The 8 Key Lessons From the SolarWinds Attacks
[Update] October 31, 2023: See the subheading: “Repercussions of SolarWinds Attacks: SEC Charges for Fraud.”
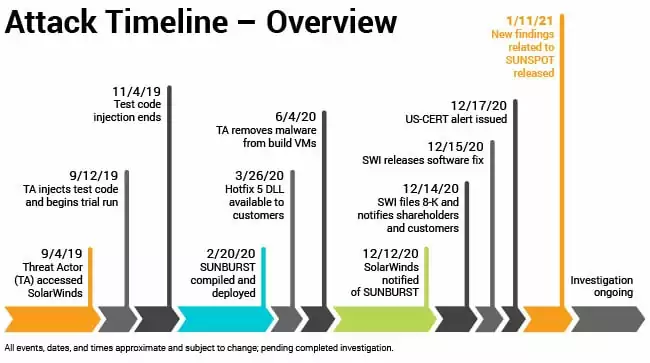
Nation-state threat actors breached the supply chain of SolarWinds to infiltrate its customers including U.S. government agencies and Fortune 500 companies. At least 18,000 organizations likely downloaded the malicious update, and thus suffered in the SolarWinds Orion Breach.[1]
On December 13, 2020, the security vendor FireEye provided details on a supply chain attack campaign involving a malicious software update of the SolarWinds Orion platform, which is used by organizations to monitor and manage IT infrastructure. FireEye named the campaign UNC2452 and has further named the backdoor as SUNBURST (Microsoft has labeled it SOLORIGATE). SolarWinds has also issued an advisory for this critical incident.
What happened?
At the end of 2020, malicious SolarWinds software has also infected more than a dozen critical infrastructure companies in the electric, oil, and manufacturing industries that were also running the software. Original Equipment Manufacturers (OEMs) have remote access to critical parts, install new software, or even control critical operations. This means that hackers who breached the OEMs could potentially use their credentials to control critical customer processes.
Threat actors – claimed to be linked to Russia’s Hacker Group APT 29 a.k.a “Cozy Bear” – breached the U.S. Treasury and Commerce departments, along with other government agencies, as part of a global espionage campaign that stretches back to March 2020. The actors behind this campaign gained access to numerous public and private organizations around the world via malicious updates to SolarWinds Orion IT monitoring and management software. The U.S. National Security Council held an emergency meeting to discuss the situation.
Here are reported victims of the SolarWinds hack so far;[2]
- US Department of Defense
- US Department of Energy
- US Department of Commerce
- US Department of Health and Human Services
- US Department of Homeland Security
- US Department of State
- US Department of Treasury
- Belkin International
- California Department of State Hospitals
- Cisco
- Cox Communications
- Deloitte
- Digital Sense
- FireEye
- Intel
- ITPS
- Kent State University
- Microsoft
- Netdecisions
- Nvidia
- Pima County, State of Arizona
- SolarWinds
- Stratus Networks
- VMware
Why did it happen?
Because they have access to most systems on the network including critical servers. Network Management Systems (NMS) use SNMP or an installed agent to learn the status of remote devices and in addition to this, they can manage and modify configurations, etc.
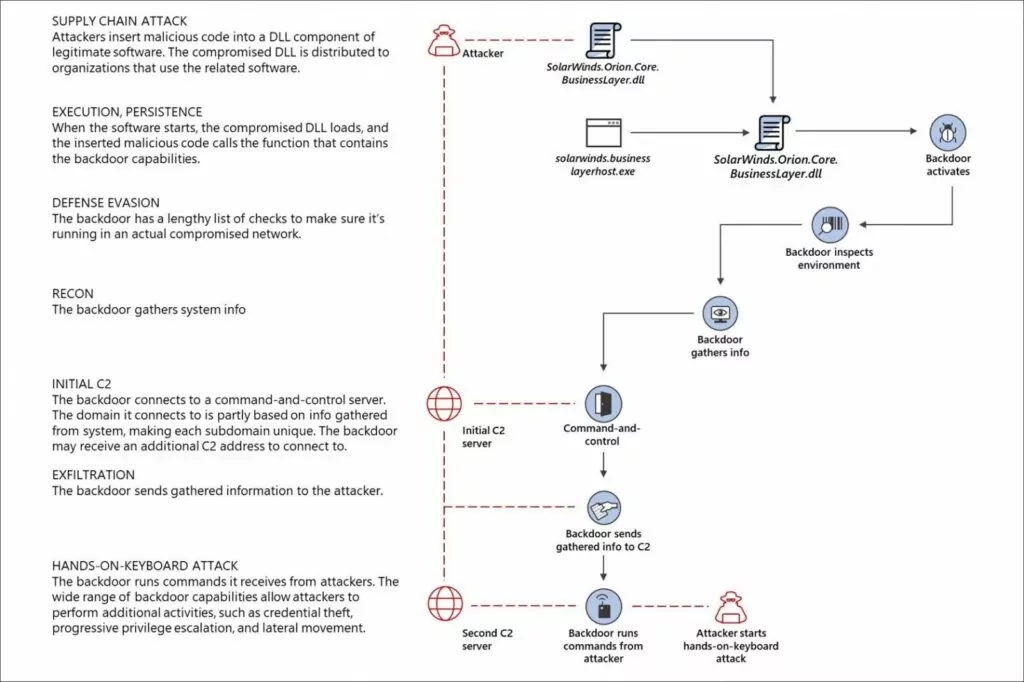
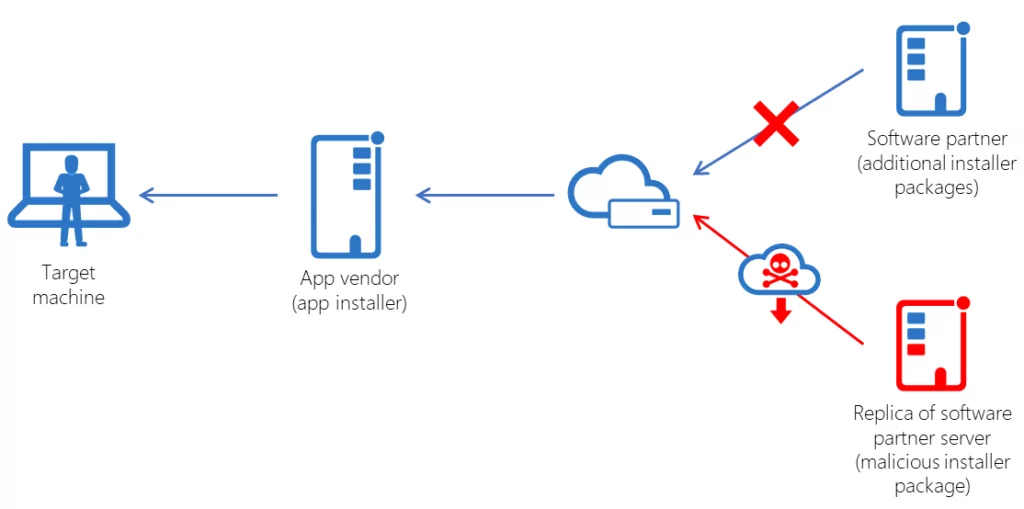
What’s supply chain attack?
Supply chain attacks, also known as third party attacks, occur when someone enters a system through a third party, such as a supplier, service provider, or vendor. The attack surface of the typical company has changed dramatically in recent years, as more suppliers and service providers than ever before touch sensitive data. With increased public awareness and oversight, the risks associated with supply chain attacks are higher today than at any time in history.
Lessons learned from the SolarWinds attacks
Many businesses fail to recognize or monitor their third-party tech vendors’ compliance policies in operation. And if organizations have the resources to follow it, it always takes too much risk for consumers (or anybody) to expose device access or compliance tactics, not to mention the additional expense of revealing it from the viewpoint of tech vendors. But what we have learned from the SolarWinds Attacks? Let’s take a look at it.
1. Practicing defense in depth
Defense-in-depth is a cybersecurity strategy that uses a number of layered, redundant defenses to protect itself from a variety of threats such as cyber-attacks, cyber espionage, and ransomware attacks. When one security check fails, the next layer of security thwarts a potential cyber attack before the potential of another.
The term “defense-in-depth “ is used to describe a multi-layered security architecture that includes the use of technology. The idea is to combine technology components with good security management practices to create protective layers that reduce the risk of attack and intrusion.
SolarWinds attacks reminded us how a defense-in-depth strategy can prevent the attacks from spreading that much.
2. Harden on-premises systems
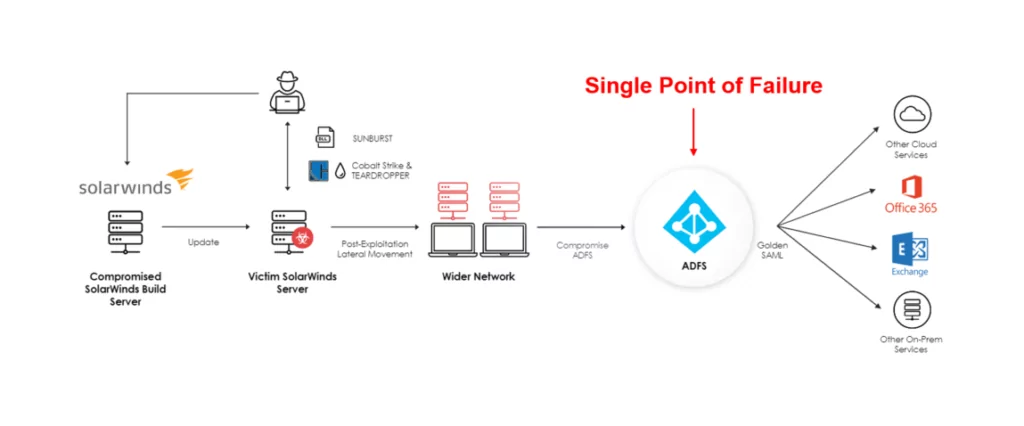
The ability of actors to conduct this attack hinges on the initial compromise of customer on-premises systems. Without administrative access to the on-premises identity provider, actors would not be able to generate tokens for use in the cloud.
Strongly consider deploying a FIPS validated Hardware Security Module (HSM) to store on-premises token signing certificate private keys. An HSM, aggressively updated, makes it very difficult for actors who have compromised the system to steal the private keys and use them outside of the network.
3. Adopting a long-term, programmatic approach to supply chain security
Attacks on software supply chains are insidious because they abuse trust between vendors and their customers and cause damage to both parties. Organizations must develop or adopt a long-term, programmatic approach and strategy to supply chain security. Such an approach should be based on sound risk management best practices, such as NIST’s Cyber Supply Chain Risk Management (C-SCRM) guidance.[3]
4. Using cyber threat intelligence platform is a must
The skilled, well-funded, well-organized, and highly-sophisticated cyber attackers use techniques that reveal security strategies to the technology alone. In order to develop a defense strategy against attackers, organizations need to know how hackers operate, how they function, and what techniques they use.
Cyber-threat intelligence allows companies to identify the dynamics and consequences of risks, to improve security plans, structures, and to reduce their attack potential to minimize damage and defend their network.
5. Effective use of static application security testing (SAST)
SAST tools are designed to detect backdoor code. SAST detection is somewhat difficult, but because of the front-end oriented nature of dynamic testing, dynamic application security testing DAST detection is largely impossible. Owing to a backlog of SAST bugs that could lead to a warning of a possible loophole, which could have never been checked by SolarWinds.
6. Securing SIEM solutions
SIEM facilitates accelerated vulnerability monitoring, which in turn helps to reduce security breaches across the entire IT infrastructure of an organization. The faster the risks are detected, the faster the solution can be, and hence the more stable the IT processes of the company.
7. Using behavioral analytics-based threat detection
It is important to note that the preliminary detection of the SolarWinds compromise by FireEye did not notice complicated lateral movements or even data exfiltration.
What prompted FireEye’s in-depth investigation was an odd remote user login from a previously unknown computer with an IP address in a suspicious location. It was only after the further analysis that FireEye found the interference and eventually tracked it back to SolarWinds.
Behavioral analytics can factor in a wide variety of data points — such as peer groups, IP association, personal email addresses, and kinetic identifiers like badge reader activity to identify a malicious intrusion by stitching together a half dozen or more events.
8. Multi-factor authentication (MFA) is not secure as you think
According to a write up issued by the National Security Agency (NSA)[4], the attackers succeeded to “compromise on-premises components of a federated SSO infrastructure and steal the credential or private key that is used to sign Security Assertion Markup Language (SAML) tokens. Using the private keys, the actors then forge[d] trusted authentication tokens to access cloud resources.”
In short, the attackers ran laps around the multi-factor authentication (MFA) security, effectively creating their own authentication tokens that allowed them access to continuing their intrusion.
Summary
This sophisticated cyber-attack is yet another example of why organizations, regardless of size, must implement cyber hygiene best practices. CIS has a number of longer-term operational and strategic recommendations.[5]
- Ensure cybersecurity is a conversation occurring at the highest levels of executive leadership. Cybersecurity is not an IT problem, it is an enterprise-wide risk management topic that requires attention.
- Monitor for high-risk events such as account creations, privilege escalation, new services created, security-related services disabled, changes to security posture, unusual network communications, etc.
- Deploy endpoint protection tools to all hosts and mobile devices. Depending on experience level and budget, consider solutions such as Endpoint Detection and Response (EDR), or a more inclusive Endpoint Protection Platform (EPP). If in-house resources don’t allow this, consider outsourcing to CIS or another MSSP for monitoring and administration.
- Become familiar with the CIS Controls and implement them according to the level of risk for the organization. Organizations must have a minimum level of cybersecurity to help mitigate threats like this in the future.
- Implement a risk-based vulnerability management program that includes patching timelines, accounting for the criticality of assets and of the vulnerabilities.
- Sign up for the monthly vulnerability scans conducted by DHS for another view of risk from an outsider’s perspective. Be sure to select the option to give the MS- and EI-ISAC access to the scan results so we can monitor for exploitation and understand the threat landscape.
- Ensure all staff have annual cybersecurity awareness training and that policies exist to provide administrative controls over areas that cannot be controlled with a technical solution.
- Implement monitoring and logging capabilities for endpoints and network infrastructure.
- Update (or create if none exists) the Incident Response (IR) protocol for the organization, and include organizations outside of IT such as public information, human resources, legal, executive leadership, and functional organizations. Be sure to include critical vendors and requirements for data and service restorations along with many other considerations. Practice the plan before it is needed through the use of tabletop exercises.
- Utilize CIS or another third party to perform internal vulnerability assessments and penetration testing to provide IT and leadership an unbiased snapshot of the current risks and condition of the organization’s cybersecurity posture.
- Detect and monitor if administrative privileges have been granted and to whom.
- Adapt Least-privileged accounts.
- Detect when privileges are granted to service accountsapplication.
- Regulate excessive service accountapplication activities across granted privileges.
- Historically determine whether such an event has occurred, creating actionable logs.
- Regulate token usage (tokens provided vs tokens used) and prevent Golden SAML attacks and similar token attacks.
- With these capabilities, organizations can better protect themselves from attempts to escalate privileges should they make it past the outer defenses, alerting to dangers and mitigating risk.
With these capabilities, organizations can better protect themselves from attempts to escalate privileges should they make it past the outer defenses, alerting to dangers and mitigating risk.
Repercussions of SolarWinds Attacks: SEC Charges for Fraud
The U.S. Securities and Exchange Commission (SEC) has taken significant action against SolarWinds Corporation and its chief information security officer (CISO) by charging them with fraud and internal control failures. This move has substantial implications for the cybersecurity landscape.
The SEC’s complaint alleges that SolarWinds and its CISO misled investors about the company’s cybersecurity practices, concealing known risks, at least from October 2018, through December 2020. This period includes the disclosure of the massive, nearly two-year-long “SUNBURST” cyberattack, during which, SEC states that SolarWinds presented investors with vague, hypothetical risks while internally being aware of specific cybersecurity deficiencies and escalating risks.
The complaint highlights the contradiction between SolarWinds’ public statements on its cybersecurity practices and internal assessments. An internal 2018 presentation flagged the insecurity of the company’s remote access setup, posing risks of reputation and financial loss. Furthermore, the CISO was aware of these vulnerabilities but failed to address them adequately, resulting in security gaps. This failure to mitigate risks left SolarWinds unable to provide sufficient protection for its key assets, including the SolarWinds Orion.
The SEC has recently introduced new rules concerning the disclosure of cyber incidents, underscoring the importance of transparency and accountability in cybersecurity efforts. This enforcement action against SolarWinds emphasizes the critical need for organizations to comply with these rules while demonstrating the repercussions of non-compliance. It sends a clear message to other companies to implement robust controls tailored to their risk environments while maintaining transparency in informing investors about known concerns.
For full details on the SEC’s action, refer to the official press release.
Prevent future cyber incidents with SOCRadar
To reduce the impact, SOCRadar’s customers can utilize Vulnerability Tracking and Threat Feeds/IOCs screens which can help you quickly take action when this kind of critical security incident happens. You can easily enter the product names within your asset inventory or keywords you’d like to monitor for vulnerability incidents and critical flaws. Then the platform will generate an email alert and deliver it right into your inbox whenever there are new updates, tweets or news found across the surface, deep and dark web. IOCs associated with threat actors or APT groups can be also provided through SOCRadar API.
For protection against supply chain attacks, SOCRadar also continuously monitors code repositories like GitHub to make sure your intellectual property or important credentials are not exposed or forgotten publicly.
Discover SOCRadar® Community Edition for free
With SOCRadar® Community Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
References
[1] SolarWinds Hack Could Affect 18K Customers, KrebsOnSecurity
[2] Here Are 24 Reported Victims Of The SolarWinds Hack (So Far), CRN
[3] Cyber Supply Chain Risk Management (C-SCRM), NIST
[4] Detecting Abuse of Authentication Mechanisms, NSA
[5] The SolarWinds Cyber-Attack: What You Need to Know, CIS
Featured image by Pexels