
What Do Conti’s Leaks Tell Us about Ransomware Groups?
Conti, a dangerous ransomware gang that first appeared in December 2019, resided in Saint Petersburg, Russia, from the very beginning. During the actual conflict between Ukraine and Russia, eyes were naturally turned to the side where the group would participate in the cyber world.
Last week, many claims about the Conti group were reflected in the media. In this blog post, we compiled the information shared from the group’s website followed by SOCRadar analysts and from various hacker channels for you.
Has the Conti Ransomware Group Declared its Side in the War?
After the Russian invasion of Ukraine, hacker crews have started to announce their sides in the military conflict. While the widely known hacktivist initiative Anonymous chose to wage a virtual war against Russia, the notorious Conti ransomware group decided to ally with Russia. It declared it on Friday with a post on the group’s leak site.
As a noteworthy incident of cyber criminals’ diplomatic engagement, Conti had to publish a second announcement to clarify its position, a move which is commented as a back step to calm down pro-Ukrainian members. However, it seems that move does not satisfy some of the Conti team, and they leaked a cache of the group’s internal communication.
In a statement on Friday, Conti declared that in any attack or military intervention against Russia, Conti would attack the critical infrastructures of the other side with any source.
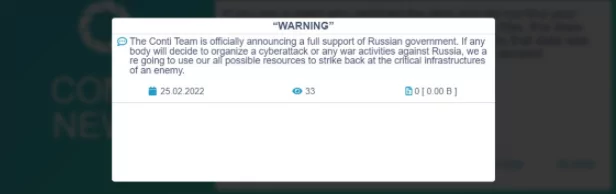
In the second statement made on the same day, it was observed that a softer language was used. The Conti gang does not mention targeting critical infrastructures in the second post. Yet, they expand the scale from Russia to Russian-speaking regions contextually, including Belarus, a strong supporter of Russian President Vladimir Putin.
Why Would a Ransomware Group Take Sides in the War?
Paradoxically, the group does not hesitate to claim that they do not have alignment with any government and added a note for condemnation of war. Equipped with anti-western and anti-American sentiments, the second announcement has provided insights into the cybersecurity community.
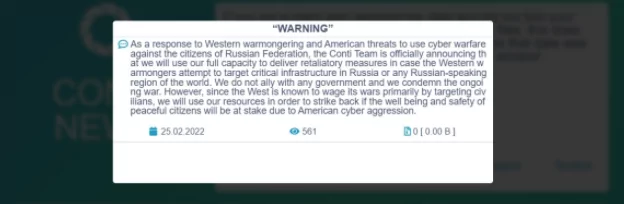
Firstly, avoiding threatening language against critical infrastructure, the group must have considered a powerful reaction from the rest of the online underground world and some officials in Washington DC.
Keeping in mind the development that occurred after the Colonial Pipeline attack, the increasing sensitivity and cautiousness to keep American critical infrastructures secure from cyber attacks would have sparked an imminent response to the group from the US.
Secondly, the first post might wreak havoc in the group’s inner circles, causing a reaction from some members that do not find it right to stand with Russia.
Considering the structure of ransomware groups, it can reasonably be argued that they are not homogenous entities that employ hackers from different religious and ethnic backgrounds.
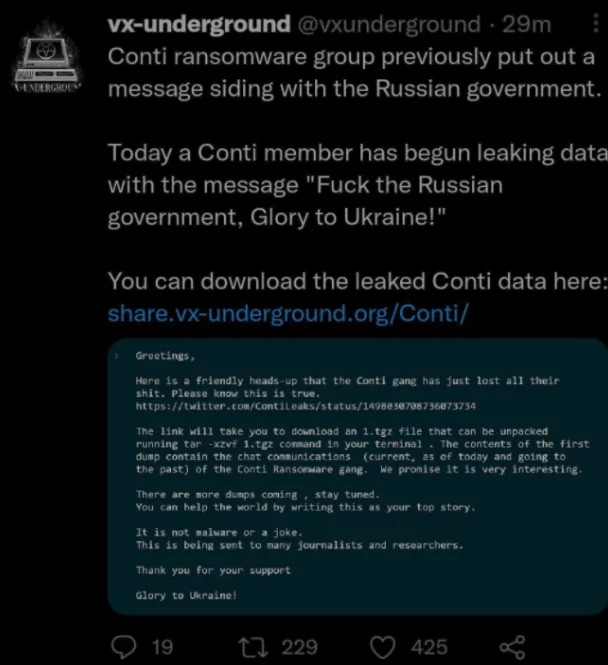
Conti Ransomware Gang Inner Chats Leaked by Insider
Meanwhile, an interesting situation occurred when a member of the Conti ransomware group leaked the gang’s internal conversations. The claim that these internal conversations included statements that they were pro-Russian quickly spread on social media.
The messages seem to have misled the Ukrainian members of Conti, and one of them was that the gang had hacked the internal Jabber/XMPP server. Correspondence was also leaked via email to many journalists and security researchers.
According to Recorded Future, the leaked data contains 339 JSON files consisting of one full-day log. Talks from January 29, 2021, to February 27, 2022, were revealed.
The LockBit Group did not Take a Part
A different situation was in question for LockBit, another dangerous and widespread ransomware group apart from the Conti group. LockBit announced that it was not a party to the war.
Noting that there are hackers from different nationalities within the group, the group stated that people from many countries, not only from Ukraine and Russia but also from China to the USA, are working for them. “Business is important to us, and we all take an apolitical stance. We are only concerned with money.”
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Get free access



































