
Dark Web Profile: AvosLocker Ransomware
AvosLocker was first detected in 2021, and it usually appears as ransomware targeting Windows systems. After a variant targeting Linux environments emerged, striking attacks began to occur. The group, which operates as a ransomware-as-a-service (RaaS), claims to offer the “fastest service on the market.”
AvosLocker Targets Critical Infrastructure

AvosLocker has a wide range of victims, from retail companies in Asia to educational institutes in the Middle East. In the FBI’sadvisory dated March 17, 2022, it is stated that the group targets victims explicitly from the USA’s Financial Services, Manufacturing, and Government Facilities sectors.
AvosLocker’s Tactics, Techniques, and Procedures
The group steals the victim’s files, encrypting them and demanding a ransom. It uses email campaigns to deliver malicious files. After obtaining RDP access, it replaces the files on the victim’s server with the extensions “.avos,” “.avos2,” or “.avoslinux.” Then leaves the ransom note “GET_YOUR_FILES_BACK.txt” linked to the “.onion” payment site.
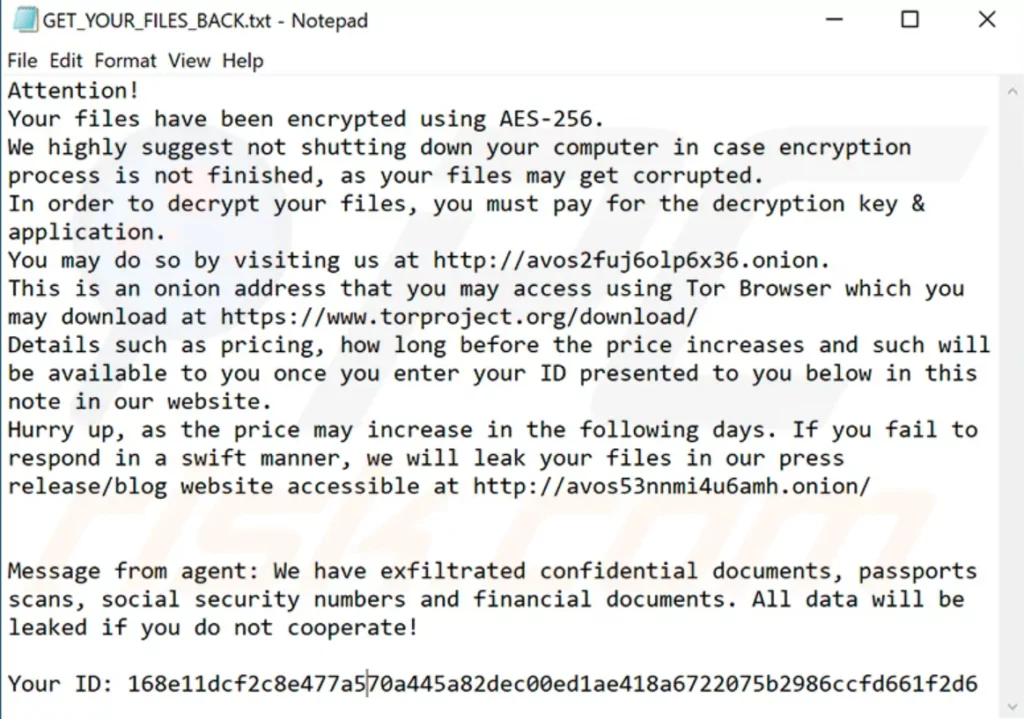
The ransomware gang threatens the victims to leak and sell their data in its own leak site if they do not agree to pay the ransom. They get offers by showing previews of stolen data to those who want it.
AvosLocker Malware IoCs
The FBI includes a list of IoCs of AvosLocker in its latest report. In the report, modifying Windows Registry ‘Run’ keys and scheduled tasks are counted among IoCs.
Other tools used in ransomware attacks are as follows:
- Cobalt Strike
- Encoded PowerShell scripts
- PuTTY Secure Copy client tool “pscp.exe.”
- clone
- AnyDesk
- Scanner
- Advanced IP Scanner
- WinLister
Vulnerabilities Exploited by AvosLocker
According to the FBI report, many victims report Microsoft Exchange Server vulnerabilities as an intrusion vector. In addition, specific vulnerabilities are also observed to be exploited by the group. CVE-2021-31207, CVE-2021-34523, and CVE-2021-34473 Proxy Shell vulnerabilities and CVE-2021-26855 are some of them.
How Can SOCRadar Help Avoiding Ransomware?
SOCRadar Threat Feed provides information about ransomware, APT groups, malware, and IoCs with its AI-supported intelligence system compiled from different feed sources. You get a proactive cybersecurity understanding against ransomware like AvosLocker and more.
You can start getting the information right away by subscribing to our free DarkMirror service.

Vulnerability exploitation is one of the most common invasion methods threat actors use. Therefore, it is essential to detect a vulnerability as early as possible and take necessary precautions. With SOCRadar Vulnerability Intelligence, you can be instantly notified when a critical vulnerability or exploit impacts your products and technologies.
See which vulnerabilities threat actors are actively exploiting and turn your insights into action.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Get free access


































