
Insider Threats: The Hidden Enemy of Cybersecurity
The human factor is one of the most challenging components of cybersecurity, and the topic where the human factor is most evident is insider threats. Insider attacks negatively impact an organization’s reputation, customer trust, and investor confidence by a strike from perceived as trustworthy and, therefore, a weak point.
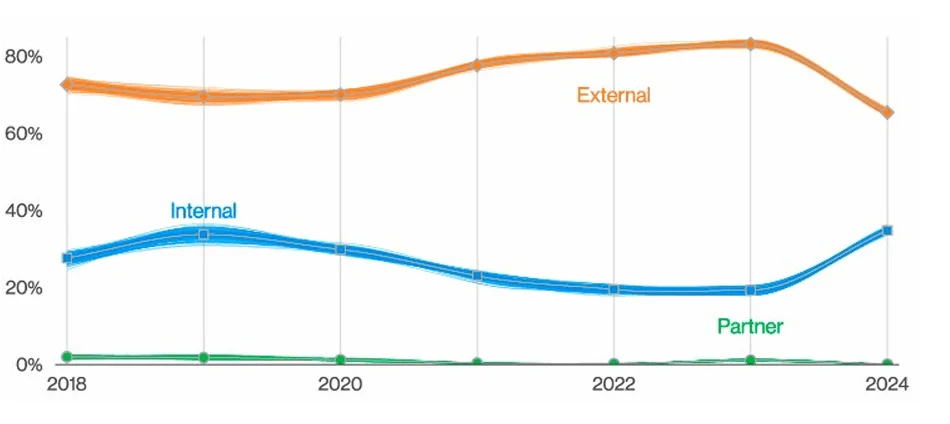
Breach factors (Source: Verizon DBIR 2024)
According to Verizon’s 2024 Data Breach Investigation Report (DBIR), insider threats now account for 35% of breaches, up from 20% previously. However, it is worth noting that 73% of these internal breaches were classified as Miscellaneous Errors, indicating unintentional incidents rather than malicious intent. These errors are frequently preventable and have been brought to light as a result of mandatory breach disclosure regulations, emphasizing the importance of organizations improving internal processes to reduce such risks.
Although insider threats appear to be less common than external threats, they are becoming increasingly complex. Organizations must continue to focus on this critical area, as human error and internal actors account for nearly one-third of all breaches.
Surprisingly, 68% of all breaches were caused by humans. This category, which excludes malicious insider activity, emphasizes the vulnerability caused by human actions such as errors or misconfigurations.
What Are Insider Threats in Cybersecurity?
An insider is a person who has or knows the structure and/or authorized access to an organization’s resources, including personnel, facilities, information, equipment, networks, and systems. So, current and former employees, contractors, and business partners are all insiders that could pose a threat.
The Cybersecurity and Infrastructure Security Agency (CISA) identifies insider threat as the risk that an insider will use their authorized access to harm the department’s resources, personnel, facilities, information, equipment, networks, or systems, whether on purpose or accidentally.
So, an insider threat is the insider’s potential to jeopardize the confidentiality, integrity, and availability of any sensitive data belonging to the organization. Insider threats may appear in different forms, including violence, espionage, sabotage, theft, and cybercrime.
Categories of Insider Threats
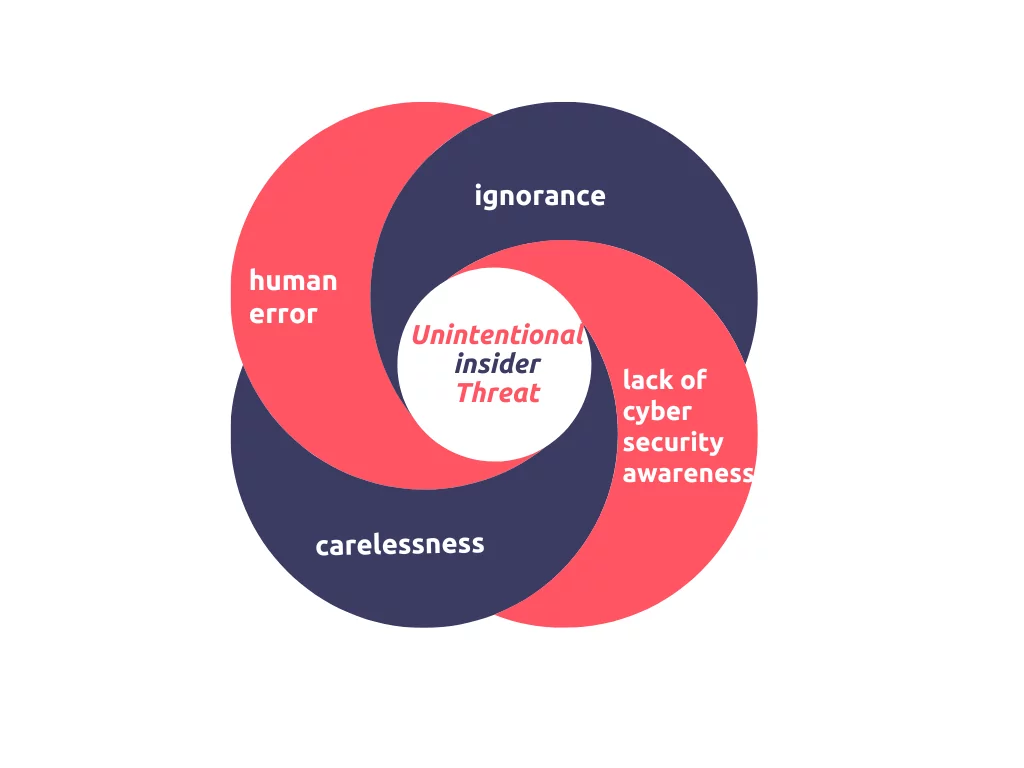
- Unintentional insider threat: Rather than resulting from malicious purposes, unintentional insider threats are typically the product of carelessness, ignorance, lack of cybersecurity awareness, or human error. Anyone can be an unintentional insider if they lose a device, use weak passwords, accidentally reveal sensitive information, fail to secure an endpoint or become subject to a social engineering attack.
2. Malicious insider threat: A malicious insider threat occurs when an authorized user intentionally causes damage to an organization. Malicious insiders may purposely install malware to disrupt system operations or share, sell, modify, or delete private/confidential data.
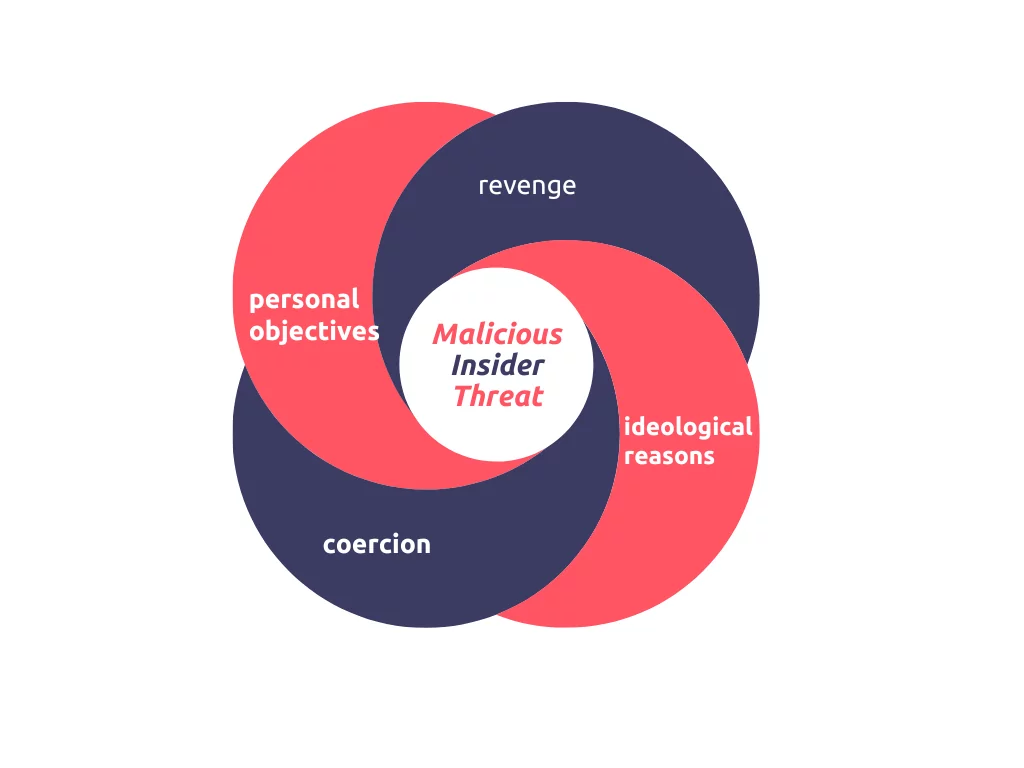
Malicious insider threats are often motivated by personal objectives such as financial gain or career advancement, revenge or desire to harm the organization, ideological reasons such as political, religious, or social benefits, and coercion such as threat or blackmail to force malicious activity. When malicious insider threats are mentioned, one of the foremost examples is Edward Snowden, who leaked classified information from the NSA’s global surveillance programs in 2013. Snowden, a former NSA contractor, had been granted a security clearance and had access to sensitive information.
Understand the Threat Landscape
All organizations, regardless of industry or size, can potentially be victims of insider threats, and insider incidents are usually part of a larger cyberattack. These threats are particularly challenging to identify and prevent because they are typically created by insiders with access to sensitive data and systems.
The first step in dealing with insider threats is to understand the threat landscape. Organizations should be aware of the different types of insider threats and understand their motivation.
Once organizations understand the threat landscape, they should identify the key indicators of insider threats on the surface and the dark web.
Insider Threat Indicators
Unusual or suspicious activity on employee accounts: User sign-ins frequently follow everyday patterns. Any login that differs from the routine, accessing and uploading sensitive data or systems outside of regular business hours or from regions outside their usual locations, attempted access to non-relevant critical data, failed authentication logs, alerts on DLP or Network Anomaly security technologies are crucial indicators of insider threat.
Suspicious social media posts: Social media posts that mention planning to leak or steal company information may indicate disgruntled employees or threat actors who are prepared to target the organization.
Sensitive data offered on dark web marketplaces: If sensitive data belonging to an organization is stolen by an employee or accidentally exposed due to negligence or carelessness, it will likely be sold on the dark web. Therefore, detecting sensitive data being offered for sale on dark web marketplaces may indicate insider threats.
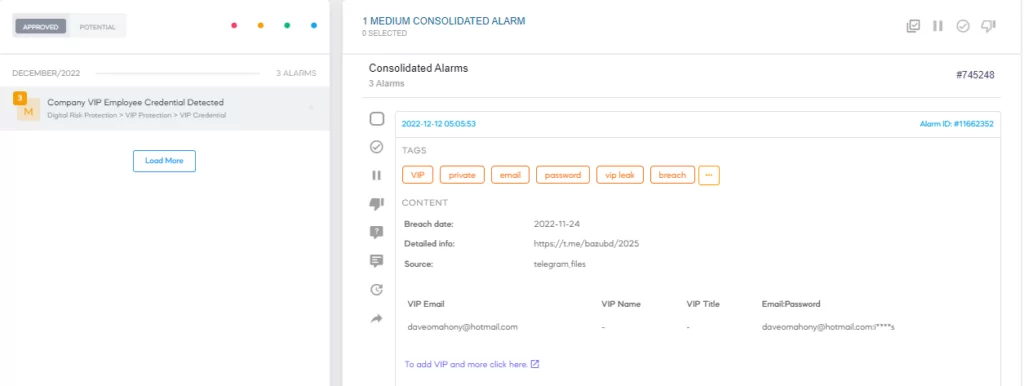
Company-related information on dark web forums: An underground forum that contains information accessible to particular individuals within a company is a serious sign that someone within the company may have leaked the information and/or someone has fallen victim to a cyber attack like phishing. In either case, the fact that company-related information appears on a dark web forum can be a strong indicator of insider threats.
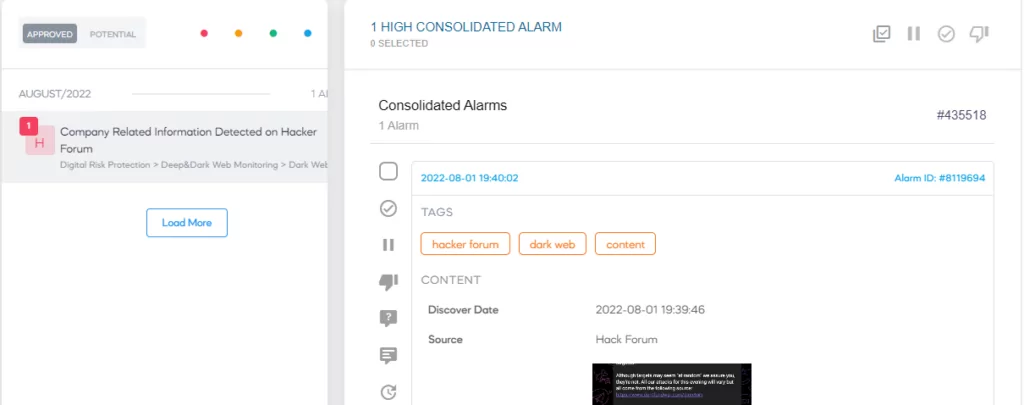
Insider Threats on the Dark Web
The dark web is often used to facilitate insider threats, with threat actors seeking insiders to exploit for monetary gain. Recruitment posts for insiders, particularly those with access to sensitive systems, are common on dark web forums. Criminals may offer rewards or leverage blackmail to coerce insiders into cooperating with their schemes.
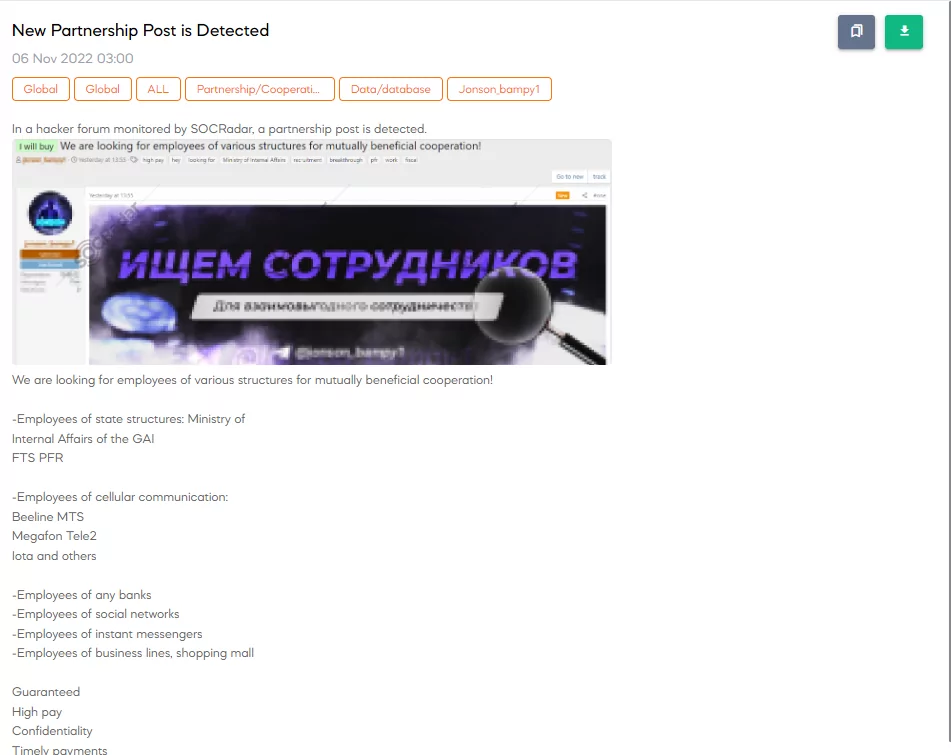
Example of a recruitment post
SOCRadar’s Dark Web Monitoring provides organizations with real-time insights into these underground forums, enabling early detection of insider-related activities before they escalate into full-blown security incidents.
Impact of Remote Work on Insider Threats
According to the 2024 Insider Threat Report [Gurucul], the widespread use of remote work has had a significant impact on the insider threat landscape. 39% of organizations blame the increase in insider attacks on the complexity of IT environments, which is fueled in large part by employees accessing networks from home. This shift broadened the attack surface, giving malicious or careless insiders more opportunities to exploit vulnerabilities. The use of personal devices and inconsistent security measures in home environments exacerbates these risks, making it difficult for organizations to effectively monitor and control access
![Main causes of the increase of insider threats (2024 Insider Threat Report [Gurucul])](https://socradar.io/wp-content/uploads/2023/04/2024-10-07-10_42_12-2024-Insider-Threat-Report-Gurucul.pdf-min.png.webp)
Main causes of the increase of insider threats (2024 Insider Threat Report [Gurucul])
Furthermore, 32% of respondents identify a lack of employee training and awareness as a major contributor to insider threats, which has become more prevalent in remote work environments. Physical separation from company resources and colleagues reduces oversight, making risky behaviors more likely to go unnoticed. To combat the increasing insider threat in remote work environments, organizations must prioritize strengthening security policies, improving employee training, and implementing continuous monitoring.
The Meta vs. Khurana Case: An Example of Insider Threats in Action
In March 2024, Meta filed a lawsuit against Dipinder Singh Khurana, its former vice president of infrastructure, accusing him of stealing confidential documents before leaving for Omniva, a rising AI cloud computing startup. The case highlighted the potential harm caused by insider threats, with Meta alleging that Khurana stole sensitive employee data, supplier contracts, and business plans to accelerate Omniva’s growth.
According to Meta’s investigation, Khurana uploaded more than 100 internal documents, including confidential contracts and strategic plans, to an external Dropbox folder before leaving. This decision gave Omniva a competitive advantage, particularly during the hiring process, as Khurana allegedly used the information to recruit Meta’s top talent. As insider threats become more sophisticated, this case highlights the importance of monitoring privileged employees and implementing strict data access controls.
Conclusion
Insider threats are a complex and challenging issue in cybersecurity that can have severe consequences for an organization’s reputation, customer trust, and financial stability and may even lead to legal sanctions. While insider threats are not new, the increasing reliance on technology and the rise of remote work have made all types of insider threats, whether malicious or accidental, well-planned or opportunistic, more difficult to detect.
Therefore, organizations need to be aware of the different types of insider threats and understand their motivation. Also, organizations need to develop a comprehensive insider threat program that includes a combination of technical controls, policies and procedures, and employee training. In this context;
- Establishing the least privilege approach, which means giving employees access only to the resources they need to do their jobs,
- Training users for awareness of data security and reaching the level of knowledge to identify suspicious activities,
- Setting policies for topics such as email and personal device usage and encouraging them with deterrent sanctions,
- Using background checks, onboarding, and offboarding checklists that enable organizations to systematically manage their workforce and minimize the risk of issues such as fraud, data breaches, or legal liability,
- Using authentication protocols,
- Establishing protocols to ensure that suppliers and contractors are regularly reviewed for compliance with security policies and industry standards will help organizations against insider threats.
Additionally, by adopting a proactive approach like Extended Threat Intelligence solutions to insider threat management, organizations can detect and respond to potential threats before they can cause significant damage.
SOCRadar Extended Threat Intelligence can provide valuable insights into insider threat activity by monitoring 7/24 surface and dark web and enable organizations to stay ahead of potential threats.




































