Top 5 Tactics Threat Actors Use for Initial Access
A short while ago, combined security advice released by several national cybersecurity agencies highlighted the top ten attack vectors most used by threat actors to access networks. Threat actors take advantage of outdated systems, external remote services, phishing, and many other vulnerabilities to gain initial access. To be appropriately protected from threats, we need to know the points we can give vulnerabilities to attack.
This writing focuses on the top five techniques malicious actors commonly use to gain initial access to victim networks.
1. External Remote Services
Adversaries may use external-facing remote services to access and remain in a network. VPNs, Citrix, and other remote access techniques enable users to connect to internal company network resources from remote locations. Remote service gateways are frequently used to manage connections and credential authenticate these services.
Access to Valid Accounts is frequently required to access the service, which may be obtained by credential pharming or by getting the credentials from users after compromising the company network. During an operation, access to remote services might be employed as a redundant or persistent access mechanism.
Access can also be obtained via an exposed service that does not require authentication, including an exposed Docker API, Kubernetes API server, or web application such as the Kubernetes dashboard in containerized systems.
Among the tactics detected by Group-IB in ransomware attacks, the employment of command and scripting interpreters and remote services, which were present in all episodes analyzed, is at the top of the chart.
Furthermore, the attackers employed various techniques to identify remote computers, steal credentials, and deactivate security measures.
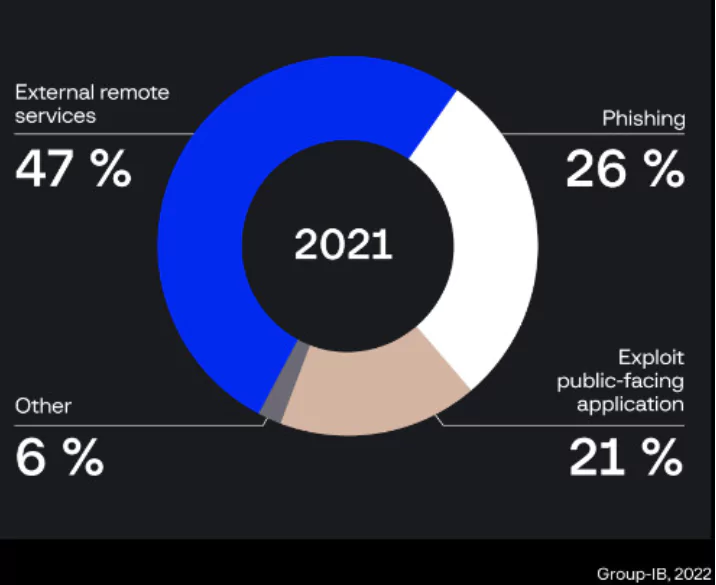
2. Phishing
Failure to recognize and prevent phishing attacks is given to cybercriminals to gain initial access. Phishing is a type of social engineering that is becoming more popular daily.
Cybercriminals send malicious emails to attack computer systems, typically included in Microsoft Word or Excel documents. According to experts, phishing attacks are the most common method used by hackers to gain first access in 2022 and cover 40 percent of attacks that provide first access. The attacker will target a specific individual, firm, or industry in spear phishing.
Adversaries can engage in non-targeted phishing, too, such as large virus spam operations. Adversaries may send victims emails with malicious attachments or links to run malicious code on target systems. Phishing can also take place through third-party services such as social networking sites. Phishing may also use social engineering tactics, such as posing as a trustworthy source.
Network intrusion detection systems and email gateways can be employed to detect phishing with malicious attachments in transit. Detonation chambers may be used to detect malware attachments as well. Signature and behavior-based solutions are possible; attackers may design extensions to circumvent these systems.
URL inspection inside the email (including expanding shortened URLs) can aid in the detection of links to known malicious sites. Detonation chambers may be used to identify these links, and either automatically go to these sites to verify whether they are harmful or wait for a user to view the link and record the content.
Because TLS encryption is employed by most third-party services used for phishing through service, SSL/TLS inspection is often necessary to discover the first communication/delivery. Intrusion detection signatures or other security gateway appliances may be able to identify malware via SSL/TLS inspection.
3. Exploit Public-Facing Application
Adversaries may attempt to exploit a flaw in an Internet-facing machine or application by leveraging software, data, or commands to create undesired or unexpected behavior. The flaw in the system might be a bug, a malfunction, or a design flaw.
These applications are typically websites, but they may also include databases (such as SQL), standard services (such as SMB or SSH), network device administration and management protocols (such as SNMP and Smart Install), and any other applications with Internet-accessible open sockets, such as web servers and related services. Depending on the fault being exploited, this might involve Defense Evasion Exploitation.
Exploiting an application hosted on cloud-based infrastructure and containerized may compromise the underlying instance or container; this can give an adversary access to the cloud or container APIs, exploit container host access through Escape to Host, or exploit weak identity and access management restrictions.
The organizations discovered 22 new security vulnerabilities exploited by ransomware gangs in the first few months of the year, representing a 7.6 percent rise from December 2021.
However, not all bugs are novel. In 2019, half of the flaws lately connected to ransomware attacks were published. However, many have public vulnerabilities, making the attacker’s task relatively easy. The four organizations discovered that ransomware perpetrators were exploiting 157 vulnerabilities in the first quarter of 2022, slightly higher than in the previous quarter.
4. Relationship of Trust
Adversaries may breach or otherwise use organizations with access to their targeted victims. Access via a trusted third-party relationship uses an existing connection that may not be safeguarded or is subject to less scrutiny than typical methods of acquiring network access.
Organizations frequently provide second or third-party external suppliers with higher access to allow them to handle internal systems and cloud-based settings. IT (Information Technology) services contractors, managed security providers, and infrastructure contractors are some of these connections (e.g., HVAC, elevators, physical security).
The third-party provider’s access may be confined to the infrastructure under maintenance, but it may reside on the same network as the rest of the organization. As a result, the other party’s Valid Accounts used to access internal network systems may be hacked and manipulated.
5. Valid Accounts
Adversaries may obtain and use existing account credentials to achieve Initial Access, Persistence, Privilege Escalation, or Defense Evasion. Compromised credentials can be used to bypass access constraints on numerous resources on network systems, as well as for continued access to remote systems such as VPNs, Outlook Web Access, and remote desktops.
Compromised credentials may provide attackers additional access to specific procedures or restricted network locations. Adversaries may opt not to employ malware or tools in conjunction with the lawful access provided by those credentials to make their presence harder to spot.
Finally, to keep hackers out of your system, the first step should be not to give them the initial entry point. Above, we shared some of the most prevalent tactics hackers used to gain initial access in 2022. Developing technology will continue to provide opportunities to threat actors, so being conscious of new cybersecurity technologies and using these technologies correctly is necessary to keep your system safe.