The Ultimate OSINT Handbook on Personal Information
OSINT is a term that refers to the process of gathering information from publically accessible sources. These sources include but are not limited to newspapers, television, blogs, tweets, social media, photos, podcasts, and videos that are publicly available, free, and legal.
OSINT is not restricted to the sphere of cybersecurity. However, corporate, military intelligence, sales, marketing, and product management use OSINT tactics to increase productivity while providing public services.
This article will discuss utilizing open-source intelligence (OSINT) to find and acquire a person’s virtual footprint and personal data. Thus, OSINT is the simplest method for gathering information from publically accessible resources.
OSINT Username Search
Assume we know a target’s login and are tasked with gathering as much information as possible from publically accessible sources. The flowchart below illustrates how you may retrieve data associated with a single username.
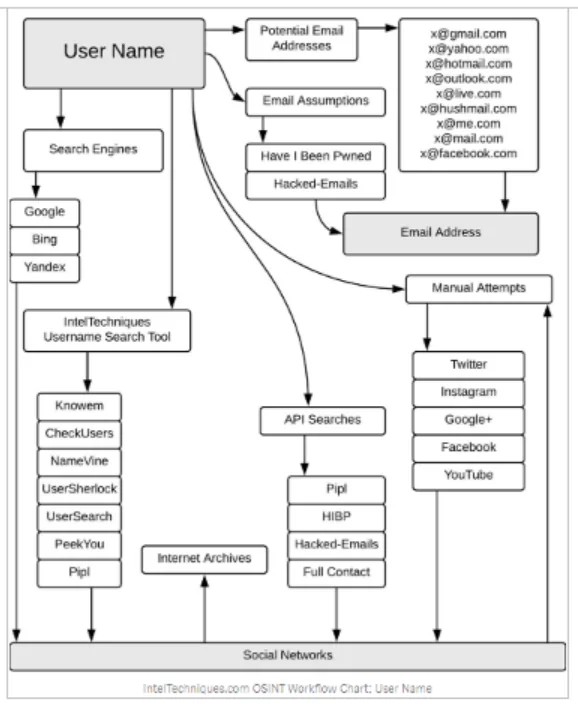
You may acquire the target’s email address from its username since usernames are often generated from email addresses. If that is not the case, you may use an assumed address and search Have I been pwned, a website that enables you to search across numerous data breaches to determine whether your email address has been hacked.
Various username search tools will direct you to the user’s social network account.
Which are:
- CheckUsernames – Social Media Username Search by KnowEm
- KnowEm Username Search: Social Media, Domains and Trademarks
- namecheckr | Social and Domain Name Availability Search For Brand Professionals
- Username Search | Find People by Username at PeekYou
- Username Search | Search Dating Sites | Find User Profiles (usersearch.org)
- SearchPOF.com – Search POF by Username
- Instant Username Search
Additionally, social networks reveal personal information such as your valid name, home address, age, gender, interests, and check-ins. That implies that accessing the social media account is the last red signal since it discloses personal information.
Also, you may make manual efforts on social networks to get the username’s email address and other personally-identifying information.
While Google is an excellent location to begin a search, it may be pretty ineffective for locating email addresses. The primary reason for this is that Google cannot access the locations where individuals enter their email addresses (for example, account login sites). Nonetheless, there are a few effective methods for locating email addresses that Google has indexed.
- Only precise matches are returned when quote marks are used. Searching for “[email protected]” instead of simply [email protected] is more exact.
- The intext search modifier may be used to locate websites with the email address as a string. This is especially useful when used in conjunction with the site:modifier to search the firm’s website with whom your target is affiliated. For instance, site:targetcompanyintext:[email protected] is far more likely to succeed than a random search. You might also use the following search phrase to discover several email addresses related to your target’s organization.
- Another compelling strategy is to use the filetype:search operator to determine the location of your target’s email address. This may be used to discover the email address buried inside a PDF or other file format. This may expose business records, invoices, meeting minutes, sports club schedules, or any other paper. For instance, consider the following search:
intext:”[email protected]” filetype:pdf
The query Will search for PDFs that include John Doe’s email address.
It’s beneficial when looking for emails associated with organizations that make many papers accessible online, such as government agencies or colleges.
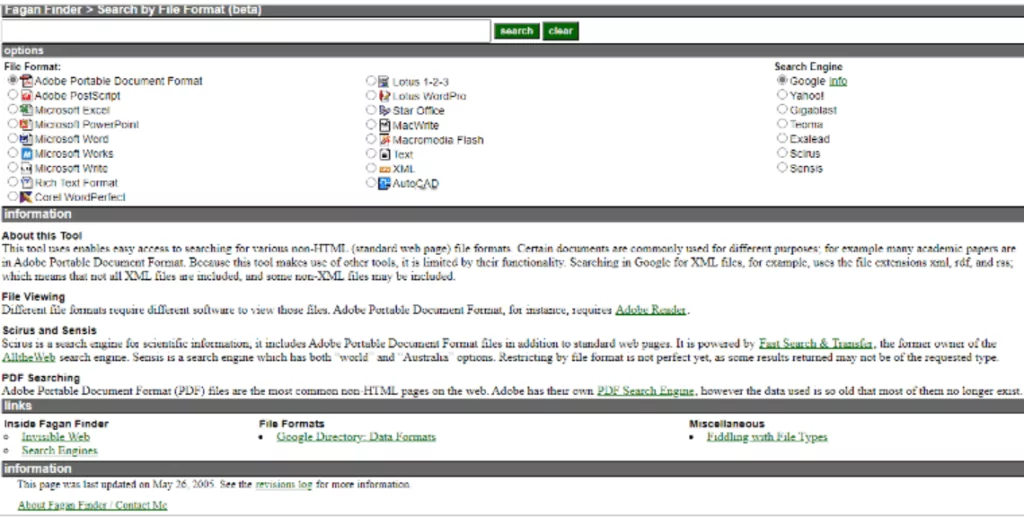
At this point, it’s also worth considering FaganFinder. It operates similarly to Google’s filetype: search but combines several file types with various search engines.
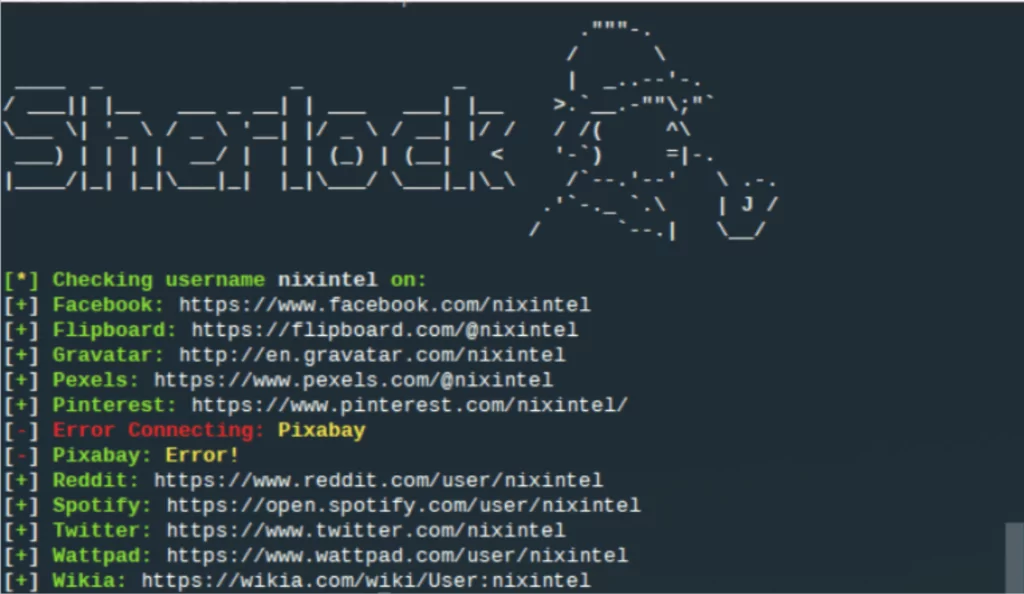
Apart from online services, you may utilize WhatsMyName, Sherlock, and Maigret, which have the unifying data necessary to execute user enumeration across several websites. Keep in mind that when doing searches across many sites, you may get false positives due to the possibility of someone else using the same login; be prepared for this.
OSINT Email Address Search
Assume we have my target’s email address; the flowchart below illustrates how I might utilize that one piece of information to disclose the target’s personal information.
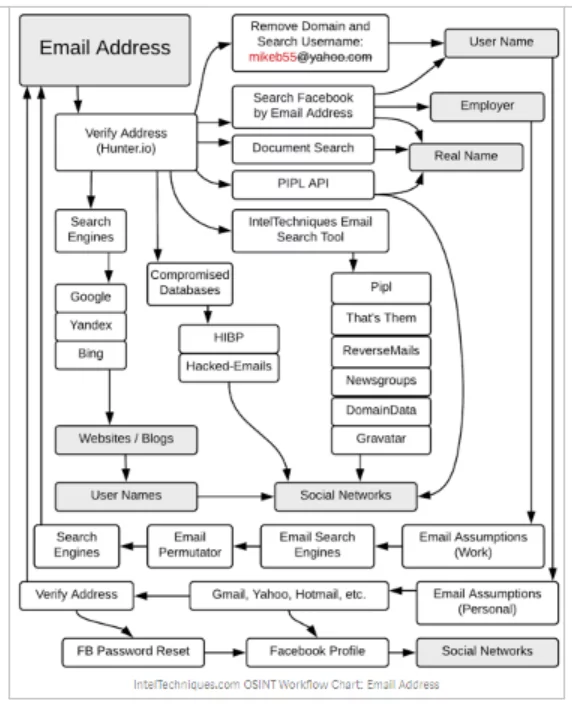
The first step is to validate your email address. There are many internet tools accessible for this purpose, which are detailed below:
1- Hunter
It allows you to locate email addresses quickly. To begin the search, just input a domain name. The Domain Search returns a list of employees in a company, including their names and email addresses, as discovered on the web.
2- Proofy
Proofy is a robust email validation solution that enables mass email validation with a rate of more than 96% accuracy. Using this program, you may validate emails in bulk, which includes email deduplication, syntax checking, MX Records verification, and other validations.
3- Email Permutator
When you input the name and domain of a person you’re looking for, this program will create many legitimate email addresses.
4- OSINT Browser Extensions
Numerous essential connections are included in browser extensions, including email search and verification. They work with both Firefox and Chrome. Some of them are:
- Sales automation & acceleration at scale | Snov.io
- Email Extractor – Chrome Web Store (google.com)
- Email Extractor — Collect Email Addresses Easily Description | AtomPark Software
- Free Email Extractor Software Download (emailextractorpro.com)
- Email Grabber – Features
After validating the email address, you may now delete the domain to get the login and access the social media account. You may also directly search for that email address on a social networking site, such as Facebook, which will reveal the job, perhaps a real name, or other pertinent information.
By looking for that address in search engines, you may be able to access the bloggers’ websites, from which you may get their usernames or social network account.
5- Paste Sites
Pastes provide a wealth of OSINT data. They include information on data breaches, public records, chatroom logs, and other relevant information, including email addresses. Pastebin is by far the most popular and has its search engine.
6- Emailrep.io
Emailrep.io is an excellent site for determining the age of an email account if it has been related to phishing, and with which other social media accounts it is known to be affiliated. This is advantageous for those tasked with combating phishing and spammers, but it is also helpful as an OSINT tool.
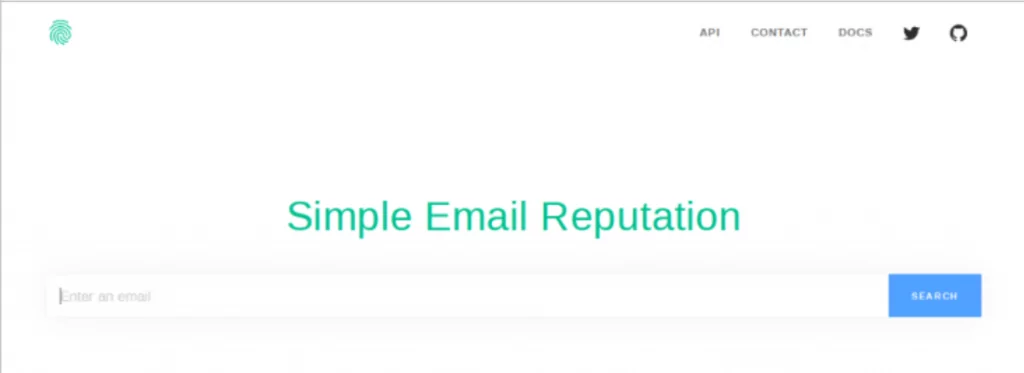
7- Epieos
Epieos, the ultimate OSINT tool, is a tool that locates user accounts without telling the user. When you input an email address and complete the captcha, you will obtain a list of places where that email address has been used online. The searched email has accounts on Twitter, Spotify, Nike, Google, Eventbrite, and Amazon. As an OSINT analyst, I should investigate if the profiles on these sites can be accessed using a search engine or by directly visiting the site.
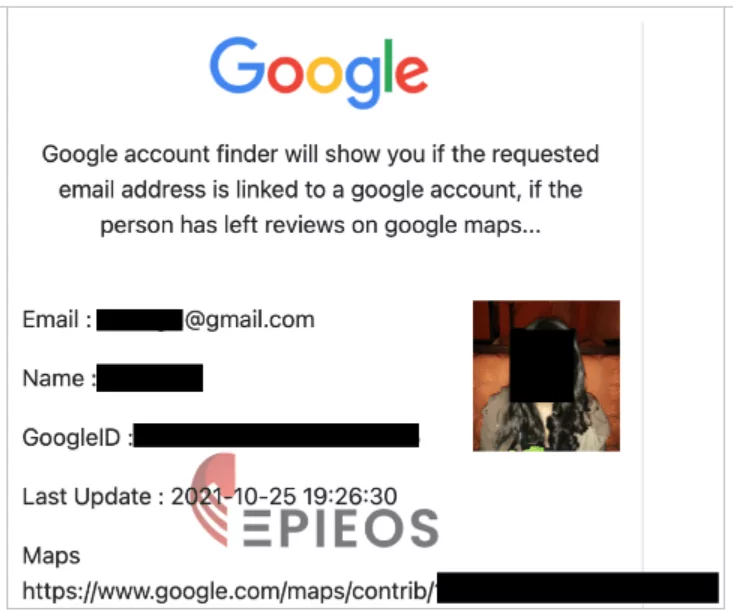

8- Skype
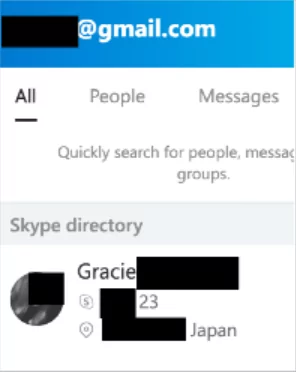
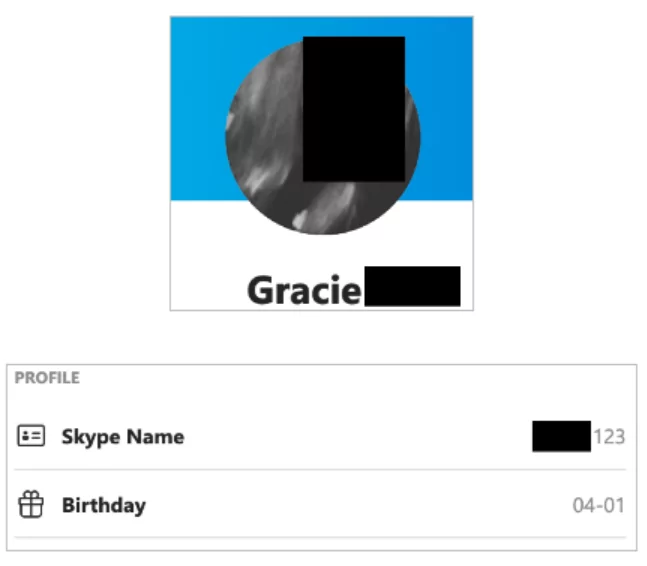
Skype search is available via the Skype App and enables you to look for not just email addresses but also names, usernames, and phone numbers to see if they are related to a Skype profile. As seen in the example below, we search for an email and discover a connected profile.
9- LinkedIn
LinkedIn is loaded with potential for OSINT, including email research. LinkedIn enables you to modify a URL to determine if a profile is associated with a certain email address. The following is the URL:
https://www.linkedin.com/sales/gmail/profile/viewByEmail/[email protected]
It will be shown if the email is related to a LinkedIn profile.
10- Whoxy
https://www.whoxy.com/ is a website that is associated with a variety of WHOIS-related queries. It’s worth noting that reverse WHOIS may also reveal historical information that is not always accurate, so it’s critical to double-check your results. In the example below, pick “email address” from the dropdown menu, input an email address, and click search. The results page includes a hyperlink to the website linked with that email address. This is the section where you would research this website and anybody linked with it.
OSINT Phone Number Search
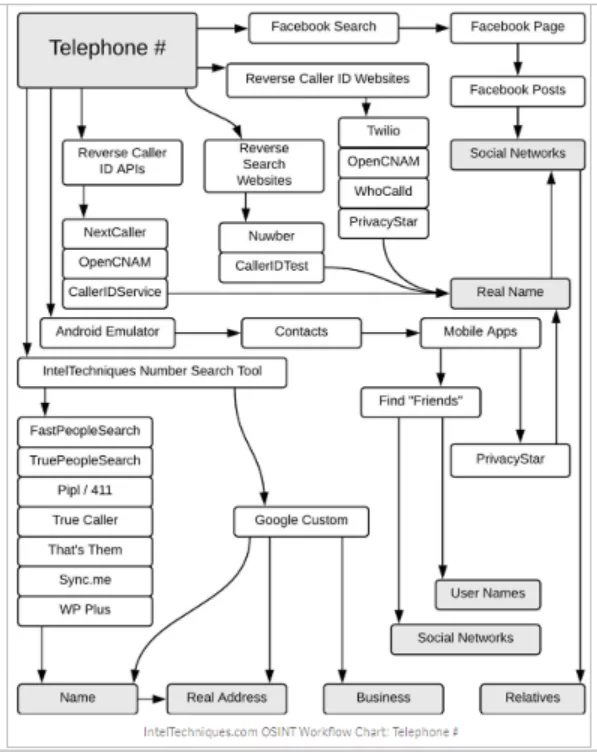
Users of social networking platforms, such as Facebook, often make the error of linking their phone numbers to their Facebook pages. Even on Facebook, if the privacy setting is modest, personal numbers may be discovered.
Apart from that, user-supplied phone number databases such as truecaller.com or whocalledme.com that gather millions of records via the sale of their services might be utilized to get the results.
PhoneInfoga is a well-known utility for scanning phone numbers using just publicly available data. The primary emphasis is on accurately acquiring relevant information such as country, region, carrier, and line type for international phone numbers. It then attempts to locate the VoIP provider or search for the owner’s traces on search engines. It saves time by checking many numbers simultaneously and conducts OSINT espionage via external APIs, Google Hacking, phone books, and search engines.
OSINT People Search Engines
Some websites specialize in doing extended personal searches using a genuine name, username, email address, or phone number all in one.
- https://www.spokeo.com
- https://thatsthem.com
- https://familytreenow.com
- https://pipl.com
- http://www.yasni.com
- https://www.beenverified.com
- https://www.fastpeoplesearch.com
- https://www.truepeoplesearch.com
- https://www.familytreenow.com
- https://people.yandex.ru
While some people search websites to enable users to opt-out, other search services containing their information arise once they do. This is because the same dataset is purchased and utilized by several services. Certain corporations possess specific databases, and even if a user deletes a listing on one of their websites, the old data is repopulated on the new domain. The previously deleted profile returns in the search. As a result, assuming individuals were somewhat diligent about cleaning up their act, you only had to wait for a new database to materialize. One approach to determining who has opted out is to visit the person’s search site, locate a unique paragraph, do a quoted Google search on it, and discover all of the domains owned by the organization. Possibly, the information your target took from site A has been replicated on site B.
OSINT Searches on Compromised Databases
Data breaches have become a significant concern, and we’ve lately seen an increase in data dumps. Troy Hunt gathered leaked data, removed passwords, associated emails with the breach in which they were implicated, and published it to haveibeenpwned.com. While the breach itself may not be significant, what is essential is that the email may include a list of services the individual uses or has used.
Another possibility is to use dehashed.com. A free account functions similarly to Troy Hunt’s website; however, with an active subscription, it displays passwords in plain text or hashed form. From an OSINT standpoint, we need it to see if it was used on any other websites – another approach to determine which services the individual uses. Searching for a password or its hash reveals the website on which it was used and the email address associated with it. As a result, we can get emails from targets that we would not have obtained otherwise. It’s critical to remember that if the password is not unique, we may get false positives due to other individuals using it.