
How Can You Detect Ransomware Attacks Using SOCRadar?
We continue to inform you about ransomware within the scope of Cyber Security Awareness Month. Today’s topic is “how SOCRadar tools can protect you against attacks?”
After ransomware attacks, victims are given instructions on how to pay to get the decryption key. The requested ransom fees are in cryptocurrencies, usually Bitcoin. The amount of the ransom can range from one hundred dollars to millions of dollars. Ransomware attacks affect institutions and individuals such as:
- Temporary or permanent loss of sensitive or private information
- Disruption of regular operations
- Financial losses incurred in restoring systems and files
- It has many adverse effects, such as loss of reputation.
While research shows that ransomware attackers do not have a sectoral selectivity regarding their targets, attackers are more focused on sectors where the targets will have to pay the ransom in high probability and will be done the most damage.
The manufacturing sector has the highest probability to attack. Public institutions, hospitals, and medical establishments are also among the primary targets of ransomware attacks, as they are likely to pay ransom due to their need for data, and systems are more vulnerable.
Which Methods Appeared More Frequently in Recent Attacks?
The most common method used in ransomware attacks is social engineering. However, with the pandemic process, ransomware attacks using RDP and zero-day vulnerabilities have also increased.
- Social engineering and phishing: Email phishing remains the top attack vector for ransomware campaigns because phishing emails are easy to send and provide a faster return on investment for attackers. As part of social engineering schemes, phishing allows the threat actor’s actions to occur undetected.
- Vulnerabilities/Vulnerabilities: Postponing updates to avoid risk business continuity leaves the door open to cyber attackers looking for an opportunity to infiltrate systems. For example, a known vulnerability (CVE-2019-19781) in Citrix systems has been exploited by many groups such as REvil, DoppelPaymer, Maze, CLOP.
- RDP: With the pandemic process, many employees’ transition from their workplaces to their homes increased the use of RDP by 41%. Due to the high increase in RDP usage, threat actors have changed their attack vectors to RDP. Some ransomware group attacks targeted compromised RDP endpoints in the first half of 2020; for example, Iranian cyber threat actors used RDP to spread the Dharma ransomware.
Biggest Cyberattack on Critical Infrastructure in the US
On May 7, a ransomware attack occurred in Texas on the Colonial Pipeline, an American oil pipeline system transporting gasoline and jet fuel to the southeastern United States. After the ransomware attack, Colonial Pipeline had to stop its full service. The attackers stole 100 gigabytes of data from the company in two hours. In coordination with the FBI, Colonial Pipeline paid the $4.4 million bitcoin ransom demanded hours after the attack. The statements made by the FBI and media outlets said that the threat actors called DarkSide were behind the attack.

American Airlines temporarily changed its flight schedules at Charlotte Douglas International Airport due to a lack of fuel caused by the pipeline shutdown. The Federal Motor Carrier Safety Administration issued a regional emergency statement for 17 states and Washington, DC on May 9 to keep fuel supply lines open. In this regard, it turned out how important ransomware attacks are for the states.
Highest Ransom Requested Attack in History
On July 2, 2021 (2 days before America’s Independence Day), at 23:00 (Turkey time), a malicious patch/update by the VSA servers of the US-based company Kaseya spread to the servers managed by Kaseya. This dissemination of malicious patches caused thousands of network nodes in hundreds of different businesses to be compromised and caused it to be encrypted.
This malicious hotfix contained a ransomware payload called Sodinokibi, known to be released by a notorious group called REvil, which caused the server and shared folders to be encrypted.
The REvil group, which held the highest ransom demand of all time with its attack on Acer (50 million dollars), increased its request by $ 20 million more to $ 70 million in this attack.
Kaseya Was Attacked For 0-Day
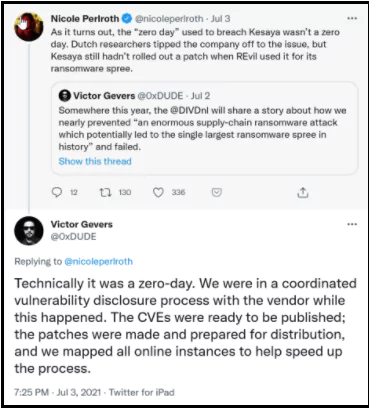
While the company was about to finish patching the 0-Day vulnerability, it discovered the exposure of the REvil group at the same time and used it in the attack. While the Dutch Institute for Vulnerability Disclosure (DIVDnl) and Kaseya were working to fix the 0-day vulnerability, it turned out that the REvil group exploited the same exposure.
As soon as the patch was ready to fix the vulnerability, the emergence of such an attack posed various questions like “Have they hijacked the communication between the DIVD.nl team and Kaseya?”
Based in America, Kaseya provides a cloud-based IT management software service for its customers, which allows remote management, monitoring, reporting, and patch management operations of tens of thousands of users from a single center.
Among the first reports of companies affected by the incident was Norwegian Financial software company Visma, which manages some Swedish supermarket chain Coop systems. Despite Kaseya being the fourth party vendor for Coop, the supermarket chain had to close 800 stores for almost a week. In addition, schools in New Zealand and SMEs in the USA were among the attack victims.
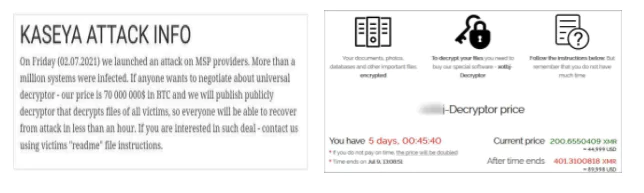
The statement of Kaseya on July 23 was announced that Kaseya bought a universal decryptor tool that helps its customers to get back the files.
Acer Suffered from a $50 Million Ransomware Attack
A $ 50 million ransomware attack was carried out against Taiwan-based technology giant Acer. In a statement made by the REvil group, the cyber-attack provided access to the company’s financial checks, bank account balances, and contact information for banks.
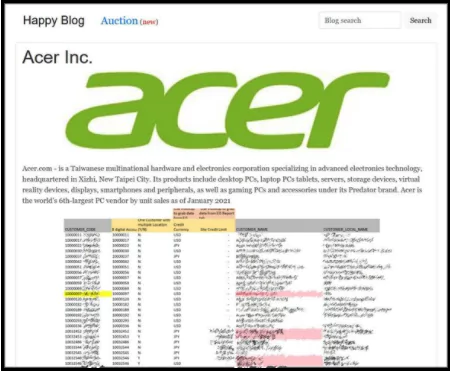
Also, the group shared screenshots on their page as evidence of the data they obtained.
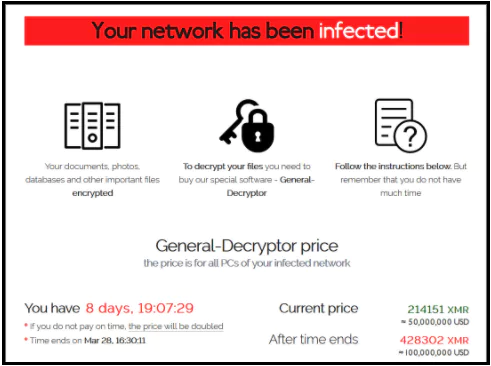
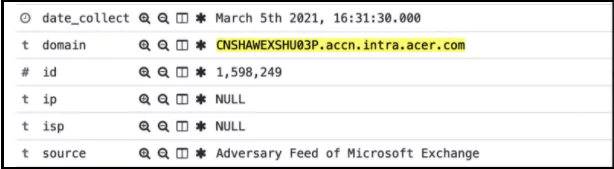
In the detection made by AdvIntel, it was shared that the attack was aimed at Acer’s Exchange Server. If the REvil group had exploited Microsoft Exchange’s vulnerability to steal data or encrypt devices, it would have been the first time they had used this attack vector.
However, Acer denied the attempted cyberattack. In its statement, Acer also stated that it is conducting detailed research on the systems related to the subject and that they do not share the details due to security measures.
How to Prevent Ransomware Attacks?
Dealing with the consequences of ransomware attacks is quite a challenge. Sending the ransom may seem like the only option to recover locked data. However, paying the ransom does not mean that your organization will get its affected data back. For these reasons, detecting an ongoing ransomware attack is not enough. It would help if you focused on preventing ransomware infection in the first place.
Step by step we can do to protect ourselves from ransomware attacks:
- Inventory your digital assets: To protect yourself against a ransomware infection, you first need to know what hardware and software assets are connected to the network.
- Customize your anti-spam settings properly and use powerful spam filters: Most ransomware is known to spread through glamorous emails with malicious attachments. That’s why you need powerful spam filters that can block such files from reaching users.
- Do not open suspicious-looking attachments: This explanation does not only apply to messages sent by people you do not know. It also applies to senders you believe are your acquaintances—the vast majority of ransomware attacks that originate from phishing result from obtaining the credentials of administrator-level employees.
- Avoid giving out personal information: Malicious people might target the ransomware to send a phishing email, and they need to get your information from somewhere. They can obtain it using OSINT techniques by reviewing your social media posts or public profiles for essential details.
- Use the Show File Extensions feature: This is useful when scammers use a confusing technique where a file appears to have two or more extensions.
- Patch your software and keep it up-to-date: In the absence of a patch, malicious people can exploit a vulnerability in your operating system, browser, antivirus tool, or other software programs with the help of an exploit kit.
- Authenticate email users: You should also use technologies such as SPF, DMARC, and DKIM to prevent malicious people from using email spoofing techniques.
- Install a browser plugin to block pop-ups: Pop-ups are a common entry point for attackers to launch ransomware attacks. That’s why you should look into installing browser add-ons to stop pop-ups in their tracks.
- Do not use unfamiliar media devices: Cyber attackers use a known attack method to compromise an organization’s supply chain and send Trojanized media devices. Do not use media devices that do not belong to you, such as a USB stick.
- Make sure you disable file sharing: You should disable file sharing so attackers can infect multiple machines in your environment. In the event of a ransomware attack, the malware will remain isolated on your device and will not spread to other assets.
- Backup Your Data: To prevent ransomware from destroying your data forever, you must have a recovery system. It’s best to create two backups: one should stay in a cloud, and the other should be stored physically
- Monitor the network for suspicious activity: No matter how you decide to organize your network, you need to watch out for threat behavior that could be indicative of a ransomware attack or security event. That’s why you need to use tools to monitor the network for suspicious activity
How to Use SOCRadar for Detecting Ransomware Attacks Early?
The cyber threat intelligence campaign strategic tactical operational service offered as SOCRadar Unified protects from ransomware attacks with the following items.
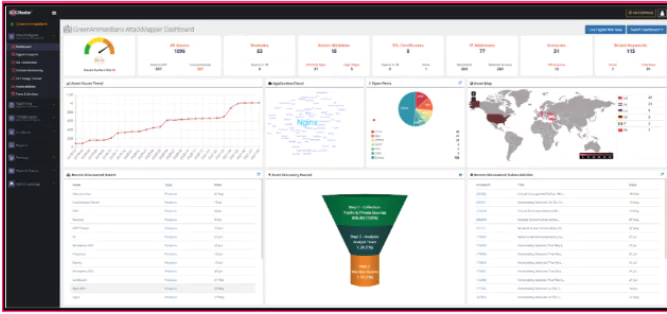
SOCRadar Attackmapper module prevents and quickly detects ransomware attacks by discovering and tracking your assets on the Internet:
- Making an inventory of digital assets open to the Internet,
- Critical port notification,
- 0-Day vulnerability detection,
SOCRadar RiskPrime Module provides the detection of intelligence information about your assets and your company:
- Creating alarms in possible situations by automatically tracking company domains in Dark and Deep web environments
- The HUMINT ability of SOCRadar dark web analysts allows your company to communicate with the threat actor to confirm the accuracy of up-to-date information and remove postings to increase the company’s reputation when necessary.
- Creating alarms in possible situations by automatically following the 3rd party companies providing services to your company in Dark and Deep web environments
SOCRadar ThreatFusion Module provides to detect intelligence on current cyber events:
- Vulnerability Tracking with internal/external systems and applications for vulnerabilities notifications,
- Integration of IOCs used by threat actors into security devices,
- Integration to detect and block phishing domains used by ransomware groups for phishing purposes,
- With the help of country-based and sector-based detections for ransomware attacks, sending threat-sharing notifications to companies that may be affected by these attacks can enable them to take action.
- Active monitoring of threat actors,
- Threat sharing about ransomware attacks actively informs security personnel.
- We are analyzing suspicious files with the Threat Analysis module.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Try for free


































