The Age of Credential Stuffing & Account Takeover
For mobile and web applications, credential stuffing attacks are considered among the top threats. While on average hackers can find matches between the stolen credentials, the credential stuffing gets simpler and more efficient. These kinds of attacks are getting more serious and harmful. For instance, more brute force and credential attacks than DDoS attacks have taken place over the last three years in the finance industry. Just in 2016, more than 3 billion credentials were spilled due to data breaches.

Account takeover (ATO) attacks are on the rise and getting more popular as well between cybercriminals from all kinds of stripes. ATO alone cost a massive loss of 16.9 billion dollars for customers and e-commerce retailers in 2019. COVID-19 has contributed to more retail online, creating an atmosphere for ATO fraudsters with far more victims.
What’s credential stuffing?
Credential stuffing is an attack technique allowing attackers to use lists of compromised account usernames and passwords.
What’s an account takeover?
Account takeover (ATO) is a form of identity fraud and deception in which fraudulent third parties have successfully accessed the credentials of a user account.

What’s the difference between credential stuffing, brute force attacks, and password spraying?
Credential stuffing is categorized as a subclass of brute force attacks by OWASP. Yet credential stuffing is somewhat different from regular brute force attacks. Attacks using brute forces aim to formulate passwords without context, often using characters arbitrarily together with password recommendations. The credentials use the exposed info, which decreases significantly the amount of potential accurate responses.
- Brute force attacks: From a list of common or weak username/passwords pairs are used to hack into an account.
- Credential stuffing: Leaked and compromised username/password pairs are used to hack into different accounts.
- Password spraying: The same password with different usernames are used to hack into different accounts.

What are the real-life examples?
According to OWASP, the following incidents were the result of credential stuffing;
In 2011, Sony revealed that more than 93,000 online consumers had experienced a breach of their accounts on the basis of their usernames and passwords for their separate properties.
2014 the JPMorgan Chase attack, which threatened 76 million households and 7 million small businesses, took more than two months for the bank’s security team before the attack was prevented.
By 2016, hackers acquired the use of employees’ usernames and passwords, stolen in prior breaches, in a private GitHub repository that was used by Uber (Uber BV, and Uber UK) users. The attackers reported that their login stocking system has taken 12 employee user accounts away as email addresses, passwords and other platforms have been re-used. However, multifactor authentication for the affected accounts has not been activated.
In 2019, researchers found that hackers were passing 2.2 billion leaked records, called the Collection 1-5, through. This ‘mega leak’ contained 1.2 billion unique email addresses and passwords, 773 million unique email addresses, and 21 million passwords in plaintext. Hackers can simply test combinations for emails and passwords on different sites in the hope that a user has used one again.
According to Akamai’s 2020 State of the Internet/Credential Stuffing in the Media Industry report; “One attack in late March, after many isolation protocols had been instituted, directed nearly 350,000,000 attempts against a single service provider over a 24 hours”.
Which industries are affected the most?
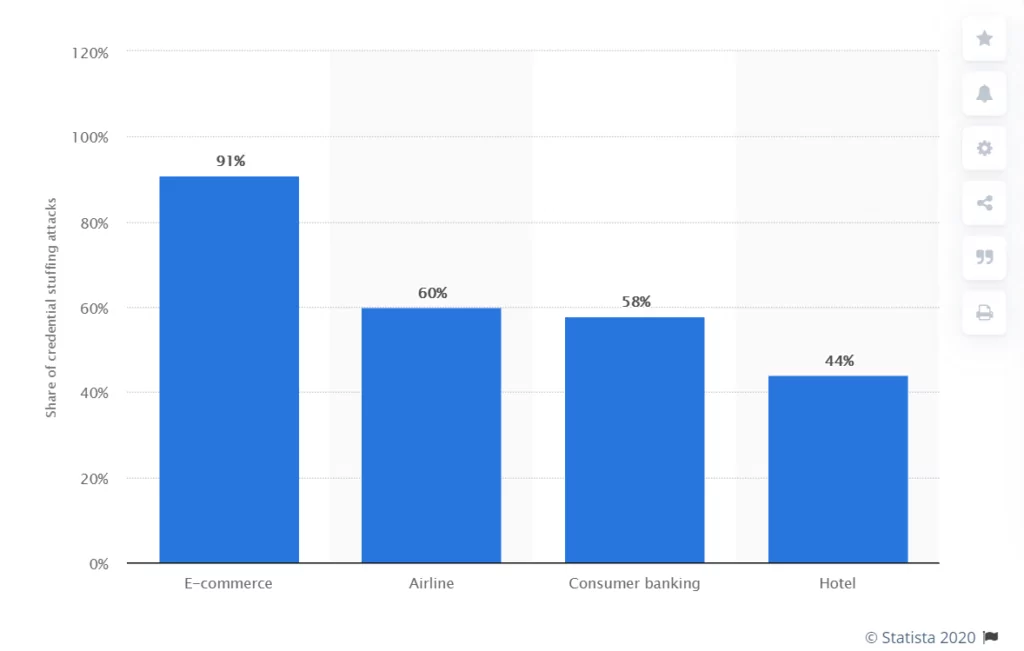
This figure shows the proportion of login attempts rendered by industry worldwide by 2018 as a credential stuffing attack. According to results, 91% of the login traffic in the e-commerce industry was categorized as credential stuffing, whereas only 44% of the traffic in the hotel industry is equally recorded.
Which countries provide credential stuffing attacks and which countries suffer from credential stuffing attacks?
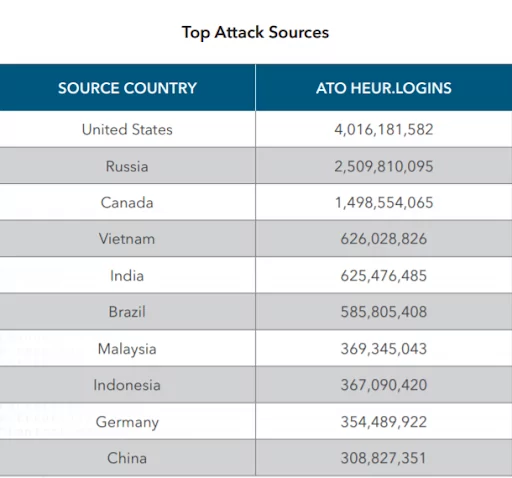
The United States remains the top source for credential stuffing attacks with 4 billion attacks since most of the common credential stuffing tools are developed there followed by Russia at 2.5 billion attacks and Canada at 1.5 attacks.
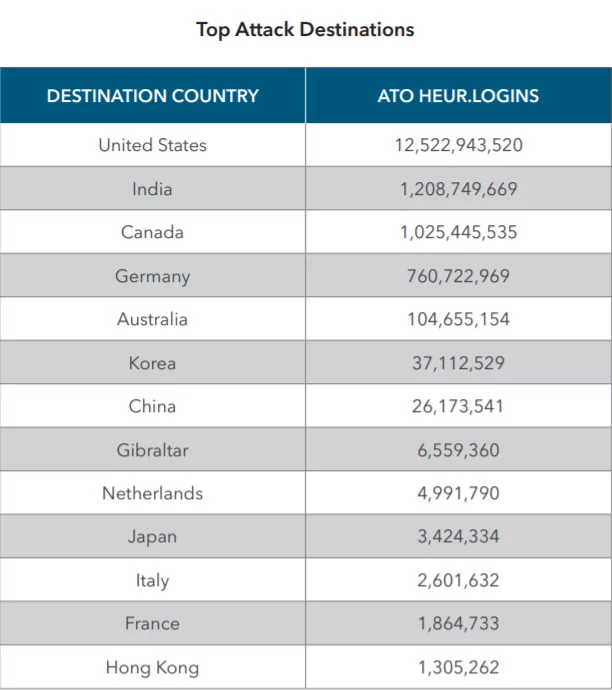
Also, the United States is the number one spot for attack destinations, because many of the most popular targets are based there. In terms of attack destinations, Indian and Canada are near second and third, but the volume is vastly overshadowed compared with the US.
Credential stuffing during COVID-19 pandemic
During the COVID-19 pandemic, cybercriminals are also beginning to re-check their credentials lists and test them against common services and applications. Zoom, a communication network that uses a wide variety of technologies to work together and that makes this accessible in corporations, governments and schools, is the most common of these services. More than 500,000 zoom accounts were confirmed to have been sold on the dark web and hacker forums in April 2020.
Between January 1 2018 and December 31 2019 (before the pandemic), 88 billion credential stuffing attacks were recorded. Of these, 20% targeted the media industry, which in many ways is particularly vulnerable compared to other sectors. On the other hand, due to the increased popularity of news content about COVID-19, the publishing industry in Q1 of 2020 has been the industry most affected by credential stuffing attacks.
How to prevent credential stuffing?
- Monitoring data breaches: Following the daily cyber incidents to determine if any of your credentials have been leaked is critically important. Most of the organizations unfortunately neither have time nor resources for keeping up with data breaches but they’d rather use CTI (Cyber threat intelligence) services.
- Change your passwords habits: Change your passwords regularly. Create complex passwords which include upper and lower case letters, numbers, and special characters. Never reuse the same username and password across multiple sites. Make sure every password is unlike the old one. Use password managers.
- Implementing two-factor authentication: Enabling and using two-factor authentication (2FA) adds another layer in defense in order to protect your sensitive data.
- Tracking logins: Organizations should track logins that lead to fraud consistently and then block the IP addresses associated with it.
Socradar can help organizations against credential stuffing attacks
Compromised credentials found in combo lists are often used in credential stuffing campaigns, phishing, and account takeover attacks to support other crimes such as banking fraud. Millions of users of Netflix, Spotify, Zoom, and many major e-commerce platforms are frequently targeted which leads the way for your adversaries.
To reduce the negative effect of combo lists on your online business and brand reputation, SOCRadar’s Fraud Protection module allows you to monitor newly-detected fresh combo lists, username password combinations of millions of users, found on the dark web. By processing and analyzing these massive datasets, it provides you statistics on heavily used credentials that can be used to enhance your fraud prevention and password policies.
Discover SOCRadar® Community Edition for free
With SOCRadar® Community Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.