
What Is Ransomware-as-a-Service (RaaS)?
While informing you about ransomware since the beginning of October, we talked about how lucrative “E-crime” has become. With this information in mind, it’s crucial to understand how malware progresses in “business” logic.
In this blog post, we will talk about Ransomware as a Service (RaaS), the benchmark for online criminal activity.
What Is Ransomware as a Service (RaaS)?
Ransomware as a Service is an illegal form of business that operators (i.e., the owner and developer of the malware) use to provide the following tools to their customers.
Depending on the contractual agreement, customers can choose to share some of the profits with the RaaS provider, keep the profit to themselves, or sign up for a pay-per-use plan that will provide access to updates, new malicious versions. In all respects, any RaaS can be considered a SaaS (Software as a Service).
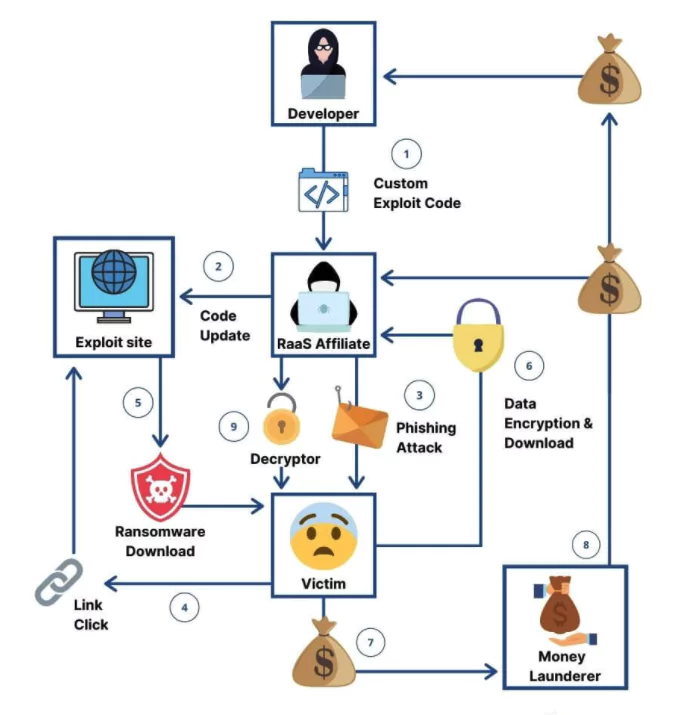
How Does the RaaS Business Model Work?
Since RaaS is not a transparent, clear-web service, monetization and customer relationships are not bound to any traditional rules. In other words, each RaaS operator has its business model. However, based on the observations made so far, all Ransomware-as-a-Service operators can be divided into four major categories:
Subscription-Based
Subscription-based services (e.g., Netflix, Dropbox, Salesforce, etc.), some RaaS operators can offer access to various types of ransomware-centric services in exchange for a flat fee, paid in Bitcoin or some other cryptocurrency. The customer can be charged at the end of each month or annually.
Other possibilities are readily available that the user can access with a password and username. Clipboard transactions can range from virtual wallet management to load customization to free products and more.
Affiliate-Based
RaaS operators running affiliate programs can claim a percentage of the profit. In return, the beneficiary will receive additional support, be granted access to paywall features or content, and receive state-specific tools and special codes.
Lifetime Licensing
Purchase-once-use-forever business model, some RaaS operators prefer selling fully licensed ransomware kits or malicious tools instead of relying on passive incomes generated by subscribers or affiliates. Off-the-shelf malicious tools are considerably more expensive compared to a subscription or enrolling in an affiliate program.
A lower ROI does not invalidate the advantages of one-time-purchase RaaS kits, since bookkeeping transparency is not a significant issue among RaaS operators. Making a one-time purchase might decrease the chances of the product being traced back to the beneficiary should the authorities catch the RaaS operator.
Partnership
The customer turns into partner-in-crime, splitting the spoils with the RaaS operator. Cuts greatly depend on how each factor contributes to the business.
Here Are the Some Examples of RaaS
1-DarkSide
DarkSide, whose name we have been talking about since the beginning of the month, is a RaaS operation associated with an e-crime group tracked by CrowdStrike as CARBON SPIDER.
DarkSide operators have traditionally focused on Windows machines and have recently switched to Linux, targeting enterprise environments running unpatched VMware ESXi hypervisors or stealing vCenter credentials.
As can be remembered from the Colonial Pipeline incident involving the DarkSide ransomware, it was reported that there were approximately 100 GB of data stolen. It was alleged that the organization paid a DarkSide affiliate about 5 million US dollars for this data.
2- Netwalker
Netwalker is probably the most profitable ransomware. Marketed by crime groups like Circus Spider and Mummy Spider, Netwalker has blackmailed both users and operators for over $ 20 million in just six months.
3- REvil
REvil was identified as the ransomware behind one of the immense ransom demands on record: $10 million. It is sold by criminal group PINCHY SPIDER, which sells RaaS under the affiliate model and typically takes 40% of the profits.
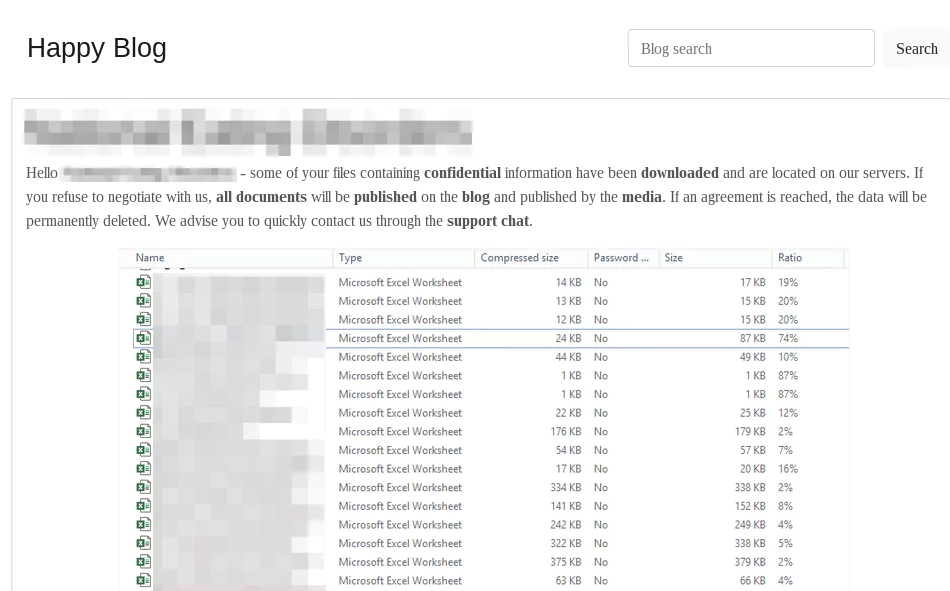
PINCHY SPIDER warns victims of the planned data leak, usually via a blog post on their DLS containing sample data as proof before releasing the bulk of the data after a given amount of time.
4- RaaSberry
RaaSberry manages to stage an outstanding performance when it comes to playing the role of the Good Samaritan. RaaSberry allows the customer to keep all revenue.
Compared to the competition, RaaSberry boasts several price tiers. A glance at their website shows that the cheapest packs are plastic.
According to the information in a blog post describing RaaSberry, the price is $60. You will receive a 250 kb EXE (packs both encrypter and decryptor), free support, multi-OS compatibility, and other features such as Task Manager Disabler, Mutex, and Delayed Start.
5- Dharma
Dharma ransomware attacks have been attributed to a financially motivated Iranian threat group. According to researchers, Dharma has been available on the dark web since 2016 and is mainly associated with remote desktop protocol (RDP) attacks. Attackers usually demand 1-5 bitcoins from targets across a wide range of industries.
Dharma is not centrally controlled, unlike REvil and other RaaS kits.
6- LockBit
In development since at least September 2019, LockBit is a RaaS advertised to Russian-speaking users or English speakers with a Russian-speaking guarantor.
In May 2020, an affiliate operating LockBit posted a data leak threat on a popular Russian crime forum:
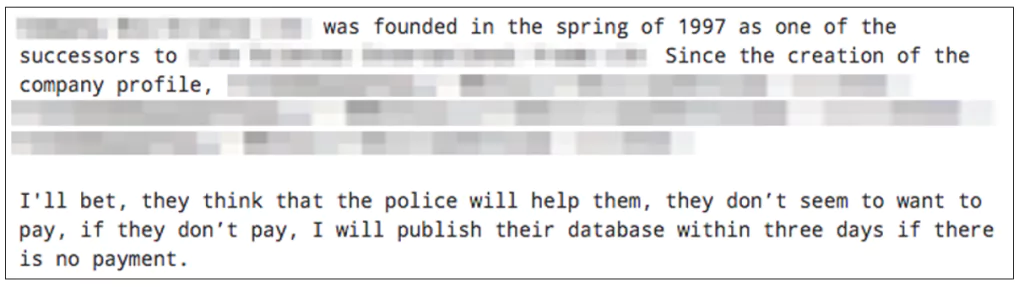
After the deadline has passed, the affiliate has been known to send a link to download the stolen victim data.
How To Prevent RaaS Attacks?
According to experts, RaaS is undoubtedly sophisticated but not infallible. The steps to prevent a RaaS attack are the same as any ransomware attack because RaaS is ransomware packaged for ease of use by anyone with malicious intent.
You can learn more about how to protect yourself from these attacks by reading our other blog posts on ransomware attacks on SOCRadar. Here are some of those steps:
- Implement reliable and modern endpoint protection that can run on advanced algorithms and run automatically in the background 24 hours a day.
- Make regular and frequent backups. Make multiple backups and store them on separate devices in different locations. Also, test backups regularly.
- Implement a rigorous patching schedule to avoid known and unknown vulnerabilities.
- Implement advanced phishing protection.
- Invest in user education in your company.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Try for free



































