3 billion as part of a global cyber scheme involving the hack of Sony Pictures Entertainment in 2014. A Canadian-American who allegedly laundered some of the stolen money also pleaded guilty. Also, the three Koreans in question are believed to be behind the 2017 WannaCry 2.0 ransomware attack, which affected computers in 150 countries and most notably damaged the UK National Health Service’s computer network.

The FBI has released a ‘Wanted’ poster
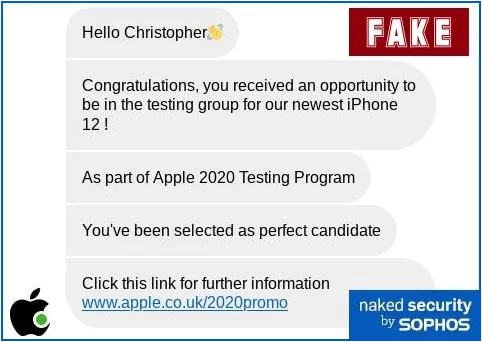
Free iPhone 12? Beware of This Fake ‘Apple Chatbot’ Invitation
Apple, one of the world’s largest smartphone companies, has reportedly been the target of a smishing campaign. With a fake Apple chatbox message, users have been informed that they have a chance to be part of Apple’s 2020 testing program for the new iPhone 12. Buyers are required to pay a delivery fee. Redirecting them to a malicious website, threat actors intercepted victims’ payment card credentials.
3- How to Avoid Phishing Attacks
One of the most important ways to prevent phishing attacks is awareness training and training of personnel on phishing attacks. Lehigh University has an important resource of recent phishing examples that you can use to train your staff.
In addition, provide training for your staff to implement the following measures in the phishing attack:
1. Customize your anti-spam settings properly and use powerful spam filters: You need powerful spam filters that can prevent files containing malware from reaching users.
2. Do not open suspicious-looking attachments: This article does not only apply to messages sent by people you do not know. It also applies to senders you believe are your acquaintances. The vast majority of ransomware attacks that originate from phishing are the result of obtaining the credentials of administrator-level employees.
3. Avoid giving out personal information: Attackers may aim to send a phishing email in preparation for the attack, and they need to get your information from somewhere. They can obtain it using OSINT techniques by reviewing your social media posts or public profiles for important information.
4. Use the Show File Extensions feature: This is useful when scammers are trying to use a confusing technique where a file appears to have two or more extensions.
5. Authenticate email users: You should also use technologies such as the Sender Policy Framework (SPF), Domain Message Authentication Reporting and Compliance (DMARC), and Domain Keys Identified Mail (DKIM) to prevent malicious people from using email spoofing techniques.
6. Install a browser plugin to block pop-ups: Pop-ups serve as a common entry point for attackers to launch attacks. That’s why you should look into installing browser add-ons to stop pop-ups in their tracks.
7. Periodically train employees against social engineering.
8. Block known malicious Tor IP addresses
9. Make them watch out for emails that create a sense of urgency
10. Make sure to use 2FA authentication on every system where possible
11. Looking at SSL extensions
12. Train your staff not to disclose personally identifiable information (PII) that could be used for spear phishing or whaling (such as date of birth, address, or phone number)
13. Be careful about URL redirects (not going to different sites with the same design)
We can reduce the effects of phishing attacks with training. As stated in the Verizon DBIR 2021 report, we cannot remove it altogether. For example, simulated phishing emails are sent to 1148 users with real phishing emails. While users never click on the simulated phishing email, 2.5% click on the real phishing email. In this context, the company should use a layered cyber security program to prevent phishing emails from reaching your personnel.
4-How to Use SOCRadar to Detect Phishing Attacks Early?
With the Extended Threat Intelligence Service, SOCRadar protects from phishing attacks with the following items.
SOCRadar AttackMapper module prevents and quickly detects phishing attacks by discovering and tracking your assets on the internet:
● Making an inventory of digital assets open to the Internet,
● Searching the e-mail accounts of your employees on the Dark & Deep Web via your MX registered domains and reporting the disclosure of your company employees’ e-mail accounts and the seizure of their passwords.
● Investigation of private e-mails of VIP and critical personnel (finance, developer, information security, Legal department, etc.) on Dark & Deep Web and reporting the situation of their passwords being compromised.
● With the DLP identifiers feature, your company’s Credit card, Critical personnel information (Identity Number, Telephone Number), etc. are searched on the Dark & Deep Web and the disclosure situation is reported.
● Provides SPF, DMARC, and DKIM control on your MX registered domains, used to prevent email spoofing techniques.
SOCRadar RiskPrime Module provides the detection of intelligence information about your assets and your company:
● Creating alarms in possible situations by automatically tracking company domains in Dark and Deep web environments,
● The HUMINT ability of SOCRadar dark web analysts provide your company to communicate with the threat actor for confirmation of the accuracy of up-to-date information and remove postings for increasing the company’s reputation when necessary
● Creating alarms in possible situations by automatically following the 3rd party companies providing services to your company in Dark and Deep web environments,
● Reporting your customers’ private emails by searching the Dark & Deep Web and revealing their passwords
● Private e-mails of VIP and critical personnel (finance, developer, information security, Legal department, etc.) are searched on Dark & Deep Web, and their passwords are reported.
● Thanks to the DLP identifiers feature, your company’s Credit card, Critical personnel information (Identity Number, Telephone Number) are searched on the Dark & Deep Web and the situation is reported.
● Creating alarms in possible situations by automatically following the 3rd party companies providing services to your company in Dark and Deep web environments,
SOCRadar ThreatFusion Module provides intelligence on current cyber events:
● Vulnerability Tracking with internal/external systems and/or applications for vulnerabilities notifications,
● Integration of IOCs used by threat actors into security devices,
● Integration to detect and block phishing domains for phishing attack purposes,
● Active monitoring of threat actors,
● Threat sharing about phishing attacks actively informs security personnel.
● Analyzing suspicious files with the Threat Analysis module.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Try for free