
How to Prevent Credential Stuffing Attacks?
We continuously come across the news about recently uncovered credential data breaches but rarely hear about the direct results of any particular breach. Since it can take a long time before the data get purchased and utilized in crimes, and even so, the connection between the data breach and its consequences is hard to observe. Here is how data breaches could threaten businesses through credential stuffing attacks and how to neutralize this threat.
What is Credential Stuffing?
Credential stuffing is a cyberattack type in which an attacker utilizes the pre-collected account credentials from one online platform to steal accounts at another platform. After breaking into an account, cybercriminals can access valuable information, including personally identifiable information (PII) and financial information like credit card numbers, to perform identity theft and financial fraud.
There has been a sharp increase in credential stuffing attacks in recent years. Plus, in the first week of January, the Attorney General Office of the New York State released conclusions of an investigation of credential stuffing attacks, indicating that 1.1 million individual accounts had been compromised. The investigation concentrated on online services connected to seventeen major businesses ranging from online retail firms to food delivery services.
Credential stuffing is a concept confused with credential dumping and credential harvesting. However, credential dumping and credential harvesting are methods for collecting login details, while credential stuffing is a form of cyberattack using these previously collected credentials.
How Does Credential Stuffing Work?
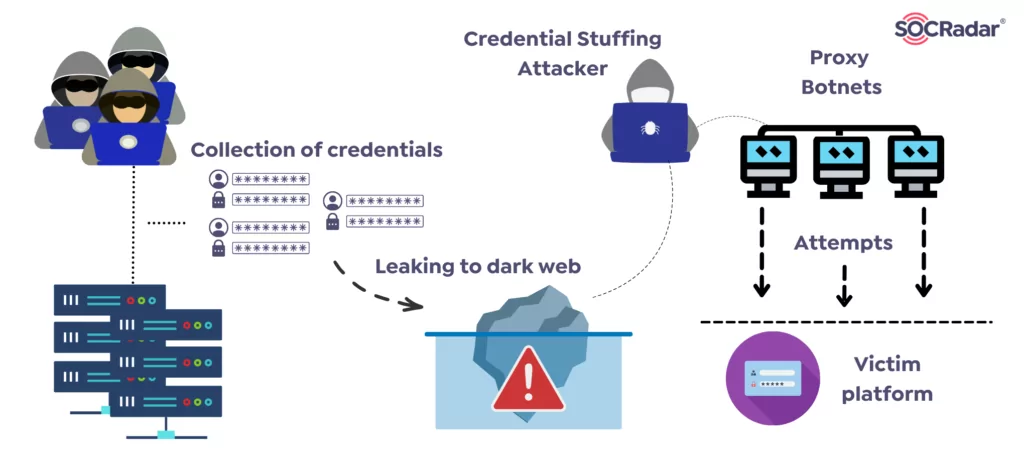
From a technical point of view, credential stuffing attacks can be performed manually by literally attempting to log in with the stolen account credentials on different online platforms. However, cybercriminals do not want to spend much time on that manually. Usually, these attacks are carried out through an automated tool distributing requests across various IP addresses and locations, which takes the form of a botnet. These credential stuffing tools such as OpenBullet scripts are being sold on the dark web for prices as low as ten dollars, allowing anyone without technical skills to carry out such an attack.
According to a Google survey, 65% of internet users reuse credentials across multiple online applications, leaving businesses vulnerable to credential stuffing attacks even if their site and their customers’ credentials have not been compromised per se.
How To Prevent Credential Stuffing?
The unfortunate tendency of reusing passwords causes organizations to be more vulnerable. However, there are several ways for businesses to ensure attackers cannot use pre-collected credentials to access their users’ and employees’ accounts and mitigate the impacts of credential stuffing attacks.
1- Using unique passwords
The first method to prevent risks of credential stuffing is to use unique passwords for each platform. An average person has more than a hundred login accounts. Creating and memorizing different passwords for each account is very hard. Nevertheless, without the necessity of technology, generating an unlimited number of unique and robust passwords is possible without memorizing them by creating an individual encryption rule for passwords. Another alternative is using a password tool like 1password, which creates and stores unique and complex passwords for the user.
2- Acquiring a web application and API protection platform (WAAP)
In credential stuffing attacks, the same IP addresses repeatedly send requests to log in for various accounts, resulting in an abnormal situation for the IP addresses. Web application firewalls (WAFs) detect anomalous traffic from botnets. Despite not being mainly designed to prevent credential stuffing, a high-skilled WAF can catch suspicious login attempts, especially when a significant number of attempts occur in a moment. Besides stopping credential stuffing, Web Application and API Protection (WAAP) solutions are the preferred choices for protecting the key internet-facing web services.
3- Limiting authentication requests
Threat actors aware of WAFs and similar mitigations deploy the credential stuffing attack from various residential IP addresses, locations, and devices. Therefore financial organizations are rigorous on this. Many permit up to three or five failed login requests before freezing the account, regardless of IP address, location, or device.
Freezing the account may appear too extreme for other platforms, but restricting the login requests within a particular time frame reduces the speed of cyberattacks. For service providers, sending emails to warn the user about the failed login requests might be critically essential. Thus, users can instantly reset their passwords and use the platform safer.
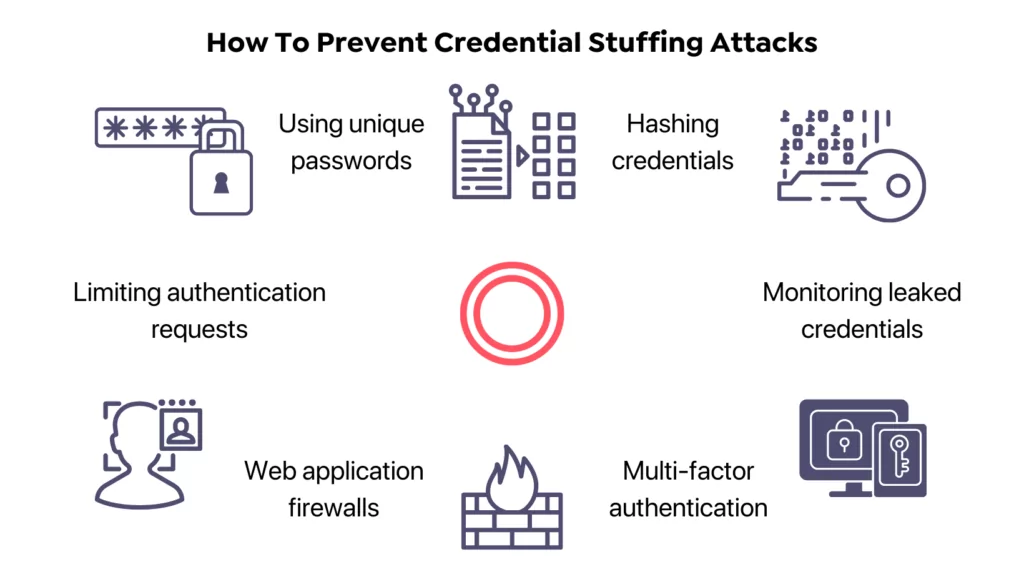
4- Hashing credentials
In theory, hashing involves encrypting and storing passwords to prevent cybercriminals from using passwords directly if they steal them. However, in practice, password hashing is not uncrackable entirely. Hackers could reach actual passwords by using different decryption techniques.
The strength of the hash determines how much time users would have to reset their passwords after a data breach. While using the SHA1 hashing algorithm does not pose a challenge for hackers, they have difficulty with passwords stored through the bcrypt hashing algorithm. So even though hashing passwords can not stop a credential stuffing attack, it can put a limit on what a cybercriminal can do with those passwords.
5- Multi-factor authentication for identity-related risk-reduction
The best defense method against password-related attacks is multi-factor authentication (MFA). It might be beneficial that system providers implement wherever practicable, depending on the platform’s users, it may not be suitable or possible to enforce the MFA. To create a balance between usability and protection, other techniques can combine to multi-factor authentication to make 2nd factor enforced for typical situations such as logins from:
- An IP address on blocklists.
- A login attempt that appears to be automated
- An unusual country or location.
- A new browser/device or IP address.
- An IP address trying to authorize multiple accounts.
6- Monitoring for leaked credentials
Organizations could prefer solutions that automatically scan some login credentials or directly domain names against an extensive database of stolen credentials leaked on the dark web. In this alternative, the user or the employee whose password is published can be warned instantly if their login information matches those in the database. If a match is detected, the victim user or employee should immediately reset all their passwords similar to the compromised password to prevent credential stuffing.
SOCRadar offers a unique way to monitor credentials published on the dark web. SOCRadar tracks dark web forums, telegram channels, and similar environments where cybercriminals might share the credential databases. Using SOCRadar Labs, you can reach a deep web report for your domain.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Get free access


































