
Lapsu$ Extortion Group Allegedly Leaked Samsung Source Code After Nvidia Breach
The infamous Lapsu$ Extortion Group has become a newsworthy threat actor while the cyber incidents escalated during the Russian invasion of Ukraine. While the group’s claim on stolen data from Nvidia GPU Designer is still the central part of the news, the group now leaked data from South Korean tech giant Samsung, including some Samsung products’ source code.
What Happened?
On a hacker chatter on Telegram monitored by SOCRadar Analysts, on March 4, 2022, Lapsu$ announced that they would publish data from Samsung. Unlike other ransomware groups that use deep web blogs (Onion sites), the group uses a Telegram channel to publish leaked data. The channel has around 14 thousand subscribers as of March 2022.
The Lapsu$ Extortion Group posted a torrent link to share the data with its followers.
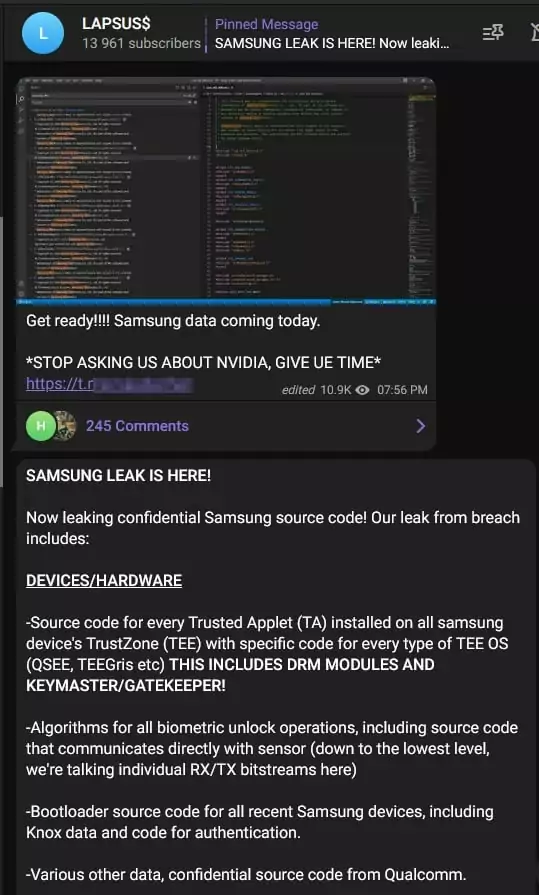
What is in the Allegedly Leaked Data?
The torrent link downloads 190 GB of data. According to the claims of Lapsu$, the data includes;
- Source code for every Trusted Applet (TA) installed in Samsung’s TrustZone environment used for sensitive operations (e.g., hardware cryptography, binary encryption, access control)
- Algorithms for all biometric unlock operations
- Bootloader source code for all recent Samsung devices
- Confidential source code from Qualcomm
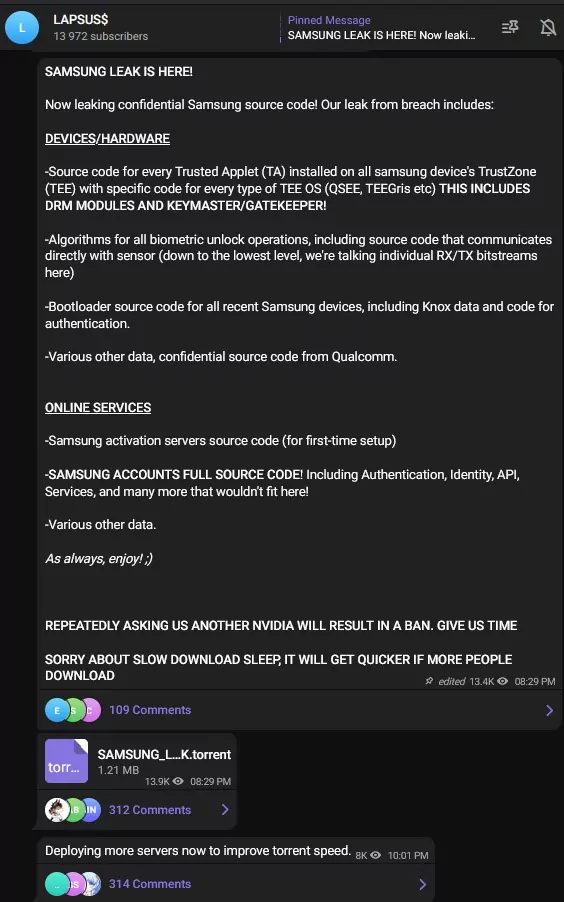
- Source code for Samsung’s activation servers
- Complete source code for technology used for authorizing and authenticating Samsung accounts, including APIs and services
Who is the Lapsu$ Extortion Group?
Lapsu$, like any other ransomware group, threatens companies to publish the stolen data if the ransom is not paid. During the Russian invasion of Ukraine, the group stated their support for Russia and leaked data allegedly stolen from Nvidia GPU Designer.
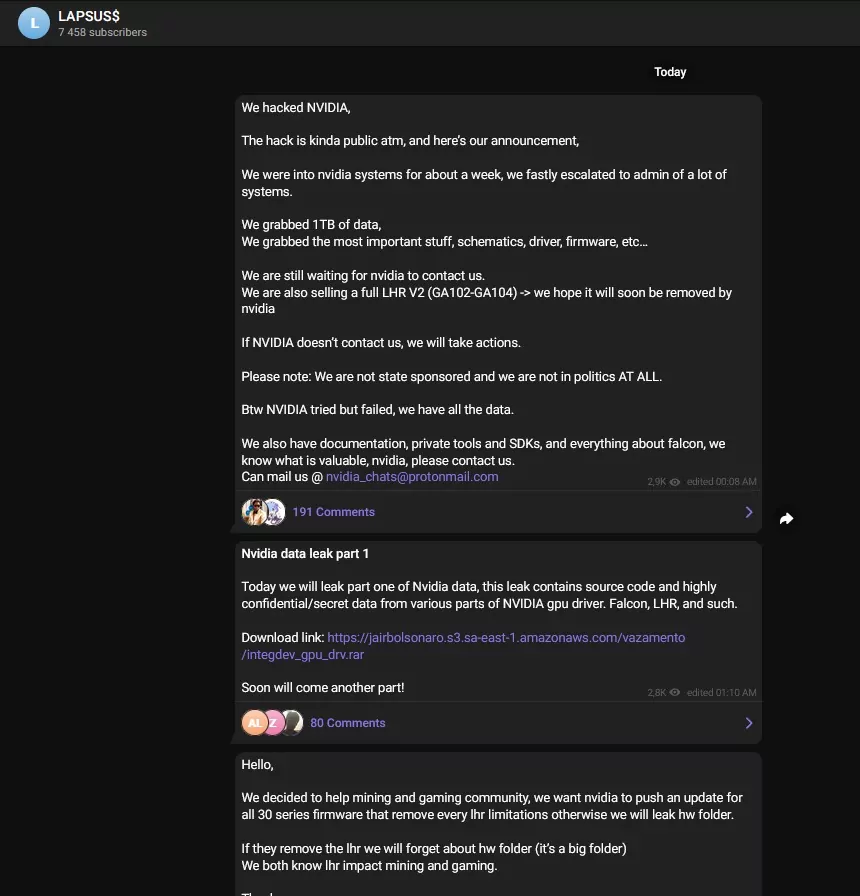
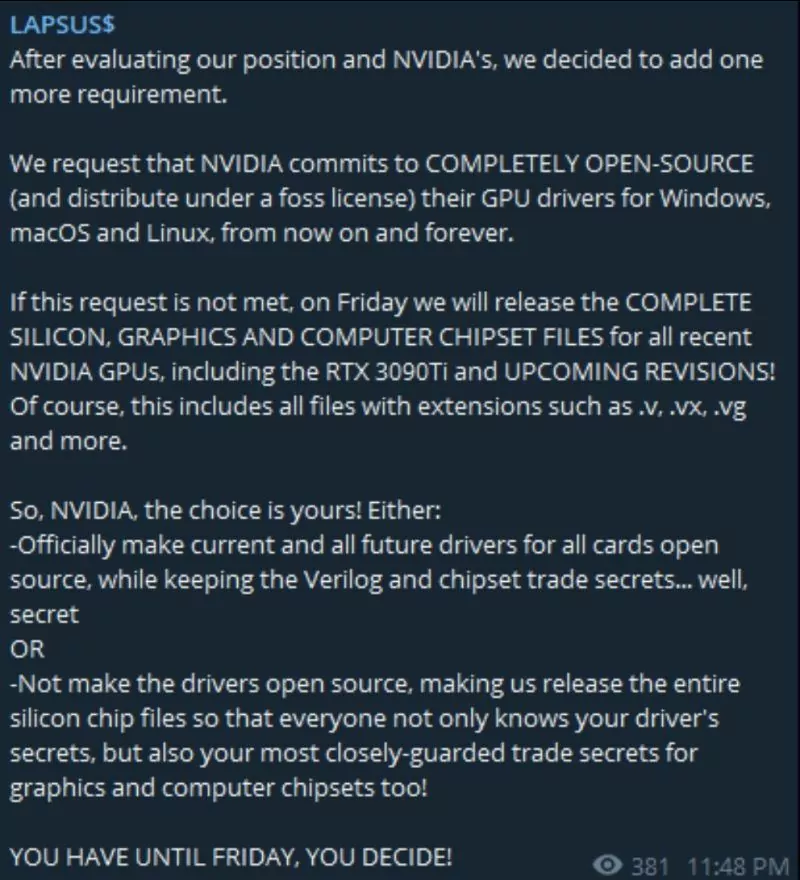
The group was claimed to be “hacked back” but claimed to recover their servers from the backup. The cyber incidents between Lapsu$ and Nvidia escalated very quickly, and the gang threatened the company to make their products open source.
Nvidia leak was not the group’s first extortion. In January 2022, Lapsu$ attacked the media group Impresa and later the Portuguese parliamentary site.
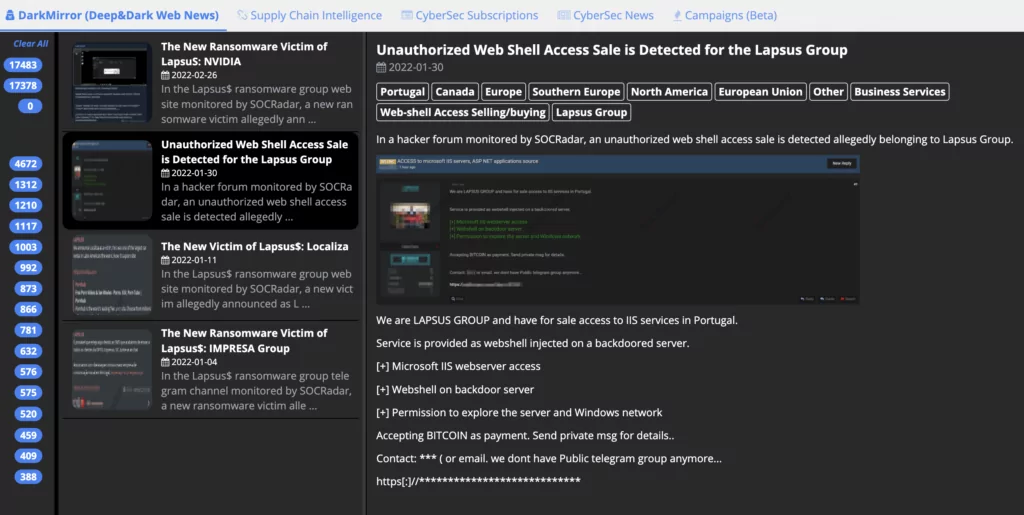
The group also posted a web shell access sale on a hacker forum that hints at its modus operandi about how they manage to get access to its victims.
The Most Effective Way to Monitor Ransomware Threats
With ThreatFusion, SOCRadar’s big-data-supported module, you can have the opportunity to monitor the activities of cyber threat actors without going into the deep web. It leverages the real-time analysis capabilities of your Threat Intelligence Teams and is fed by a wide range of data sources, from copy websites to dark web forums. With its API-ready structure, it easily integrates with your other security products. You can request the ThreatFusion demo for your industry-specific contextual intelligence needs.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Get free access


































