
Verizon 2022 DBIR: All Sizes of Businesses Suffer from Ransomware
Verizon has released the 15th Data Breach Investigations Report (DBIR), an in-depth analysis of trends in cyberattacks and data breaches for cybersecurity experts and leaders worldwide. The report includes reviews of around 24,000 cybersecurity incidents that took place between November 1, 2020, and October 31, 2021.
Verizon analyzed over 5,000 confirmed breaches under 2022 DBIR. Some of the key findings obtained as a result of the analysis can be summarized as follows:
- Ransomware attacks increased by 13% in just one year. This is even more than the total increase rate of the last five years.
- The prevalence of ransomware attacks has increased in data breaches.
- The human factor played a significant role in analyzing more than 80% of the data breach incidents—striking data showing that organizations need to provide more cybersecurity awareness training to their employees.
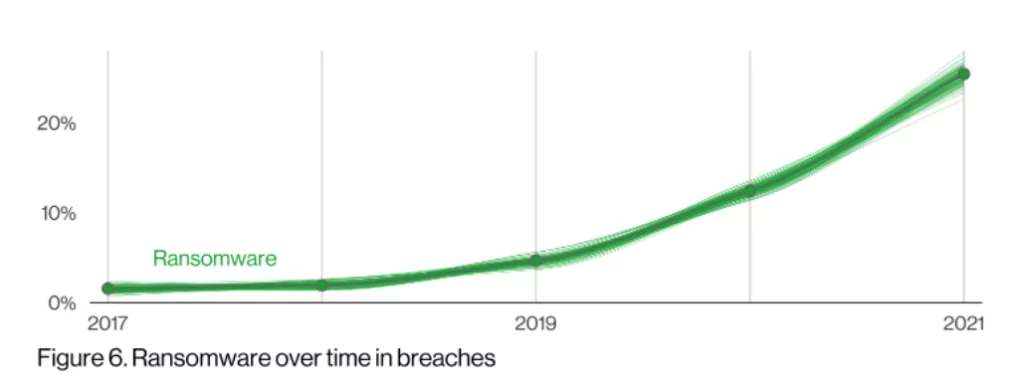
Even Small Businesses are Threatened by Ransomware
There is an important reason behind the rising ransomware attack curve. Ransomware is no longer just targeting large organizations or companies with high turnover. Even businesses with ten or fewer employees can be on the target. In our opinion, one of the reasons for this is the ransomware-as-a-service (Raas) market. People who do not have technical knowledge can demand ransom through this malicious software.
As we can see in Verizon’s 2022 DBIR, ransomware and the human factor are two crucial interrelated issues. The human errors, omissions, or carelessness caused by the human element can lead to ransomware attacks that cause substantial financial losses. SOCRadar can provide you with a more robust security posture with its ThreatFusion, AttackMapper, and RiskPrime products, combined with the Extended Threat Intelligence approach, and work wonders in sync.
How SOCRadar Blocks Ransomware
We said that ransomware infection vectors are linked to the human factor. But the issue is not limited to this, of course. The most common infiltration techniques of threat actors are to gain access to RDP (remote desktop protocol) and VPN (a virtual private network). SOCRadar keeps you alert to these threats in two different ways.
1. Keep an Eye on Threat Actors
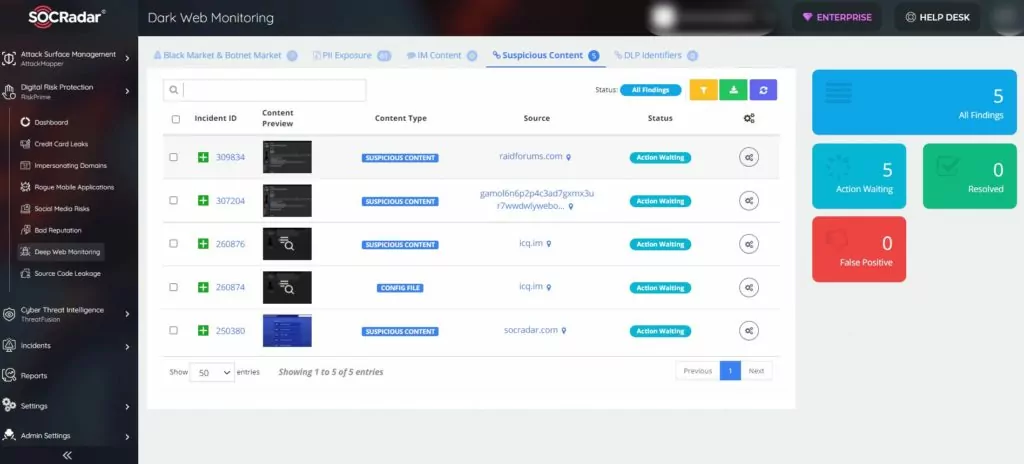
CTI4SOC is an advanced Cyber Threat Intelligence product that shares actionable insights against potential cyber threats. It scans the deep/dark web, Telegram channels, forums, and black markets for you and notifies you if any RDP or VPN is up for sale. Thus, you have the intelligence that can disrupt the attack plans of cybercriminals in advance.
2. Safeguard Your Growing Attack Surface
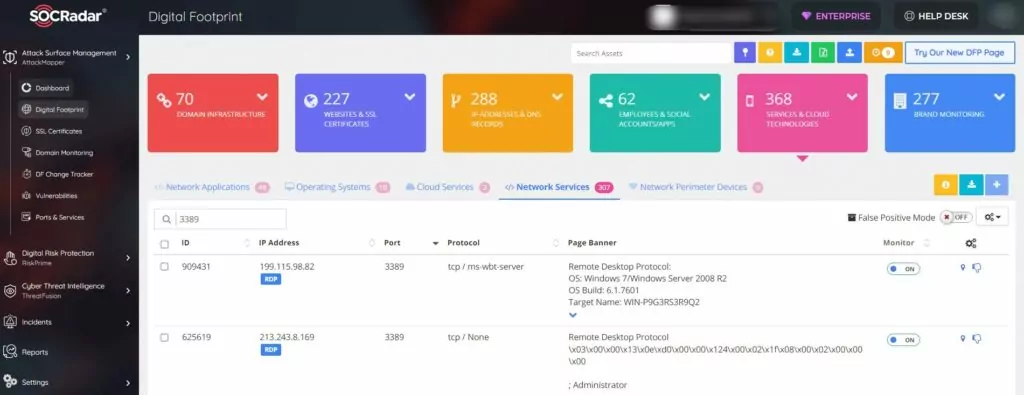
The digital assets of organizations constantly increase according to periodic needs. The automatic detection of these assets that are open to the Internet is essential for a good cyber defense line. AttackMapper, SOCRadar’s External Attack Surface Management, helps keep your sensitive data safe by detecting RDPs that are open when they shouldn’t be.
Eliminate the Human Factor
1. Phishing campaigns
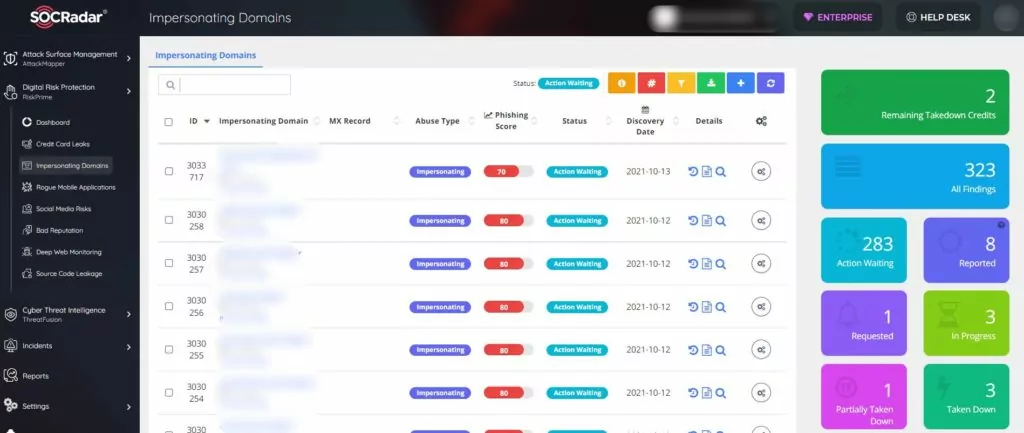
Phishing attacks are beneficial for obtaining information necessary for ransomware. Threat actors try to infect the system by creating interfaces that mimic trusted websites or by using fake domains and emails that look like the real thing. With SOCRadar, you can detect these fake domains and ensure that they have closed, thanks to the integrated takedown service.
2. SSL certificate expiration date
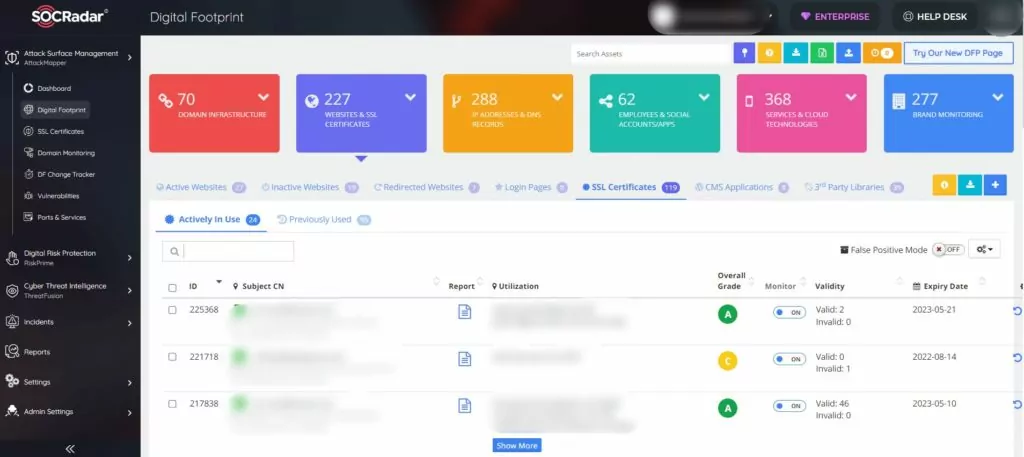
The SSL certificate aims to help keep the users’ sensitive data safe by encrypting the private information with 2048 byte data way. If the renewal date of SSL certificates purchased for a certain period is not followed and forgotten, the information on the website is kept in an insecure environment. SOCRadar timely warn you about expired SSL certificates and optionally renews or recommends you renew them.
3. VIP email breaches
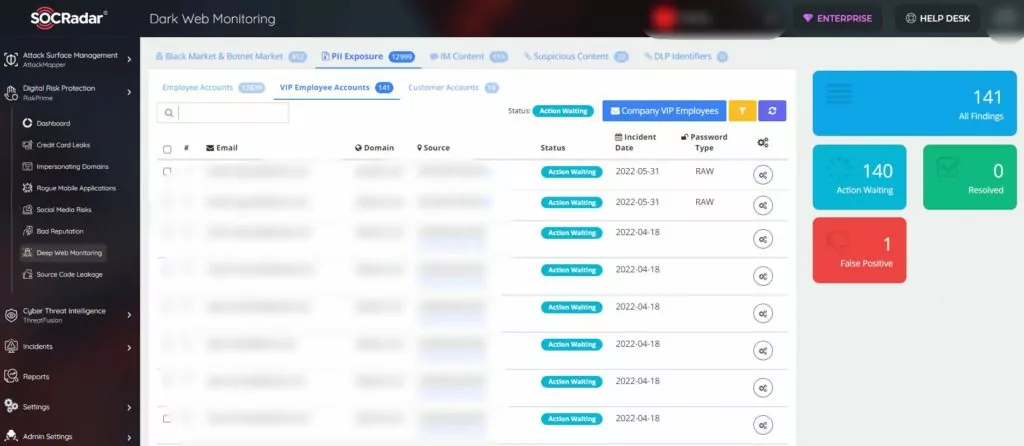
When phishing campaigns target corporate emails, they can be detected using various filters, or the threat can be circumvented by sending warnings to employees. What if a personal email from a senior executive is compromised?
In this scenario, the process usually goes like this: A C-level administrator logs in or subscribes to a third-party system with their personal email. When there is a breach of this third-party software, threat actors examine the data and realize they have accessed a VIP employee’s email. Thus, they can individually target this person in phishing campaigns.
When a data breach occurs, SOCRadar searches for the VIP emails it receives from you in the leak and notifies you as soon as it detects it.
Use SOCRadar® FOR FREE 1 YEAR
With SOCRadar® Free Edition, you’ll be able to:
- Prevent Ransomware attacks with Free External Attack Surface Management
- Get Instant alerts for fraudulent domains against phishing and BEC attacks
- Monitor Deep Web and Dark Net for threat trends
- Get vulnerability intelligence when a critical zero-day is disclosed
- Get IOC search & APT tracking & threat hunting in one place
- Get notified with data breach detection
Free for 12 months for one corporate domain and 100 auto-discovered digital assets.
Get Free Access.



































