Finance Threat Landscape Report: 17.5M Credit Card Numbers Sold on Blackmarket
The dark web’s levels of anonymity make it the ideal hub for all kinds of cybercrime activity. Finance is one of the critical industries that dark web threats impact, and threat actors frequently highlight it in data theft or leak posts.
Credit card numbers, employee PII, banking, and customer databases are frequently among the exposed data on offer. 17.5 million credit card numbers were sold on black markets and dark web hacker forums until September 2022.
So far in 2022, the finance industry was almost always the top posting category in dark web forums monitored by SOCRadar. Click the button below to download the full report.
With the increasing usage of the internet, financial services, and fintech applications, the finance industry is a large attack surface for hackers to abuse.
Threat Actors’ Motives
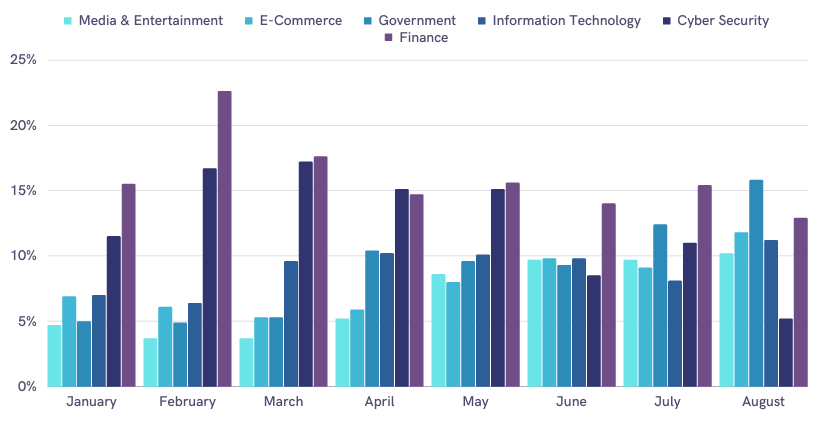
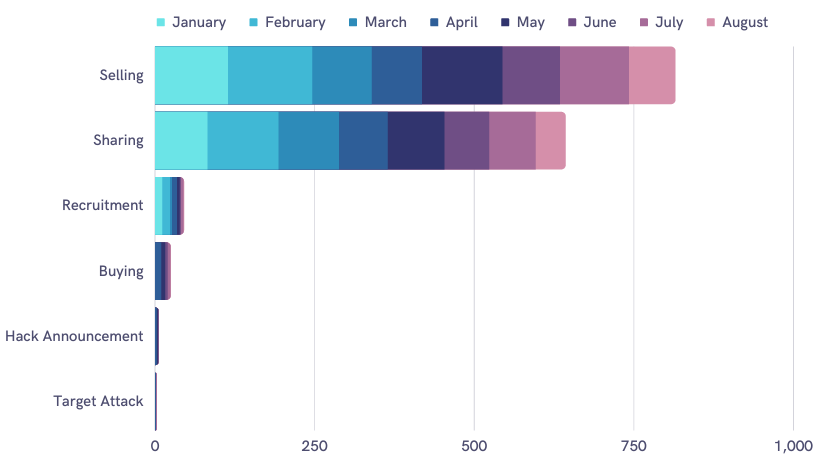
A threat actor could distribute the sensitive data they have gathered in various ways. In the first eight months of 2022, SOCRadar discovered that threat actors in the dark web usually posted about selling or sharing finance-related data. There also were other posts in which they looked to recruit attackers or buy data.
Dark Web Threats Targeting Finance Industry
Cybercrime forums attract a wide range of threat actors, from novices to skilled hackers. To make a profit or carry out their attacks, these threat actors seek information among millions of pieces of data available on the dark web.
- Phishing: Threat actors can use leaked information on the dark web, such as customer email addresses, bank names, and phone numbers, to conduct phishing attacks.
- Data Leak: Threat actors often sell or share data free of charge. Some who leak data may also have ulterior motives, such as covering up their tracks after an attack in which they have already used the data.
- Vulnerabilities: Threat actors sell unauthorized network access information, such as VPN or remote access, and vulnerability exploits, like SQL injections, on the dark web. Malware operators and various other attackers may be able to use this information to cause more harm.
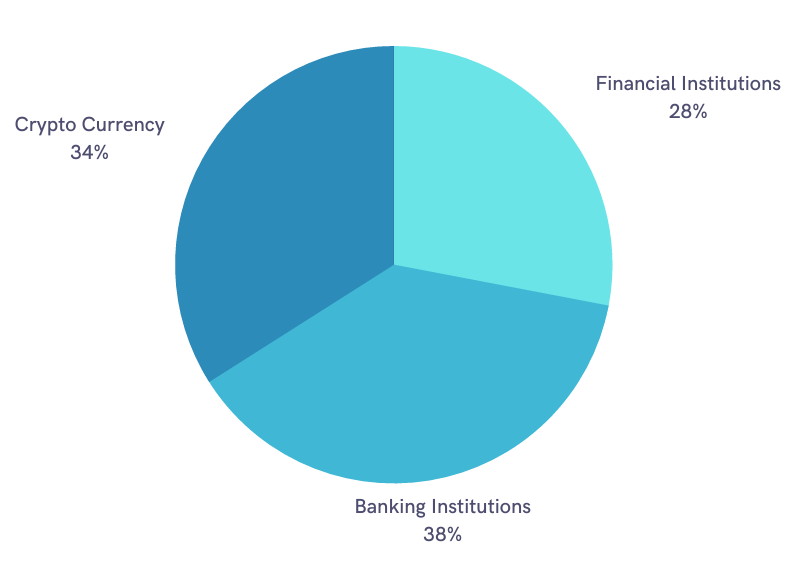
- Ransomware: Data published through ransomware operations can also threaten finance industries. SOCRadar CTIA Team analyzed that in 2022, about 4.5% of ransomware posts published in dark web forums and Telegram channels were related to the finance industry, targeted at financial and banking institutions and cryptocurrency.
To investigate these risks, our research team examined indicators found by DarkMirror. DarkMirror is a tool by SOCRadar, to monitor and collect activities on the dark web forums, channels, and leak sites, fed by more than 9,500 entries to define the finance industry’s threat landscape.
Protect your brand against dark web threats. Find out more in SOCRadar’s 2022 Financial Industry Threat Landscape Report.
Dark Web Mentions in 2022 (by DarkMirror)
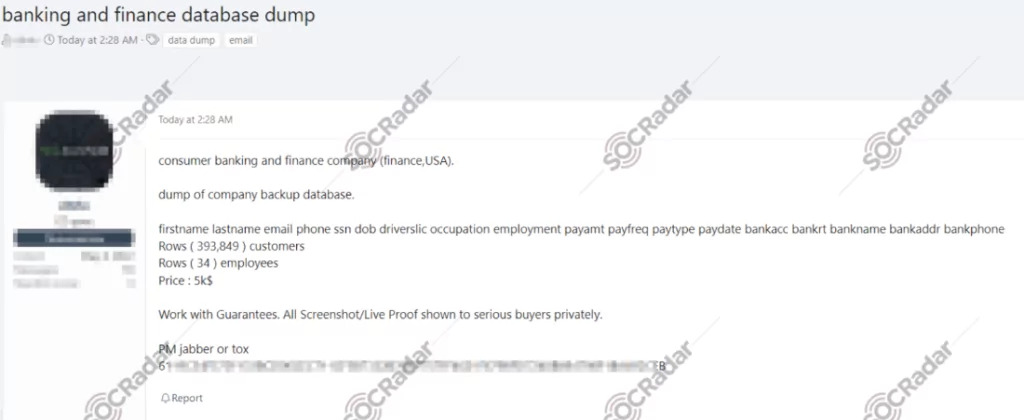
- Threat actors dumped the backup database of a banking and finance company in the U.S. in a hacking forum. The database includes the personal and financial information of 34 employees and nearly 400,000 customers.
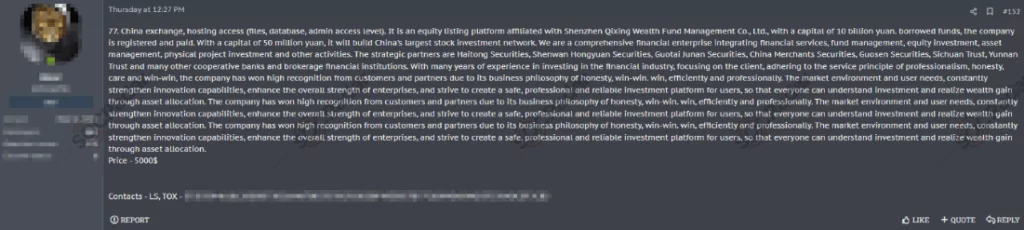
- An unauthorized network access sale is detected, allegedly belonging to an exchange company that operates in China.
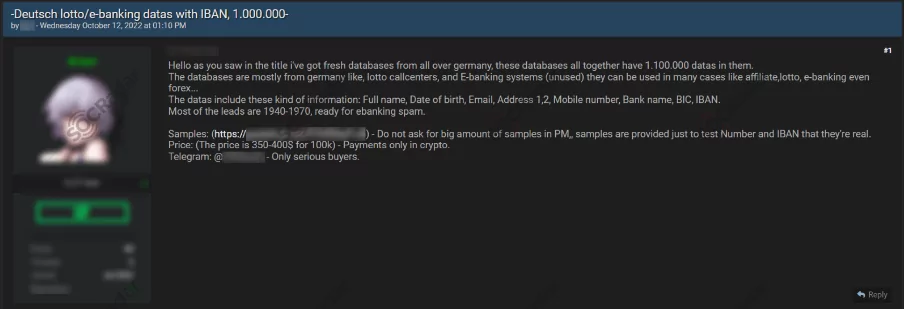
- A database of 1.1 million pieces of data for German bank leads is on sale, including information such as names, emails, bank names, and IBANs.
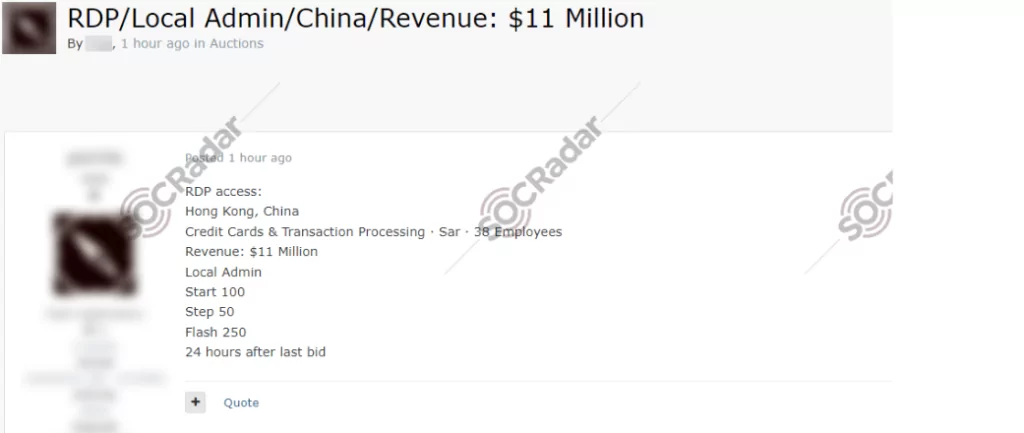
- Unauthorized RDP access was auctioned in a dark web forum, allegedly belonging to a credit card processing company that operates in China.
- A stealer log purchasing announcement by a potential threat actor was detected for Chase Bank and Wells Fargo.

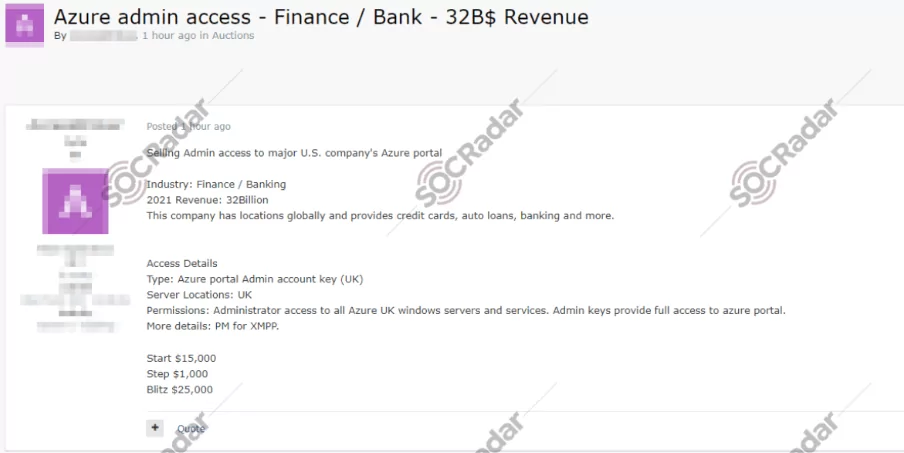
- An unauthorized admin access sale for the Azure portal of an allegedly major bank in the U.S. was detected.