
Intelligence Pioneers: Meet the Top 10 CTI Experts
The expertise of Cyber Threat Intelligence (CTI) professionals is essential in strengthening digital defenses against ever-evolving threats. Within this elite cadre of experts, the top 10 CTI Experts featured in this compilation stand out for their visionary insights, groundbreaking research, and unwavering dedication to cybersecurity excellence.
From pioneering threat hunters to innovative researchers, these individuals represent the forefront of CTI, driving forward the frontiers of knowledge and resilience in the face of cyber adversaries.
While we’ve previously explored the Top 10 Twitter Accounts to Follow for Threat Intelligence, this blog takes a deeper dive into the top 10 CTI experts overall. Join us as we explore the remarkable contributions and enduring impact of the top 10 CTI experts, whose unwavering commitment to cybersecurity continues to shape and secure our digital world.
Will Thomas (BushidoToken)
Will Thomas, widely recognized by his alias BushidoToken, emerges as a prominent figure in the cybersecurity field. With a background as a security researcher and a co-author of the esteemed FOR589: Cybercrime Intelligence course, Thomas showcases profound expertise in threat analysis and cyber defense strategies.
His contributions extend beyond traditional avenues, as evidenced by his active engagement on GitHub, where he shares insights on open-source tools for CTI, deep dark web CTI (in which he collects Deep and Dark web sources that can be useful in CTI), OSINT, and more. Moreover, as a Cyber Threat Intelligence (CTI) Researcher at the Equinix Threat Analysis Center, Thomas leverages his diverse skill set to effectively decipher and counter evolving cyber threats.
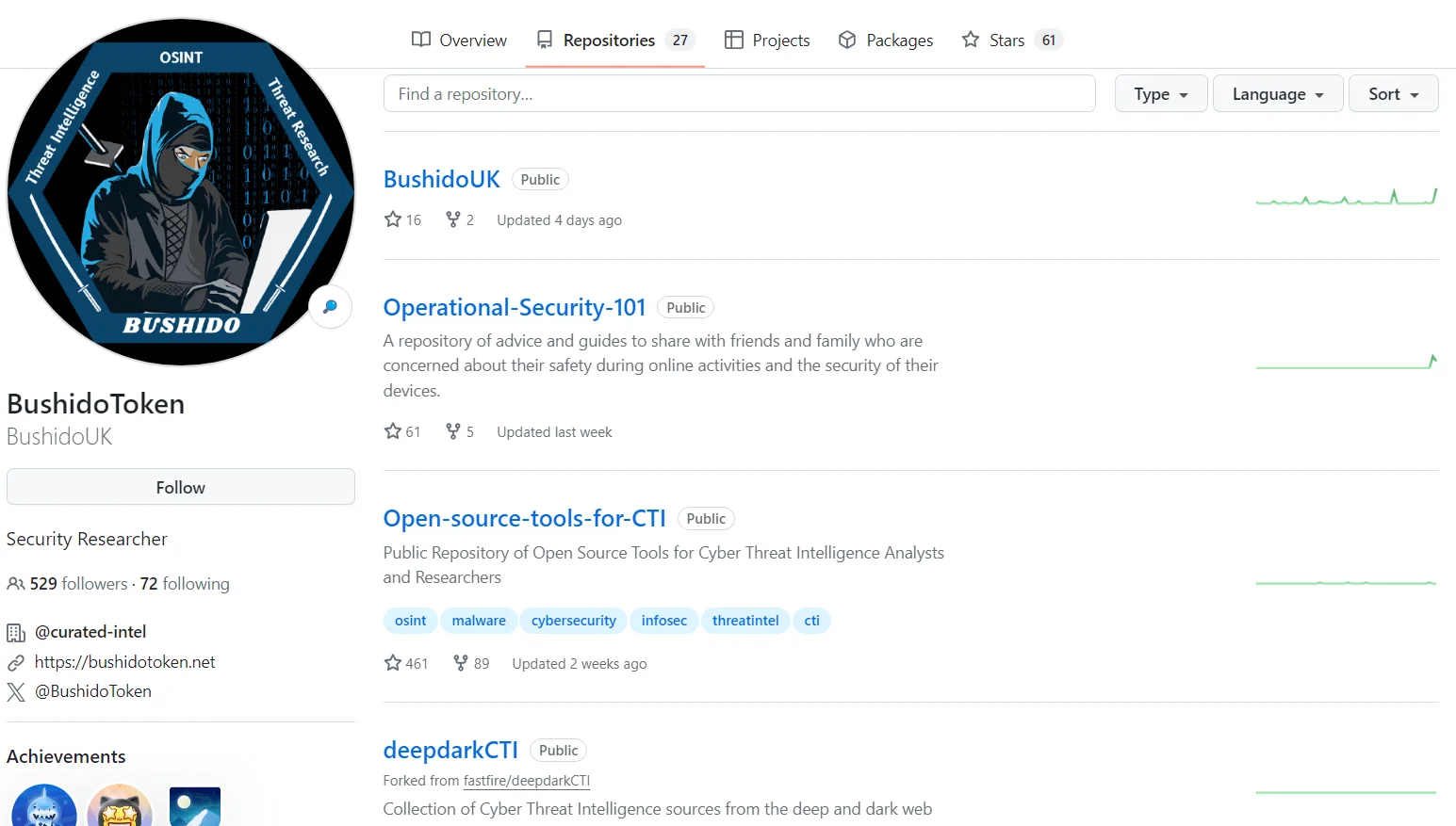
BushidoToken GitHub repositories
He maintains an active presence on social media, engaging in discussions about significant cyber events, recent examples being LockBit and Operation Cronos. Through his insights and opinions, he offers valuable perspectives on these events and potential solutions to address emerging challenges in the cyber world.
Additionally, he shares updates and analysis on his research blog, ensuring the cybersecurity community stays informed about the latest developments and trends.
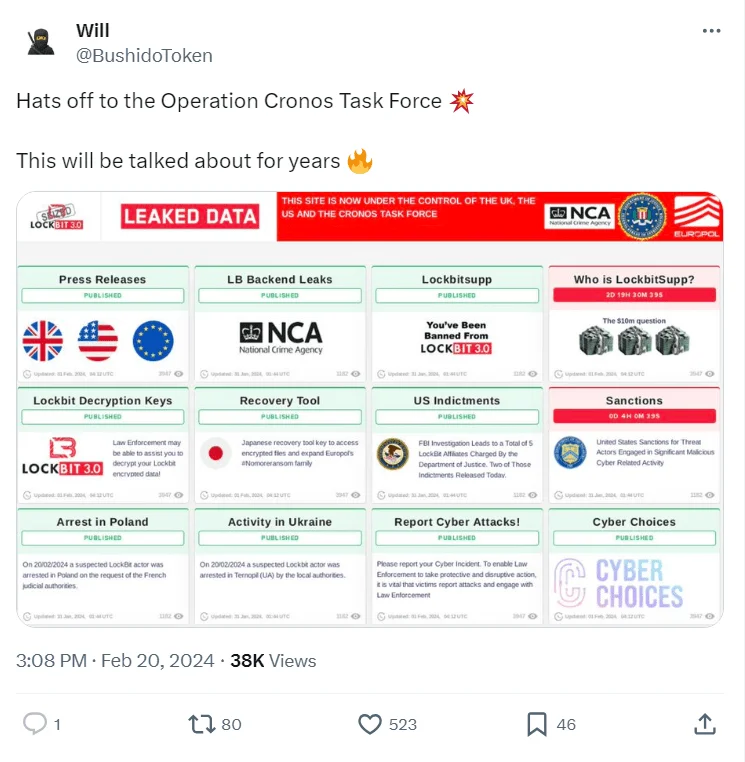
BushidoToken tweet about Operation Cronos (source: X)
In October 2023, Will Thomas participated in the STAR Threat Analysis Rundown Livestream Summary on YouTube alongside host Katie Nickels. Leveraging Will’s extensive experience in monitoring adversary chats and dark web forums, they discussed cyber threats that defenders should pay attention to in recent times.
SOCRadar’s Dark Web Monitoring module provides real-time surveillance of the hidden corners of the internet, identifying potential threats and breaches before they impact organizations. By continuously monitoring underground forums and illicit marketplaces, it proactively detects stolen credentials, sensitive data leaks, and emerging threats.
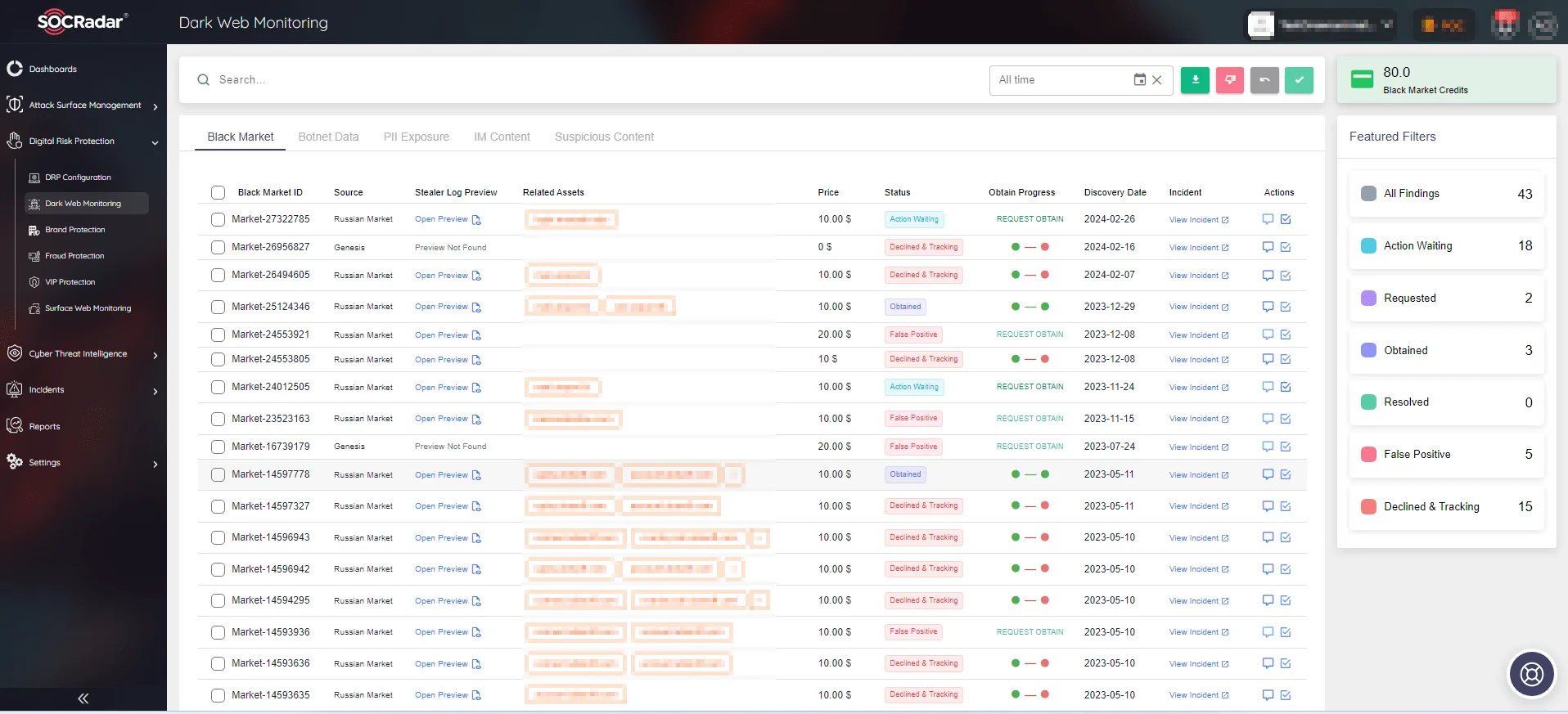
SOCRadar’s Dark Web Monitoring
Rebekah Brown
Rebekah Brown’s journey in intelligence began with traditional military work, focusing on Chinese cryptologic linguistics before transitioning to network warfare analysis, where she merged linguistic expertise with network defense. Her enthusiasm stemmed from blending various intelligence facets innovatively, shaping her impactful career trajectory.
Rebekah Brown SANS profile
Rebekah has provided threat intelligence across diverse security programs, including national security operations, governmental entities, and Fortune 500 companies. Currently at Apple, she focuses on Security Engineering and Architecture while also serving as a course instructor and mentor at SANS.
Rebekah co-authored the renowned book “Intelligence-Driven Incident Response” with Scott Roberts, showcasing her expertise. Her dedication to understanding intelligence sources, conducting analyses, and elucidating implications to various audiences underscores her influence. A pivotal White House briefing on cyber warfare highlighted her role in shaping coordinated defensive and offensive cyber operations. As a mentor, Rebekah fosters an environment where diverse backgrounds contribute to collective intelligence endeavors. With academic accolades and a holistic approach to intelligence analysis, Rebekah exemplifies dedication to her craft.

Intelligence-Driven Incident Response, 2nd Edition
Scott J. Roberts
Scott J. Roberts is a prominent figure in the realm of CTI experts and Incident Response, highlighted by his co-authorship of the acclaimed book “Intelligence-Driven Incident Response.” His contributions underscore the pivotal role of CTI in enhancing Incident Response methodologies. Scott’s work underscores the symbiotic relationship between CTI and Incident Response, emphasizing the need for proactive intelligence-driven approaches to mitigate cyber threats effectively.
Scott J. Roberts SANS profile
Through his research and advocacy, Scott has championed the integration of CTI into Incident Response frameworks, advocating for a holistic and intelligence-driven approach to cybersecurity. His insights and expertise have influenced the evolution of CTI practices, shaping strategies to combat emerging threats effectively. As a thought leader and practitioner, Scott continues to drive innovation in the field, empowering organizations to bolster their cyber resilience through informed decision-making and proactive threat mitigation strategies.
Kevin Beaumont
With over two decades dedicated to cybersecurity, Beaumont’s career trajectory exemplifies expertise and commitment worth following. Beginning as an analyst in the UK, he transitioned into roles as an information security architect and eventually assumed the mantle of SOC manager. His insights and contributions are reflected in platforms like DoublePulsar and his Mastodon account, where he shares valuable cybersecurity perspectives.
Kevin Beaumont Mastodon profile
Beaumont’s GitHub repository hosts hunting queries, shedding light on critical vulnerabilities like Follina, PaperCut, DogWalk, and notable incidents such as the Kaseya VSA attack. His extensive experience and proactive engagement make him a notable figure within CTI experts, offering valuable insights and resources for professionals and enthusiasts alike.
Kevin Beaumont AdvancedHuntingQueriesGitHub repository
Valentina Costa-Gazca
Valentina Costa-Gazca, CEO & Founder of V·ONE Labs, is a prominent figure in the cybersecurity realm, dedicated to revolutionizing threat management practices.
Costa-Gazcón LinkedIn profile
Her book, “Practical Threat Intelligence and Data-Driven Threat Hunting,” serves as a cornerstone for cybersecurity professionals, offering insights into identifying and neutralizing threats in a data-centric manner.
Beyond writing, Costa-Gazca’s passion extends to creating transformative solutions. She is spearheading the development of a cutting-edge platform that provides real-time insights into malware activity, empowering CISOs to proactively manage operational and tactical risks.
With a profound understanding of the evolving cybersecurity landscape, Costa-Gazca is committed to fostering a safer digital future. She actively seeks investors who share her vision for groundbreaking cybersecurity solutions, aiming to mitigate the ever-present threat of cyber attacks.
Johannes Ullrich
Johannes Ullrich is a prominent figure in computer security, known for his leadership at the SANS Technology Institute and foundational role in founding the SANS Internet Storm Center (DShield). With a Ph.D. in physics from the University at Albany, Ullrich’s expertise spans both physical sciences and cybersecurity, evident by research grants from esteemed institutions like NASA and the Department of Energy.
Johannes Ullrich SANS profile
As the Dean of Research and a SANS Faculty Fellow, Ullrich oversees crucial systems protecting networks from cyber threats. He founded the SANS Internet Storm Center, a pivotal platform for monitoring global cyber threats. Network World Magazine recognized him as one of the Top 50 Most Powerful People in Networking in 2004. His influence extends to the daily ‘Stormcast’ and LinkedIn, where he shares insights on cybersecurity, making him a key figure in the battle against cyber threats.
He also provides online courses at SANS, including “Application Security: Securing Web Apps, APIs, and Microservices,” emphasizing proactive measures against web attacks. Throughout the course, participants explore the vulnerabilities of web applications and learn practical strategies for understanding web app security.
Johannes Ullrich SANS courses
Graham Cluley
Graham Cluley is a prominent figure in cybersecurity, boasting a career spanning several decades and encompassing various roles from programming to public speaking. Beginning as a programmer at S&S International, later known as Dr. Solomon’s Software, Cluley ascended to senior positions at renowned security firms like Sophos and McAfee.
Graham Cluley (X) profile
Notably, he edited the respected Naked Security site during his tenure at Sophos, serving as a reliable source of security news and analysis. Widely recognized for his contributions.
Cluley was named Twitter user of the year by Computer Weekly and inducted into the InfoSecurity Europe Hall of Fame. His blog and extensive public speaking engagements (his regular presence on TV and radio, where he explains computer security threats to a broader audience) further solidify his influence in the cybersecurity sphere, where he communicates complex threats in a comprehensible manner.
Will Dormann
Will Dormann is a one of the CTI experts renowned for his profound contributions to software vulnerability analysis. As a senior vulnerability analyst at Vul Labs, Dormann specializes in discovering and dissecting vulnerabilities across diverse products and platforms. Leveraging his extensive expertise, he has uncovered thousands of vulnerabilities, employing innovative tools and automation to streamline the vulnerability discovery process.
Will Dormann (X) profile
Dormann’s impact extends beyond mere discovery; his findings have shed light on critical security flaws exploited by attackers. Notably, his analysis at CERT/CC and Vul Labs has unearthed vulnerabilities with far-reaching implications, such as Windows’ mishandling of tainted Authenticode signatures. His research has heightened public awareness and prompted the development of mitigation strategies, emphasizing the importance of user vigilance and official patches.
Recognized for his 14-year tenure at CERT/CC, Dormann’s recent endeavors have delved into zero-day vulnerabilities and critical outlook vulnerabilities, including CVE-2023-23397 affecting Microsoft Outlook. His commitment to responsible disclosure underscores his dedication to cybersecurity integrity. Dormann’s work continues to shape the cybersecurity landscape, safeguarding users and organizations against emerging threats while advancing the field’s knowledge and resilience.
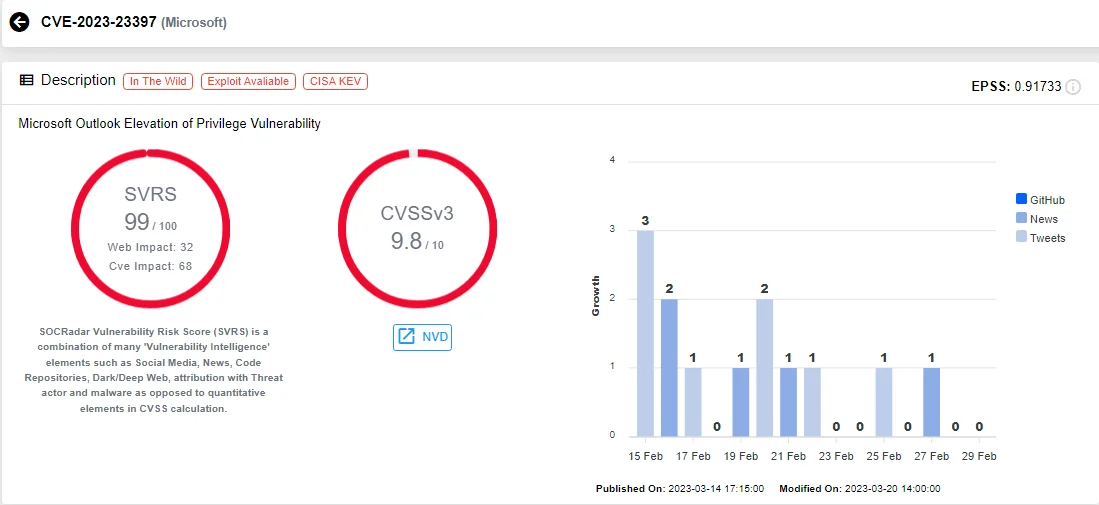
SOCRadar’s Vulnerability Intelligence card of CVE-2023-23397
Florian Roth
Florian Roth stands as a trailblazer in the realm of CTI experts and Detection Engineering, renowned for his expertise and innovative contributions to cybersecurity. Serving as the Chief Technology Officer at Nextron Systems GmbH, Roth has spearheaded the development of groundbreaking tools such as the APT Scanner THOR and the Valhalla Yara rule feed service. His collaboration with Thomas Patzke birthed the Sigma project, an acclaimed tool for threat hunting that detects generic malicious behavior.
Florian Roth GitHub repositories
Roth’s journey began as an offensive researcher at Siemens in Frankfurt before evolving into a prolific creator of open-source projects like yarGen, LOKI IOC Scanner, and FENRIR, all of which have left a significant impact on the cybersecurity community. His academic background spans Political Science, History, Arts, and Media, with research contributions at esteemed institutions like the University of Konstanz and ETH Zürich.
As an advocate for collaborative defense strategies, Roth emphasizes the pivotal role of detection engineering in cybersecurity, advocating for Detection-as-Code (DaC) and the integration of threat intelligence feeds into detection methodologies. His thought leadership extends to publications and platforms like his blog and LinkedIn, where he shares insights on practical threat intelligence and data-driven threat hunting.
SOCRadar’s Threat Feed/IoC module empowers your security operations with a rich repository of Indicators of Compromise (IoCs) sourced from diverse threat intelligence feeds. Seamlessly integrate IoCs into your security infrastructure to fortify defenses against known threats and enhance threat detection capabilities across your network.
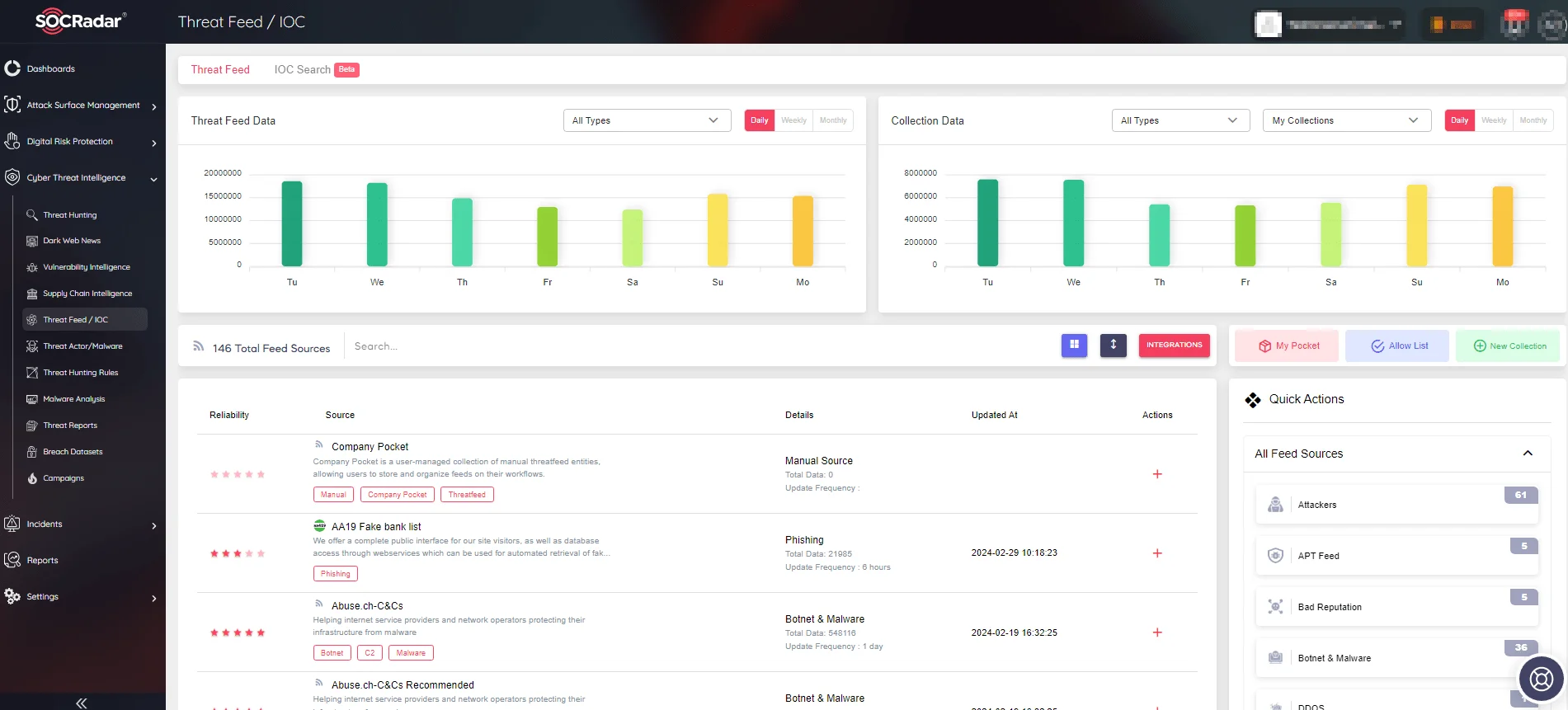
SOCRadar’s Threat Feed/IoC
With SOCRadar’s advanced Threat Hunting module, users can explore billions of records to search for Indicators of Compromise (IoCs) and access pertinent attribution data.
The module not only supports manual searches during incident response activities but also offers automated features for streamlined threat detection and response processes, enabling organizations to stay ahead of emerging threats, identify vulnerabilities, and bolster their overall cybersecurity defenses.
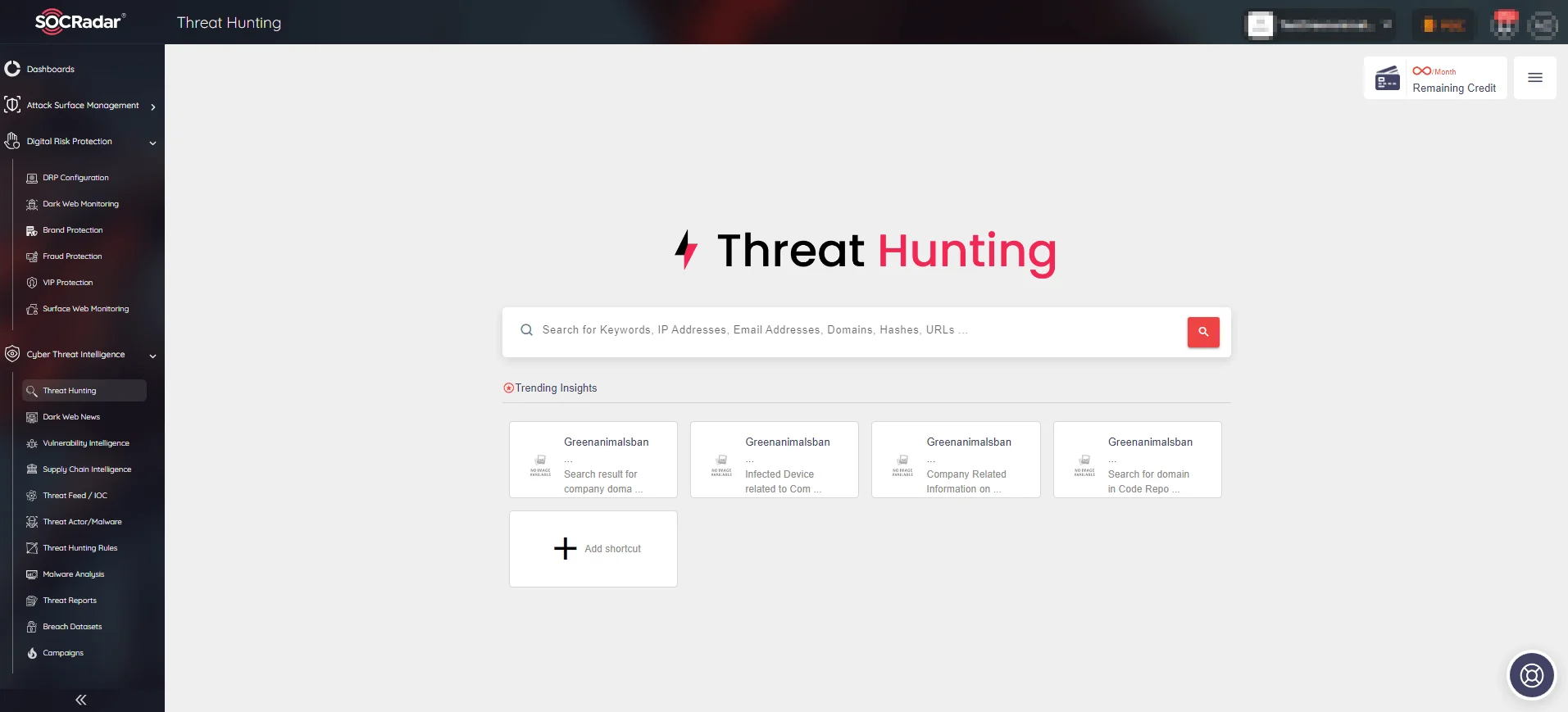
SOCRadar’s Threat Hunting
Troy Hunt
Troy Hunt is a renowned security expert, recognized as a Microsoft Regional Director and Microsoft Most Valued Professional.
Troy Hunt (X) profile
He is widely known for his significant contributions to cybersecurity and for creating “Have I Been Pwned?” (HIBP), a widely-used platform that helps individuals determine if their personal data has been compromised in data breaches. Hunt’s expertise extends across various domains within the cybersecurity landscape, and he is respected for his insights and advocacy for better security practices.
HIBP main page
For regular updates and insights into the cybersecurity field, individuals can visit his website, troyhunt.com, where he shares weekly updates, analysis, and commentary on significant cybersecurity events, trends, and developments. His platform is a valuable resource for professionals and enthusiasts seeking to stay informed about the latest happenings in the cybersecurity world.
Check SOCRadar Labs service Account Breach Check. It will discover if your accounts have been exposed to data breaches and determine if any crucial information associated with your accounts has been compromised. Don’t wait to safeguard your digital identity—take proactive steps to secure your online presence.
SOCRadar Labs’ Account Breach Check
Bonus: Brian Krebs
Even though he identifies himself as an “investigative journalist,” Brian Krebs has provided invaluable contributions to the field of cybersecurity. Renowned for his relentless pursuit of truth amidst the shadowy world of cybercrime, his journey into the domain of digital threats was sparked by a personal encounter with Chinese hackers in 2001. This encounter ignited a passion that would shape his illustrious career.
Brian Krebs (X) profile
Krebs’ investigative prowess blossomed during his tenure at The Washington Post, where he delved into internet security, cybercrime, and technology policy, solidifying his reputation as a leading authority in the field.
Pioneering cybercrime reporting became Krebs’s forte, as he broke the news on major data breaches like those at Target, Home Depot, and Neiman Marcus. His groundbreaking coverage of the malware, later known as Stuxnet, set a new standard for investigative journalism in the cybersecurity realm. He also has a daily blog that become a staple for those seeking comprehensive insights into the latest hacks and breaches.
Krebs’s influence extends beyond journalism, as evidenced by his award-winning book “Spam Nation,” which offers a riveting journey into the world of organized cybercrime. Despite facing relentless attacks from cybercriminals, including massive DDoS assaults, Krebs remains undeterred, continuing to provide invaluable contributions to the fight against digital threats. His unwavering dedication and unmatched insights make Brian Krebs an indispensable luminary in the ongoing battle for cybersecurity.




































