
Top 10 Deep Web and Dark Web Forums
[Update] May 14, 2024: “Bonus: Daily Dark Web”
The dark web hosts a myriad of forums that operate beyond the reach of conventional internet users, serving as epicenters for cybercriminal activities. These forums are not just meeting places for hackers and threat actors; they are vibrant ecosystems where stolen data, hacking tools, and illicit services exchange hands in the shadows. From the depths of this hidden internet, we’ve distilled a list of the top ten dark web forums, each distinguished by its unique contribution to the cybercrime landscape.
Our exploration takes us through the digital alleyways of the internet’s underbelly, where forums like BreachForums and XSS offer a glimpse into the sophisticated world of cyber threats and data breaches. These platforms shrouded in anonymity, are where the boundaries of legality blur, challenging cybersecurity efforts worldwide. As we unveil these forums, we aim to provide insights into their operations, memberships, and the overarching impact they have on both the cyber and physical realms.
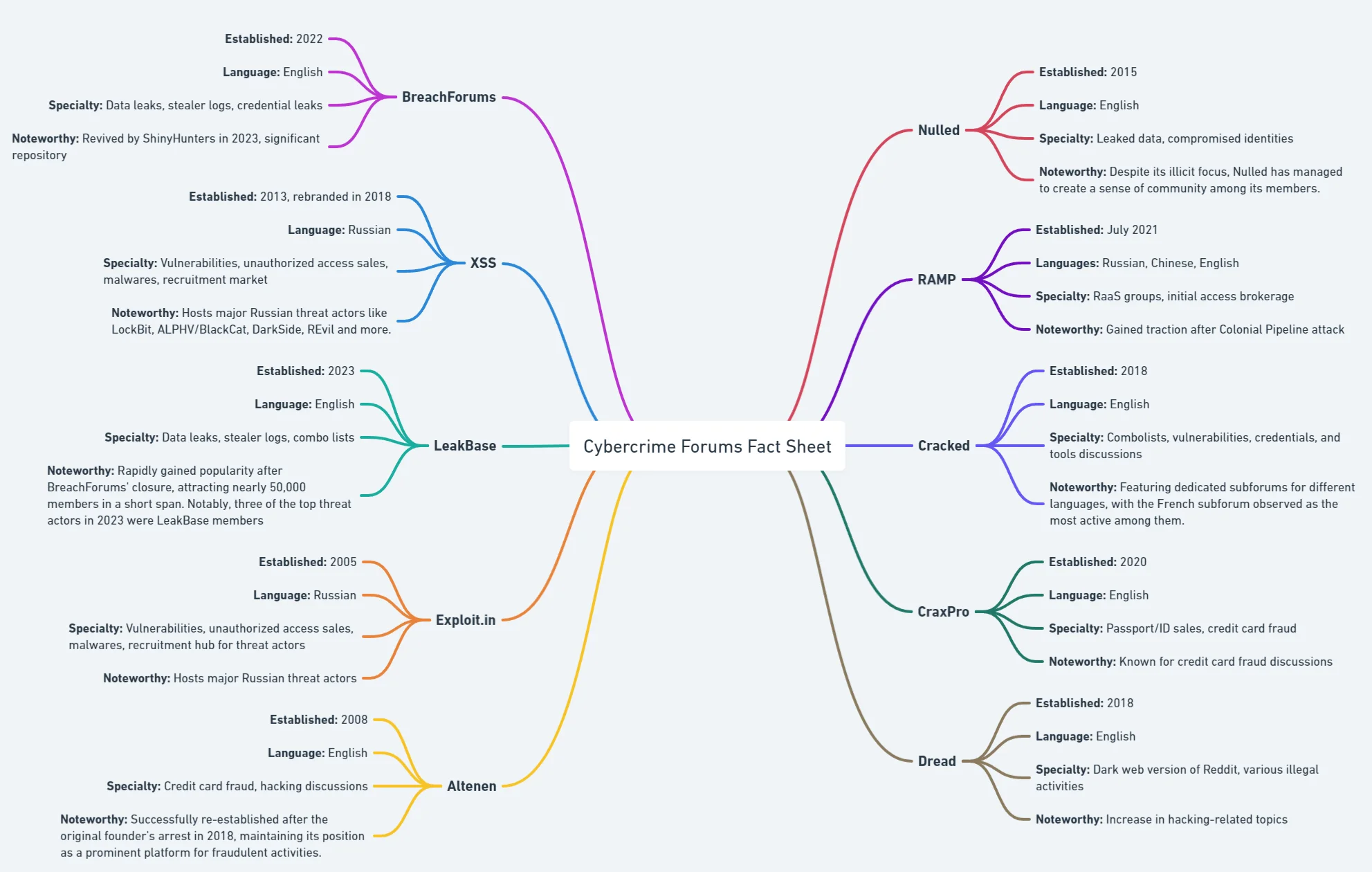
An overview of the cybercrime forums
1 – BreachForums
BreachForums quickly emerged as a hot topic among mainstream media discussions about dark web forums, especially after RaidForums was closed and BreachForums took its place. The story began when a known threat actor, Pompompurin, launched Breached after RaidForums’ demise.
This development resulted in Pompompurin’s arrest by US law enforcement on March 15, 2023, and the subsequent closure of Breached (also known as BreachForums) didn’t mark the end. Instead, a new team revived the forum under the BreachForums banner, swiftly becoming the dark web’s focal point and succeeding where previous forums had been silenced.
BreachForums’ home screen
On June 12, 2023, BreachForums returned under the banner of ShinyHunters, one of the most active threat groups. Despite initial skepticism over its legitimacy, with some fearing it was an FBI trap, a PGP-signed message from a former administrator, Baphomet, confirmed its return. ShinyHunters, notorious for significant alleged data breaches targeting companies like Tokopedia and Microsoft’s GitHub, has continued to draw attention for selling stolen data, underscoring ongoing cybersecurity and data protection challenges.
BreachForums stands out for its administrator-approved database category, boasting over 15 billion records from 936 datasets. The forum’s active sections, including Leaks, Stealer Logs, and its unique ranking system (VIP, MVP, GOD), alongside an in-forum transaction credit points system, mirror the operational model of its predecessor, Breached. The forum also implements an escrow system to secure transactions, a strategy that reportedly netted Pompompurin $1,000 daily.
The forum’s significance, however, lies in its membership, including the founders ShinyHunters and other high-profile threat actors. Threat actors such as CyberNiggers and USDoD, known for their claims of breaching major organizations, contribute to the forum’s notoriety and the broader implications for global cybersecurity.
2 – XSS
XSS, with a history stretching back to 2013, emerges not only as one of the oldest forums but also as a prominent hub for dangerous threat actors within the Russian-speaking cyber landscape. Established in 2013, the forum underwent a rebranding in 2018, adopting the name XSS in reference to the Cross-Site Scripting vulnerability following the arrest of one of its administrators in 2017. Operating as both a TOR and surface web-accessible platform, XSS serves as a bustling hacker forum where discussions revolve around unauthorized access sales, malware, security vulnerabilities, and database trading.
Main screen of XSS, featuring a BriansClub advertisement banner
Given its Russian-speaking user base and notorious reputation, XSS has hosted numerous prominent Russian threat actors, including LockBit, ALPHV/BlackCat, REvil, and the DarkSide threat group behind the Colonial Pipeline cyberattack. The forum serves as a meeting point for threat actors, facilitating recruitment announcements and various cyber threat exchanges. Ransomware-as-a-Service (RaaS) groups and other threat actors utilize XSS for PR purposes, engaging in discussions and promoting their activities to bolster their reputations.
Notably, underground markets for stolen credit cards, such as BidenCash and BriansClub, frequently advertise on this forum. According to comments from threat actors, XSS’s longevity and popularity are attributed to its offshore nature and the admin’s operational security (OPSEC) knowledge, which purportedly enhances forum-wide secrecy and privacy.
Navigating a Risky and Changing Environment Safely
Monitoring dark web forums critically underpins the establishment of a proactive defense against cybersecurity threats. This essential vigilance now spans traditional dark web forums, deep web repositories, Telegram channels, underground marketplaces, and ransomware group platforms. SOCRadar Threat Hunting empowers organizations to navigate and monitor these complex environments safely, avoiding direct exposure.
The service identifies potential threats through real-time tracking and sophisticated analysis across a wide range of illicit activities, including data breaches, exposures of Personally Identifiable Information (PII), financial fraud, and ransomware campaigns. Leveraging advanced search algorithms and customizable news feeds, SOCRadar delivers targeted insights into specific threats.
SOCRadar Cyber Threat Intelligence Module, Threat Hunting
3 – LeakBase
LeakBase emerges as one of the newest and most prominent hacker forums on this list. Estimated to have commenced operations in January 2023, this English-speaking forum accessible on the surface web quickly gained traction, especially following the closure of BreachForums in March 2023. It swiftly stepped in to fill the void in the ever-evolving cybercrime landscape, earning itself a notorious reputation.
LeakBase’s home screen
With a rank system reminiscent of BreachForums and its unique credit point system, LeakBase garnered attention, attracting nearly 50,000 members in a short span. The forum highlights discussions on data leaks, stealer logs, combo lists, vulnerabilities, malware, and even legal tools, each occupying a distinct category.
Its active community, particularly its members and predominantly its administrative team, fuels its prominence. In fact, according to Daily Dark Web, three of the top threat actors in 2023 were LeakBase members, with the founder of the Chucky forum securing the first position. Moreover, the forum features a dedicated private database section for exclusive content.
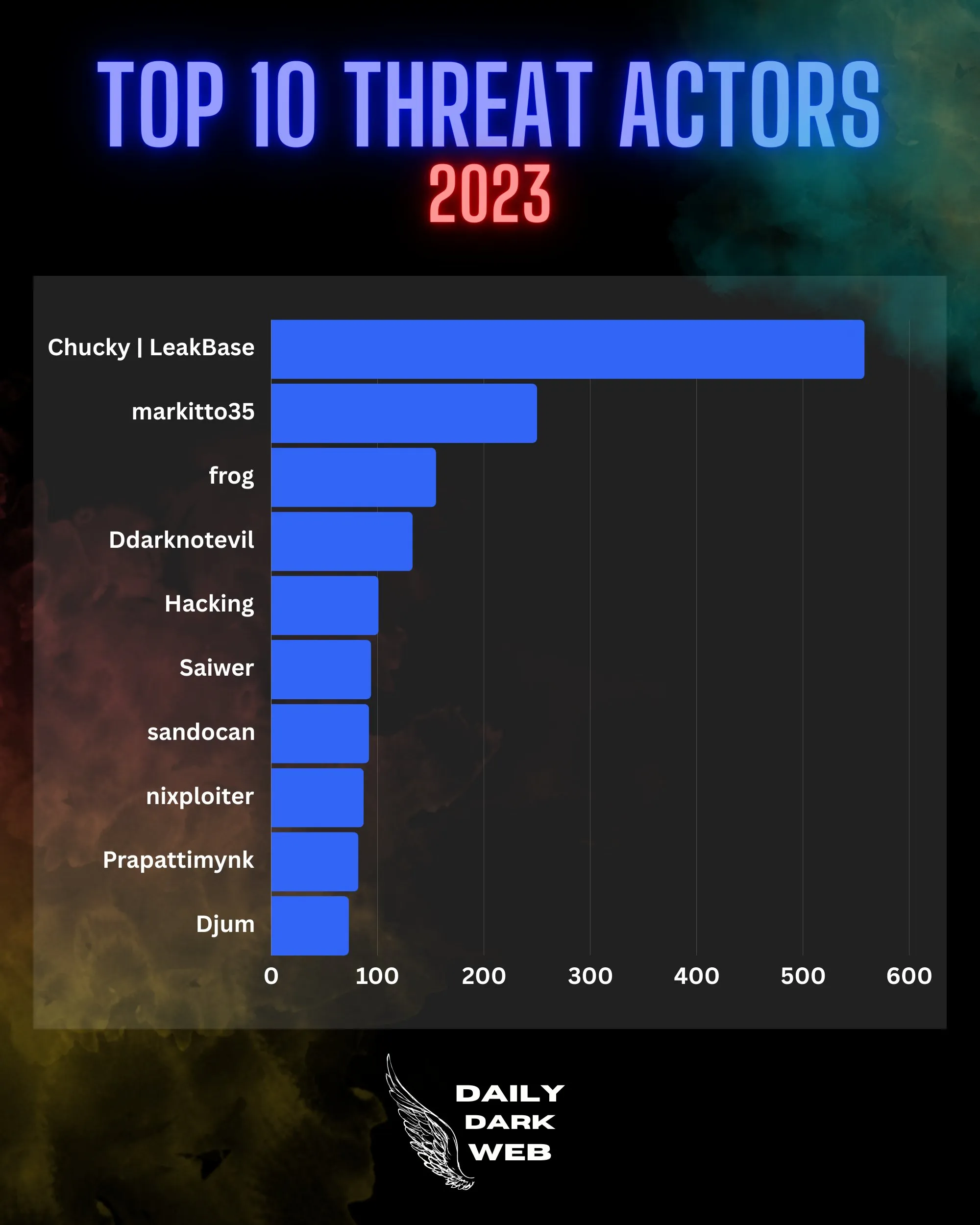
Top 10 Threat Actors in 2023 (Source: Daily Dark Web)
An underline is that it is forbidden to share data about Russia on Leakbase, which may give a little insight into the position of the administrators, or perhaps a deliberate effort to avoid attracting the attention of Russian threat actors. This stance sheds light on the forum’s nuanced approach to managing geopolitical sensitivities while navigating the complex landscape of cybercrime.
4 – Exploit.in
Established in 2005, Exploit stands as one of the leading Russian hacker forums in the cybercrime sphere, akin to XSS. Operating across TOR and the surface web, Exploit serves as a rendezvous point for initial access brokers, facilitating unauthorized access sales, malware dissemination, security vulnerabilities, and database transactions, either for sale or free distribution.
Main screen of Exploit
Much like XSS, Exploit plays a pivotal role in connecting career-oriented cybercriminals with potential collaborators for illicit ventures, such as hacking, fraud, or involvement in Ransomware-as-a-Service (RaaS) groups.
With its tightly structured organization and membership policies, Exploit projects an aura of professionalism. This stringent approach has propelled it into the spotlight of the cyber threat landscape, establishing itself as a forum where predominantly genuine content is shared. Non-Russian speakers and amateur threat actors find themselves marginalized within this forum’s community due to its exclusivity.
5 – Altenen
Altenen stands out among English-speaking hacker forums accessible on the surface web. Focused on a variety of fraudulent activities, notably credit card fraud, the forum delves into discussions on fraud techniques, cracking, hacking, IT topics, and much more.

Altenen’s home screen
Established in 2008, Altenen faced a setback when its founder was apprehended in May 2018, leading to the closure of the original forum. However, its successor continues to be actively used. To maintain its activity, Altenen mandates new members to share the forum’s domains on platforms such as X, Youtube, and other social media platforms to activate their memberships, ensuring the forum’s continued operation.
6- Nulled
Established in 2015, Nulled is a notorious English-language cybercriminal forum prevalent on the dark web. It hosts a variety of illicit content, including leaked data, compromised identities, credit card information, and tools for illegal activities. Despite its illegal focus, it markets itself as a community for sharing leaks and engaging in discussions.

Nulled’s main page
In 2016, Nulled faced infamy due to a major data breach exposing personal user information. Despite the risks, it maintains both public internet-facing and dark web forums, attracting users with varied access levels.
While not as prestigious as other forums like Breach and XSS, Nulled’s broad focus on illicit content ensures its continued relevance in the cybercriminal world.
7 – RAMP
Established in July 2021, RAMP (Russian Anonymous Market Place) stands out among dark web forums where Russian, Chinese, and English are spoken. The forum maintains stringent policies for membership, with one of the most crucial being the requirement of a good reputation on XSS and Exploit forums. RAMP surged in popularity by capitalizing on the aftermath of the Colonial Pipeline attack in the US, leveraging its effects on the dark web.
RAMP’s home page
Following the Colonial Pipeline attack, many hacker forums imposed restrictions on data related to ransomware groups. Serving as a vital point for Ransomware-as-a-Service (RaaS) groups, RAMP carved out a special place under its “partners program” for these groups to conduct activities such as recruiting new hackers or selling initial access. This could be one of the most significant distinctions between RAMP and other forums.
8 – Cracked
Subforums of Cracked
Cracked operates as a hacker forum active on the surface web. Conducted in English, discussions on combo lists, vulnerabilities, credentials, and tools are prevalent on this platform. The forum also features 12 dedicated subforums for different languages, with the French subforum observed to be the most active among them.
9 – CraxPro
Main screen of CraxPro
Established in 2020. Conducted in English, within its forum, discussions revolve around topics such as passport/ID sales, cookie, and credential sales, combo lists, SOCKS4 proxy sales, and credit card fraud. While the activity related to credit card fraud may sometimes surpass that of Altenen, threat actors suggest that the distributed credit card information is often inaccurate.
10 – Dread
Dread’s frontpage
Established in 2018 and conducted in English, Dread was founded by the threat actor known as HugBunter. Many liken this forum to the “Reddit of the dark web” due to its similar interface. While Dread is one of the largest forums on the dark web, we’ve chosen to place it last on the list. This decision stems from the fact that discussions on drug sales often overshadow hacking-related topics such as database sales, malware sales, and vulnerabilities. However, it’s worth noting that there has been an observed increase in discussions related to hacking topics on Dread at the time of writing this article.
Conclusion: The Critical Role of Dark Web Monitoring
In navigating the complexities and hidden dangers of the dark web, the significance of having a robust defense mechanism cannot be overstated. This is where Dark Web Radar emerges as a pivotal ally for businesses aiming to safeguard their digital frontiers against the ever-evolving threats lurking in the internet’s shadowy recesses. As we conclude our exploration of the top ten dark web forums, it’s clear that the insights and capabilities offered by Dark Web Radar could prove invaluable in extending an organization’s cybersecurity measures into these concealed territories.
The journey through the dark web’s most notorious forums underscores the vastness and complexity of the cybercriminal ecosystem. From forums specializing in data breaches to those facilitating illicit transactions, the dark web is a dynamic landscape of digital threats. However, with Dark Web Radar, organizations are not left in the dark. Instead, they are equipped with the tools necessary for proactive protection and resilience against these hidden dangers.
Dark Web Radar’s Monitoring capabilities act as a digital periscope, scanning the depths of the dark web to detect threats and exposures. This service not only tracks the unauthorized distribution of sensitive data but also keeps a vigilant eye on discussions and activities related to your organization among threat actors. By enabling real-time alerts and providing a comprehensive overview of potential risks, Dark Web Monitoring ensures that businesses can act swiftly to mitigate threats, safeguarding their data and reputation.
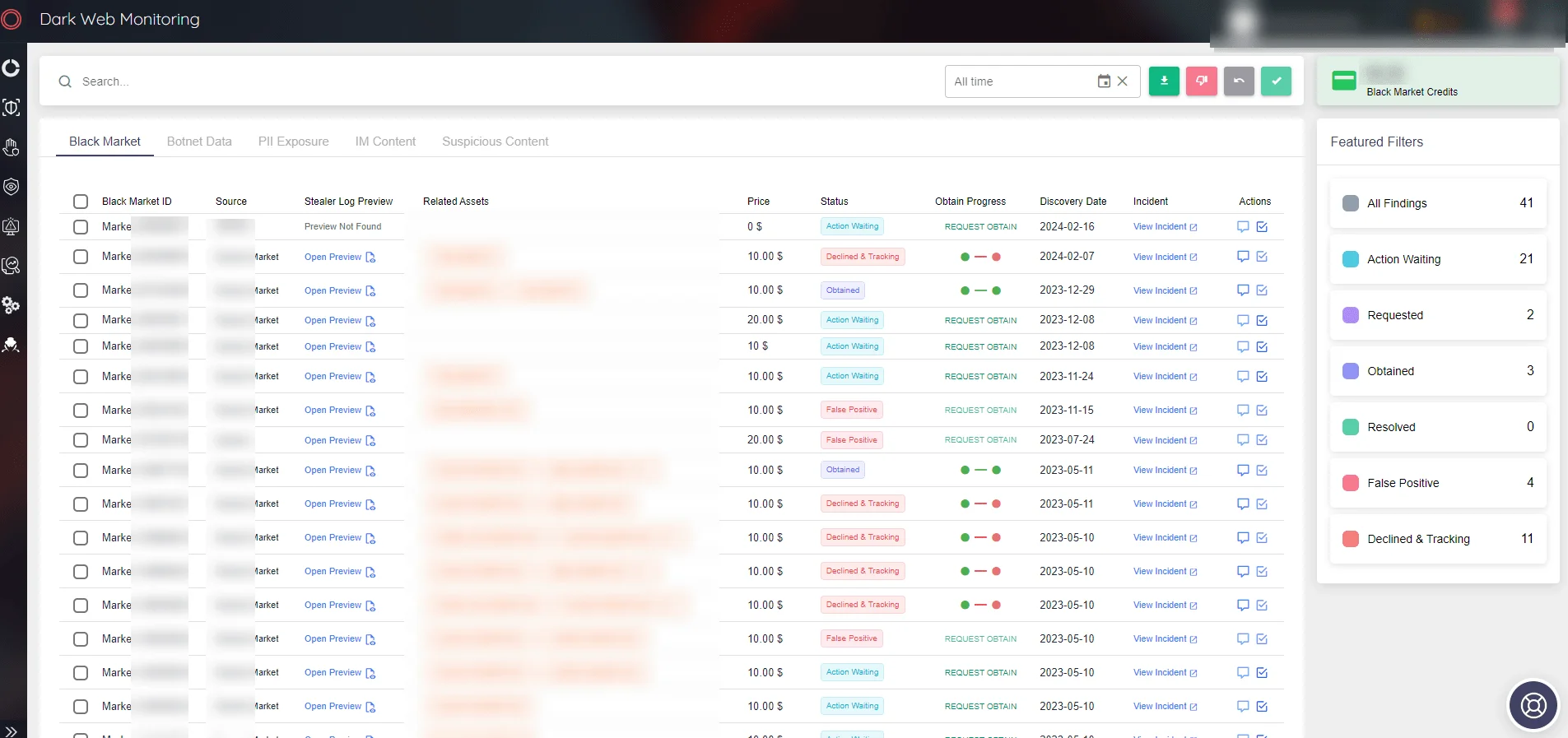
SOCRadar Dark Web Monitoring
The dark web is a hotbed for financial crimes, making Fraud Protection an indispensable feature of Dark Web Radar. By offering VIP Protection and real-time tracking of stolen credit card information, this service empowers organizations to defend against unauthorized transactions and financial exposures effectively. With Fraud Protection, businesses gain a critical advantage in preserving their financial integrity and protecting their executives from targeted cybercriminal activities.
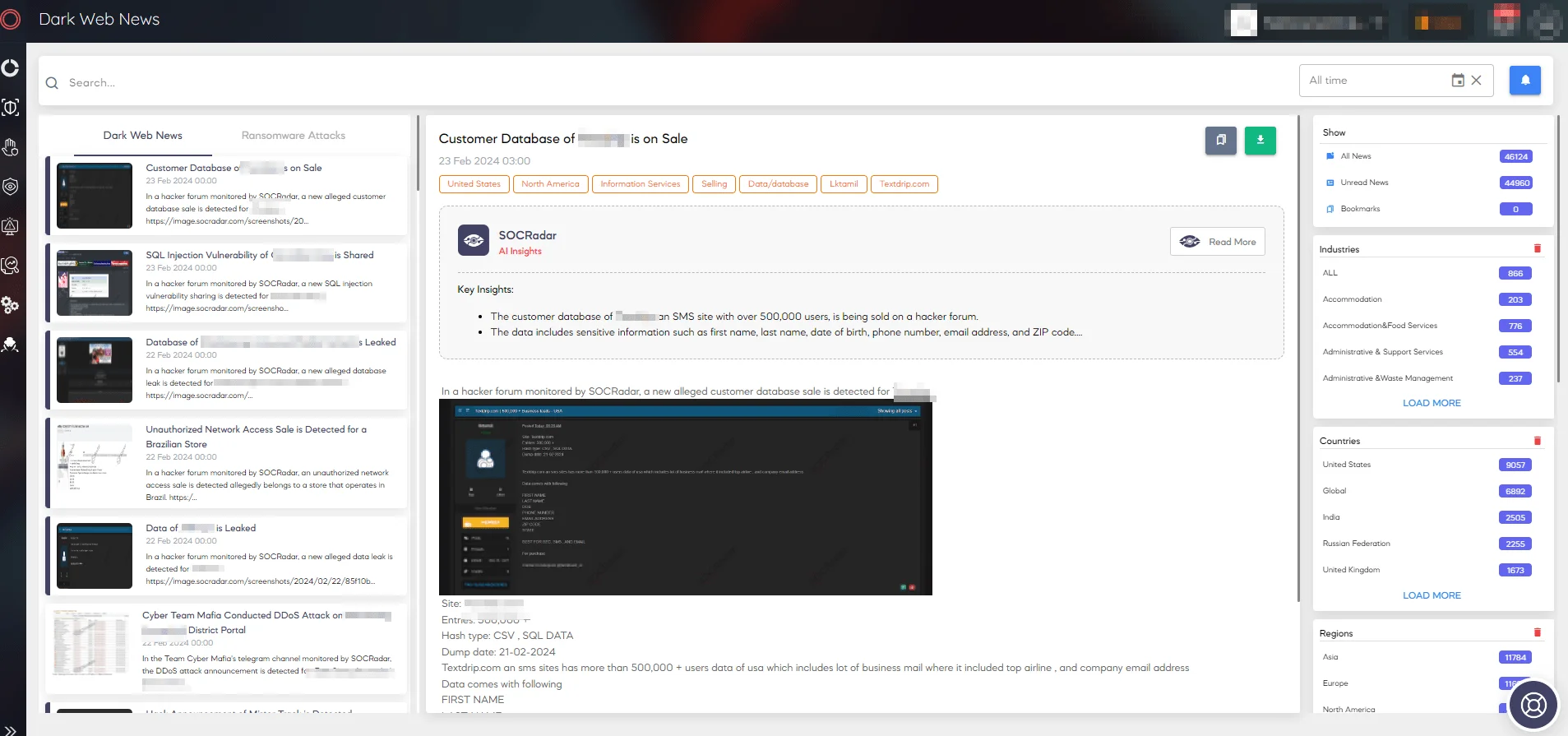
SOCRadar Dark Web News
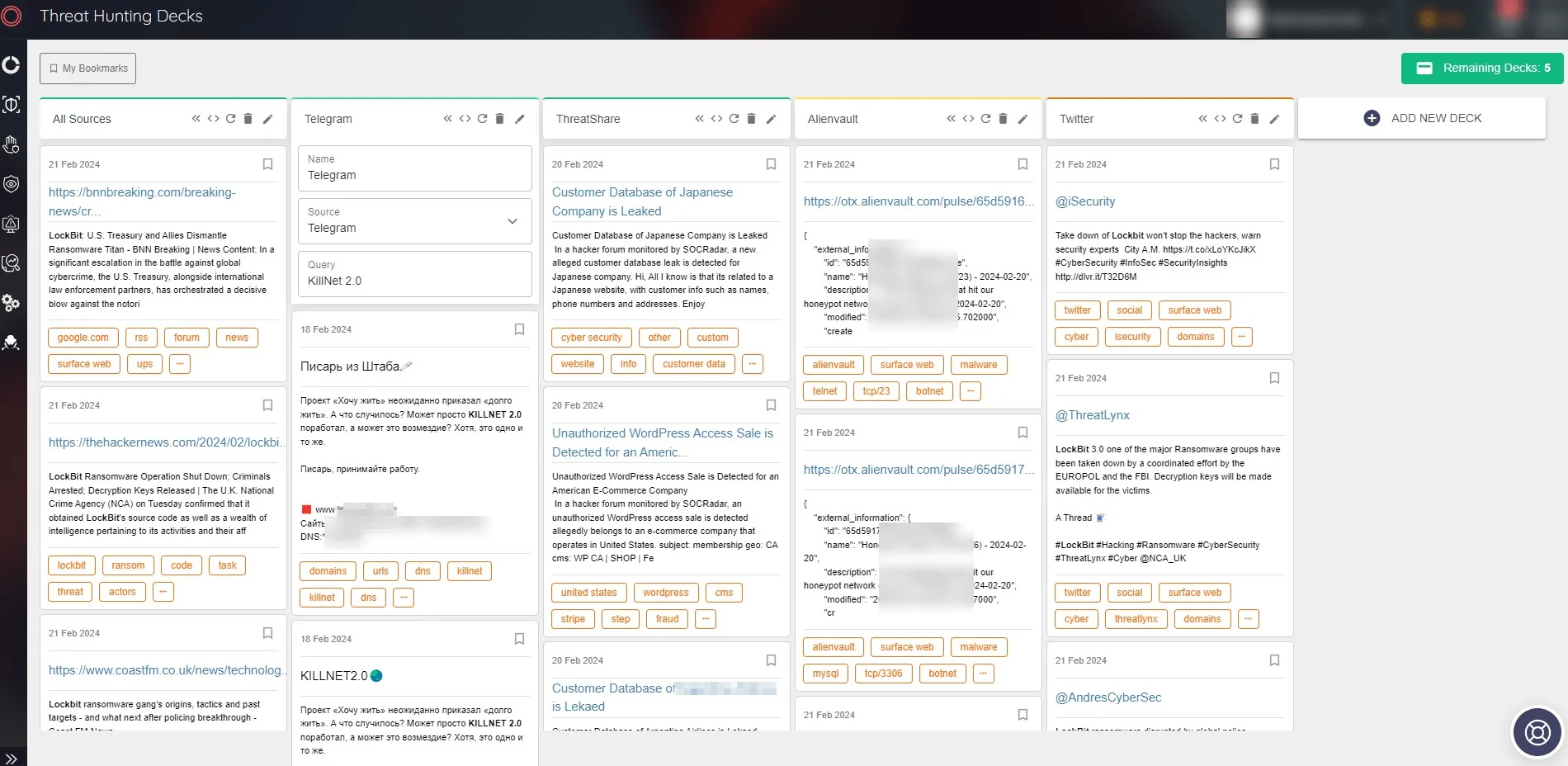
SOCRadar Threat Hunting, Threat Hunting Decks
Armed with Dark Web Radar’s Search Engine, organizations have at their disposal a powerful tool for uncovering potential threats with pinpoint accuracy. This “Google of the Dark Web” provides a highly customizable platform for threat hunting, enabling users to search for specific keywords, IP addresses, and more. The curated news feeds and search capabilities offer tailored intelligence, allowing businesses to stay one step ahead of cyber threats specific to their industry or region.
Bonus: Daily Dark Web
For those intrigued by the complexities of the dark web, maintaining confidentiality, ensuring robust security measures, and understanding the profiles of threat actors are essential. One notable platform excelling in these areas is the Daily Dark Web.

Daily Dark Web’s interview with the threat actor known as ‘USDoD’. (Source: Daily Dark Web)
Daily Dark Web specializes in comprehensive analysis and reporting of dark web activities. Their coverage includes detailed insights from hacker forums, Telegram channels linked to threat groups, and updates from ransomware groups. Their approach extends beyond mere reporting; they’ve also managed to secure interviews with well-known threat actors like USDoD and RansomedVC, offering a rare glimpse into the minds and motivations driving these shadowy figures.
Moreover, Daily Dark Web enriches its audience’s understanding through regular dissemination of statistics on dark web activities. These reports, presented weekly, monthly, and annually, help paint a clearer picture of the evolving landscape in cybersecurity threats. By providing such detailed and engaging content, Daily Dark Web plays a pivotal role in illuminating the often obscure aspects of the dark web.



































