
MFA Bypass Techniques: How Does it Work?
Identification and authentication are the first phase of verification in the login processes of Information Systems. Malicious threat actors use various methods, such as brute force to pass this phase unauthorized. Authentication solutions are named by the number of factors used in the process. Single-Factor Authentication (SFA) requires only one element (e.g., password) to authenticate the login. The name of the authentication process will turn into Two-Factor Authentication (2FA) if two factors (randomly generated code etc.) are required, then named Multi-Factor Authentication if more than two elements are needed to verify. Security experts recommend using two or rather Multifactor Authentication (MFA) solutions in login processes.
Additionally, there are two authentication types which are in-band and out-of-band authentication. It is called in-band authentication if the identity check is made in the same system or communication channel. A login page requests a security code on the same page is an example of in-band authentication. When the authentication factor is sent over a different system or channel, such as approving the login from another application or entering a pin from a separate location is out-of-band authentication.
What is Multifactor Authentication?
Multifactor Authentication (MFA) is a security approach that uses multiple verification methods to authenticate the user to access their profile, system, etc. MFA adds a new layer to the authentication process, strengthening security. Infrastructures and endpoint devices can be safer and more secure using protection methods such as MFA.
Why Do We Need MFA?
Verifying user identity using MFA became essential because threat actors have been using stolen or exploited user credentials, and another layer must deny connection by unauthenticated ones.
We understand that there is a need for another factor, but why do we need “Multi-factor” Authentication? Single-factor Authentication (SFA) requires only one piece of evidence to authorize the user, primarily passwords. Brute force attacks or stealing credentials bypasses the SFA technology; we need another factor to add a layer to this security process.
Multifactor Authentication (MFA) is a technique that requires more than one piece of evidence to authorize the user. If two pieces of evidence are needed to verify, this approach is called Two-factor Authentication (2FA) or 2-step verification. It depends if asked how many factors we need to be more secure, but it is known that 2FA or MFA is more secure than SFA. The difference between 2FA and MFA is that 2FA requires only two factors; on the other hand, MFA can add more layers until the login attempts do not seem suspicious anymore.
What are the Types of MFA?
There are three main types of Authentication factors that work with MFA:
- The first is Knowledge Factor (something you know), which is anything the user knows to verify its identity. This could be a password, credit card PIN, or One-time Password (OTPs).
- Another one is the Possession factor (something you have) which means any tool the user uses to verify itself. It could be a security token such as a smart card, a USB flash drive, a wireless tag, or one of the mobile authentication methods such as a mobile app, text message, or an automatic phone call directly to the user.
- The last MFA factor is called the Inherence Factor (something you are), which only the user has to verify biologically. This could be a retina or an iris scan, fingerprint, user’s voice, or the user itself to recognize its face.
Top 10 Most Commonly Used MFA Bypass Techniques
Although MFA is much more secure than other authentication solutions, it can be bypassed by various techniques. These techniques can be categorized into three main groups: Social engineering techniques, technical methods, and a mixture of both.
Social Engineering techniques are generally non-technical to MFA itself that exploit human error.
- Stealing the victim’s security/recovery questions’ answers with a fake website using phishing is a widespread technique to bypass the MFA.
- Attackers usually concoct a story (such as the victim losing their phone or being in a hurry to get access) by acting like the victim itself and trying to disable the MFA or gain access by contacting tech support of the firm.
Technical approaches to bypass MFA usually exploit MFA itself or steal credentials using various techniques to eliminate the victim’s MFA.
- Skimming is used in Automated Teller Machines (ATMs) when stealing people’s credit card credentials by directly bypassing Factored Authentication.
- The victim could be using an already hacked device, or the attacker could get admin access. The attacker could do anything that the device’s user can typically do. This technique is known as the Man-in-the-Endpoint Attack.
- Attackers also use the single sign-on technique, which uses the sharing authentication systems. If a website that does not use MFA is connected with another website that requires MFA to log in, the attacker prefers the one without authentication service to gain access to another.

- Using authorization code flaws (also known as Response Manipulation or Status Code Manipulation) to bypass is another common way to eliminate MFA; if the response is like “Success: false,” turning it to “Success: true” may work to bypass or change the status code to 200 (OK) from 401, 402, 403, etc.
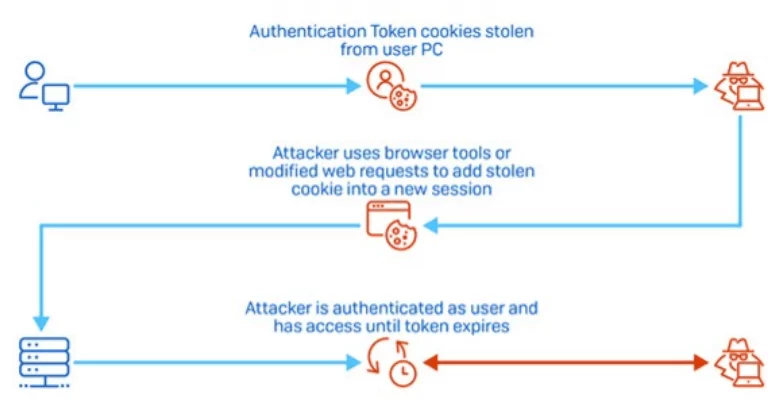
- Stealing a victim’s session cookie and bypassing the MFA with the stolen cookie, also known as the pass-the-cookie attack, is increasingly used by attackers nowadays.
- Some MFA applications use One-Time Passwords (OTPs). OTP displays a randomly generated number from a predetermined “seed value,” and the authentication system waits for the user to enter the code to verify the identity. The attacker can generate its OTP code to bypass the MFA if the attacker accesses this seed value. This process is known as duplicate code generating.
- Another bypass technique is the SMS Swap scam (Simjacking). Usually, people contact the provider to get their SIM information back when their phone is stolen or lost. Attackers currently use this idea as they know the victim’s personal information well. They contact the providers using the gathered credentials of the victim and port a phone number to another device the victim does not own. In this way, the attackers can steal codes generated by SMS-based MFA.
- MFA Fatigue is one of the most recent techniques to bypass MFA and is becoming a common technique among attackers. It seems like a brute force attack; the attacker sends many access notifications until the victim approves.
What are the Recent Cyber Incidents That Happened Using MFA Bypasses?
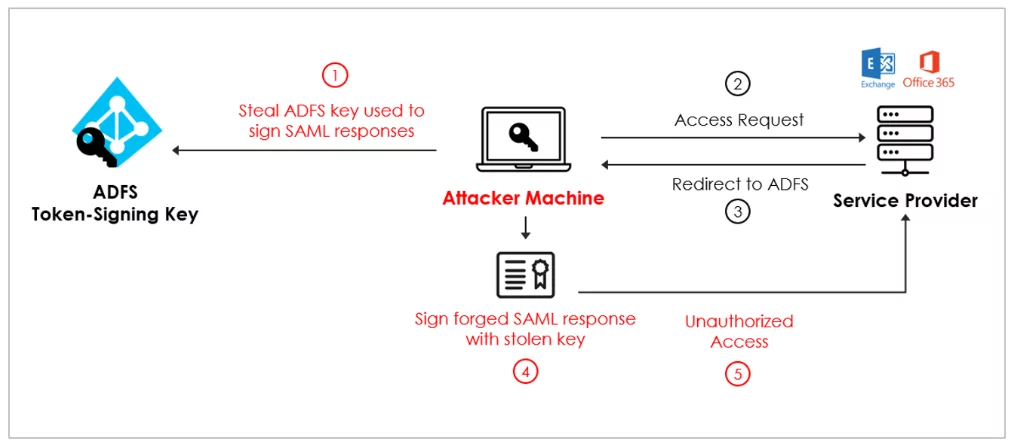
There is an attack called Golden SAML, which bypasses the authentication process compromising the SAML signing certificate. The Security Assertion Markup Language, or SAML, is a protocol for exchanging authentication and authorization data between identity and service providers. This attack starts with the attacker’s access to Active Directory Federation Services (AD FS) -a service in a domain that gives other service providers in the federation access to domain user identities. – server and extract private key and certificate. Then the attacker signs a forged SAML response using the stolen key and accesses unauthorized. In 2020, the SolarWinds Orion compromise was the first appearance of using the Golden SAML attack.
The recent attack on Cisco Systems by a ransomware group Yanluowang used voice phishing (vishing) and the MFA Fatigue technique to access the victim’s computer. Another attack happened in Mid-September 2022 to video game developer Rockstar Games, and the same initial access method (MFA Fatigue) was used as well as Cisco’s recent attack.
Recommendations for Using MFA
- MFA provides maximum security to a system; enable MFA if possible.
- Do not use SMS-based MFA because attackers can bypass it easily. Implementing the necessary security solutions is critical if SMS-based MFA is needed to be used.
- Be aware of rogue links and always check the URLs, and sometimes the attackers send short URLs (For Example, bit[.]ly/XXXX, cutt[.]ly/XXXX, etc.), expanding the URL before clicking will be much safer.
- Make sure MFA limits the number of failed authentication attempts and has an account-locking ability. In addition to that, monitor authentication attempts regularly.
- Use a firm password policy, such as creating a minimum 12 characters long password with upper-lower cases and special characters. Do not use words in the dictionary when creating a password.
- Do not reuse your passwords.
- Prefer biometric authentication (fingerprint, facial detection, voice detection, etc.) as one factor in the authentication process. It will be more secure than the generated codes.
How Can SOCRadar Help?
It could be one of the most secure ways, but we cannot say using MFA makes us cyber-attack-proof. Most of the bypass techniques are made by exploiting human error. MFA can not prevent the success of social engineering attacks.
People should be aware of social engineering attacks such as phishing, shoulder surfing, etc. Self-awareness may not be adequate regarding company-wide risks but taking Cyber Security Awareness training is vital for reducing the success rate of attacks. Cyber Threat Intelligence (CTI) comes to mind because unknown threats become known with dark web intelligence. SOCRadar’s CTI tools can help you boost your resiliency against social engineering attacks by providing malicious phishing domains.




































