
SOCRadar Turkey Threat Landscape Report: ‘Skyrocketing Ransomware Threats in 2021’
Ransomware attacks are on the rise around the world. In 2021, we saw the names of various threat actors in the headlines. The revenue of 10 significant ransomware gangs that attack critical infrastructures reached $5.2 billion by 2021. Of course, this cyber-attack trend also reflected in the world was in Turkey. Due to their exposed attacks, global businesses operating in Turkey had to stop their business.
Ransomware attacks increased rapidly in the last three months of 2021. Threat intelligence experts agree that this increase has reached alarming proportions. Insights from SOCRadarDarkMirror show that attackers targeting critical verticals such as Manufacturing and Finance were operating three times more in December than in June.
Click the button to read the full report.
Ransomware Groups Most Targeting Turkey
According to the insights of SOCRadar DarkMirror, the 10 most targeted ransomware groups in Turkey are as follows:
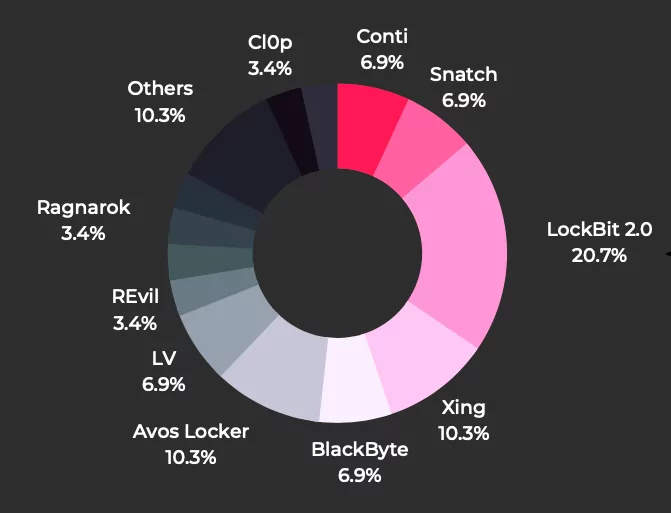
- LockBit 2.0
- Avos Locker
- Conti
- Snatch
- BlackByte
- LV
- REvil
- Ragnarok
- CI0p
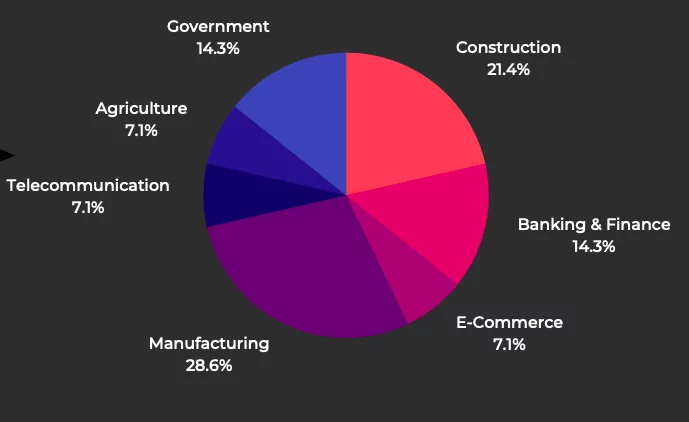
We said that the vertical threat actors targeted most in Turkey in 2021 is Manufacturing and Finance. However, activities of cybercrime gangs are observed not only in these sectors but also in areas such as construction, government, and telecommunication. You can see the distribution of targeted sectors in the chart below.
A Closer Look at the Big Three Ransomware Gangs
LockBit
LockBit, a ransomware-as-a-service operator, is renowned for designing the fastest and most functional lockers on the ransomware market.
Global energy company Schneider Electric, management consulting firm Accenture, and Bangkok Airways are among the group’s recent targets.
Conti
Conti, whose location is estimated to be outside Russia, also operates as a ransomware-as-a-service operator. The threat actors, which has carried out high-profile attacks on Turkish companies since its first appearance, targets critical areas such as the pharmaceutical industry.
The name of the threat actor means “star” in Mandarin. They are seen as derivatives of MountLocker and Avaddon ransomware. They use Enterprise Windows Active Directory APIs to worm through networks.
Other Threats and Critical Findings
- APT groups continued to target large organizations in Turkey in 2021 as well. They have openly expressed their interest in institutions and organizations from different sectors to derive financial benefits and collect valuable data.
New APT groups such as ChamelGang started to expand their spheres of influence in Turkey and neighboring countries. Especially the energy, public infrastructures, and finance sectors continue to attract these groups.
- A notable increase was observed in threat actors’ phishing activities towards new brands with digitalization in Turkey. SOCRadar has detected 42,136 phishing attacks targeting millions of consumers in the last 12 months. The bulk of these was to delivery, online retail, and banking apps.
- The critical vulnerability in Log4j 2 made many software and applications that depend on this library risky. Ransomware gangs such as Khonsari and APT groups can exploit this vulnerability and infiltrate internet-facing hosts, gaining access to misuse millions of valuable digital assets.
- Leaking credentials remains the most effective method of access. SOCRadar discovered more than 5 billion logins on dark web forums during 2021. Threat actors, such as ransomware gangs exploit networks by stealing digital identities.
- It may be necessary to run a global precaution mechanism against DDoS attacks. DDoS attacks can be devastating for any organization. To reduce these attacks, which negatively affect the internet ecosystem and cause financial losses, every actor should act upon a collective “risk-to-others” approach.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Try for free



































