
How Can You Avoid Potential Attacks with SOCRadar Integrations?
Today’s blog post is about API services, security solutions, and integrations that SOCRadar offers. You can access the SOCRadar API documents regarding the APIs provided by SOCRadar (used depending on licenses/packages) from this link.
SOCRadar, as an Extended Threat Intelligence (XTI) platform, provides alarm-based event notifications via e-mail and API integrated products.
SOCRadar offers the opportunity to monitor all your inventory controls, changes, vulnerabilities, update/end dates, posts targeting your brand on the dark/deep/surface web, mentions on social media, in short, all of your accessible digital assets.
Our platform monitors the IOCs of the threat actors up-to-date. It presents them to you on the SOCRadar Threat Feed IOC Dashboard after passing over 43 million whitelists and validations (IP, Hash, MD5, etc.). It also provides integration with your security products depending on your license type.
SOCRadar’s big data, which you can use for threat hunting, is presented to you with the SOCRadar Threathose module. You can also benefit from the API to perform Malware Analysis with additional package purchases and query Shodan with VirusTotal.
You can follow our articles on follow-ups and use cases by SOCRadar on our blog page on our website and threat share posts.
What are SOCRadar’s APIs and Security Solutions?
1. Incident API
SOCRadar’s alarms are transmitted via the Incident API. Alarm management is provided effectively and grouped according to the need-to-know principle, and it can manage from the platform and Incident API.
The second API version is available to SOCRadar users in Q4 2021, ensuring existing integrations are not disrupted. In addition, with the double-sided structure of the API, “resolve” or “false positive” can be drawn independently of the platform, and you can ask questions to one of our analysts.
All the filters you will need (severity, is_resolved, is_false_positive, incident_main_type, incident_sub_type, incident_type_id, start_date, end_date) are presented in the alarm headers, and alarms that require urgent action can be instantly transmitted to the relevant team thanks to multiple filtering.
You can send SOC-related alerts to your SOC team, network-related alerts to your network team, fraud alerts to your fraud teams, and brand reputation alert to your brand reputation team. In this way, while the platform limits the number of users, it ensures that alarms are instantly transmitted to the relevant units according to the need-to-know principle.
For more information on Incident API, you can refer to our Incident API – SOCRadar Docs document and contact the [email protected] team for integration.
2. Leak API
In case of data leaks about your employees, VIP personnel, and customers in hacker forums and combo lists, SOCRadar will send instant notifications to you. Although it is transmitted instantly, it isn’t easy to take immediate action manually due to the size of this data and the intensity of the security teams.
In this context, you can feed your different Active Directory structures with the filtering options (customer, employee, and VIP) in the Leak API we offer.
You can take various actions according to the leak type. In addition, with the Incident ID information in the Leak API, you can make “resolve” or “false positive” by the action you take for user accounts whose data has been leaked.
The Leak API is not integrated into Active Directory; it writes to a file. Then, you’ll provide the necessary actions.
3. Threat Feed IOC Endpoint API, SOCRadar TAXII Server ve SOCRadar MISP Server
IOCs of threat actors are updated daily; thus, SOCRadar’s suggested lists and Endpoint API points of manual lists that you will create on the platform remain up-to-date. Outdated IOCs are removed from the Endpoint API to prevent possible FP situations.
In addition, all feeds are presented to you on the SOCRadar ThreatFeed IOC Dashboard after processing through above 43 million whitelists and validations (IP, Hash, MD5, etc.).
You can find the phishing domains/URLs SOCRadar offers its customers and get the IP feeds that will make DDoS attacks. You can prevent collecting and sharing data about your system and security products by blocking the source addresses of vulnerability scanning services such as Shodan on the firewall.
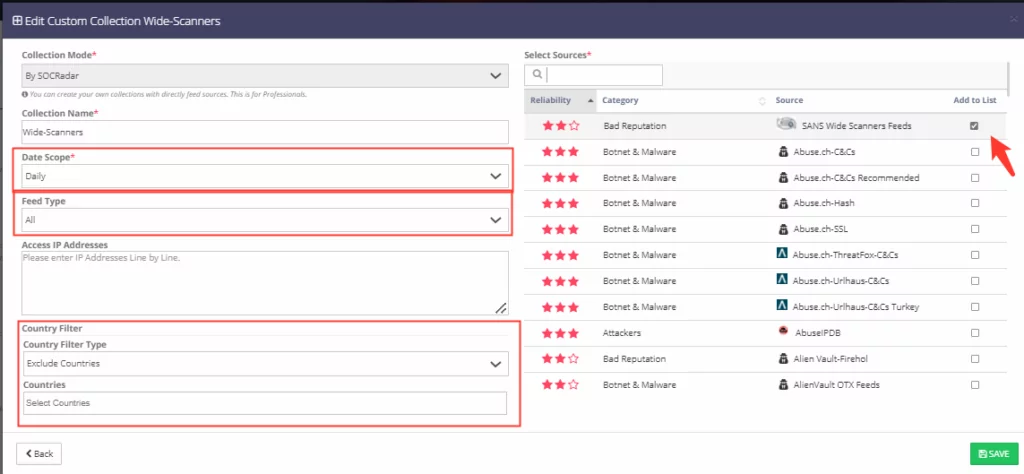
In addition to SOCRadar’s recommended lists, you can create feed lists specific to the rules you will apply to your company from the feeds provided by over 115+ different sources and SOCRadar’s honeypots in 12 other countries and 15+ locations.
You can apply filters to these manual lists, such as country (IOCs belonging or not belonging to added countries), frequency (daily, weekly), and validation (IPv4, MD5, URL, SH256, etc.).
You can integrate them into your security products (SIEM, SOAR, XDR, EDR, FW, etc.) with MISP Server and Endpoint API. If your products receive feeds only with TAXII support, you can integrate SOCRadar Recommended Feed lists with SOCRadar TAXII Server service.
For example, let’s consider that you receive a feed from AlientVaut. Possible questions about the feed are:
-Does it go through the Whitelist Policy?
-How big is the whitelist’s data? Does it include all cases? Does it go through validation (IP, Hostname, Hash, SHA256, MD5, etc.)?
If your answer is not enough, SOCRadar passes all IOCs through 43+ million whitelists and various validations (IP, Hash, domain, SHA256, etc.). You can create multi-country filters on your feeds without the need to create country-based rules.
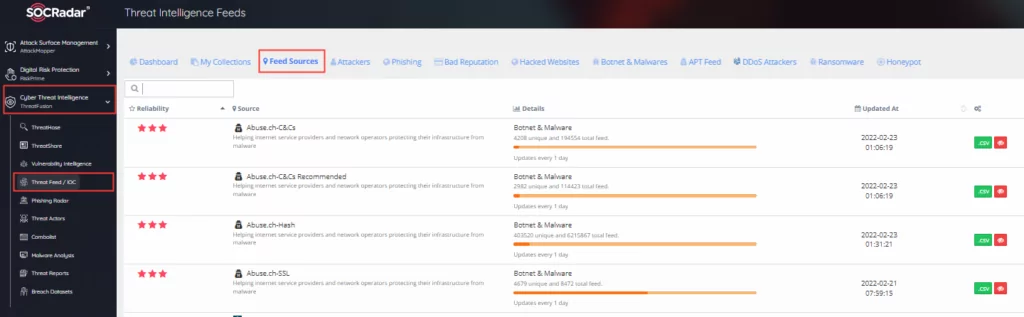
You can check the details of 115+ feeds offered on the platform from Cyber Threat Intelligence ->Threat Feed / IOC->Feed Sources Tab, and check the latest updated feeds.
For more information on the ThreatFeed/IOC API, you can refer to our Threat Feeds/IOC API – SOCRadar Docs and contact the [email protected] team for integration (if within license/package).
4. SOCRadar Threathose & Malware Analysis API
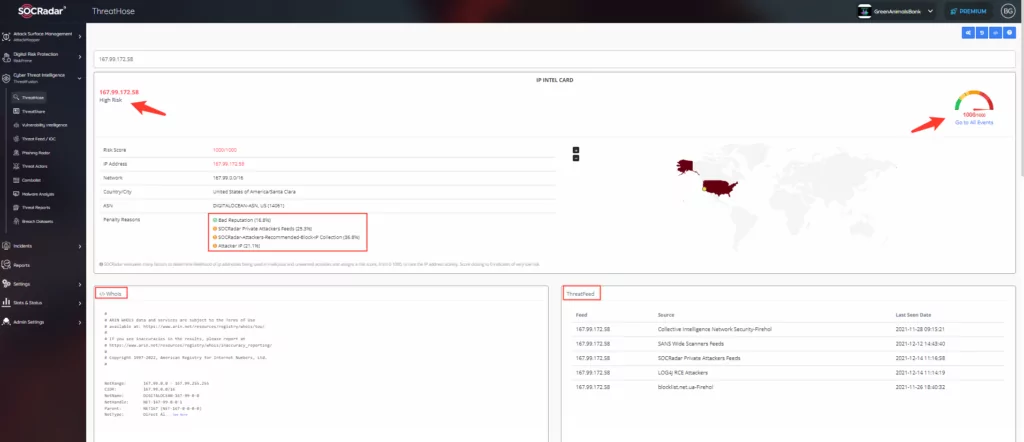
Thanks to the SOCRadar Threathose module, you can access SOCRadar’s big data and get IP and Hash Score, query account information in Combolists, hacker forums, and stealer logs (log records from computers that have turned into botnets).
You can also make a keyword search in the public bucket and public repositories on information obtained from the dark web and whether it is mentioned in tweets and cybersecurity news.
With SOCRadar Threathose, you can also access geolocation, ASN, Whois record, subdomain and DNS records, IP-oriented ASN, geolocation, Whois record, passive DNS record.
Threathose is a large data repository where you can access information like this. By integrating the API with your SOAR products, you can present your threat hunters using your SOAR products with a data pool to check known malicious IP addresses, malware, IOC findings. We have APP/Connectors in Cortex SOAR, Sumo Logic, and FortiSOAR products.
With the Malware Analysis API additional package purchase, You can make queries to Shodan and VirusTotal in addition to SOCRada Big Data. This API also allows malware analysis of your platform-independent files.
5. How Can You Avoid Potential Attacks with SOCRadar Integrations?
Alerts about your digital assets that SOCRadar is tracking are instantly transmitted to your relevant teams (network, fraud, AD Teams, brand violation, etc.) according to the need-to-know principle.
Thus, taking action is accelerated to detect and eliminate threats to your digital assets, which are becoming increasingly difficult to track. In this way, it is possible to take proactive action against transactions, vulnerabilities, and threats that may damage the brand’s reputation due to the delay.
Suppose your customer, VIP, and employee accounts are leaked in any way without wasting time with the automated rules you set in the Active Directory. In that case, you will prevent any possible damage to the brand reputation and leaks to the system.
You can feed your security solutions with an additional 115+ IOC feeds (vulnerabilities scanners, DDoS, Botnet C&C, APT groups, Log4j scanning IPs) to SOCRadar’s recommended lists.
In this way, you will ease the burden on your security teams and prevent possible attacks by cyber threat actors. You can support your multiple security structure by feeding not only a single security solution but also your EDR, SIEM, FW, and SOAR products. In the integrations created by SOCRadar, your security products do not need any account information.
SOCRadar Extended Threathose API enables your Threat Hunting teams to make quick decisions by accessing SOCRadar’s big data, looking at IP scores and hashes, ASN/GEO location of IPs, whitelist/blacklist status, passive DNS information, domain information.
SOCRadar also provides the big data pool to your Threat Hunting teams’ needs with the Extended Threat Intelligence structure of SOCRadar. And also provides data from Shodan and VirusTotal with the Malware Analysis API, enabling a faster, more effective, and accurate response to cyber incidents.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Get free access

































