
How to Stop a DDoS Attack? (2023 Edition)
What is a DDoS Attack?
A DDoS attack, also known as distributed denial of service attack, is a type of web attack aiming to cripple a web system’s servers and make the servers unreachable to users. Web servers are typically designed according to the system’s estimated user count, process volume, and maximum number of instant requests. In a DDoS attack, the aim is to flood the server with requests from numerous devices far above the maximum process volume a server can handle; so that the server becomes temporarily unavailable, or in some cases, permanently.
DDoS Attack as a Growing Threat
DDoS attacks have become more complex, volumetric, and frequent over the last decade than ever. Not only are they increasing in attack traffic volume, but they also threaten even small organizations. Internet Service Providers, as well as Cloud Providers, are reporting thousands of attacks every day. With the increasing usage of 5G technologies with billions of IoT devices, the average volume of the attacks can be projected to grow.
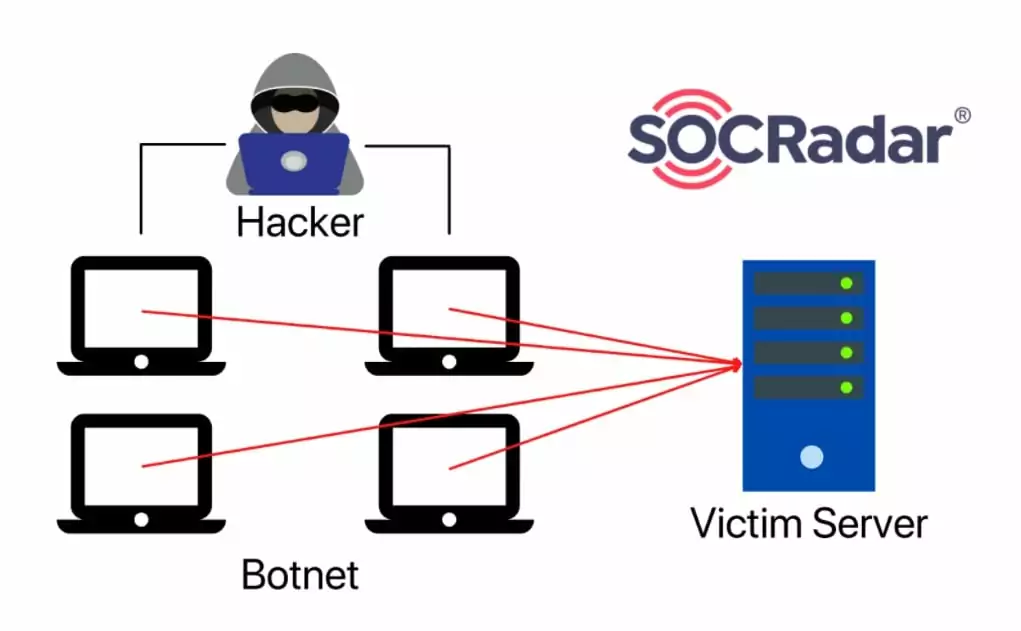
Botnets are Commonly Used in DDoS Attacks
To load a web server with a high amount of requests, threat actors utilize botnets: networks consisting of enslaved devices controlled by the threat actor. Botnets have various uses, such as crypto-mining, web crawling, and in our case, DDoS attacks. Since there are tens of thousands of compromised devices in some botnets, threat actors can easily exceed the maximum traffic a web server can handle and make the server inaccessible.
Record-Breaking DDoS Attack
In October 2021, Microsoft announced that one of its Azure customers in Europe had experienced a DDoS attack with an incredibly high attack volume. The attack volume was 2.4Tbps, breaking the highest volume DDoS attack record. The DDoS attack lasted for about 10 minutes.
Microsoft also states that the attack came from about 70.000 devices located in Asia-Pacific.
This example of a DDoS attack shows us that threat actors utilize botnets to reach incredibly high attack volumes, resulting in hard to mitigate DDoS attacks.
What are Types of DDoS Attacks?
DDoS attacks can be divided into three main types.

Volume Based Attacks
Volume-based attacks target the network (3) layer and the OSI model’s transport (4) layer.
In a volume-based attack, the aim is to create extreme traffic to a server and exceed the bandwidth of the server. UDP floods and ICMP floods are counted as volume-based DDoS attacks.
Application Layer (Layer 7) Attacks
As the name suggests, application-layer attacks target the seventh layer of the OSI model, the application layer.
In this attack type, the threat actor targets specific components of the highest layer. Since requests in this layer consume more server and network resources, application-layer attacks can be quite deadly and hard to mitigate.
Application layer attacks are stealthier than other types of DDoS attacks since they resemble real web traffic. Examples of seventh layer attacks include HTTP GET and HTTP POST floods and low-and-slow attacks.
Protocol Attacks
The third main type of DDoS attack is called Protocol Attacks, also known as state-exhaustion attacks. The goal in these types of attacks is to consume the network resources of a server and exhaust additional network equipment such as firewalls and server load balancers.
The most common attack in this category is the SYN Flood, and although they are deprecated and no longer pose a threat, smurf attacks and ping of death attacks also fall into this category.
Most Common DDoS Attack Vectors and Mitigation Methods
UDP Flood
According to Azure’s 2020 Q1 and Q2 DDoS reports, UDP Flood is the most common attack vector in DDoS attacks.
Source:https://azure.microsoft.com/en-us/blog/azure-ddos-protection-2021-q1-and-q2-ddos-attack-trends
The reason behind its popularity is that no connection is required while sending UDP (User Datagram Protocol) packages, and generating and sending UDP packages can easily be achieved through many programming languages.
This attack is a volume-based attack, and the goal is to overwhelm the server so that it cannot process incoming packages and respond to them.
Potential mitigation for the UDP Flood is that some servers set a maximum response rate to incoming packages. Even though this mitigation has downsides, such as legitimate traffic packages can be unanswered during a UDP Flood attack, it effectively protects the server against UDP Flood attacks and keeps network resources from running out.
SYN Flood
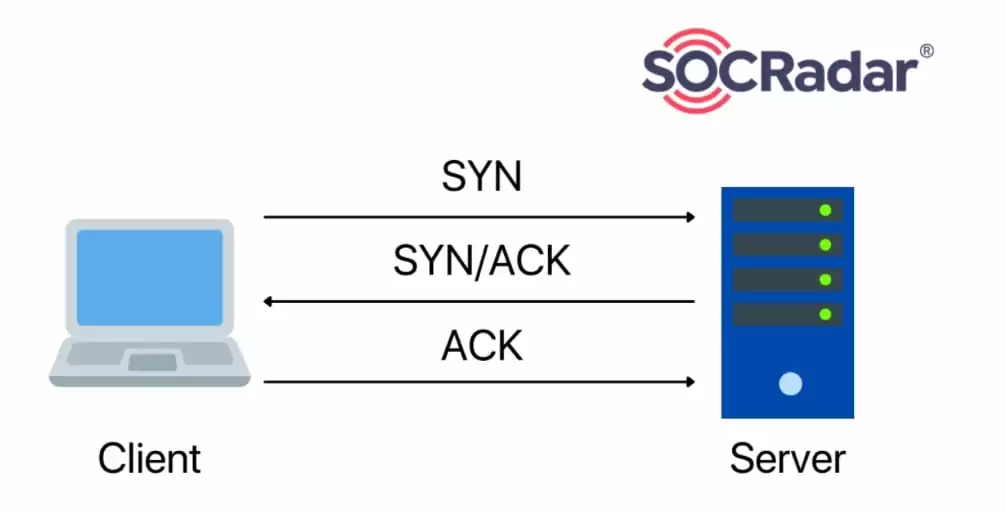
Also known as TCP Flood or half-open attack, SYN Flood attack vector exploits the infrastructure of the three-way handshake principle.
In a three-way handshake, the user sends an SYN package, and when the server receives the SYN package, the server sends an SYN-ACK package back to the user. After the SYN-ACK package, the user will send an ACK package to confirm the connection, and the three-way handshake protocol will be completed.
During an SYN Flood attack, the threat actor will send SYN packages from numerous devices, but after all these devices receive SYN-ACK packages from the server, they will not respond. As a result, all these incomplete connections will take up memory in the server, denying new connections from being made.
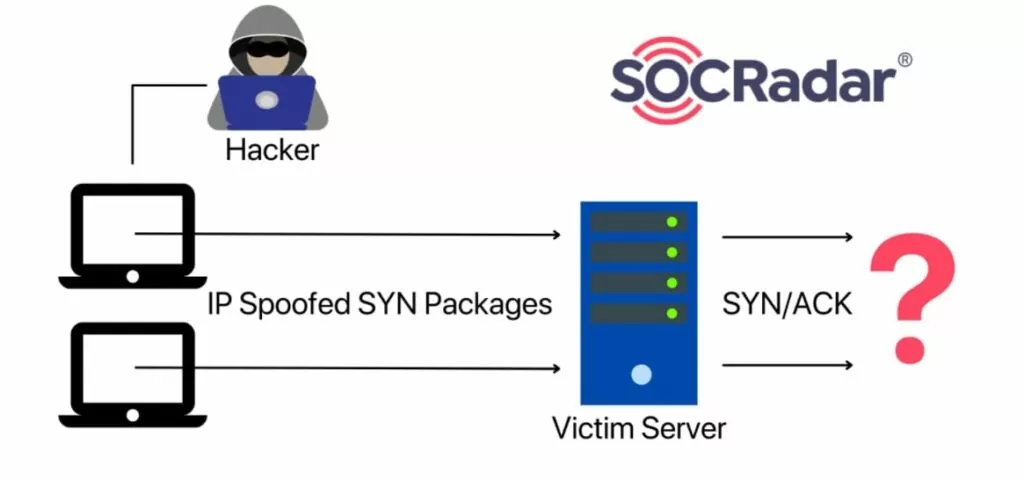
To mitigate SYN Flood attacks, servers implement different techniques such as limiting the maximum number of half-open connections and reserving memory to increase the limit when required or overwriting the longest half-open connection with a new one when the maximum number of half-open connections is reached.
ICMP (Ping) Flood
ICMP (Internet Control Message Protocol) packages are packets that are primarily used for error messaging and generally do not convey data between the server and the client.
Like the UDP Flood attack, ICMP Flood utilizes a high-volume DDoS tactic to interrupt the target server. The aim is to load the target server with ICMP packages in order to consume network and server resources. As a result, the server will be overwhelmed, and it will become unable to respond to legitimate traffic.
HTTP Flood
HTTP Flood attacks use HTTP GET and POST requests to flood the target server.
Targeting the seventh layer of the OSI model, the HTTP Flood attack can be very dangerous since HTTP requests are legitimate traffic, so noticing and blocking an HTTP Flood attack is more challenging than other types of DDoS attacks.
Like other DDoS attack vectors, the HTTP Flood attack aims to overwhelm the target server with packages and interrupt its operations.
Since the number of different types of HTTP requests is limitless, this attack can be very simple to very complex, depending on the contents of the HTTP packages.
Potential Impacts of DDoS Attacks
DDoS attacks could have many consequences for a company and might damage the company in different ways.
Some possible consequences of DDoS attacks are listed below.
- Money: During a DDoS attack, the company’s servers will be down, unable to make a profit.
- Time: Recovering from a DDoS attack could take hours, days, or even weeks.
- Reputation: Being the subject of a DDoS attack could damage a company’s reputation in the client’s eyes.
How to Mitigate
A layered and hybrid approach can help you mitigate DDoS attacks. Following is a list of technologies and providers to leverage to keep your internet-facing systems accessible and avoid business interruptions.
Internet service providers (ISPs): ISPs limit the network bandwidth of your servers to stop DDoS attacks. If a large amount of traffic is detected, ISPs block all incoming traffic quickly. Even though the server is unreachable during the attack, there is no aftermath of the attack because the DDoS attack never actually happened.
Content delivery networks (CDNs): Content delivery networks are networks of servers scattered worldwide aiming to distribute the load off an original server. CDNs can handle high volumes of traffic and help companies mitigate DDoS attacks.
Web application firewalls (WAFs): Web application firewalls filter and monitor HTTP requests of a server, and they provide effective mitigations against Application layer (Layer 7) attacks.
Cloud scrubbing centers (CSCs): Cloud scrubbing centers operate in the external layer, and they are responsible for filtering and cleansing the incoming traffic before it reaches the target server.
On-premises appliances: On-premises appliance solutions offer advanced protection against DDoS attacks designed to bypass security solutions operating in the external layer.
DNS protection: DNS protection solutions also filter and monitor incoming queries and detect malicious DDoS packets to protect servers from DDoS attacks.
Native cloud providers: Native cloud providers offer cloud-based servers with high traffic handling capabilities and accelerated traffic features. Popular cloud providers such as Cloudflare states that cloud providers provide effective solutions against DDoS attacks.
These technologies can be categorized into three layers:
- The external layer consists of cloud scrubbing centers, content delivery networks, DNS protection solutions, and Internet service provider services. The external layer is responsible for handling, monitoring, and filtering the incoming traffic before it reaches the main servers.
- The perimeter layer is specific to on-premises solutions. The security solutions in this layer provide extensive protection against DDoS attacks able to circumvent the external layer of your network.
- The internal layer consists of WAFs inside your network. It offers protection against application layer (Layer 7) attacks by filtering HTTP GET/POST requests aiming to exploit specific components of your servers.
How to Protect Your Organization from a DDoS Attack?
SOCRadar analysts suggest you,
- Implement an effective detection and analysis solution to identify DDoS attacks quickly.
- Be ready to implement a fast incident response solution in case of a DDoS attack.
- Acquire a firewall solution to protect your organization.
- Tweak your firewall to apply specific mitigations against individual types of DDoS attacks.
- Cleverly route your traffic to mitigate the damage in case of flooding.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Get free access

































