
Stop BEC Attacks with SOCRadar Takedown Processes
Attacks such as phishing, business e-mail compromise (BEC), and malware infection, which are among the fraud activities, increasingly pose a serious threat to organizations. The numbers in the “Phishing Activity Trends Reports” of the last quarter of 2021, published by APWG, reveal the dimensions of the event. December 2021, in which more than 310 thousand attacks occurred, peaked as the month with the most attacks. While phishing attacks tripled compared to January 2020, the most affected sector was the financial sector, with a rate of close to 25%.
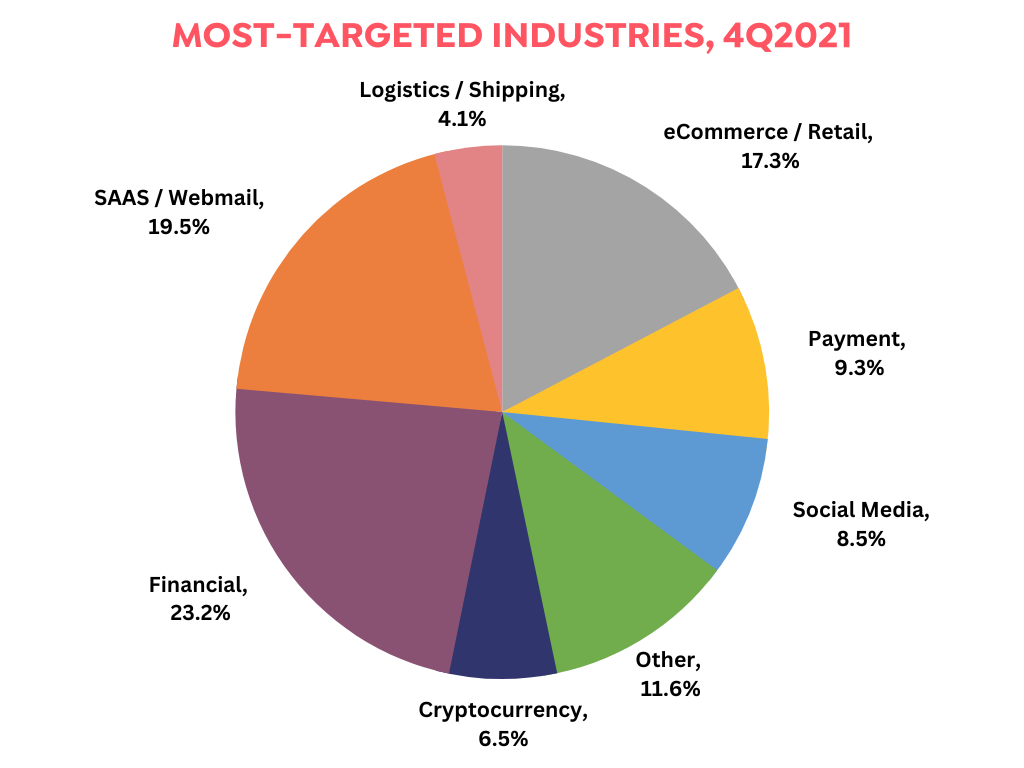
The attacks cause financial loss and reputational loss for the stakeholders and customers of the attacked organization.
An organization that wants to have a proactive defense system must first detect all domains and fake social media accounts that may threaten it. Detection as early as possible will activate the organization’s defense mechanism and provide an opportunity for a counter-attack. The disclosure of the methods followed by the attackers pushes them to seek new ways and discover new methods. For this reason, the follow-up of new phishing campaigns is a factor in keeping the defense mechanism strong.
Most Common Attacks
Ads given to various browsers: It redirects the victim, who searches in the browser to access the target organization, to the phishing site prepared by the attacker. The threat actor, which reaches its goal within hours, completes its attack by terminating the advertisement.
Fake social media accounts: It directs users to phishing sites with explanations such as campaigns, discounts, special days, gifts, debt restructuring, or makes publications containing defamatory statements.
Messaging applications: As with social media accounts, users are persuaded to click on malicious links with various promises.
Sending e-mails: By using domain names close to the original domain name of the organization, attachments, links with malicious content are sent to employees, stakeholders, or customers, or different redirects are made for fraudulent activities. Requesting payments to specific accounts, requesting in-house special information/documents, etc.
The assassination of reputation: By making publications that will damage the organization’s reputation with baseless claims, a specific audience (customer/stakeholder) is adversely affected or misdirected.

Considerations
If an attack is detected, immediate action is required. This intervention sometimes includes removing content, deactivating the address used by the email sender, and closing the social media account.
In case of detecting an inactive but potentially risky domain or social media account, the monitoring activity should be activated. An attack can be carried out after three days or three months with a purchased domain with a name similar to the original domain name. The absence of activity in the domain or social media account for a while does not mean there will be no attack. Considering the possibility that it may turn into an active attack at any time, it must be followed up.
Fast Takedown and Tracking with SOCRadar
SOCRadar provides notification to its customers by quickly detecting domains and social media accounts that pose/may create threats by monitoring. If requested, it is activated with takedown processes to eliminate the threat.
SOCRadar has a team that provides 24/7 service and is responsible for takedown processes. This team is the SOCRadar Takedown Analyst Team (STAT), made up of cyber threat intelligence analysts.
Each type of threat to defeat has different challenges. STAT treats each event as a different state. As a result of the research, they created the fastest and most practical takedown solutions with the findings they encountered and obtained. These solutions are tried and implemented solutions. They also try to continuously improve the takedown processes by analyzing the TTPs of the attackers.
With SOCRadar, you can initiate the takedown process with one click via email or the platform. You start to receive notifications with the request, and you will be informed about the developments until the process is completed.

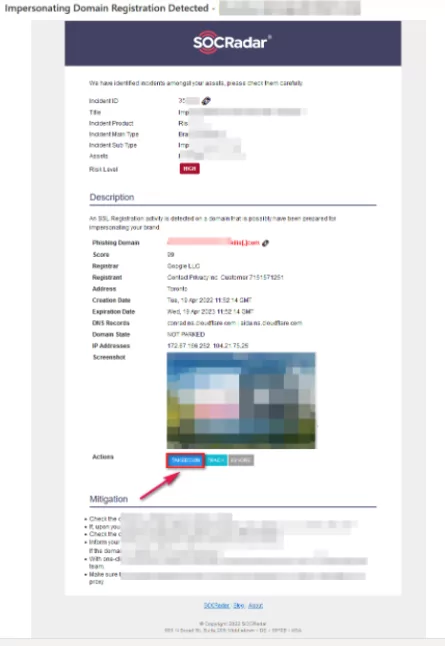
Takedown of Attacked Websites
SOCRadar contacts the following to takedown phishing or spreading/containing malware websites. The fastest method of communication (mail, telephone, online chat, etc.) is determined, and action is taken.
- Domain Registration Company
- Hosting Provider
- Website Owner
- Blacklists
- Browsers
- Name Server Operators (DNS)
- CERT/CSIRT Teams
- SSL Certificate Generator
SOCRadar does not need any input from you to start the run and moves the process forward.
Upon completion of the work, access to the published content is blocked. In some scenarios, when browsers or Name Server Operators request access to the domain, the user is greeted with a warning.
Such a takedown process is completed in 2-6 hours. The minimum and maximum times vary between 10 minutes and 48 hours. The reason for giving an average time is that attackers prefer organizations that are less sensitive to the issue or react late to operate for a longer period.
Takedown of Domains Actively Attacked via Mail
SOCRadar supports your defense system with its alarms and takedown feature, especially to protect your employees/customers/stakeholders against BEC attacks. In the Cyber Crime Repot 2021 published by the FBI, it is seen that the attack that causes the most financial loss is the BEC attack. While the report states that the attacks continue, their investigations state a financial loss of $2.39 billion. Most of these attacks made via mail are BEC attacks.
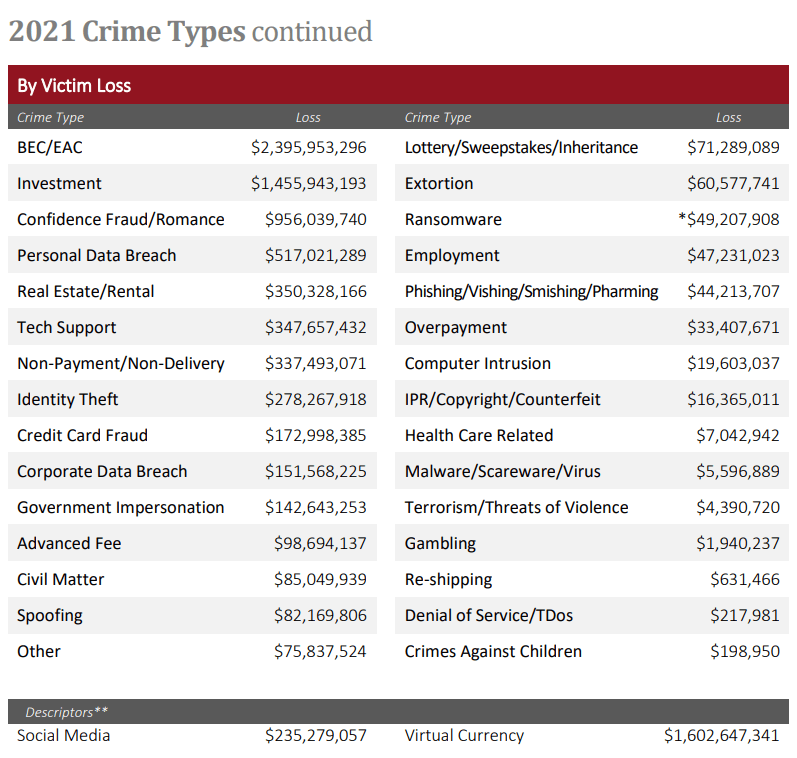
SOCRadar works in sync with various organizations to takedown domains used in attacks such as BEC, identity theft, and malware spread/infection over email.
SOCRadar requests the original email sent to the victim or the email’s header information to start the process.
Takedown of Brand Violating Websites
SOCRadar provides a takedown service for websites that imitate an organization, give false information about it, use its logo unauthorized, and publish content that will damage its brand reputation. The attackers’ intent here is not to steal credentials or sensitive data, so it does not include a login page. SOCRadar works in sync with various organizations, as in other cases.
Upon completion of the work, the infringing content is removed from the publication within 24 hours. Minimum and maximum times vary between 10 minutes and 72 hours. Organizations generally operate more slowly, as there is no direct acquisition of sensitive data. Authorities may request a document showing that SOCRadar is authorized to apply for domain takedown on behalf of the organization. For this reason, SOCRadar may request power of attorney from you before service to provide a fast takedown service.
Takedown of Domains Not Actively Involved in Attacks
STAT states that for domains that are not actively involved in an attack, the best thing to do is regularly monitor them. SOCRadar monitors all your suspicious domains until the domain is available for purchase again. It notifies its customers when there is a significant change. When it carries any of the above features, it enters the radar and is taken down by STAT.
SOCRadar helps protect its customers against BEC attacks, especially with its MX record changes. STAT considers domains with MX records and no content as a potential threat that can be attacked via email.
Takedown of Fake Social Media Accounts
SOCRadar takedowns for fake Facebook and Instagram accounts that impersonate your organization or violate the terms of use. The minimum and maximum times for a social media account taken down in an average of 1 hour vary between 20 minutes and 20 hours. Just request to start the process; no input will be requested.
Tracking
STAT also informs and performs actions for other domains associated with a domain that is requested to be taken down and targets your organization. Thus, it helps to eliminate other parts of the threat as well. Once you become the target or part of a campaign, the attack will continue, so it is necessary to anticipate the next step or thwart the attack as soon as possible. In such cases, SOCRadar will support you with STAT.
Takedown for Sensitive Data
If a file containing sensitive data about your organization (API key, login credential, employee data, etc.) is published to a GitHub repository or pasted sites without your permission, it will be taken down.
At the end of the takedown process, the GitHub file or the content on the paste site is unpublished.
Takedown for Mobile Apps
Any application published in any application store, belongs to your organization, or imitates your mobile application without your permission and knowledge, is taken down.
As a result of the takedown process;
- You will not have to follow the version of your application in a market that you do not want or know.
- You will prevent the use of old versions with possible vulnerabilities.
- With fake mobile applications created using your logo, you will protect your customers from spyware and identity theft threats.
Use SOCRadar® FOR FREE 1 YEAR
With SOCRadar® Free Edition, you’ll be able to:
- Prevent Ransomware attacks with Free External Attack Surface Management
- Get Instant alerts for fraudulent domains against phishing and BEC attacks
- Monitor Deep Web and Dark Net for threat trends
- Get vulnerability intelligence when a critical zero-day is disclosed
- Get IOC search & APT tracking & threat hunting in one place
- Get notified with data breach detection
Free for 12 months for one corporate domain and 100 auto-discovered digital assets.
Get Free Access.



































