
5 Tips for Social Media Security
Social media is great but a lot of risks and threats have evolved with this social media frenzy. Financial fraud, blackmailing, phishing, invasion of privacy, and identity theft have become commonplace attacks targeted at individuals. On a more global level systemic human rights violations, illegal data collection and data mining, consumer profiling, and tracking have become a familiar tune. Thanks to all the data we are generating and sharing.
In today’s world, it’s easy to get caught up in the habit of oversharing on social media since it only takes a few clicks on the screen, but it can also be dangerous.
In the aftermath of the dangerous side of social media, threat actors sell corporate or personal information on the dark web forums. In order to avoid these scandals, we should take precautions before such events happen.
We listed 5 tips that you can perform in order to stay secure online.
1- Use unique, strong passwords for each social media account

There are rules in the various regulations in terms of creating a unique, strong password, since it’s pain to remember all the unique passwords for each social media account, there is an easier way to perform this precaution which is “password manager” software.
This software can help you create your password without writing anything and keep it encrypted in the memory until you enter your master key.
So using such software is the easiest way to keep yourself secure.
2- Use two-factor authentication
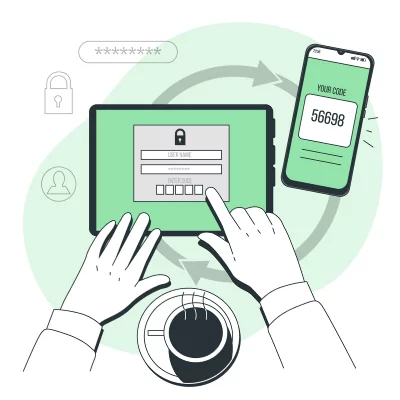
No matter how complex the password is; two-factor authentication also called two-step verification is recommended method in terms of keeping personal accounts safe. Because it takes only one phishing email or database exploit, and your password is out in the world.
Two-factor authentication, or 2FA, adds a second method of identification verification to secure your accounts. First, the thing you know, your password, then something unique that you have, like your phone or fingerprint.
By combining your password with one of these factors, attackers can’t access your account even if they have your password.
The most common 2FA systems use a unique one-time code with every log-in attempt. This code is tied to your account and generated by a token, smartphone, or sent to you by text message.
The more modern and most secure form of 2FA uses a mobile app to send an approval notification to your smartphone or smartwatch for the least hassle possible.
With 95% of breaches involving account takeover, two-factor authentication is the most effective method of prevention.
It’s time for everybody, businesses, governments, and you to take the easy and effective step of enabling two-factor authentication on all accounts.
3- Be cautious of sharing too much

As individuals, we collectively create and share more and more information every day. The increasing use of smartphones and tablets has intensified this trend. Your acts online may be categorized into two:
- Data that is left behind when you are using the internet; could be your IP address, your browser cookies, your e-mail username, or simply your browsing habits the other is called: Passive digital footprint.
- The other kind of digital footprint is called “active”: It’s the data you are willingly sharing and storing. It includes everything you’ve ever shared like copied or bought.
With all the information you provided an IT enthusiast can easily navigate to a website, drag a square around your house on Google Maps, and instantly have access to every tweet, photo, link, or post that has been shared from this house using the information contained in what you share, it is possible to profile you.
4- Lock your phone

Keeping your social media accounts is not the subject of the cyber world itself. Your phone could potentially end up in the hands of a stranger, giving access to your social media accounts and more. Once threat actors profile you, they can use the information you provide yourself against you and change your social media password through phishing attacks on your friends.
In order to reduce the possibility of an intruder, you have to enable the password lock on your phone and set it to time out no more than a few minutes
5- Invest in security products that keep social accounts secure

Let your business’s social media accounts be monitored by professional products.
SOCRadar would alert you about possible impersonating social media accounts and continuously monitor your digital corporate identity on both the surface web and deep web.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Get free access.


































