
20 Interesting Facts About Ransomware
Ransomware attacks marked 2021 and continue to make a splash in 2022. We’ve compiled some interesting information about this type of attack that has frightened financial institutions, government agencies, and even NGOs worldwide.
We know how flexible threat actors can be in a changing and transforming digital environment. Ransomware also gets its share of this flexibility and is being implemented with more effective techniques every day. In particular, ransomware-as-a-service (RaaS) has created a whole new market and allowed even non-technical malicious actors to target organizations.
Let’s pay attention to 20 interesting facts together to decipher the anatomy of ransomware attacks.
1. Approximate cost of a successful ransomware attack

Ransomware attacks mean billions of dollars in losses for companies. The cost of ransomware attacks reported in 2019 was approximately US$12 billion. In 2021, it was known that this number had reached around 20 billion USD.
Interestingly, the financial loss of companies is seven times the ransom demanded by threat actors. The picture becomes direr when business interruptions, system restructuring, the cost of legal procedures, and extra labor are added to the ransom paid.
2. The most leveraged vulnerabilities in ransomware attacks
The most common attack vectors used by ransomware gangs are unpatched vulnerabilities. In particular, we can say that zero-day vulnerabilities and vulnerabilities that allow RCE or privilege escalation are the most exploited. In 2021 alone, threat actors exploited 65 new vulnerabilities and deploy ransomware.
Notorious ransomware gangs like DarkSide and Conti are using both old and recent vulnerabilities as attack vectors, according to a report published in September 2021 in CisoMag.
Some of these vulnerabilities are:
3. The highest amount requested in a ransomware attack
CNA Financial (2021)
CNA Financial, one of the ten largest commercial insurance companies in the USA, announced that it was attacked by ransomware on March 23, 2021. The attack was carried out by a threat actor named Phoenix. As a result of negotiations that lasted until May, the company was able to get its data back by paying 40 million USD.
MediaMarkt (2021)
On November 8, 2021, a ransomware attack took place against MediaMarkt, Europe’s largest electronics retailer. The Hive gang, which carried out the attack, initially demanded a ransom of 250 million USD, but the amount was reduced to 50 million USD after a while.
Kaseya (2021)
In this attack, REvil had operated a supply chain attack by exploiting a vulnerability in Kaseya VSA software and demanded $70 million in exchange for a decryptor. Then, according to the US Director of National Intelligence (ODNI) statement, Kaseya had provided the decryptor to his customers.
4. Hacked Ransomware Groups

The biggest ransomware news of 2022 was the Contileaks. The incident showed that threat actors could also be hacked and their sensitive data exposed. The Russia-Ukraine war triggered a cyberwar and made this possible. Threat actors openly took sides in the war and made mutual threat statements. Conti’s taking side with Russia made them a target, and a hack that ultimately exposed the gang’s internal correspondence and ransomware source codes took place. It can be said that this was a process that accelerated the termination of the Conti brand.
5. Reward offers for ransomware gangs

Conti: The US State Department announced on May 6 that 10 million USD for information that would help identify or locate anyone with a key position in the Conti ransomware gang; it also announced that it is offering a 5 million USD reward for information that will help catch people attempting a Conti-linked attack in any country.
DarkSide: The US State Department also placed a bounty on DarkSide, the name behind the Colonial Pipeline attack, in May 2021. He announced that he would give a reward of 10 million USD for information that could lead to the identification of the leaders in the gang and 5 million USD for those involved in DarkSide-related attacks.
6. Average revenue of ransomware groups
The 2022 Crypto Crime Report released by Chainalysis shows that there has been a noticeable increase in ransomware payments. The amount, approximately 90,000 USD in 2020, is at the limit of 120,000 USD in 2021. This amount is expected to increase further in 2022.
According to this report, Conti, who has been associated with over 400 attacks, was able to obtain a ransom of close to 200 million USD from his victims.
DarkSide, which became famous for its Colonial Pipeline attack, earned 85 million USD in 2021. Thus, it became the second-highest-earning ransomware gang. Phoenix and REvil are thought to be the third and fourth gangs with the highest revenue.
7. How do ransomware groups determine ransoms?
Some ransomware gangs operate for political reasons or in connection with state-sponsored espionage activities. But most of them have profit motives purely. It is estimated that gangs act according to the endorsement information available on ZoomInfo or similar platforms when setting targets. This also explains the fact that financial institutions are mostly targeted.
You can view the chart below regarding the ransoms demanded from Conti victims in a study conducted by Check Point.
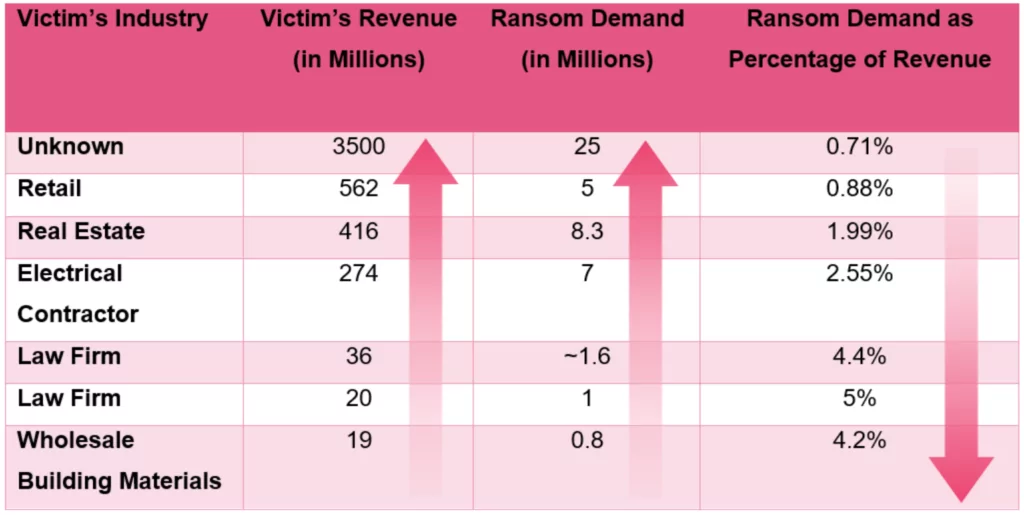
As you can see, the Conti group does not apply the same formula for each company when calculating the ransom demand and determines a number based on their income.
8. Average ransom demand, amount requested and paid after discount
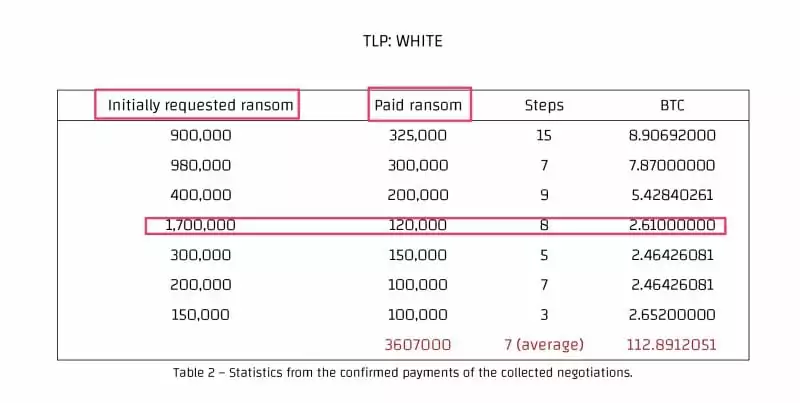
You can examine some of the data on the negotiations conducted by Conti in the table above. It seems that negotiations end in an average of 7 stages, and there is no apparent correlation between the amount initially demanded, and the ransom paid. Click here to read the complete analysis of ransomware negotiations.
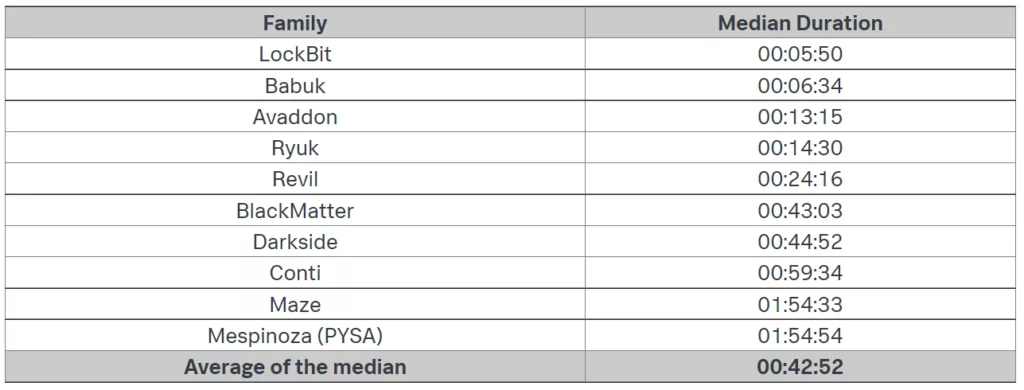
9. Which ransomware group has the fastest encryption algorithm?
“How long do you have until the ransomware encrypts your system?” This question is critical for companies’ cybersecurity teams. Threat actors are also striving to find the fastest encryption algorithm because they know its importance. We know that LockBit markets itself as the “fastest encryption” in the ransomware market. What about the others? Shannon Davis researched the subject and shared the data he obtained. In the table below, you see the ransomware and its encryption time.
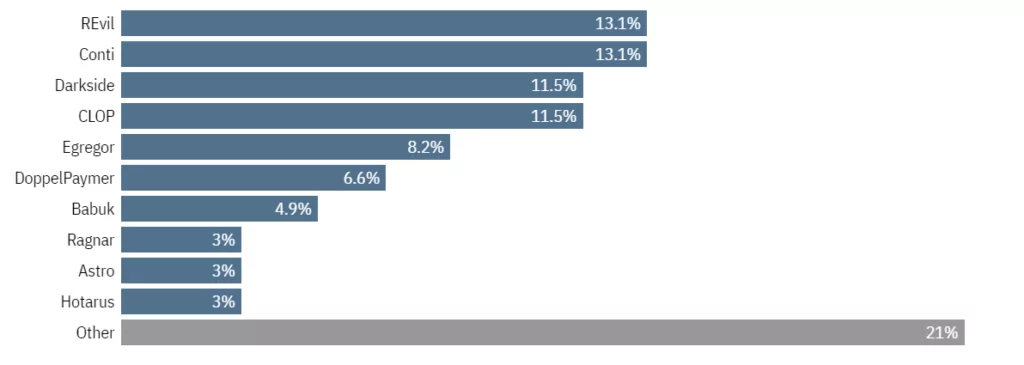
10. Top 10 ransomware gangs
When we evaluate the ransomware gangs according to the impact of the attacks, REvil and Conti stand out as the biggest names of 2021. When both the ransom amounts and the damage to the victims are taken into account, there are hardly any other threat actors that can be as effective as these two names. Of course, the arrests of REvil and the self-destruction of Conti may indicate that we will hear more new players using the extortion technique such as Lapsus$ in the coming days.
11. Countries most affected by ransomware
According to research by NordLocker, the country most affected by ransomware in 2021 was the USA. The United States, which held the first place with 732 cases last year, is followed by the United Kingdom with 74 attacks and Canada with 62 incidents. It is stated that in 2021, 58 ransomware attacks took place in France and 39 in Germany.
12. Most targeted industries by ransomware
The three industries most targeted by ransomware attacks are banking, utilities, and retail. However, this does not mean that other sectors are safe. Cyber security researchers underline that all companies and organizations should take the necessary precautions.
22% of ransomware attacks detected between July and September of 2021 targeted the banking and financial sectors. Utilities followed with 20% and retail with 16%.
13. Most used extortion techniques
The basic technique ransomware has followed so far is: Pay the ransom and get your encrypted data back. But advanced backup systems thwarted this threat from threat actors. So they started to discover new ways. Double extortion was the first example of this. Attackers began threatening to release the data publicly if the ransom was not paid.
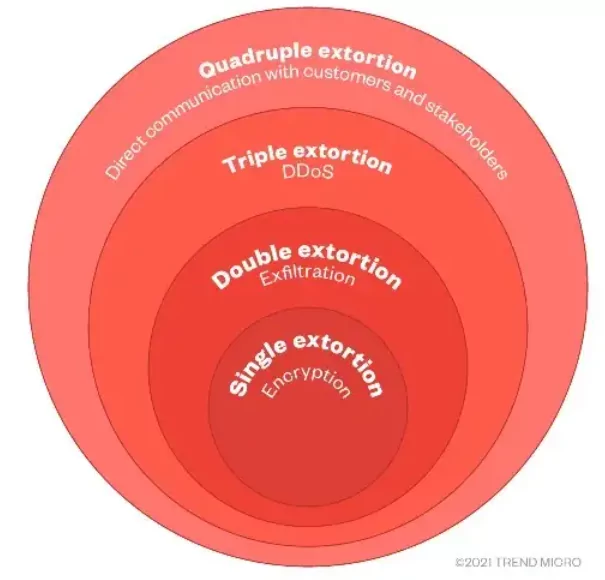
Although we do not meet very often, some gangs tried triple extortion. Simply put, triple extortion, which meant adding double extortion DDoS attacks, would not have motivated companies to pay the ransom, so quadruple extortion ensued.
Unlike other techniques, quad extortion targets the victim and the victim’s customers and stakeholders. This includes contacting customers directly, sending malicious emails, etc.
14. Could ransomware attacks be following a secret agenda?
The Conti ransomware attack, which started with a phishing email targeting the Health Service Executive on March 18, 2021, became far-reaching in May 2021, disrupting overall healthcare across the country. The exposure of the HSE, which is classified as critical infrastructure, to such an attack raised suspicions about whether the threat actors were acting intending to affect the entire country’s infrastructure.
Indeed, threat actors may commit certain security breaches for other purposes. You can click here to read the mind-opening report of PWC on the subject.
15. No More Ransom Project

Law enforcement, government authorities, and information security companies have created a new initiative to address ransomware gangs. The project, which emerged as “No More Ransom,” is run by the Netherlands National High-Tech Crime Unit, Europol European Cybercrime Center, Kaspersky, and McAfee. You can visit the official website for detailed information about the project, whose primary purpose is to support the victims in avoiding the threat, not after the system is affected.
16. “Corporate” structures of ransomware gangs
You may be surprised to see the term “corporate” about a cybercrime network. But Conti leaks showed us that a ransomware gang could have their HR department and even select high performers as “employee of the month.”
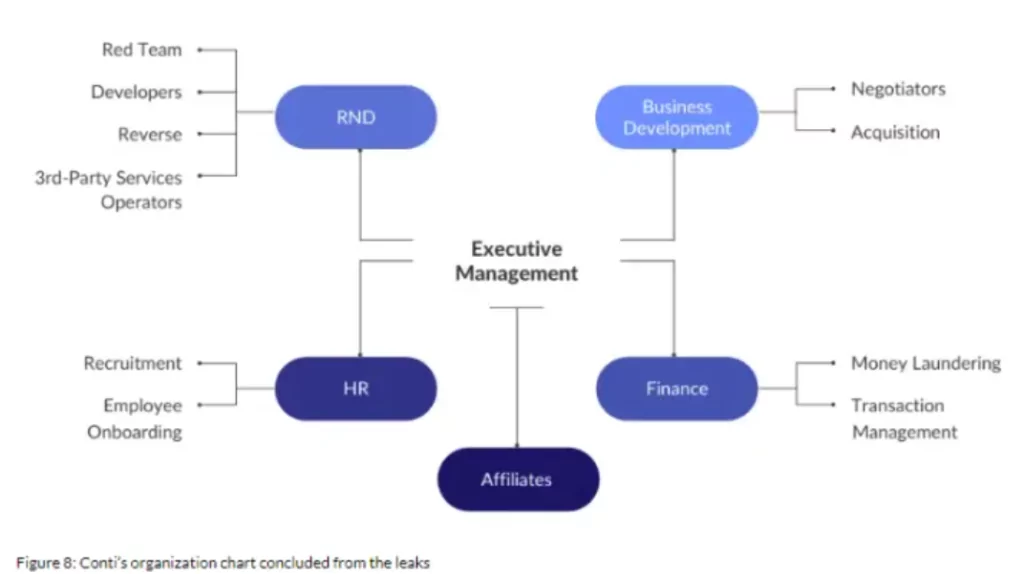
Conti, which has a company structure that we are almost used to, has created such a wide network similar to large holdings that some employees were unaware that they were working for cybercriminals.
It turns out that the cybercrime gang has upper management, finance, RND, and even business development departments.
17. DarkMirror: Follow data leaks blogs and Telegram channels
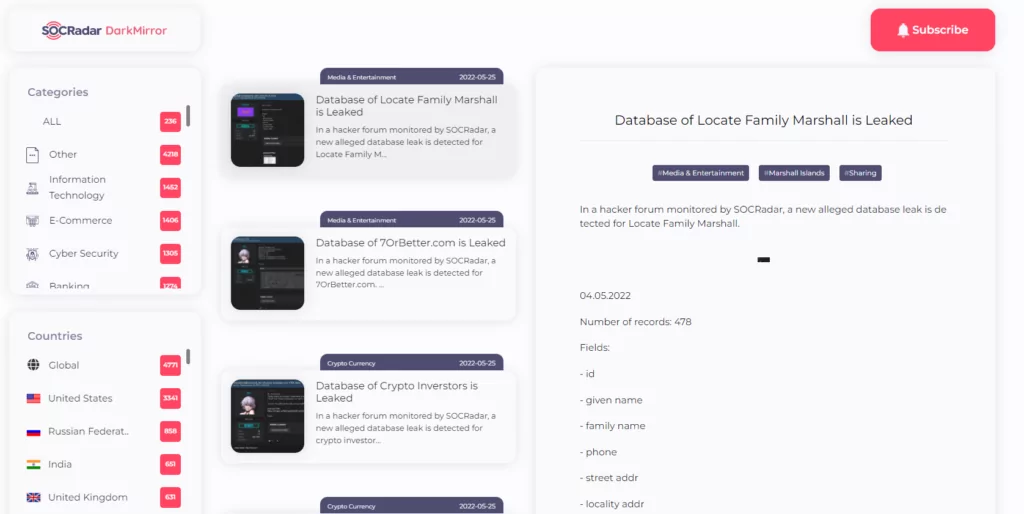
Actionable threat intelligence and digital risk protection must work in sync to stay vigilant against deep and dark web threats. Threat actors are constantly developing new techniques that are difficult to follow, making constant monitoring a time-consuming task. Automated systems should be used because even the smallest detail that is overlooked can lead to significant results. SOCRadar’s DarkMirror service allows you to easily track the posts of threat actors and filter by country or industry. You can click here to subscribe DarkMirror for free.
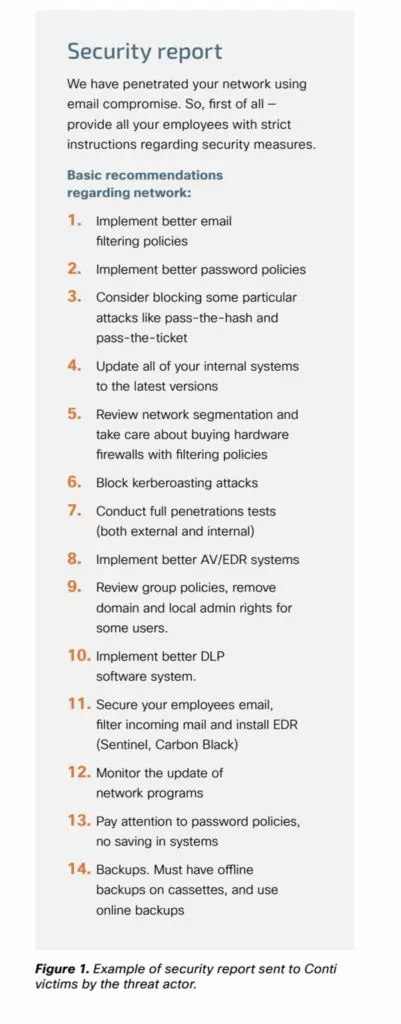
18. Million-dollar security advice from threat actors
Most ransomware groups take the ransom after a successful attack and deliver the decryptor to the victim and provide a brief note on any security vulnerabilities. This note may contain hints of attack vectors and recommendations for the victim to take better security measures.
Below you can see the security report Conti sent to the victim after a successful attack.
19. Country origins of ransomware groups
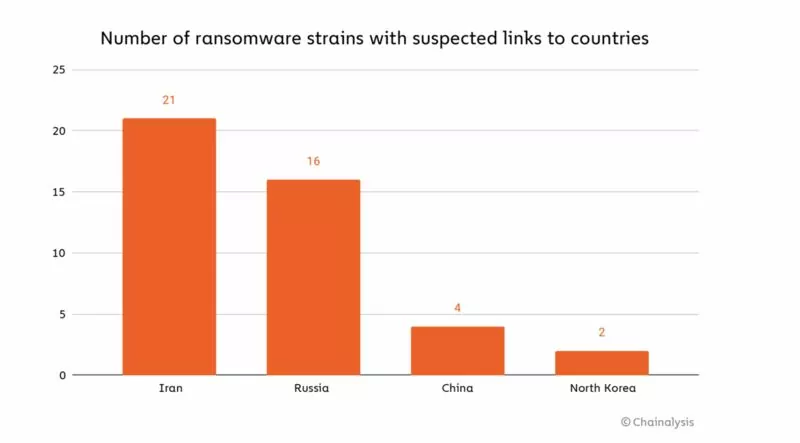
While the most notorious ransomware attacks are made by threat actors of Russian origin, according to research by Crowdstrike and Microsoft, most ransomware gangs originate in Iran. It is followed by Russia, China, and North Korea.
20. Estimated time of the infection process
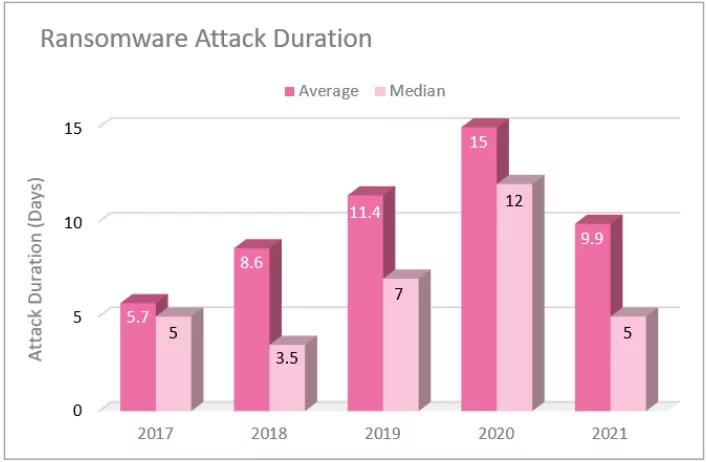
The damage that ransomware will cause to organizations is directly related to how long the encryption process will take. In the table above, you can see how this process has changed over the years. Cybersecurity experts think that the reason for the unexpected lingering of the process in 2020 is the increased attack surface with remote working practices. The shortened times with 2021 push threat actors to create new methods and faster encryption algorithms.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Get free access.


































