
Conti Ransomware Ended: They Operate With Other Groups Now
The Conti ransomware gang had taken its infrastructure offline and ceased operations. According to the news of Advanced Intel’s Yelisey Boguslavskiy, the Tor admin panel, where Conti held the ransom negotiations and published new data leak news, has been closed.
Experts believe that the process ended like this because Conti took the side of Russia in the Russia-Ukraine war, and critical information about the gang’s operations was disclosed.
A New Strategy?
Conti, which has recently come to the fore with a 672 GB data leak allegedly belonging to the Costa Rican government, surprised cybersecurity researchers by announcing its ending operations. Still, it is widely believed that this may be a new strategy. According to Boguslavskiy, Conti has already started partnering with other smaller ransomware groups.
The Conti brand is doomed, but the gang members’ role in the ransomware environment will continue. Members of famous ransomware groups such as REvil and BlackMatter, which had previously stopped their operations, continued their activities under other names or partnerships with different groups.
Conti Forms Partnerships With Other Ransomware Groups
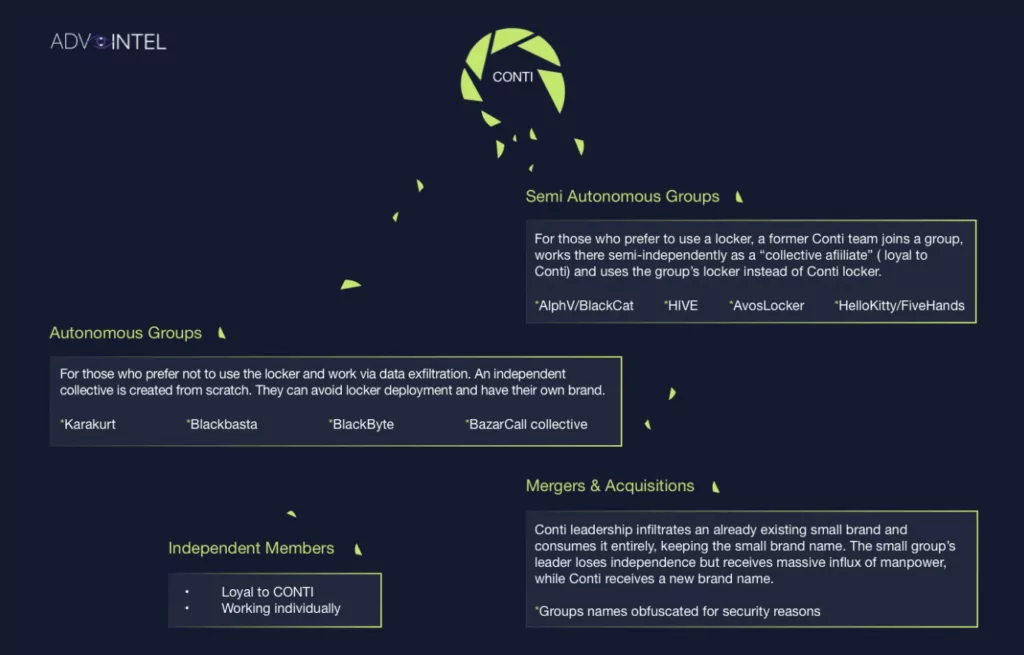
According to cybersecurity experts, this move by Conti will mobilize both the gang members and the ransomware industry. It will also make it harder for the group to be identified by official authorities. The group’s decision can be better understood given that the US government has placed a $15 million reward for gang leaders.
According to Advanced Intel’s report, Conti members partner with known ransomware gangs such as AvosLocker, Hive, HelloKitty, BlackByte, and BlackCat. Some gang members form groups such as Bazarcall and Karakurt, which only focus on data theft.
Who’s Next?
With the end of the Conti brand, it can be said that among the ransomware groups, LockBit and Lapsus$ have reached the top. Cybersecurity researchers think these gangs may follow a similar tactic.
As cybercrime groups gain popularity, they attract the attention of law enforcement and often end up in prison. Conti’s strategy can set an example for other gangs. Thus, a cybercrime network may be formed that is more difficult to track and detect.
Conti IoCs
|
Initial Access |
|
|
T1566 |
Phishing |
|
T1190 |
Exploit Public-Facing Application |
|
Execution |
|
|
T1106 |
Execution through API |
|
T1059.003 |
Command and scripting interpreter: Windows command shell |
|
T1047 |
Windows Management Instrumentation |
|
T1204 |
User execution |
|
T1053.005 |
Scheduled task/job: scheduled task |
|
Persistence |
|
|
T1053.005 |
Scheduled task/job: Scheduled task |
|
Privilege Escalation |
|
|
T1078.002 |
Valid accounts: domain accounts |
|
T1083 |
File and directory discovery |
|
T1018 |
Remote system discovery |
|
T1057 |
Process discovery |
|
T1016 |
System network configuration discovery |
|
T1069.002 |
Permission groups discovery: domain groups |
|
T1082 |
System information discovery |
|
T1033 |
System owner/user discovery |
|
T1012 |
Query registry |
|
T1063 |
Security software discovery |
|
Credential Access |
|
|
T1003 |
OS credential dumping |
|
T1555 |
Credentials from password stores |
|
T1552 |
Unsecured credentials |
|
Lateral Movement |
|
|
T1570 |
Lateral tool transfer |
|
T1021.002 |
Remote services: SMB/Windows admin shares |
|
Defense Evasion |
|
|
T1562.001 |
Impair defenses: disable or modify tools |
|
T1140 |
Deobfuscate/Decode files or information |
|
T1055 |
Process injection |
|
Command and Control |
|
|
T1071 |
Application Layer Protocol |
|
T1219 |
Remote access software |
|
Exfiltration |
|
|
T1567.002 |
Exfiltration over web service: exfiltration to cloud storage |
|
Impact |
|
|
T1486 |
Data encrypted for impact |
|
T1489 |
Service stop |
|
T1490 |
Inhibit system recovery |
Source: TrendMicro
Use SOCRadar® FOR FREE 1 YEAR
With SOCRadar® Free Edition, you’ll be able to:
- Prevent Ransomware attacks with Free External Attack Surface Management
- Get Instant alerts for fraudulent domains against phishing and BEC attacks
- Monitor Deep Web and Dark Net for threat trends
- Get vulnerability intelligence when a critical zero-day is disclosed
- Get IOC search & APT tracking & threat hunting in one place
- Get notified with data breach detection
Free for 12 months for one corporate domain and 100 auto-discovered digital assets.
Get Free Access.


































