
Lapsus$ Group Allegedly Breached Okta After Microsoft Source Code Leak
The Lapsus$ group has announced that they are responsible for authentication service provider Okta’s digital breach. Threat actors posted screenshots on their Telegram channel, showing the internal system.
Cyber security experts think that the attack on Okta could have enormous consequences. The company has over 15,000 customers.
What Happened?
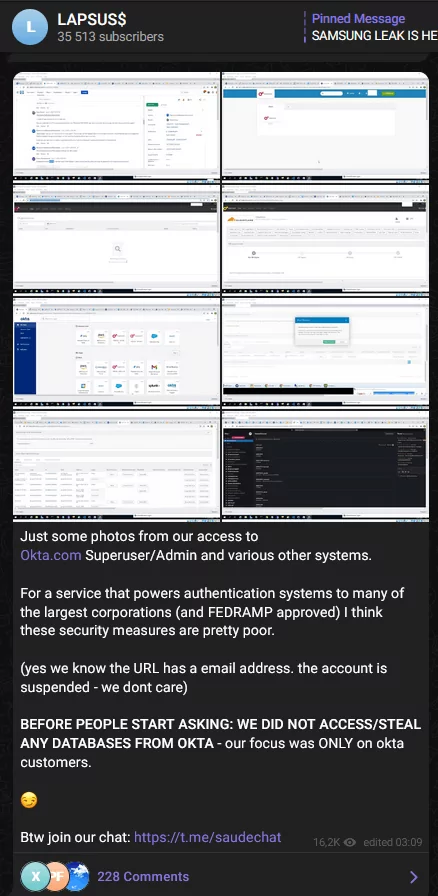
In a post published on a Lapsus$ Telegram channel and subsequently on SOCRadar Analysts on March 22, 2022, the group claimed that they had achieved “superuser” status on Okta.com and related systems.
In the same statement, the threat actors, who say they focus on “Okta customers only,” may have gained unauthorized access to the information of millions of users around the world.
An Overview of the Okta Breach
Okta helps companies authenticate apps, and developers create authentication services to apps, web services, and devices. This is an important clue as to how far-reaching the breach could be.
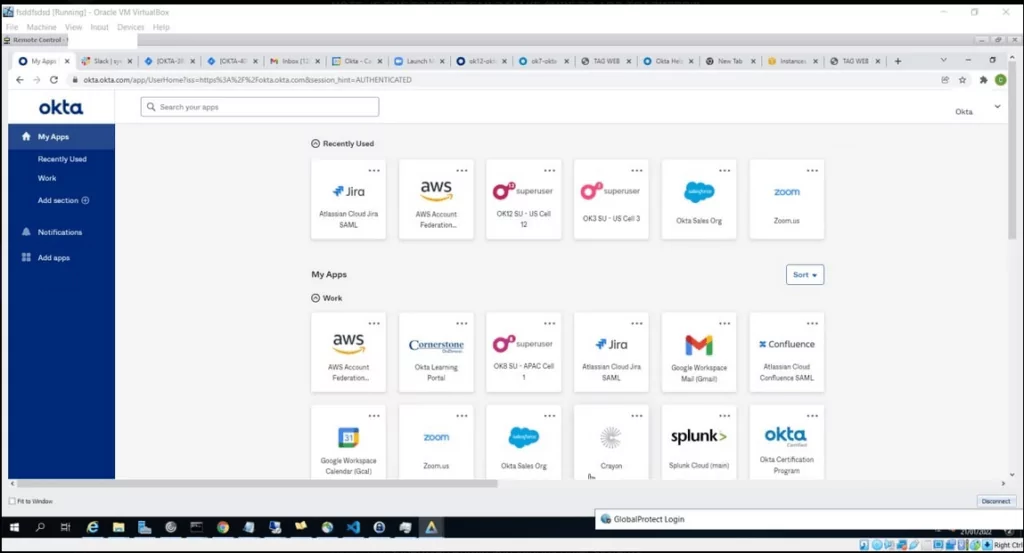
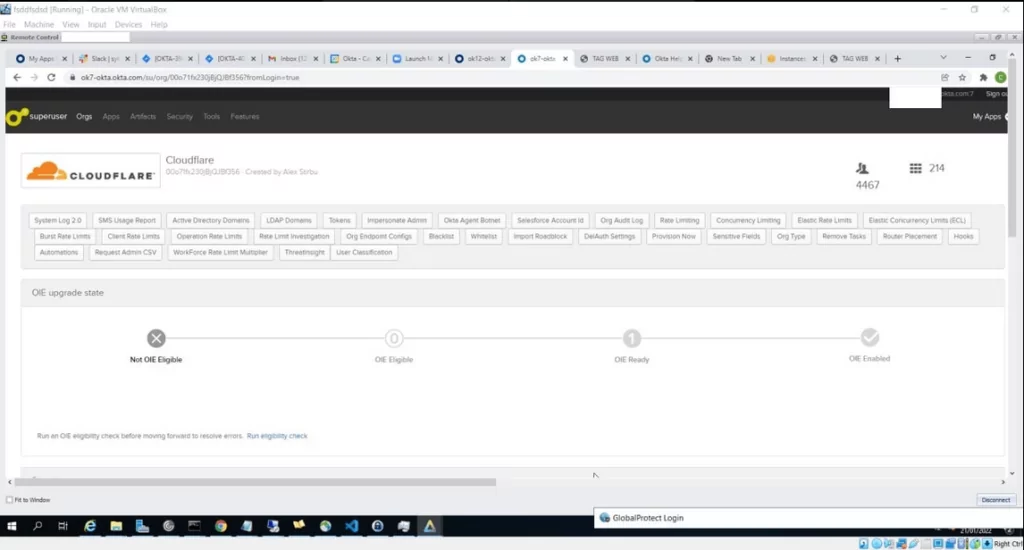
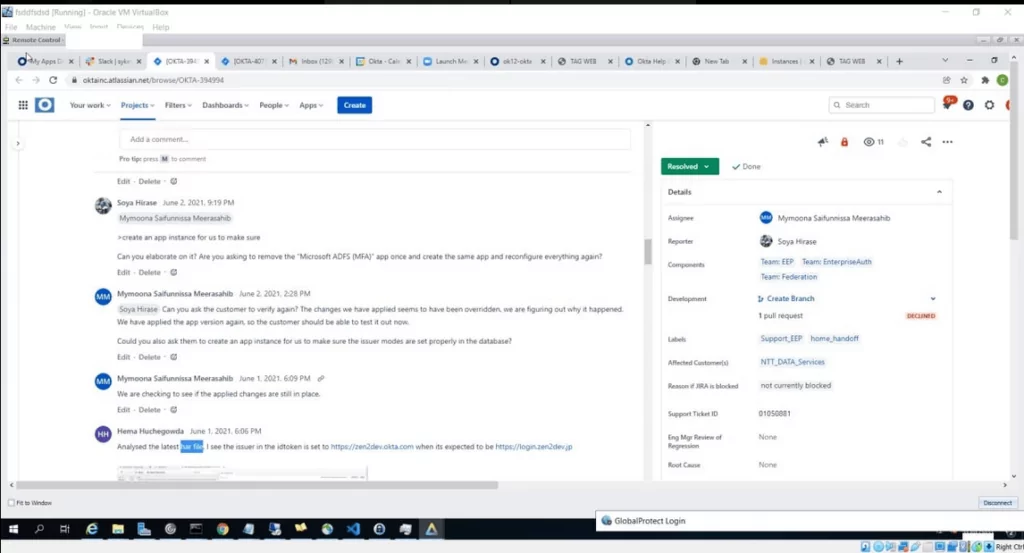
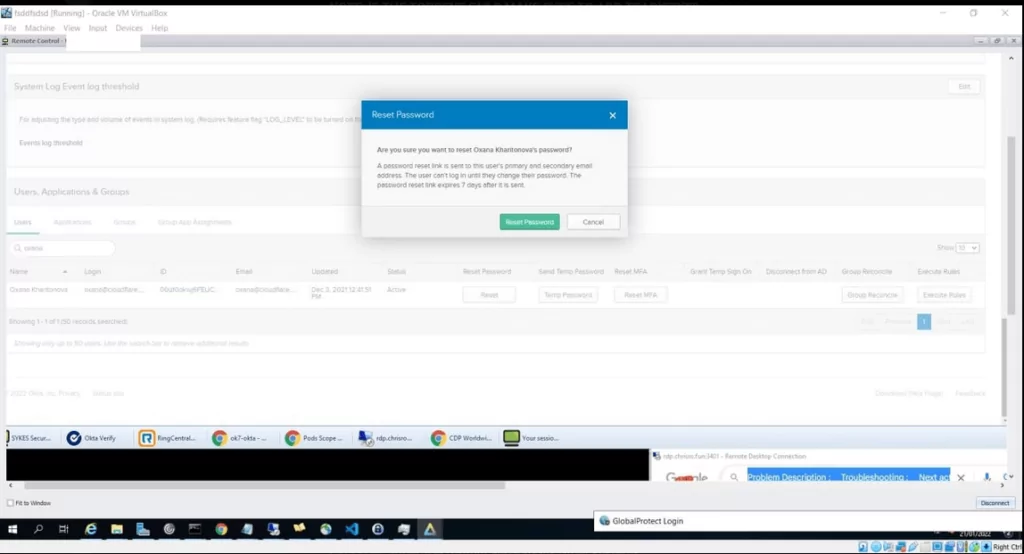
Screenshots shared by Lapsus$ confirm the concerns. According to these, threat actors have accessed the “superuser” account, which provides access to apps Okta uses, such as AWS, Zoom, Jira, Crayon, Slack.
Okta confirmed the Lapsus$ attack in their statement. The firm announced in January that a security incident occurred on a support engineer’s computer, and threat actors had a chance to access the laptop for five days. The screenshots published by Lapsus$ overlap with Okta’s description.
The company says there are no actions customers need to take.
Lapsus$’s Reaction to Okta’s Statement
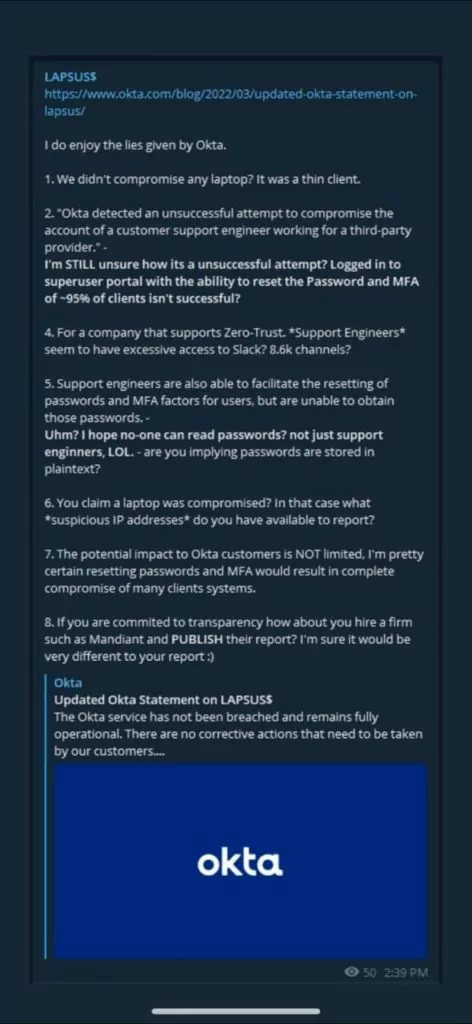
The Lapsus$ group’s response to Okta’s statement was quick. The threat actor said they had compromised a thin client, not a laptop of an Okta employee. Cybercriminals underline that they have the ability to reset about 95% of Okta customers’ passwords, and it is not a failed attempt as the company claims.
Other Attacks by Lapsus$: Microsoft, Samsung, and NVIDIA
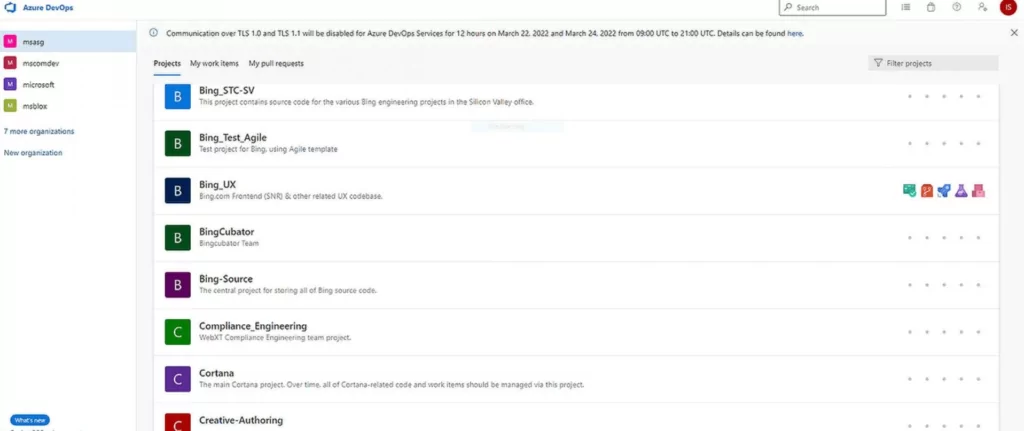
On March 20, 2022, the group announced that it had hacked Microsoft’s Azure DevOps Server and internal source code repositories. They claimed that they had source codes for Bing, Bing Maps, and Cortana in the message they shared.
Microsoft has published a statement exposing the group’s tactics confirming that the source codes have been compromised. It looks like the 37GB source code Lapsus$ claims to have leaked is actual. Microsoft states that no customer code or data is relevant in the activity of threat actors. They add that a single employee’s account has been compromised, and cybersecurity teams have secured the account.
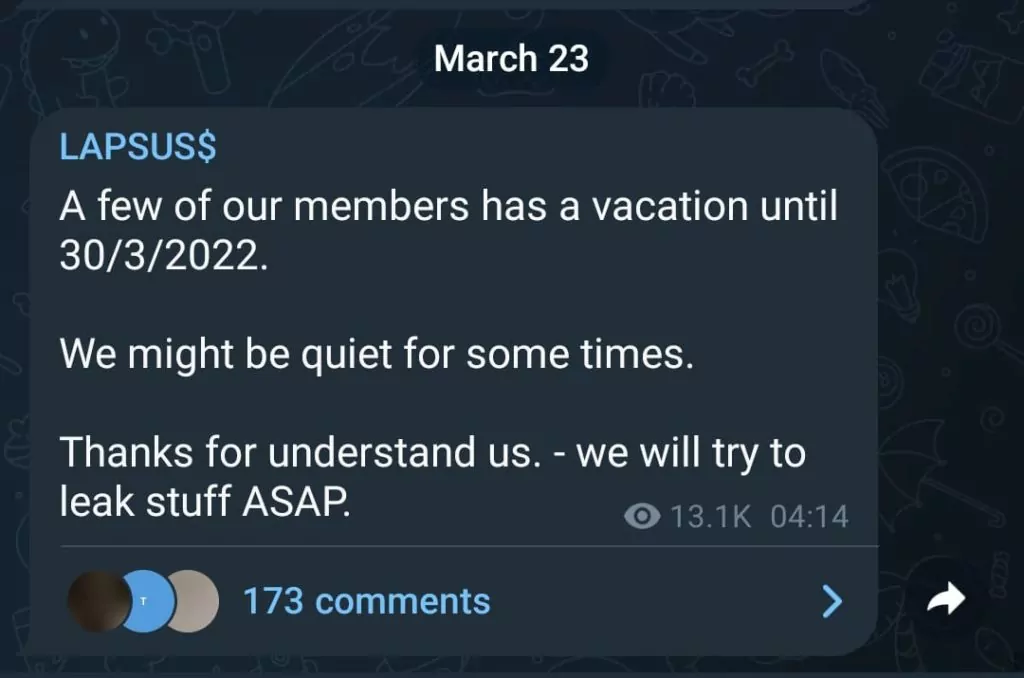
While it is unknown whether the group has agreed to a ransom with Microsoft, Lapsus$, which has targeted big companies such as NVIDIA and Samsung in recent months, shared a message on their Telegram channels. The message said that some group members would be on vacation until March 30, 2022.
How Can You Protect From Threat Actors Like Lapsus$?
Microsoft makes the following recommendations for companies to secure their digital assets and sensitive data and recommends a detailed review of the tactics used by the group.
- Strengthen multi-factor authentication applications.
- Provide healthy and strong endpoints.
- Use modern authentication methods for VPNs.
- Take measures to strengthen your cloud security and monitor it regularly.
- Give importance to awareness against social engineering attacks.
Check for Account Breaches on SOCRadar Labs
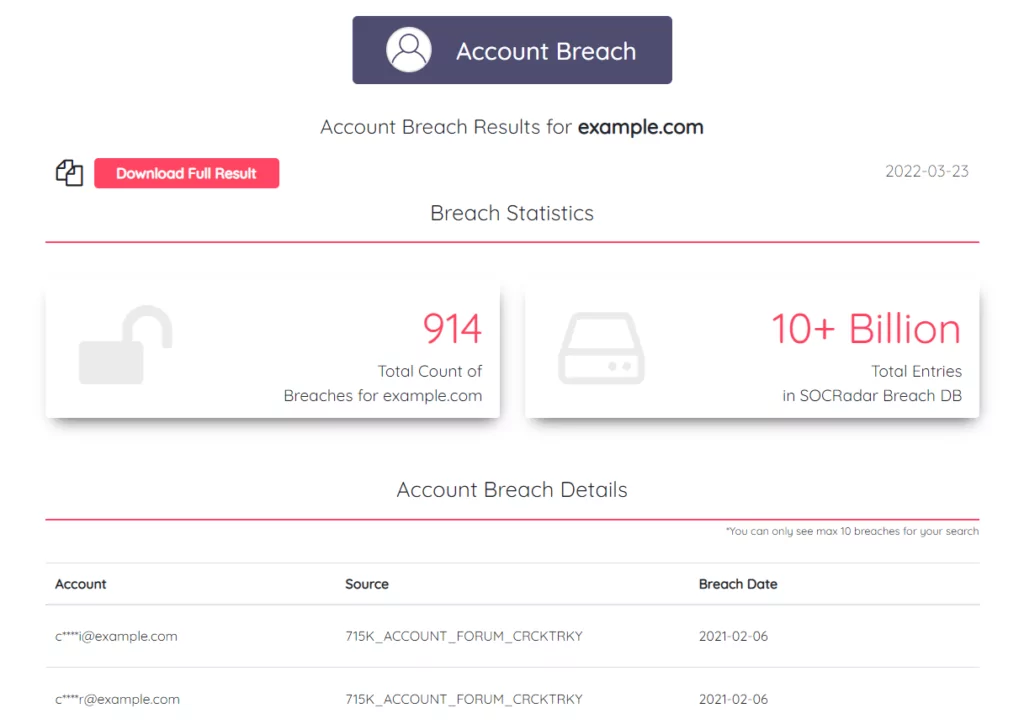
Search cybercrime black markets, combolists, and known breaches with SOCRadar’s free AccountBreach tool. There are more than 10 billion records in the SOCRadar Breach Database. Check it out right now if there is anything to do with you.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Get free access


































