
How Did Cisco Get Hacked, What Was Leaked, and What Did We Learn?
1-Is Cisco really hacked?
On Tuesday evening, August 10, the Yanluowang ransomware group (linked to Lapsus$ extortion group) claimed to have hacked Cisco and will release its files. Two hours after this claim, Cisco published a detailed statement about the case on its official blog. Cisco has announced that it has experienced a partial cyber incident through an employee, albeit late. The detection date of the attack was stated as May 24, 2022.
In this short informative article, you’ll find the answers of how Cisco was hacked and what lessons can be learned from this attack.
2-How did the incident take place? What is the initial access vector?
According to the published blog post, threat actors seized the personal Google account of a Cisco employee -probably by a stealer log- and attempted to log in to the systems using the password to the corporate network. Then, with this account information, remote access was obtained via VPN to the systems.
Following initial access, the threat actor registered new devices for MFA and verified their identity with the Cisco VPN. The Citrix environment was compromised, and the attacker elevated administrative privileges and gained privileged access to domain controllers. The threat actor dropped several tools and payloads to carry out malicious activity.
The first payload is a backdoor that receives instructions from the C2 server and uses the Windows Command Processor to carry them out on the target system. There are two commands included in backdoors for stealth: one of them is the WIPE command, which wipes the last executed command from memory through the backdoor, and the other command is DELETE_SELF, which deletes the backdoor.
Threat actors dumped NTDS from controllers using ntdsutil[.]exe, then exfiltrated the dumped NTDS to the compromised VPN system. This way, they accessed credential databases and were able to move laterally in the network. Using the net[.]exe commands of Windows, a new administrative user named z was created and added to the local admin group.
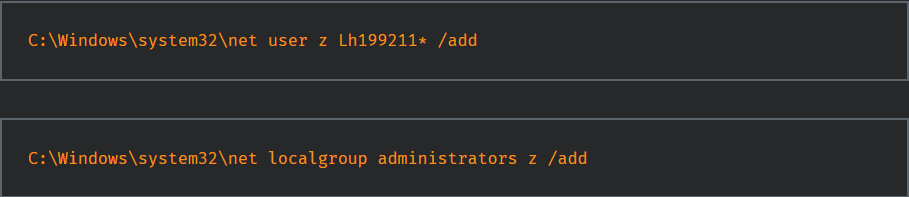
The created user was used to deploy enumeration tools like AdFind and SecretsDump to gather more information.
The attacker deleted the previously established local administrator account and event logs to erase the evidence.
It was observed that they installed RAT tools like TeamViewer and LogMeIn and enabled RDP access to move files inside the environment.
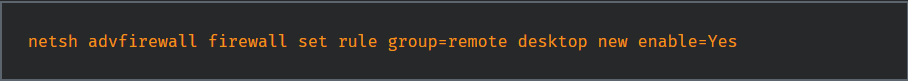
Windows logon bypass was leveraged to maintain a presence in the system with elevated privileges. Registry keys were added remotely using PSEXESVC[.]exe.
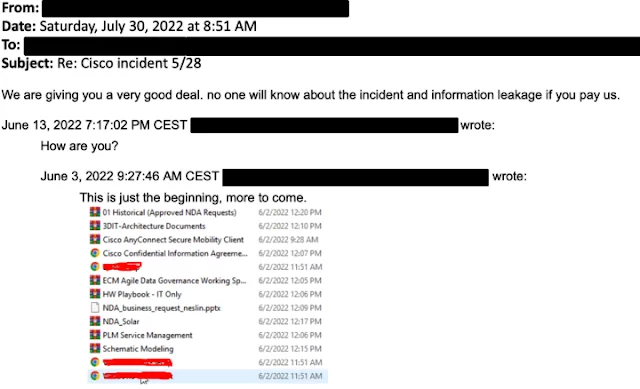
The threat actors tried to exfiltrate data during their presence. They could only exfiltrate non-sensitive Box folder data linked to a compromised employee account.
Their efforts to gain access persisted after Cisco completely removed them from the environment. They then tried to communicate via email and sent Cisco a screenshot of exfiltrated Box data.
If you want to find out if the corporate accounts have been shared on the Dark Web, you can use SOCRadar’s free Deep Web Report service.
3-Cisco doesn’t use multi-factor authentication? How could it be circumvented?
By using voice phishing and similar MFA (multi-factor authentication) bypass techniques, the attacker group managed to receive/confirm the verification code received by the user. With this method, it has completed VPN access to the network.
Check here for detailed information on the commonly used MFA Fatigue method to bypass multi-factor authentication.
4-Did threat actors access internal systems and source codes?
After obtaining VPN access, the attacker took over the active directory accounts, tried to put them on the internet, and was successful. Cybersecurity experts think that the attacker who took over the active directory administrator account may have access to many different systems.
5-Which threat actors might have carried out this sophisticated attack?
Allegedly, UNC2447, Lapsus$, and Yanluowang ransomware group may be the actors behind this attack. The threat actor that announced that it would release the data is the Yanluowang ransomware group.
6-What are the tools and TTPs used in the attack?
The tools used in the attack are not much different from what the attackers have used frequently for the past five years.
In addition to LogMeIn and TeamViewer, offensive security tools such as Cobalt Strike, PowerSploit, Mimikatz, and Impacket are used by attackers. The TTPs of threat actors are as follows.
- Initial Access
- Execution
- Persistence
- ATT&CK Technique: Create Account: Local Account (T1136.001)
- ATT&CK Technique: Account Manipulation: Device Registration (T1098.005)
- Privilege Escalation
- Credential Access
- ATT&CK Technique: OS Credential Dumping: LSASS Memory (T1003.001)
- ATT&CK Technique: OS Credential Dumping: Security Account Manager (T1003.002)
- ATT&CK Technique: OS Credential Dumping: NTDS (T1003.003)
- ATT&CK Technique: Multi-Factor Authentication Request Generation (T1621)
- Lateral Movement
- Discovery
- Command and Control
- ATT&CK Technique: Application Layer Protocol: Web Protocols (T1071.001)
- ATT&CK Technique: Remote Access Software (T1219)
- ATT&CK Technique: Encrypted Channel: Asymmetric Cryptography (T1573.002)
- ATT&CK Technique : Proxy: Multi-hop Proxy (T1090.003)
- Exfiltration
7-What should we do for not to be affected by this event?
According to the analysis published by Cisco, only the files of the relevant employee and the account information of Cisco employees (information registered in the domain) seem to have been leaked. Although Cisco has updated all account information, cybersecurity experts recommend that you switch off these connections for a short time (one week). It advises not to open the relevant accounts without receiving a mail from Cisco that the passwords have been changed.
8-What can we do to avoid a similar security breach?
- Ban requests from anonymization systems such as TOR at the Gateway level.
- Test alerts to SOC teams by writing strict SIEM rules for suspicious activity for systems using MFA.
- Actively use Dark Web monitoring and Threat Intelligence systems against stolen accounts.
- Monitor your systems for suspicious activities 24/7.
- Conduct cyber drills to be prepared for potential attacks.
9-How can a reliable cybersecurity company like Cisco be hacked? Should we stop receiving services from Cisco?
With the expanding attack surface, every firm with a size above a certain scale will likely encounter similar results. Because attackers have accumulated more data than ever before to attack organizations. This attack is slightly different from the attacks we’ve seen before.
Using the browser sync feature, the personal account was directly accessed, and corporate information was obtained from it. Although MFA is active in the corporate account of the Cisco employee, it is understood that not used in the personal account.
Using MFA is strongly suggested by security experts. This incident shows that cybersecurity is a process, not a goal. It should be kept in mind that cyber attackers develop a solution for every measure taken.
10-What are the IOCs used in the attack?
Domains
- cisco-help[.]cf
- cisco-helpdesk[.]cf
- ciscovpn1[.]com
- ciscovpn2[.]com
- ciscovpn3[.]com
- devcisco[.]com
- devciscoprograms[.]com
- helpzonecisco[.]com
- kazaboldu[.]net
- mycisco[.]cf
- mycisco[.]gq
- mycisco-helpdesk[.]ml
- primecisco[.]com
- pwresetcisco[.]com
SHA256:
- 184a2570d71eedc3c77b63fd9d2a066cd025d20ceef0f75d428c6f7e5c6965f3
- 2fc5bf9edcfa19d48e235315e8f571638c99a1220be867e24f3965328fe94a03
- 542c9da985633d027317e9a226ee70b4f0742dcbc59dfd2d4e59977bb870058d
- 61176a5756c7b953bc31e5a53580d640629980a344aa5ff147a20fb7d770b610
- 753952aed395ea845c52e3037f19738cfc9a415070515de277e1a1baeff20647
- 8df89eef51cdf43b2a992ade6ad998b267ebb5e61305aeb765e4232e66eaf79a
- 8e5733484982d0833abbd9c73a05a667ec2d9d005bbf517b1c8cd4b1daf57190
- 99be6e7e31f0a1d7eebd1e45ac3b9398384c1f0fa594565137abb14dc28c8a7f
- bb62138d173de997b36e9b07c20b2ca13ea15e9e6cd75ea0e8162e0d3ded83b7
- eb3452c64970f805f1448b78cd3c05d851d758421896edd5dfbe68e08e783d18
IPs:
- 104.131.30[.]201
- 108.191.224[.]47
- 131.150.216[.]118
- 134.209.88[.]140
- 138.68.227[.]71
- 139.177.192[.]145
- 139.60.160[.]20
- 139.60.161[.]99
- 143.198.110[.]248
- 143.198.131[.]210
- 159.65.246[.]188
- 161.35.137[.]163
- 162.33.177[.]27
- 162.33.178[.]244
- 162.33.179[.]17
- 165.227.219[.]211
- 165.227.23[.]218
- 165.232.154[.]73
- 166.205.190[.]23
- 167.99.160[.]91
- 172.56.42[.]39
- 172.58.220[.]52
- 172.58.239[.]34
- 174.205.239[.]164
- 176.59.109[.]115
- 178.128.171[.]206
- 185.220.100[.]244
- 185.220.101[.]10
- 185.220.101[.]13
- 185.220.101[.]15
- 185.220.101[.]16
- 185.220.101[.]2
- 185.220.101[.]20
- 185.220.101[.]34
- 185.220.101[.]45
- 185.220.101[.]6
- 185.220.101[.]65
- 185.220.101[.]73
- 185.220.101[.]79
- 185.220.102[.]242
- 185.220.102[.]250
- 192.241.133[.]130
- 194.165.16[.]98
- 195.149.87[.]136
- 24.6.144[.]43
- 45.145.67[.]170
- 45.227.255[.]215
- 45.32.141[.]138
- 45.32.228[.]189
- 45.32.228[.]190
- 45.55.36[.]143
- 45.61.136[.]207
- 45.61.136[.]5
- 45.61.136[.]83
- 46.161.27[.]117
- 5.165.200[.]7
- 52.154.0[.]241
- 64.227.0[.]177
- 64.4.238[.]56
- 65.188.102[.]43
- 66.42.97[.]210
- 67.171.114[.]251
- 68.183.200[.]63
- 68.46.232[.]60
- 73.153.192[.]98
- 74.119.194[.]203
- 74.119.194[.]4
- 76.22.236[.]142
- 82.116.32[.]77
- 87.251.67[.]41
- 94.142.241[.]194
Visit Talos Intelligence for the other IoCs.
You can visit the websites below to find detailed information and Cisco’s technical explanations:
https://blog.talosintelligence.com/2022/08/recent-cyber-attack.html
https://tools.cisco.com/security/center/resources/corp_network_security_incident



































