
Building Cybersecurity Awareness for Organizations
Cybersecurity has become a vital phenomenon for every institution today, but ensuring safety is a long process that includes different layers, and one of these layers is human. Since a crack at any point can overturn all security, problems that can occur at the human layer, often due to unawareness of people, can cause a significant problem.
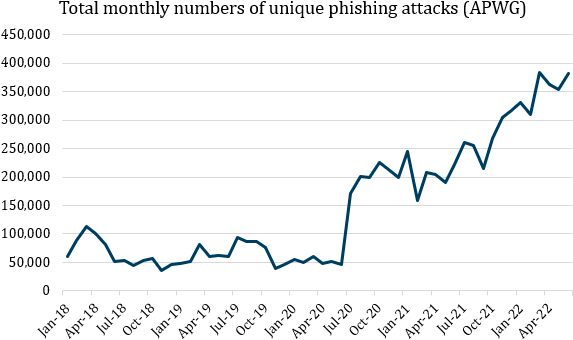
According to Verizon’s 2022 report, 82% of cyber incidents are human-based; the IBM Cybersecurity Intelligence Index Report, on the other hand, gives a different rate and claims that human error comes first in 95% of cybersecurity breaches. These reports clearly show that focusing on human vulnerabilities should be the top priority to ensure cybersecurity. At this point, the concept of Cybersecurity Awareness appears as a solution to this dire situation.

What is Cybersecurity Awareness?
Cybersecurity Awareness is an ongoing effort to protect yourself and your organization by enabling employees to answer essential questions such as threats in the cyber world, how to prevent them, and how to be protected from them.
When the precautions are not taken, cyber incidents may have severe consequences for all organizations:
- They may face legal challenges or penalties when adequate cybersecurity is not ensured. Organizations suffer damage to their functions in case of an incident, resulting in property and reputational damage, and most importantly, endanger people’s security and even their health. However, the awareness culture, built on employees through periodic training, will strengthen the cybersecurity posture.
While we understand why these topics are important, we should also understand threat actors to know why Cybersecurity Awareness programs require continuity. Threat actors constantly improve themselves, look for vulnerabilities, and discover new tactics and techniques to hack humans, but keeping the information of the relevant parties up to date helps to have a high level of Cybersecurity Awareness.
How Can Humans be Hacked?
Social engineering is a set of techniques used to manipulate people and extract sensitive or critical information. Attackers try to achieve their ends by manipulating our thoughts or feelings. Their gains from this malicious action could be stealing sensitive data or credentials, but mostly creating or trying to find an initial access point to gain financial income.
As one of the most common social engineering attack types, the impersonating attack is a type of modern phishing scam. It’s a widespread and growing technique targeting any employee, employer, C-level executive, investor, shareholder, or even customer; threat actors try to deceive their victims by impersonating a trusted source.
Although phishing-type attacks try to manipulate people in the cyber world, the term human hacking can also find a response in the physical world.
A good example of this is the technique called tailgating. An attacker who wants to enter an environment that requires authorization for entry can wait at the entry point with his hands full, asking someone authorized to open the door for him, abusing the victim’s intention to help.
Threat actors use many other social engineering techniques, but that’s not all, as discussed above. Threat actors are also developing new methods, such as MFA Fatigue, one of the MFA Bypass techniques, and hybrid attacks that combine multiple techniques, like Callback Phishing.
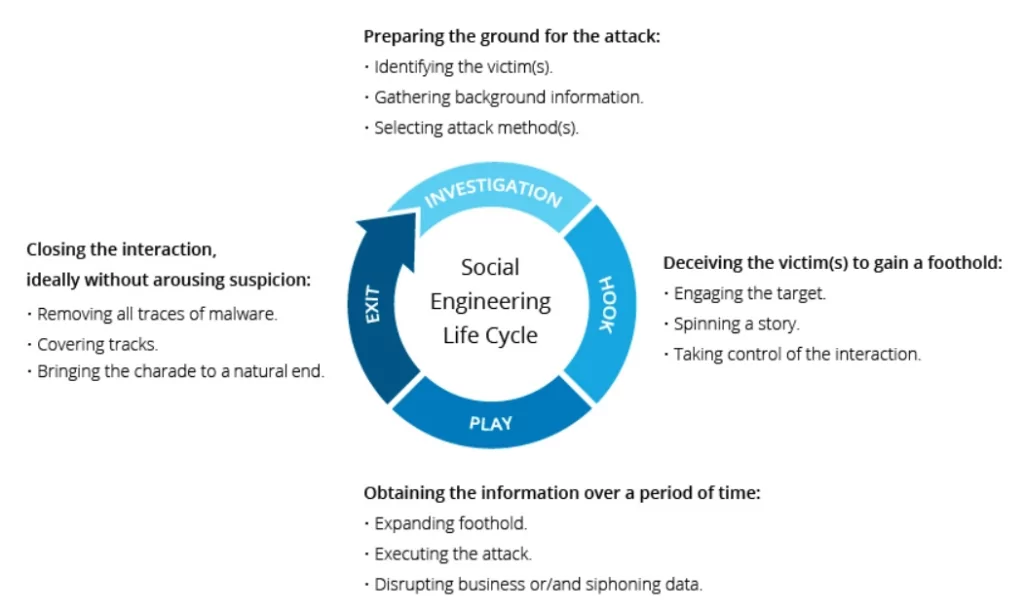
In conclusion, with social engineering techniques, attackers try to gain an advantage by exploiting our humane emotions, such as people’s willingness to help, curiosity, desire, pride, or trust. Thus, they can hack humans by psychologically manipulating and abusing these structures.
Social Engineering Cases
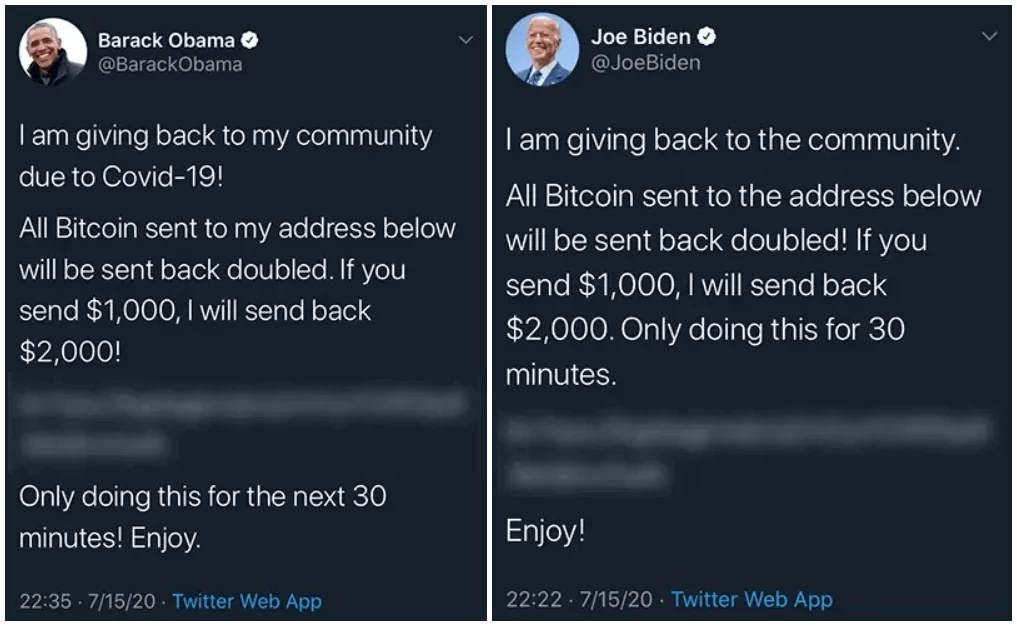
- In an incident in 2020, Twitter employees were hacked. Threat actors, who infiltrated Twitter’s internal systems and accessed the identity information of many users, raised money in a short time. By sending phishing messages from many verified accounts, they abused users’ trust in important figures and Twitter’s verified user system.
- In April 2021, a phishing attack exploited the sense of curiosity. Victims received an email attachment of an Html file that looked like an excel file named “Price Revision.” Users who clicked on this attachment encountered a page on a website containing malicious codes, where their Microsoft 365 account session was supposedly terminated, and they were asked to re-enter their username and password. Those who tried to log in again had their credentials stolen by threat actors.
- In another attack in 2020, there was an attack that took advantage of the Google Drive notification system. The attack begins with creating a document containing malicious links to a phishing site. The scammer then asks the victim for help with a tag. Once tagged, the target receives a legitimate email notification from Google with the comment’s text and a link to the relevant document. The victim gets infected by the malicious document by clicking on the link. This attack also abuses human feelings: the willingness to help and pride.
Social engineering is based on the abuse of human nature. The key to avoiding attacks that exploit such human vulnerabilities, like the abovementioned incidents, is building Cybersecurity Awareness.
Best Practices for Cybersecurity Awareness
- Firstly, all employees and managers, even those responsible for cybersecurity, must receive periodic cybersecurity awareness training.
Everyone can make mistakes, and all internal employees can be a target for an attacker; spear-phishing attacks are specific to people at critical points, so even a CISO should keep their awareness alive.
- You should ensure that cybersecurity training is taken seriously and presented engagingly.
To achieve this, organizations can create cyber-attack scenarios for their employees and organize interactive games to simulate these techniques.
- Awareness should be a part of corporate culture, and activities related to Cybersecurity Awareness should be included in long-term company planning.
“People think of security as boring and are reluctant to care about it, so it is important to create an emotional connection to make it effective.”
Jinan Budge
Top Recommendations for Building Cyber Awareness
- Newly recruited employees should be remembered and go through training during orientation.
Fresh recruits can adapt to security policies, and they cease to be an additional vulnerable point.
- You should know where an attack can be made against you and take proactive measures against these vectors.
Using attack surface management, you may discover the most vulnerable spots to cyber-attacks on your organization.
- By following the security threats and intelligence via CTI platforms, you can develop and expand your Cybersecurity Awareness programs that will keep you up to date.
Cyber threat intelligence can give you insights into the latest attacks and help you understand the context of such threats.


































