
Dark Web Threat Profile: pompompurin
[Update] June 26, 2023: BreachForums was seized by the FBI three months after the arrest of its administrator. Added the subheading “FBI Seizes BreachForums After Arrest of Admin.”
[Update] June 20, 2023: Rival forums leak the database of the new BreachForums, added the subheading: “BreachForums Hacked by OnniForums.”
[June 14, 2023] Update: BreachForums has reemerged under new management by the hacking group ShinyHunters. Added the subheading “BreachForums Reemerges Under ShinyHunters.”
[March 22, 2023] Update: The BreachForums has been shut down. Added the subheading “Fearing Compromise, BreachForums Shuts Down.”
[March 20, 2023] Update: The BreachForums admin Pompompurin has been seized by law. Added the subheading “Authorities Arrested Pompompurin.”
The dark web world can be considered an ever-changing place consisting of countless opportunities and numerous platforms threat actors use to communicate with each other. One of these platforms, RaidForums, was one of the famous dark web forums where threat actors hang out daily and share their hacks and leaks. One of the hackers using RaidForums, pompompurin, was just an active everyday member in RaidForums back in the day.
Another Active Member with Great Potential: pompompurin
Pompompurin was not a moderator or an admin but a respected member among RaidForums’ hackers.
RaidForums was not the only forum he was a member of; he was also a member of Russian dark web forums such as XSS. Although we do not know where he is from, we know that he speaks Russian. It is safe to assume he is from one of the Russian-speaking countries.
Pompompurin also was a hacker and a data leaker himself. He hacked and leaked the data of countless companies since he first joined RaidForums in 2020. Three of his hacks have attracted massive attention in the threat actor community.
Pompompurin Exploits FBI Domains to Discredit a Cybersecurity Entrepreneur
In November 2021, one of the FBI’s domains was used to send hoax emails to thousands of people. Pompompurin claimed responsibility for the hack. Pompompurin’s main goal was to carry out his vendetta against an innocent cybersecurity entrepreneur, whom he had hacked many times. Just as the hack happened, Pompompurin messages his victim on Twitter, informing him of the attack with a sarcastic message, “enjoy.”
Leaking PII of 2.5 Million People
In April 2021, pompompurin leaked a database containing personally identifiable information (PII) of 2.5 million Americans. The leak included full names, date of birth, email addresses, phone numbers, home addresses, marital status, political affiliation, salary, and other private details about US residents. This massive leak was approximately 263 GB and contained about 1255 CSV files and 59 million unique e-mails.

Hacking Crypto and Investing Company Robin Hood
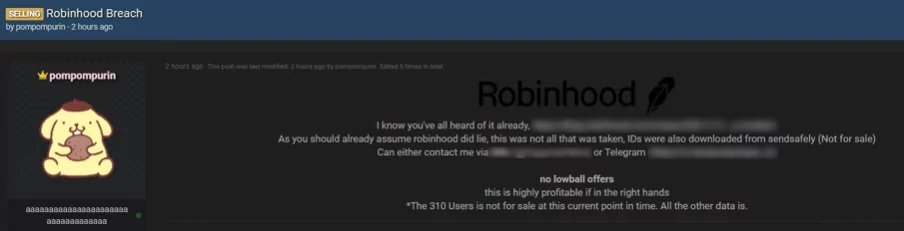
Also, in November 2021, the threat actor pompompurin hacked crypto and the investing company Robin Hood. The hack has begun with a social engineering attack on one of the customer support employees of the company.
Then, pompompurin gained access to customer support platforms the company uses. He could harvest emails and full names of approximately 7 million Robin Hood customers.
Pompompurin attempts to sell the breached data on a dark web underground forum, adding that he was also able to harvest IDs of Robin Hood’s customers, which were not for sale then. He puts at least five figures price for the dataset and claims that the dataset is profitable in the right hands.
Raid’s End
RaidForums was the forum pompompurin the most active until it was seized by the FBI and closed permanently. The forum was abruptly shut down and replaced with a honeypot server mimicking the login page of the old RaidForums.
No one understood what happened to RaidForums at first, but as time passed, it was clear that RaidForums was no more. Our person of interest, pompompurin, also waited at first to see and understand what happened to RaidForums.
When it was for sure that RaidForums was shut down, pompompurin did not wait long to open an alternative forum; Breached, aka BreachForums, filling the void RaidForums left.
A New Era: Breached
A couple of weeks after Raid was closed, pompompurin was sick of “all the stupid people trying to take the empty spot RaidForums once filled” and opened Breached.co. Below, you can see the first post pompompurin posted on BreachedForums, welcoming all users and stating the goal of his forum.
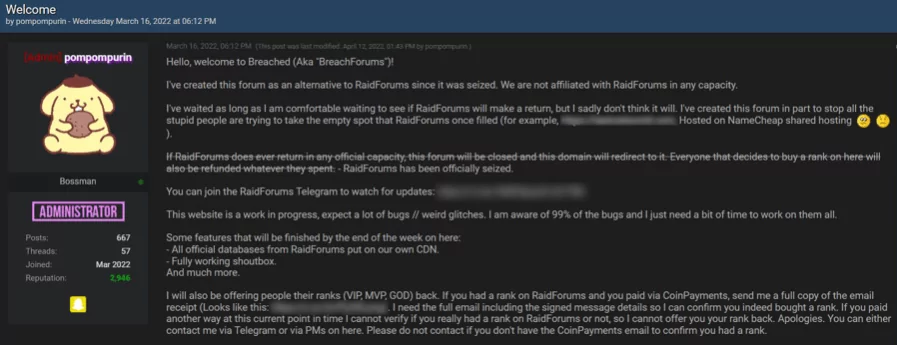
On the welcome post, pompompurin says that if RaidForums makes a return, he will close the forum. He says that Breached is not a competitor to RaidForums, but rather an alternative.
From this, we see that his main objective was to continue the RaidForums’ legacy. He did not want to lose the active user base and the market RaidForums had. He was able to fulfill his goals up to some extent, and he continues to make Breached as good as RaidForums was.
Breached directly “copies” or “transfers” the functionalities in RaidForums, such as the credit system or the ranking system. Pompompurin states that he will be offering people their ranks, VIP, MVP, GOD, in RaidForums back if they are able to prove it.
Breached also copies the looks and appearance of RaidForums to continue RaidForums legacy and for simplicity. In the first days of BreachedForums, there were lots of reposts of old data leaks and breaches. Pompompurin and other threat actors were trying to move Raid’s database to Breached as fast as possible and attract the attention of previous Raid members.
Breached has been growing its user database each and each day and since its start, Breached.co has become one of the most actively used dark web forums thanks to its admin pompompurin and the threat actor community.
Climbing the ladder from an active member to single admin of a massive forum, pompompurin is writing his name as one of the most influential threat actors in the community, as the founder and the admin of BreachedForums.
Authorities Arrested Pompompurin
“Pompompurin” has recently been arrested by US law enforcement for running the BreachForums hacking forum. The FBI filed an affidavit stating that the suspect, who identified himself as Conor Brian Fitzpatrick, admitted to owning the website and has been charged with conspiring to sell unauthorized access devices.
“Pompompurin” has been involved in some of the most notable hacks recently, including multiple cases involving the FBI. They claimed responsibility for breaching the agency’s email servers in 2021 and disseminating thousands of false cybersecurity warnings.
He was released on a $300,000 bond signed by his parents and is set to appear before the District Court for the Eastern District of Virginia on March 24, 2023. As part of his release conditions, Fitzpatrick is not allowed to obtain a passport, contact his co-conspirators, or use any narcotic drugs unless prescribed by a licensed medical practitioner.
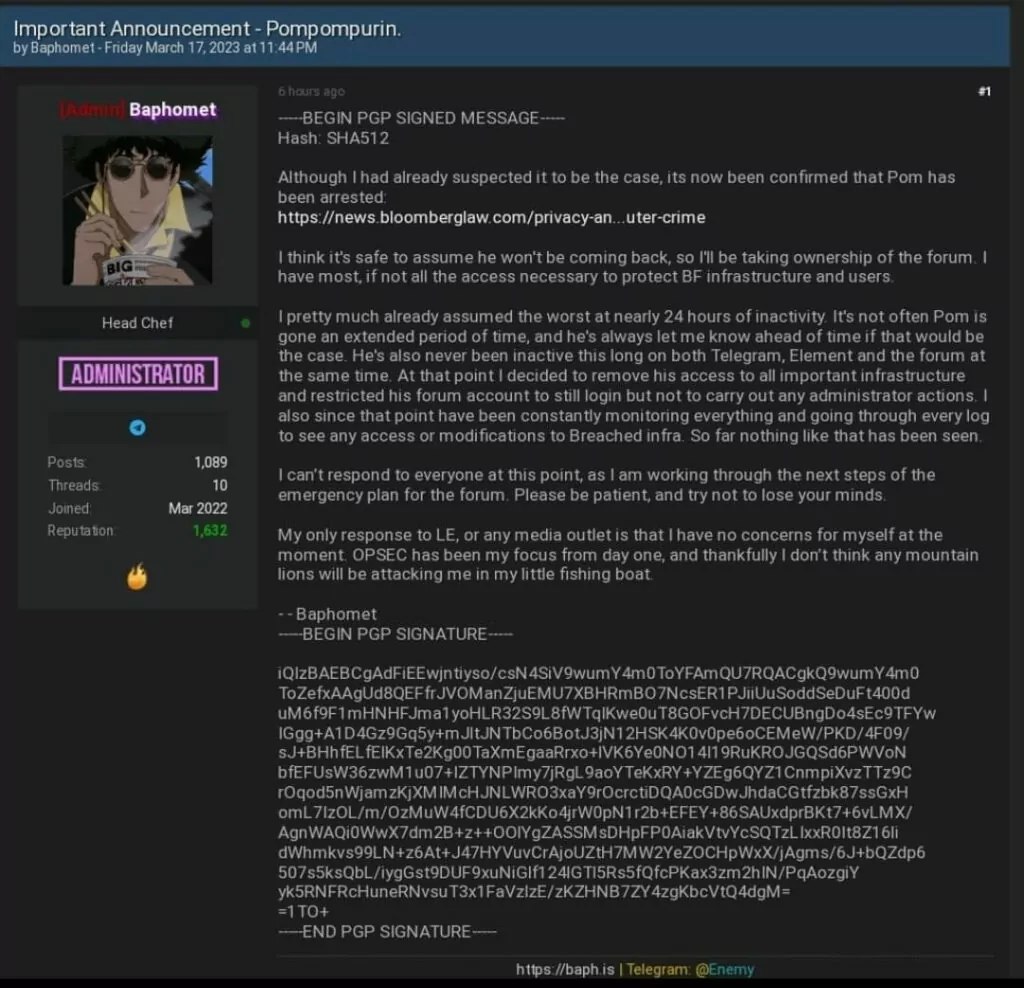
After Fitzpatrick’s arrest, another forum user named Baphomet said they would take control of the website.
Fearing Compromise, BreachForums Shuts Down
Following the arrest of “pompompurin,” the remaining administrator, Baphomet, took the BreachForums site offline and began moving it to a new infrastructure that would be safe from law enforcement.
The plan was to migrate the site to an untraceable infrastructure, but Baphomet later announced that they canceled this plan because law enforcement likely had access to Poms machine.
Baphomet discovered that someone had logged into an old CDN server, indicating that nothing could be considered safe, including the configurations, source code, and user information.
Fearing that the infrastructure was compromised, Baphomet announced on March 21, 2023, that the hacking forum had been taken down but stated that this might not be the end of the forum.
The Telegram channel will remain up, and Baphomet will continue to have an online presence to discuss with other forum owners and potentially build something new.
BreachForums Reemerges Under ShinyHunters
BreachForums has reemerged under new management by the hacking group ShinyHunters. Baphomet, an administrator of the original forum, confirmed the return in a PGP-signed (PGP stands for Pretty Good Privacy and means cryptographically signed) message, leaving little doubt about its authenticity.
ShinyHunters, operating through a Telegram account, has started sharing updates and information on the platform. On BreachForums, ShinyHunters announced their return with the following post:
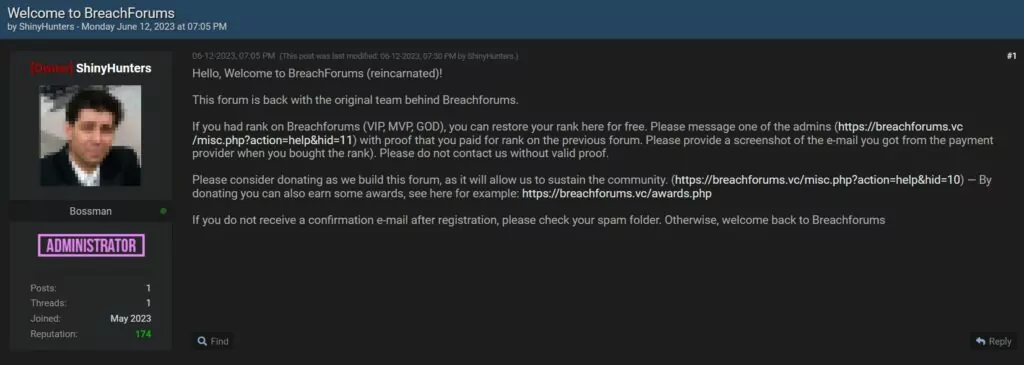
The revival of BreachForums has raised the alarm among cybersecurity experts and law enforcement agencies globally.
ShinyHunters is known for high-profile data breaches. They have targeted organizations to steal sensitive information by selling user data for financial gain.
They gained attention in 2020 for their involvement in major data breaches, including Tokopedia, a popular Indonesian online marketplace, and Microsoft’s GitHub.
They accessed and leaked millions of user records, selling the stolen data on underground forums and dark web marketplaces.
While ShinyHunters’ exact identity remains unknown, their activities and the scale of breaches they are associated with raise concerns about cybersecurity and data protection.
BreachForums Hacked by OnniForums
Shortly after its revival by ShinyHunters, BreachForums faced a new threat from its rivals. A database containing the personal information of 4,700 BreachForums users began circulating among other cybercrime forums.
The leaked database comprises usernames, password hashes, login keys, email addresses, IP addresses, registration dates, social media handles, and some user activity data. Researchers have confirmed that the leaked information corresponds to users who registered on the reemerged forum.
The exposure of cybercriminals’ personal data can have serious consequences, as their identities and activities are now revealed to researchers and, furthermore, to law enforcement.
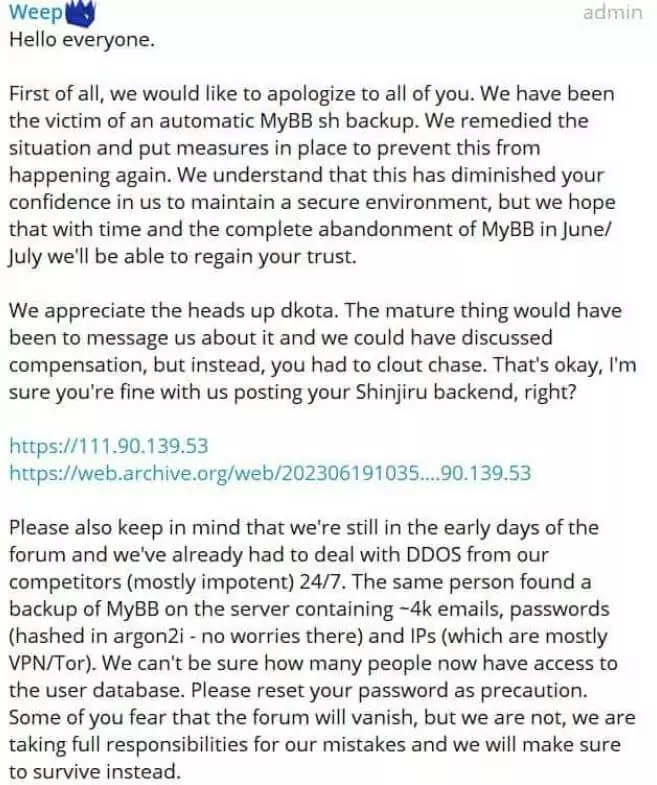
In a Telegram chat, a BreachForums admin named “Weep” confirmed the cyberattack and stated that the breach occurred due to a zero-day vulnerability in the open-source forum software MyBB. Weep attributed the breach to a hacker forum called “OnniForums.”
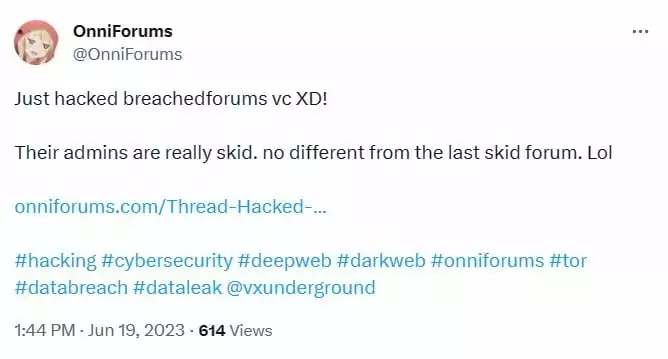
OnniForums’ seemingly official Twitter account has claimed responsibility for the attack.
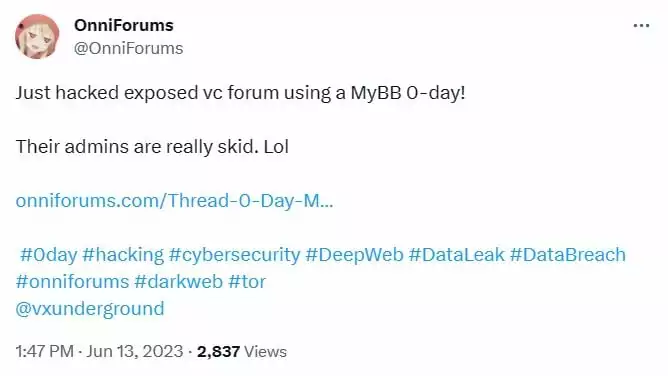
OnniForums has lately also revealed that they were involved in breaching the hacker forum called “Exposed.”
FBI Seizes BreachForums After Arrest of Admin
BreachForums was seized by the FBI three months after the arrest of its alleged administrator. According to FBI testimony, millions of US citizens and various US-based companies were victimized.
The Department of Justice credited the FBI with a disruptive operation that caused the forum to go offline, although the web domain remained accessible but inactive.
After the RaidForums administrator’s arrest and domain seizure last year, BreachForums gained popularity as a platform connecting hackers and buyers of stolen data.
The FBI collaborated with international law enforcement agencies to take down the site. The status of the ongoing investigation and its conclusion remain uncertain.




































