Brand Protection
Stay one step ahead of threat actors with actionable intelligence alerts.
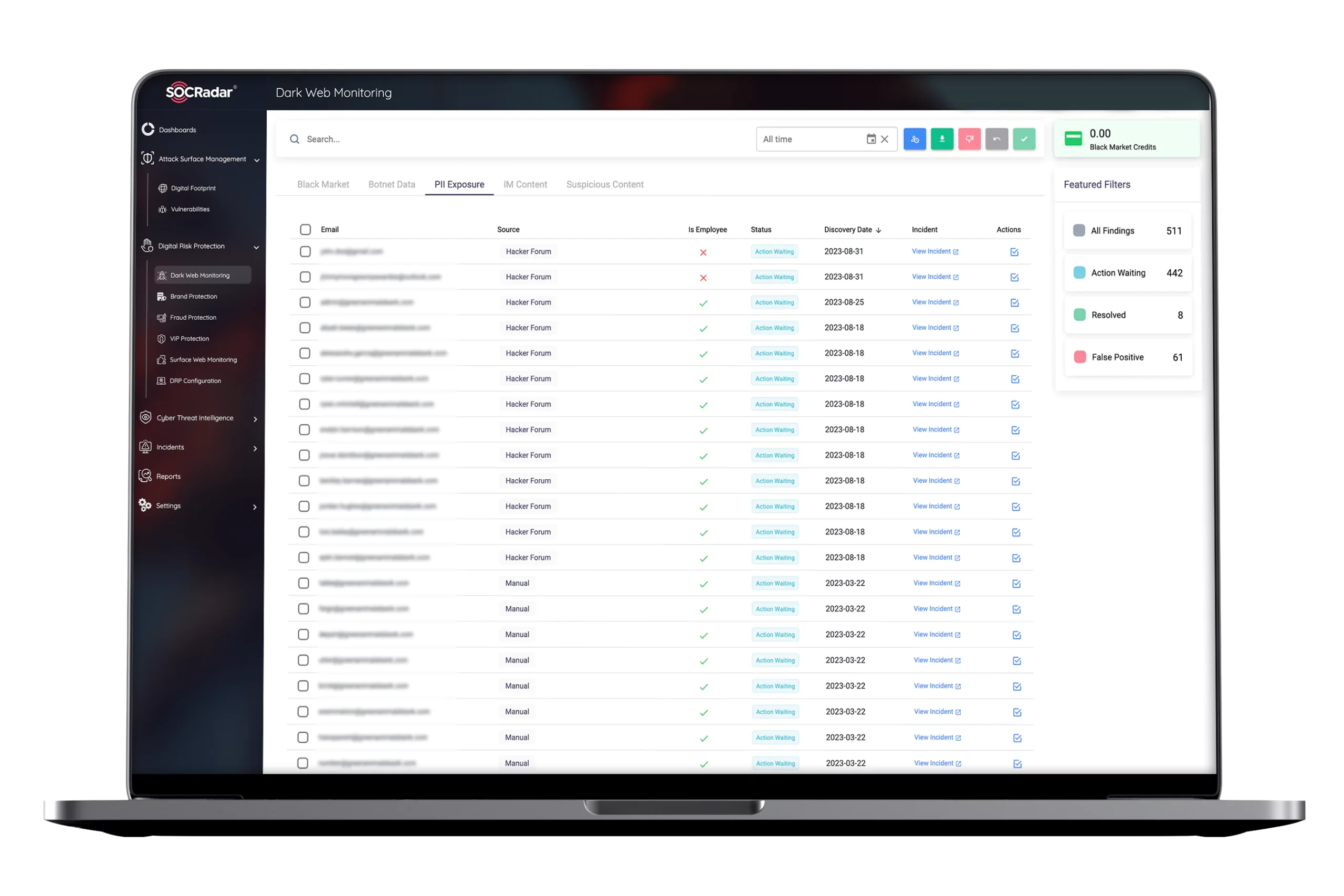
Empower your security teams for brand protection from being discredited, legal trouble, and your intellectual property falling into the hands of malicious actors. SOCRadar’s Brand Protection Services helps organizations check the exposure of their sensitive data by regularly monitoring the surface/dark web and other sources like Telegram channels.
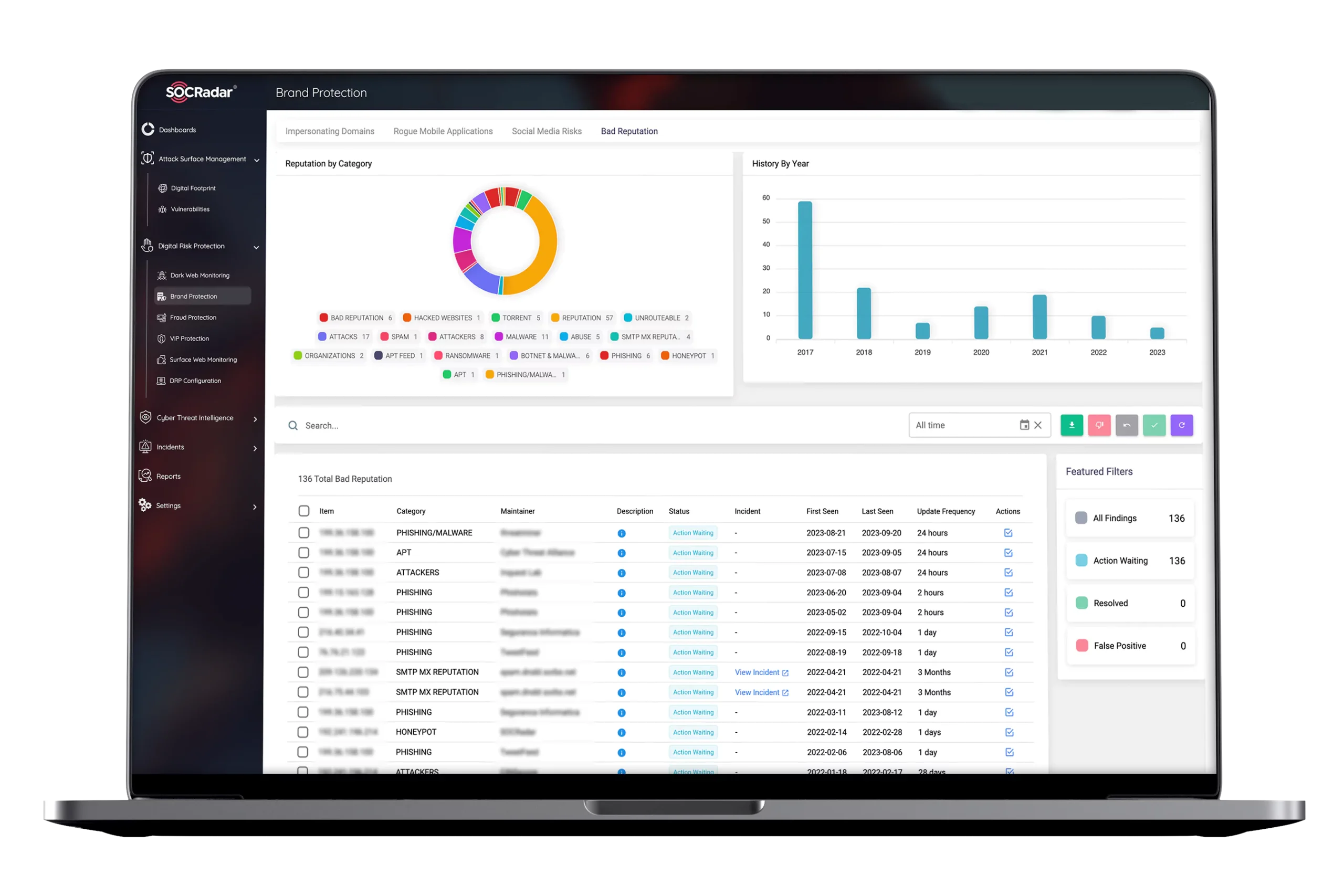
By automatically monitoring black markets, IRC channels, social media, hacker forums, cloud buckets, and more, SOCRadar’s Brand Protection Services always helps security teams stay informed about emerging threats, vulnerabilities, and supply chain risks.
SOCRadar Brand Protection (BP) Services proactively guard against phishing scams by detecting suspicious activities concerning your digital assets, identifying compromised credentials, and facilitating the takedown of fraudulent sites.
Learn more about how SOCRadar’s Brand Protection Services may help institutions learn about sensitive data sold on the dark web, source code or data leaks, compromised passwords, and data breaches.
Get a Digital Peace of Mind
Compromised Credentials Risk
Detect compromised credentials belonging to your employees and customers to prevent breaches.
Typosquatted Domain Risk
Identify new typosquatting, look-alike and phishing domains that impersonate your brands.
Proactive Credential Stuffing Protection
Empower your existing login security mechanisms to prevent hackers from stealing your customer’s trust.
Social Media Risks
Discover data leakages, mentions and discussions about your organization in real-time with.
Unknown Data Exposure Risks
Detects any piece of sensitive data belonging to your company across thousands of web sources.
Credit Card Fraud Risks
Enhance your credit card fraud prevention mechanisms with AI-powered intelligence at scale.
Rogue Mobile Apps
Prevents malicious intent to appear legitimate and performs unauthorized or harmful activities on a user's mobile device.
Individual modules used in Brand Protection
Brand Protection
SOCRadar’s Brand Protection is based on industry-leading instant phishing domain identification, internet-wide scanning, and compromised credential detection technologies by aggregating and correlating massive data points into actionable intelligence alerts.
It enables cybersecurity, fraud and risk management teams to swiftly and effectively understand how particular cyber threats have evolved through digital transformation and what to do for risk mitigation.


Brand Protection is a cybersecurity strategy that focuses on identifying, monitoring, and mitigating digital risks that can impact an organization’s information security and business operations. These risks can include data breaches, phishing threats, brand impersonation, data leakage, exposed credentials, cyber fraud, and many more.
BP involves the use of various tools and technologies to constantly scan the digital landscape — the web, social media platforms, deep and dark web, mobile apps, and other digital channels — for potential risks to an organization’s digital assets.
As businesses continue to expand their digital footprint, they expose themselves to increased risk. BP helps businesses proactively identify and manage these risks, protect their reputation, maintain customer trust, and avoid potential regulatory fines.
Key aspects of BP include Data Leakage Protection, Identity Protection, Vulnerability Management, and Compliance Monitoring.
Brand Protection tools constantly monitor various online platforms for potential data leaks or exposure. They alert organizations to these leaks so they can be fixed before they’re exploited.
Yes, BP can help ensure that a company is following all necessary regulations related to data protection and privacy by constantly monitoring the organization’s digital landscape and alerting them to any potential compliance issues.
Brand Protection (BP) platforms gather and analyze information about potential threats that could harm the organization’s digital assets. This intelligence is then used to strengthen the organization’s cybersecurity defenses.
While traditional cybersecurity measures focus on securing an organization’s internal IT infrastructure, BP focuses on the broader digital landscape, including the web, social media platforms, mobile apps, and even the deep and dark web. BP provides a more holistic approach to cybersecurity by considering all aspects of an organization’s digital presence.