Cyber Threat Intelligence
Get actionable intelligence against cyber threats. No wasting time with irrelevant feeds!
Even tiny pieces of information can save your organization from a devastating cyberattack. Getting one step ahead of cyber criminals can only be possible with monitoring them in the reconnaissance phase. Most of the SOC analysts can barely find time to monitor the deep and dark web, although they would like to do.
Your SOC’s virtual team member, SOCRadar, can monitor hacker forums, Telegram channels, and many other communications tools attackers use to organize an attack.
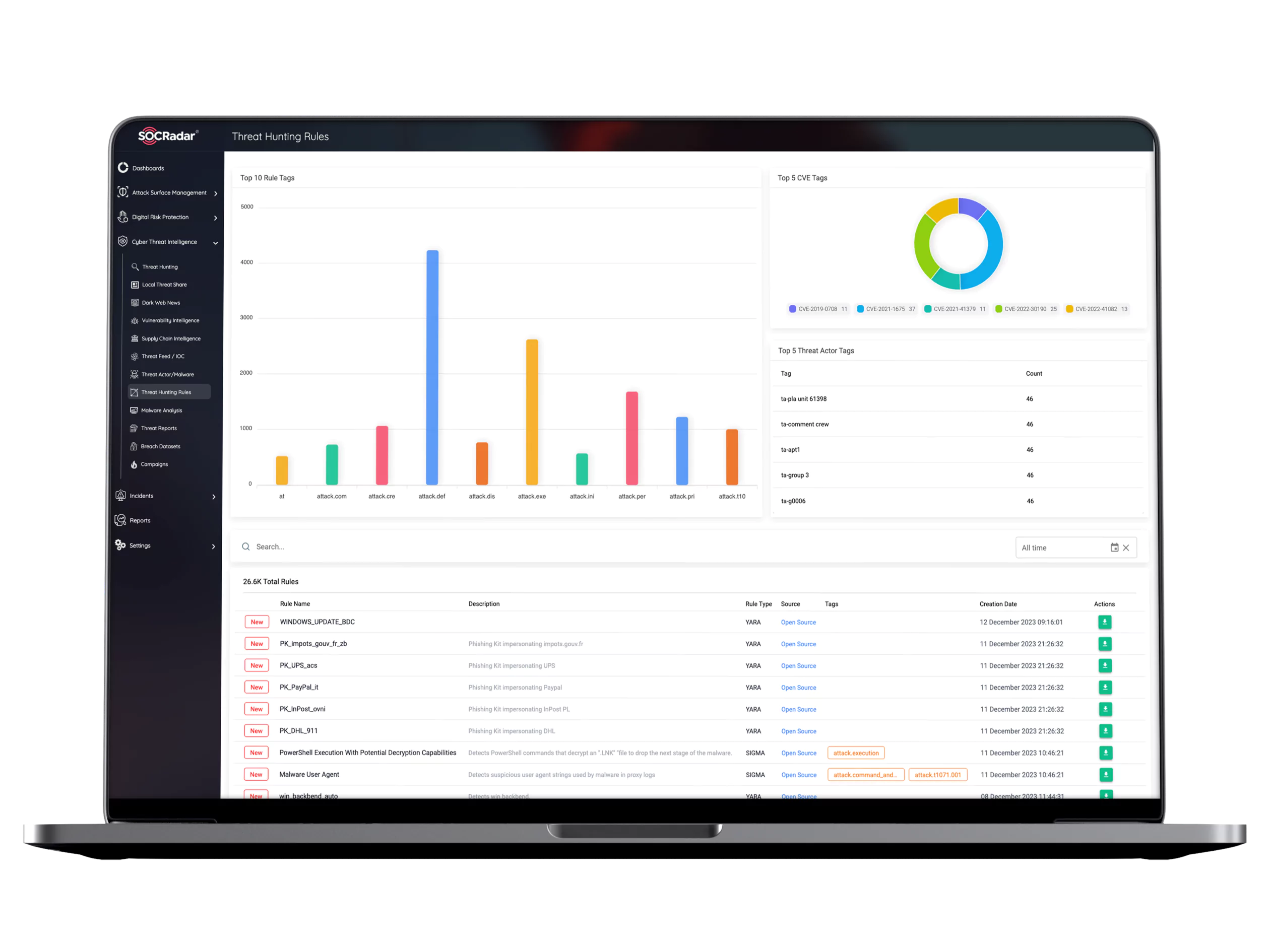
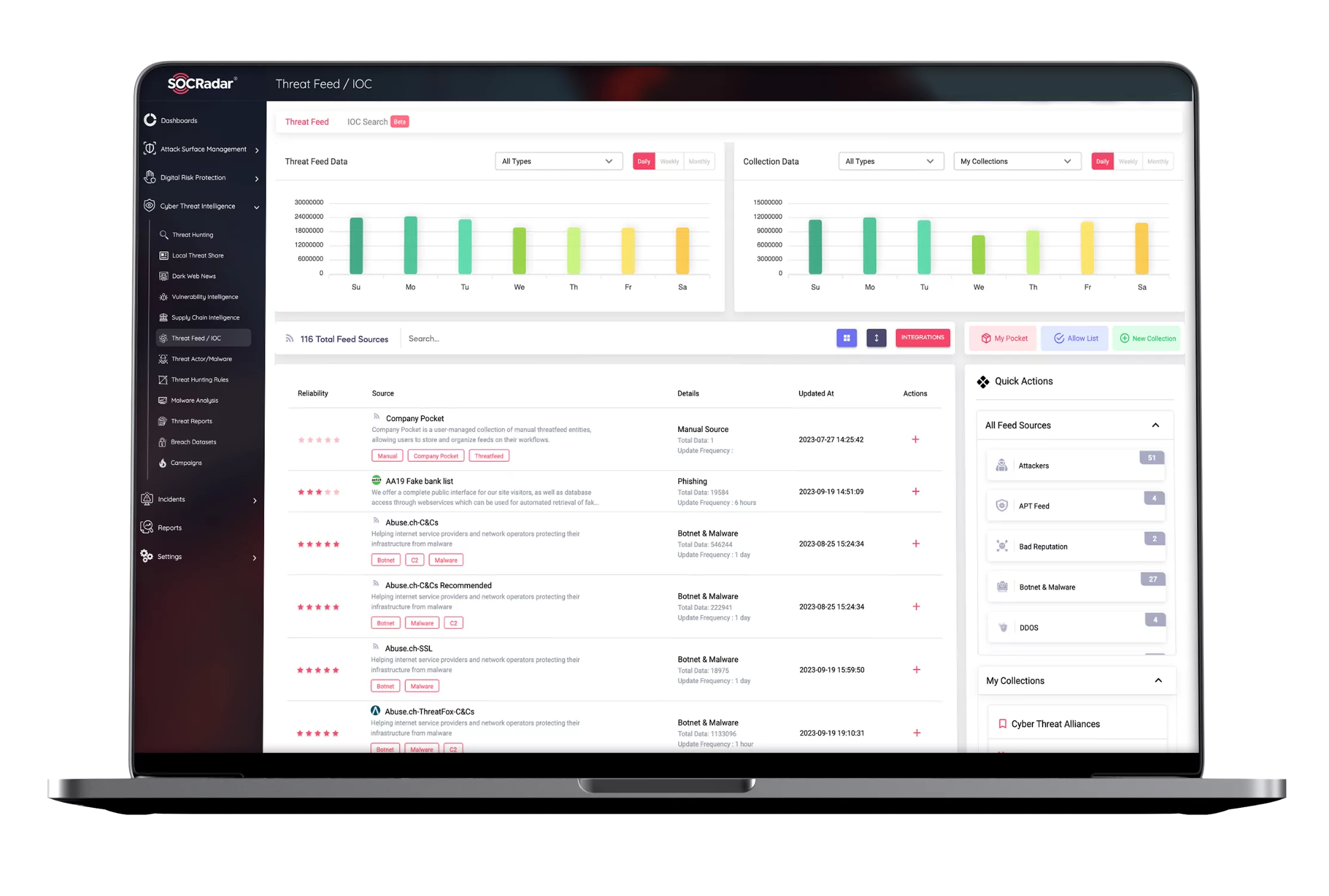
One of the indispensable parts of threat hunting is the IOC search and enrichment. When analyzed effectively IOCs has become extremely useful signals for SOC teams in identifying potentially malicious activity.
Dealing with IOCs is a delicate task. While querying data for specific artifacts, SOC analysts must avoid result overload. For an actionable outcome, IOC search should be enriched with threat intelligence.
SOCRadar correlates IOCs with your digital assets and malicious indicators for a streamlined workflow in IOC management.
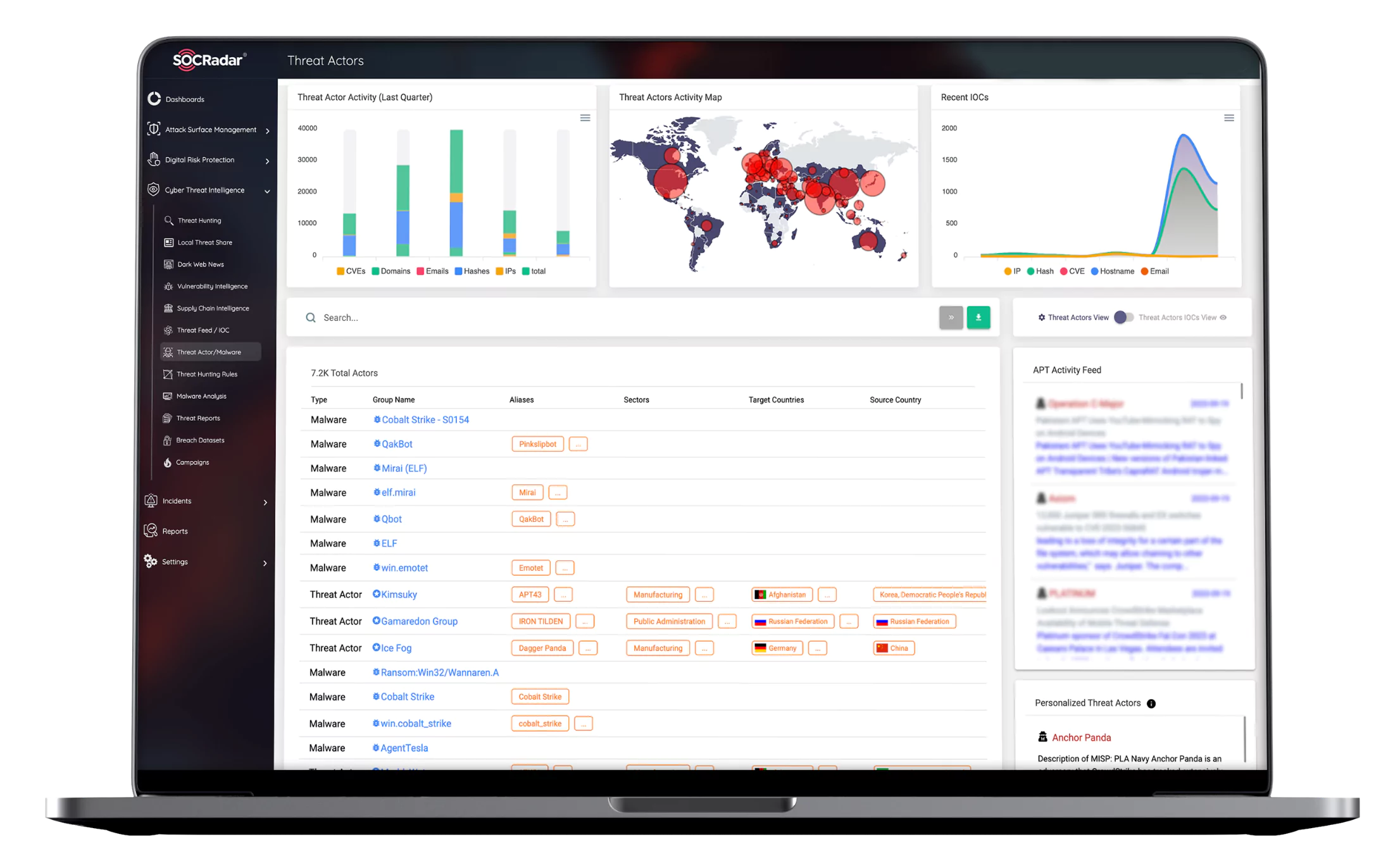
APT groups pose serious threats to organizations’ cyber security as they have long-term plans to exploit highly-sensitive information. Trying to remain undetected, APT groups use sophisticated tools in a strategic manner.
Intelligence is the best weapon against these sneaky cyber threat actors. Through automated data collection, classification, and AI-powered analysis of hundreds of sources across the surface, deep and dark web, SOCRadar monitors the activities of APT groups in a MITRE ATT&CK-compliant structure. It enables organizations to identify the use cases to more effectively detect and prevent malicious activity.
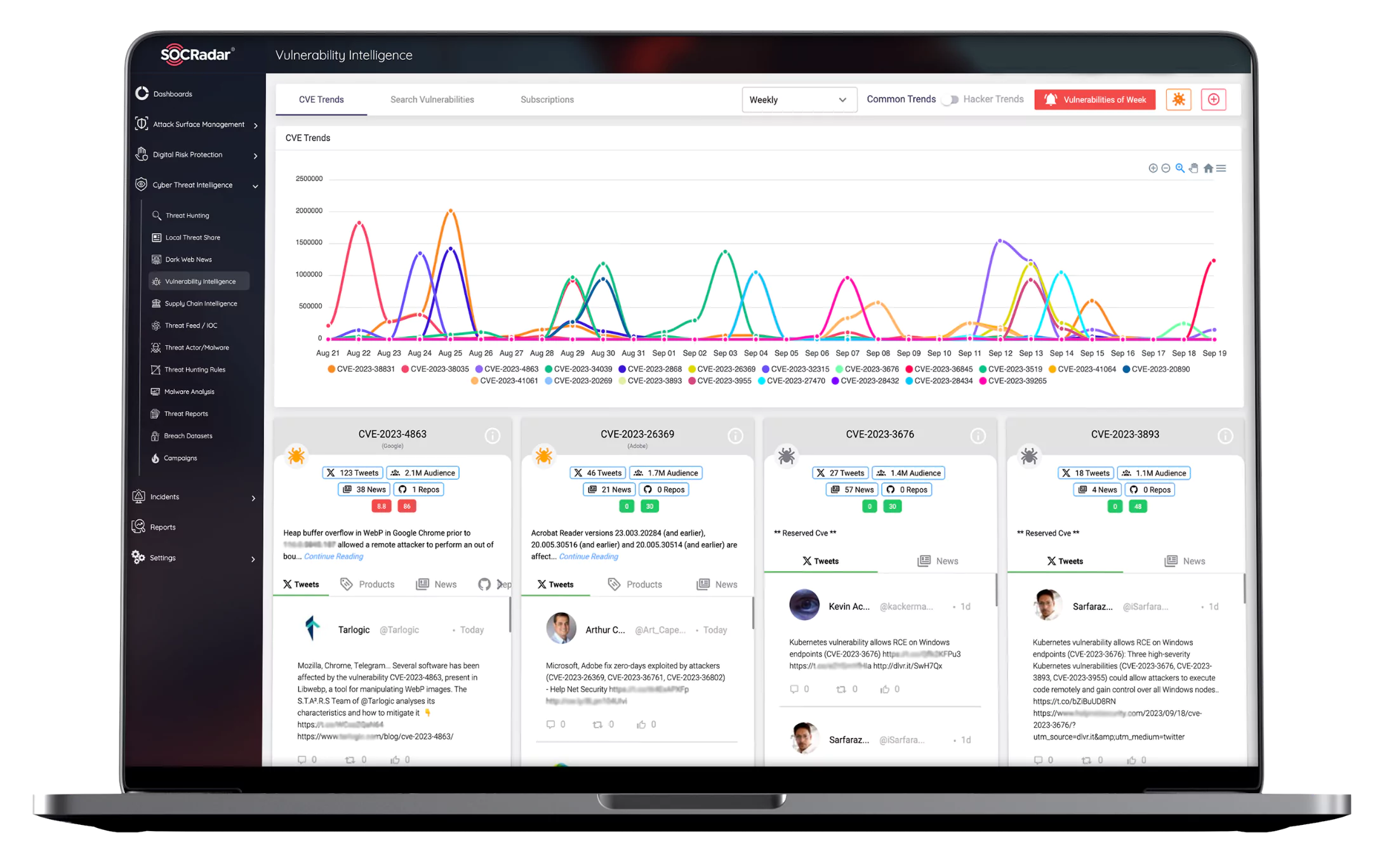
This is a contest against time! Research shows that threat actors scan for vulnerable endpoints within 15 minutes of a new CVE being publicly disclosed. Patching all the vulnerabilities discovered during scans is almost mission impossible. Therefore, security analysts need prioritization.
“Which vulnerability is more critical for my organization?” is an essential question and that is the exact point where SOCRadar vulnerability intelligence comes into play. Assigning risk rankings to each vulnerability throughout the entire digital footprint of an organization, SOCRadar provides security experts a comprehensive view on the real threats the organization faces, not a bunch of irrelative CVE lists.
See Threats Before They Strike
Visibility Into Dark Web
Gain in-depth and actionable threat intelligence to profile current and future threats.
Accelerate Investigation
Get fast, relevant and accurate results from the darkest parts of the internet.

Respond Quicker
Combat and mitigate identified threats by understanding adversarial capabilities.
Shed Light On APT Actors
Get essential insights into the latest activities of state-sponsored APT groups.
API-Ready Feeds
Consuming threat intelligence feeds by leveraging millions of data points in the wild.

Trends Visualization
Access vulnerability trends as well as auto-aggregated, customizable news.
Free Threat Intelligence for SOC Analysts
Contextualized Threat Intelligence is a game changer.


According to Gartner, “threat intelligence is evidence-based knowledge, including context, mechanism, indicators, implications, and actionable advice, about an existing or emerging menace or hazard to assets that can be used to inform decisions regarding the subject’s response to that menace or hazard”.
EC Council’s definition is very similar, “threat intelligence is the analysis of data using tools and techniques to generate meaningful information about existing or emerging threats targeting the organization that helps mitigate risks”.
Cyber threat intelligence aims to help institutions and organizations understand the risks of cyber attacks or cyber threats. These attacks can range from zero-day attacks, crypto viruses, APTs (Advanced Persistent Threats), botnets, or exploits. These threats are reported with the intelligence activities after being reviewed by CTI analysts to provide special protection methods to assist in an active defense in your organization.
The skilled, well-funded, well-organized, and highly-sophisticated cyber attackers use techniques that reveal security strategies to the technology alone. To develop a defense strategy against attackers, organizations need to know how hackers operate, how they function, and what techniques they use.
Cyber-threat intelligence allows companies to identify the dynamics and consequences of risks, improve security plans and structures, and reduce their attack potential to minimize damage and defend their network.
CTI can identify and analyze cyber threats against your business. Therefore, CTI can help you to:
- Focus on actionable alarms; the legacy threat intelligence solution provided only feeds and (Indicator of Compromise) IOCs, which were not actionable. But organizations started to need more and more of the latest intelligence about them. With real-time intelligence on threat actors, botnets, malware, and data from the dark web and the deep internet, organizations need to detect phishing domains targeting their customers.
- Collect, Verify, and Prioritize External Threats; CTI can deliver the hard work for your business with enriched intelligence that allows you to apply smarter defense and improvement processes.
- Detect Forgotten Assets and Monitor Attack Surface in Real-time; CTI can determine the blind spots by following the changing attack surface all the time.
- Prevent Data Loss; by using CTI, cyber threats can be detected, and security breaches can be prevented from disclosing confidential information.
Various threatening knowledge and theoretical approaches are useful at various businesses’ levels. The four categories of cyber threat intelligence have to do with different objectives:
- Strategic Cyber Threat Intelligence; It utilizes comprehensive pattern and emerging risk analysis to provide an outline of future cyber-attack implications.
- Operational Cyber Threat Intelligence; It is mainly used to make resource management decisions regarding actual and potential risks, historical resources, affiliations, and motives of threat actors.
- Tactical Cyber Threat Intelligence; Primarily, its main target is a technically trained audience and allows them to learn more specific details on threat actors’ tactics, techniques, and procedures (TTPs).
- Technical Cyber Threat Intelligence; It focuses on the technological details suggesting a cyber-security threat, such as phishing email lines or malicious URLs.
| Information | Intelligence |
| Unfiltered and raw data | Processed and sorted data |
| Not evaluated | Evaluated by Threat Intelligence Analysts |
| Too much-aggregated data | Only useful data |
| Not actionable | Actionable |
| Disconnected, incomplete, irrelevant | Connected, completed, and relevant |
Usually, cyber threat intelligence and cyber intelligence terms are used for the same meaning. But in theory, the two terms have different contexts.
CTI is the collection and revealing of threats that may harm business elements and security at any level to institutions and organizations. It is a type of intelligence that enables early measures to be taken by detecting the goals, methods, or types of attacks of the attackers as a result of analyzing the data collected and enriched from electronic media through a process.
CTI provides information on malicious actors, their tools, their infrastructure, and their methods for;
- Identifying types of attacks,
- Defining, guiding, and prioritizing operational requirements,
- Understanding threat actor capability, tactics, techniques, and procedures,
- Deploying detection systems,
- Developing defense strategies.
- Cyber intelligence (CI) translates the data obtained from the attackers’ networks into an operative report through “standard intelligence approaches.”
As can be understood from the definitions, while CTI focuses information on cyber threats, CI focuses on useful Intel from the Internet.