
What is RedLine Stealer and What Can You Do About it?
RedLine Stealer (a.k.a. RedLine) is malicious software that can be bought from $150 – $200 depending on the version on hacker forums. RedLine can steal data and infect operating systems with malware.
In general, cybercriminals try to infect computers with malicious software like RedLine Stealer to create cash by misusing accessed stolen information and infecting systems with additional software of this type for the same goal. If you have any evidence that your computer is infected with RedLine Stealer, you should immediately remove it from your computer.
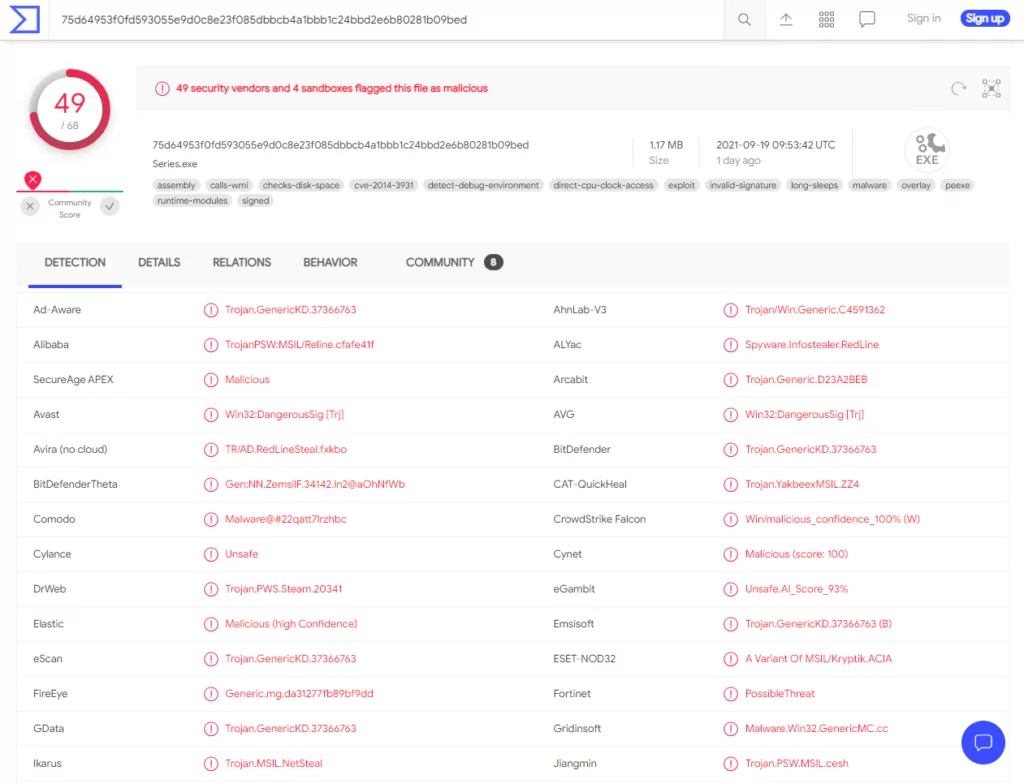
RedLine Stealer can collect information from all Gecko and Chromium-based web browsers, including logins, passwords, autofill data, cookies, and credit card numbers. Cybercriminals can use this information to access various accounts (e.g., social media, email, banking-related accounts, cryptocurrency wallets).
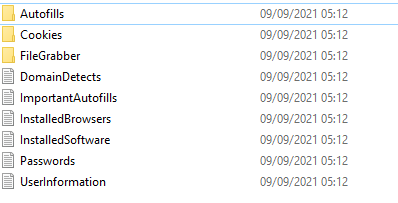
They also use them to spread malware, start spam campaigns, conduct fraudulent transactions and purchases, mislead others into sending money, and steal identities. RedLine Stealer may capture files from compromised systems by collecting data from various FTP (File Transfer Protocol) and IM (Instant Messaging) clients.
It can also capture system data such as IP addresses, usernames, keyboard layouts, UAC settings, security solutions installed, and other information. This kind of application is capable of infecting systems with further infections such as download and execute malicious files.
Cryptocurrency miners use computer hardware to mine cryptocurrency, while ransomware-type programs encrypt files which is causing data loss, Trojans can generate chain infections, and RATs allow criminals to control an infected person’s machine and do dangerous operations.
How RedLine Works
A dedicated WSDL application connects the RedLine Stealer to a remote command-and-control server. The hackers in command can browse through search records, download, conduct tasks, and export the data they want using that server.
Security researchers have determined that the RedLine Stealer’s wide-ranging capabilities are as accurate as they get after conducting a thorough investigation of the program. RedLine’s qualities, when combined with its low asking price, make it a hazardous malware piece. If a person willing to pay around $200 for such a weapon gets their hands on it, that person’s power will increase.
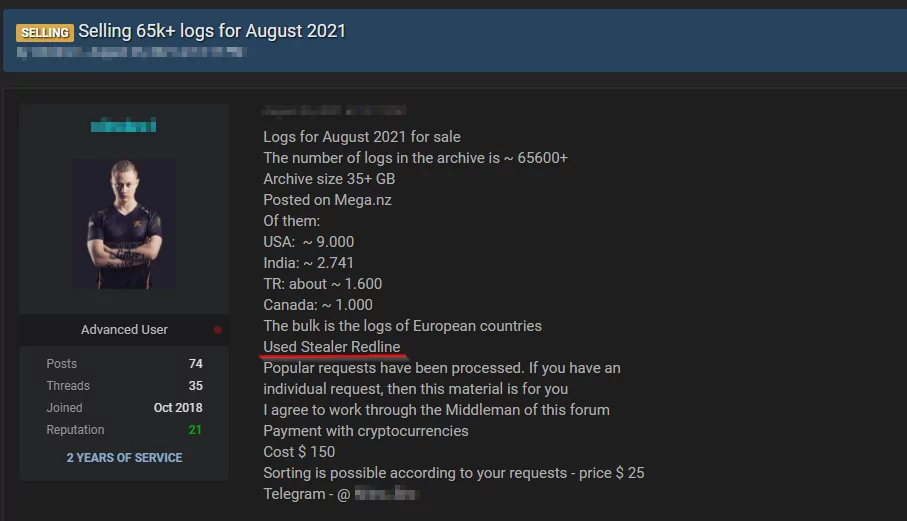
Given its frequent updates, RedLine’s creators will continue to improve the tool’s functionality when new targets emerge. In this regard, it’s not possible that RedLine will deliver additional malware payloads anytime soon. The global COVID-19 pandemic is being used as a backdrop for a growing number of social-engineering scams, and this trend is unlikely to change very soon.
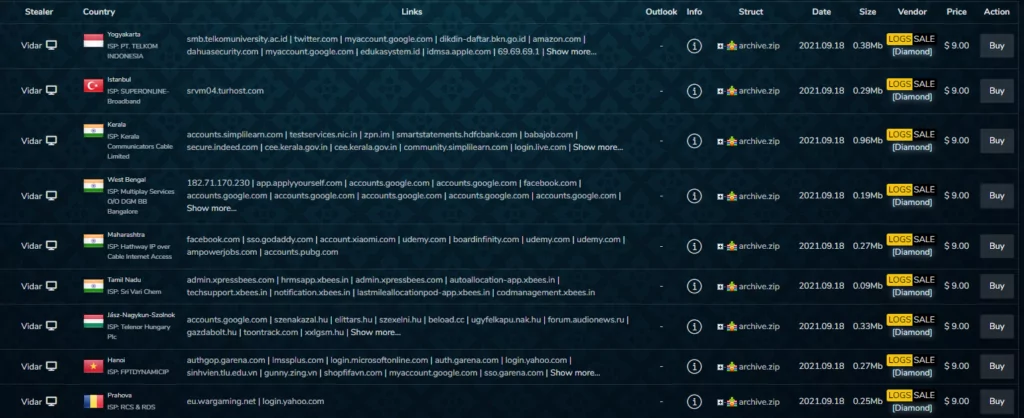
RedLine Stealer is likely to have spread worldwide since it is available to anyone who would like to pay the price for the software. That is why no users are confidential against a potential RedLine Stealer infection.

Using third-party tools to deploy the threat, such as Cryptors or Packers, to prevent signature-based detection is no concern for the threat actors as the subscription comes with free Cryptor as a package.
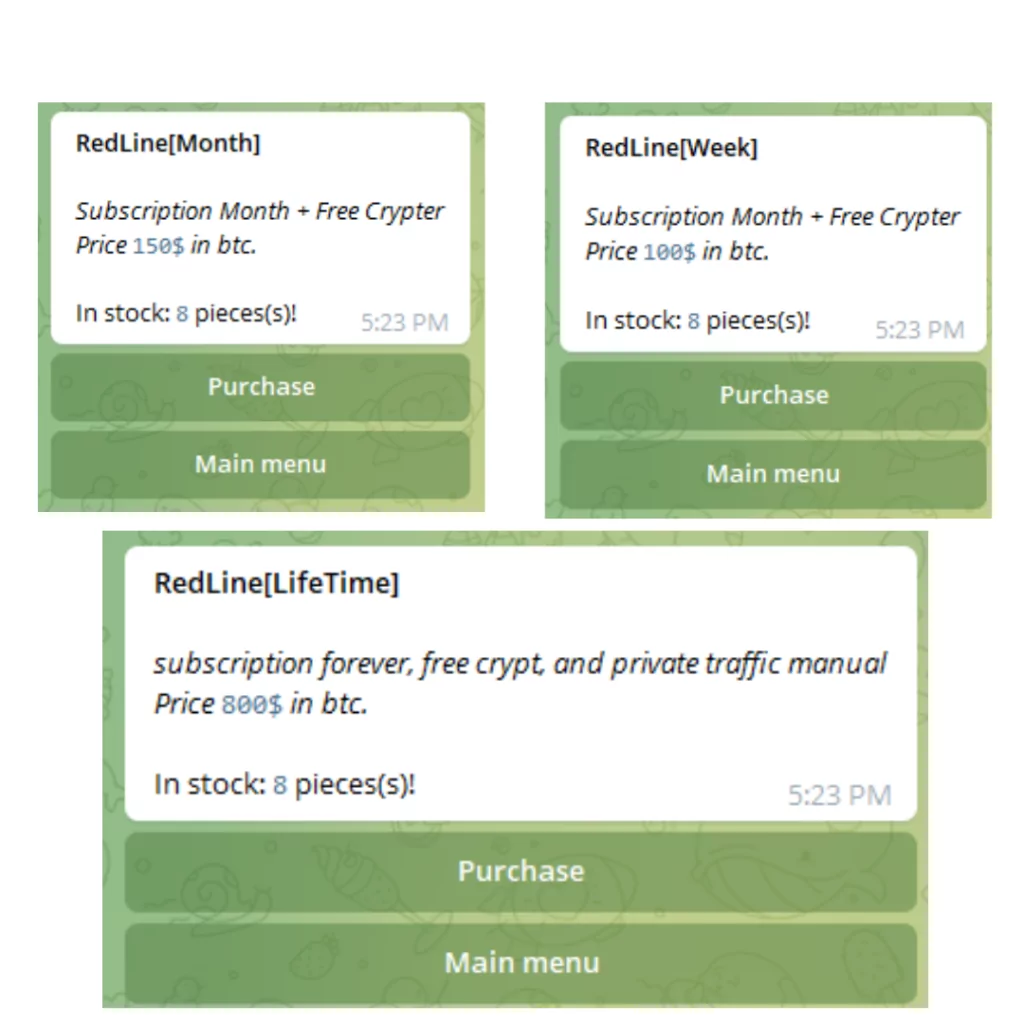
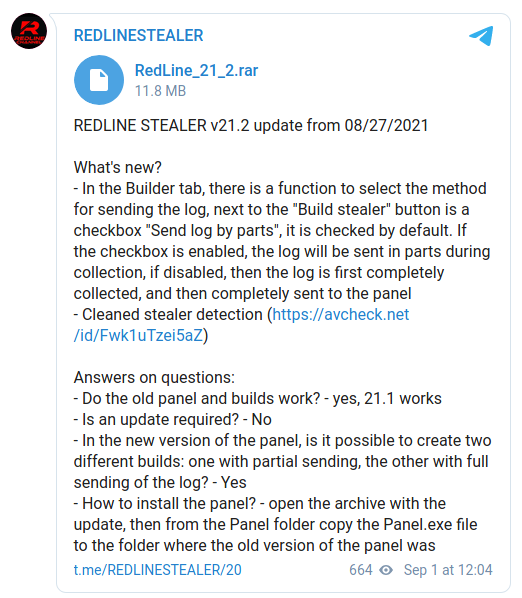
These tools are praised for the high level of service, and their management dashboard, much like the malware element, is reportedly straightforward to use. Notably, based on the analysis of recent samples and a changelog posted on the threat actor’s Telegram channel, the most recent release of Redline is version 21.2 and introduced support for additional stolen data management options, notification management, logging, and bugs fixed which indicates the dedication and ongoing development of the product.
How Can RedLine Stealer Affect You?
RedLine Stealer victims may suffer money and data loss, identity theft, privacy issues, personal and corporate account theft, and other significant consequences. To reduce your chances of falling victim to a threat like RedLine Stealer, you need to have a legitimate anti-virus software package that will protect your system and data. Also, don’t forget to regularly apply any pending updates to all your apps.

Recommendations
- Security awareness training for employers is critical in helping them recognize and be suspicious of unsolicited emails and phishing campaigns, as well as suspicious social media cases, like messages including embedded links or file attachments that might lead to the distribution of further malicious payloads.
- Multi-factor authentication should always be used to reduce the effectiveness of any stolen credentials.
- The organization should mandate strong password policies to all employees.
- Ensure that e-mail security precautions are taken to prevent end-users from receiving potentially malicious attachments or links, as well as configuring protocols and security controls like DKIM, DMARC, and SPF.
- Continuous monitoring of abnormal endpoint behaviors, such as requests to domains with a low reputation, can detect intrusion early.
Indicator of Compromise
SHA256 files hashes
Sample hashes since August 2021. It might be helpful for better understanding the nature of this threat.
- 95f79fdcfb83a5035a2e3fa8621a653a0022925a9d1cb8729b8956db202fc3d8
- 9072f90e16a2357f2d7e34713fe7458e65aae6e77eeb2c67177cf87d145eb1a6
- f224b56301de1b40dd9929e88dacc5f0519723570c822f8ed5971da3e2b88200
- ffee20e0c17936875243ac105258abcf77e70001a0e8adc80aedbc5cfa9a7660
- 88ff40bd93793556764e79cbf7606d4448e935ad5ba53eb9ee6849550d4cba7f
- 6be3a52cd5c077794a03f0596d1cbf3aee2635d268b03b476f6a2eaeb87d411c
Domains
- licensechecklive[.]xyz -License checks centralized server, Used for initial authentication of a Redline control panel user.
URLS
- licensechecklive[.]xyz/IMainServer
IPS
- 185[.]215[.]113[.]114
- 37[.]0[.]8[.]88
- 193[].142[.]59[.]119
- 136[.]144[.]41[.]201
HTTP Headers
- SOAPAction: “hxxp://tempuri[.]org/IMainServer/Connect”
- SOAPAction: “hxxp://tempuri[.]org/Endpoint/EnvironmentSettings”
- SOAPAction: “hxxp://tempuri[.]org/Endpoint/SetEnvironment”
- SOAPAction: “hxxp://tempuri[.]org/Endpoint/GetUpdates




































