10 Best SIEM Tools, Products & Providers List
SIEM solutions are vital to log management and complete security. Here is a list of the finest SIEM tools for organizations wanting to add or improve their systems.
SIEM, or security information and event management, gives a company’s IT environment visibility through log management and security information management. Almost every organization may benefit from the full security capabilities that only the finest SIEM software can provide.
Consider compliance reporting, threat detection, historical log analysis, a user-friendly interface, and powerful analytic capabilities when selecting a SIEM product.
What Is Security Information and Event Management (SIEM)?
A SIEM system is the most efficient approach for a business to build a successful cybersecurity procedure. More than a decade old, Security Information and Event Management (SIEM) products are the most effective approach for enterprises to secure sensitive data.
Small- and medium-sized companies (SMBs) may still enjoy the advantages of SIEM capabilities, often via a relationship with a managed service provider. Large corporations are the major users of SIEM solutions since they are more likely to need IT control (MSP).
A SIEM product might describe distinct capabilities like log management, security log and event management, security event correlation, and security information management. Not every SIEM solution contains every function. In addition, organizations are increasingly using SIEM systems because they may assist them in aligning their security approach with specific regulatory frameworks.
In many instances, most of these functions are bundled into a single product for commercial usage. However, there is no assurance that each component is similarly optimized.
SIEM tools operate by gathering and consolidating log data. A SIEM system analyzes security warnings from all network applications and hardware types, including antivirus products, servers, and firewalls. These more specific solutions are insufficient to defend a corporation; only a SIEM tool can provide a “big picture” view of your cybersecurity threat environment.
SIEMs can identify and fight against active threats and analyze logs for insights into abnormalities and assaults after the fact, providing the “why” behind an occurrence.
SIEM systems are proving to be more vital than ever. It has become indisputably advantageous to consolidate data and risks from your whole IT infrastructure into a user-friendly dashboard. In addition, many of today’s intelligent instruments are programmed to identify suspicious patterns on their own and occasionally even to address the underlying problem automatically.
The finest SIEM technologies are excellent at leveraging historical patterns to distinguish between serious threats and legitimate usage, allowing you to prevent false alerts while providing maximum security. There is no need to use a subpar tool when so many great alternatives are readily accessible.
What to Look for in the Best SIEM Solutions
SIEM products share a few fundamental qualities. They analyze data from many sources (including threat intelligence), provide warnings, do analytics, and offer a historical overview or summary. When selecting a SIEM security solution, each firm will use its own criteria to determine if a tool’s capabilities correspond with its requirements.
This will rely on company size, data kinds, vendor selection, particular regulatory frameworks, budget, and, of course, the usability preferences of the IT staff. As you investigate the top SIEM products on the market, there are certain things you should ask.
- Will the tool increase your ability to gather logs? This is essential since you need software that improves log collection and management. Consider system and device compatibility, and having a dashboard with user-friendly features never hurts.
- Will the tool help you get compliance? Consider using a platform that facilitates auditing and reporting. You should be concerned about compliance even if you are not now. A SIEM tool is an excellent method to improve your performance in this area.
- Is the threat response process configured to assist with managing prior security events? A primary benefit of a SIEM tool is that it enables you to review previous events, assess what occurred, and teach the system to utilize historical patterns to influence its future action. Look for useful, granular analytic functions.
The following list gives a detailed review of the top SIEM tools available on the market if you are pondering these sorts of queries.
1- Micro FocusArcSight ESM
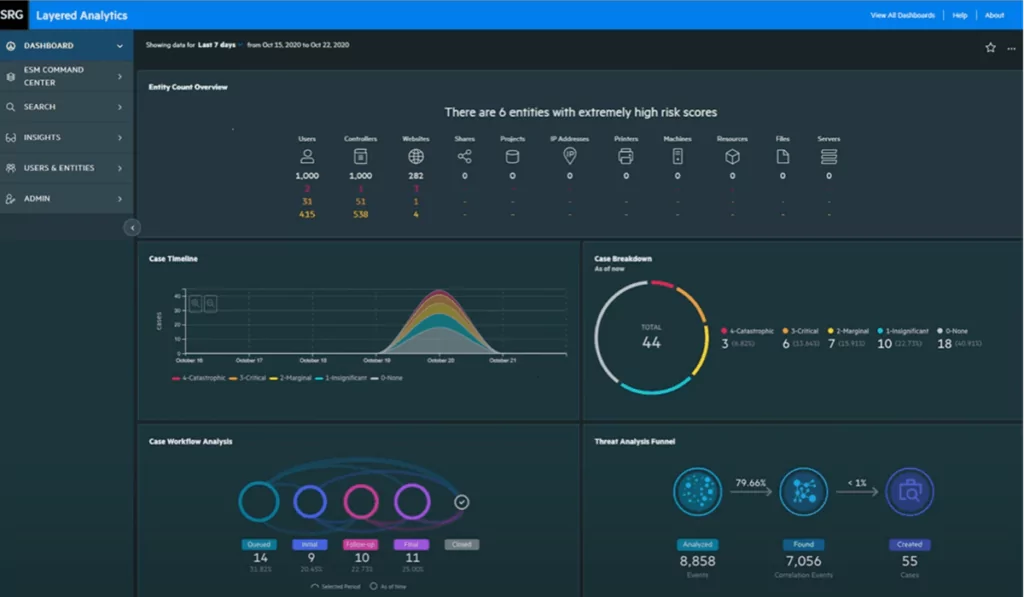
ArcSight’s open design affords it many distinguishing features. This tool can ingest data from a wider variety of sources than many SIEM systems, and its structured data may be utilized outside of ArcSight, which may be advantageous for IT teams with advanced skills. In addition, Micro Focus recently purchased security analytics software startup Interset to expand its behavioral analytics and machine learning offerings.
It is not a good idea that depends on these features appearing in ArcSight just soon, but it may be worthwhile to keep a watch on this market segment.
2- Splunk Enterprise Security
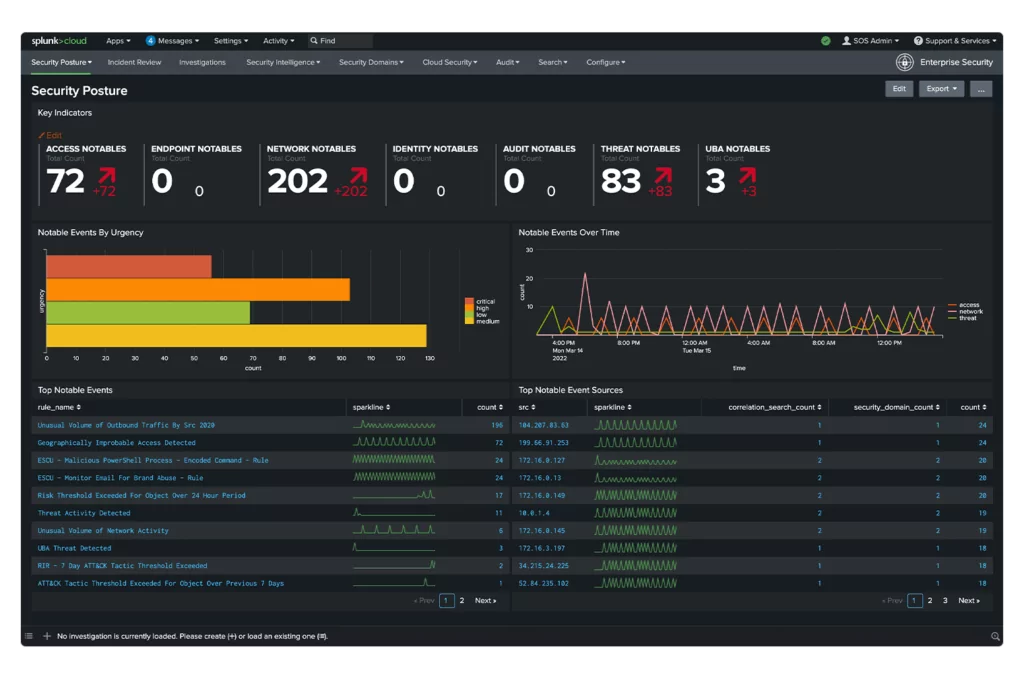
Splunk Enterprise Security is a well-known solution that has existed for over a decade. As the name suggests, this is an enterprise-level alternative, which means the license charges are not especially competitive; this tool may be too expensive for some. This utility is available as on-premises software or a SaaS offering (ideal for AWS users).
The dashboard contains valuable visualizations such as graphs and charts. It supports a sufficient number of plugins and third-party integrations. However, the learning curve might be severe if you want to use advanced analytics functions.
3- Forti SIEM
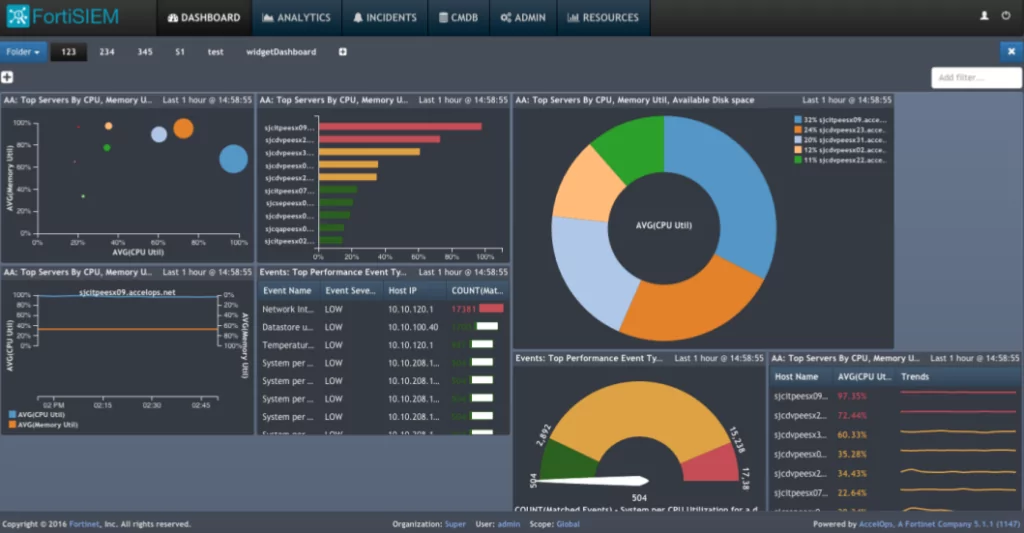
Fortinet provides its FortiSIEM platform. FortiSIEM offers SIEM, FIM, CMDB, and availability and performance features. The provision of analytics-driven IT operations and cloud management assists businesses in managing and monitoring network performance, security, and compliance needs. FortiSIEM profiles network traffic based on network flows and firewall records to identify network services.
It also provides Managed SIEM-as-a-Service; end-users and Managed Service Providers have access to it (MSPs).
4- IBM
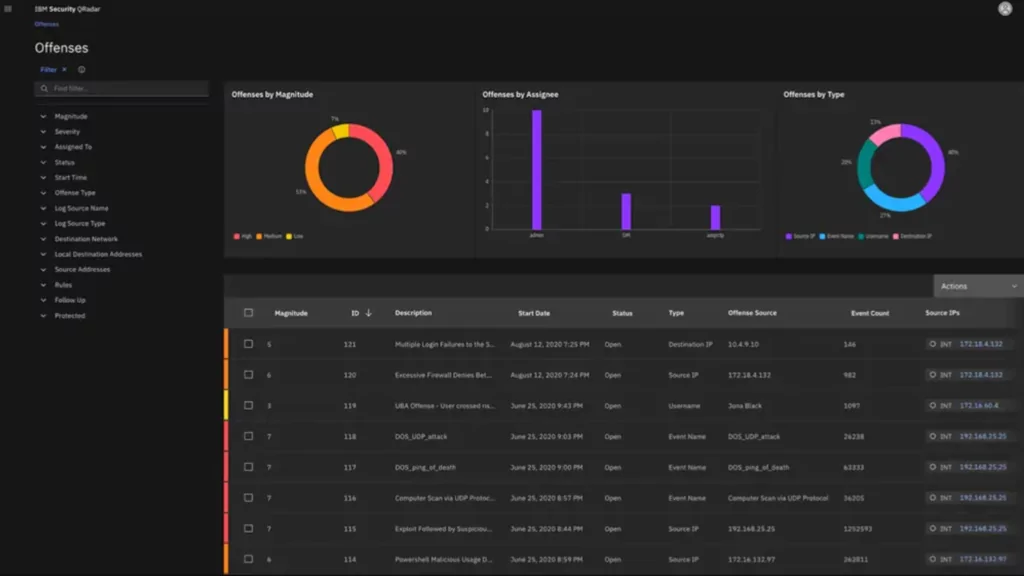
The QRadar Platform from IBM Security provides log and risk management that may be implemented as an appliance, a virtual appliance, or a SaaS infrastructure-as-a-Service (IaaS); this makes them suitable for various IT settings. Optional remote monitoring from their managed security service operations centers is included in the package.
IBM solutions integrate security information and event management, log management, anomaly detection, incident forensics, and configuration and vulnerability management through a single architecture.
5- LogPoint
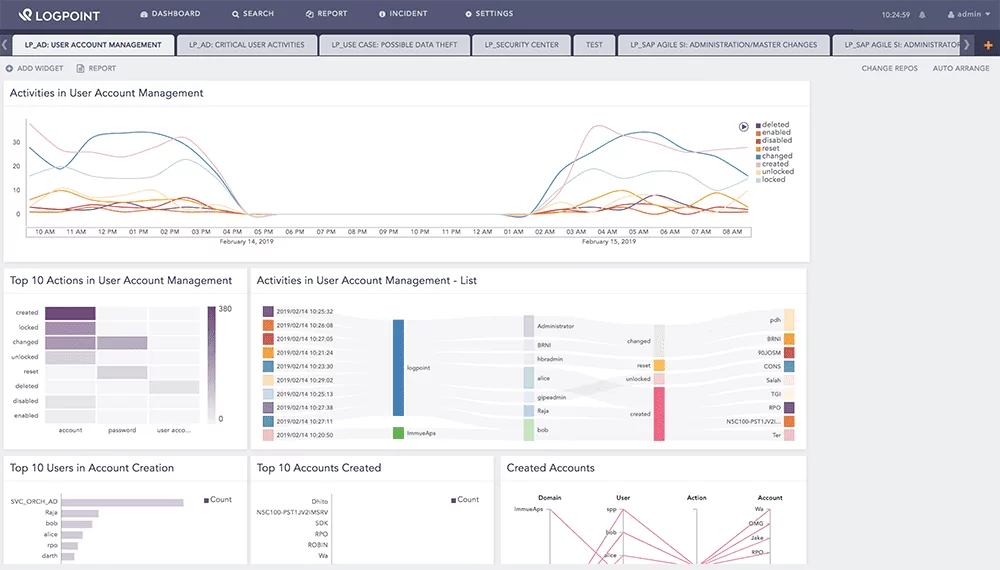
LogPoint’s comprehensive business SIEM solution pulls security events and incidents from the logs of IT systems and infrastructures of any scale. Real-time data that has been filtered and linked are shown on dashboards that may be customized depending on the roles and responsibilities of each user.
LogPoint also generates real-time, actionable insights from raw machine data to improve operational efficiency and expedite compliance with regulatory demands, enhancing companies’ security posture. LogPoint provides IT teams with visibility into all infrastructure-wide problems.
6- McAfee
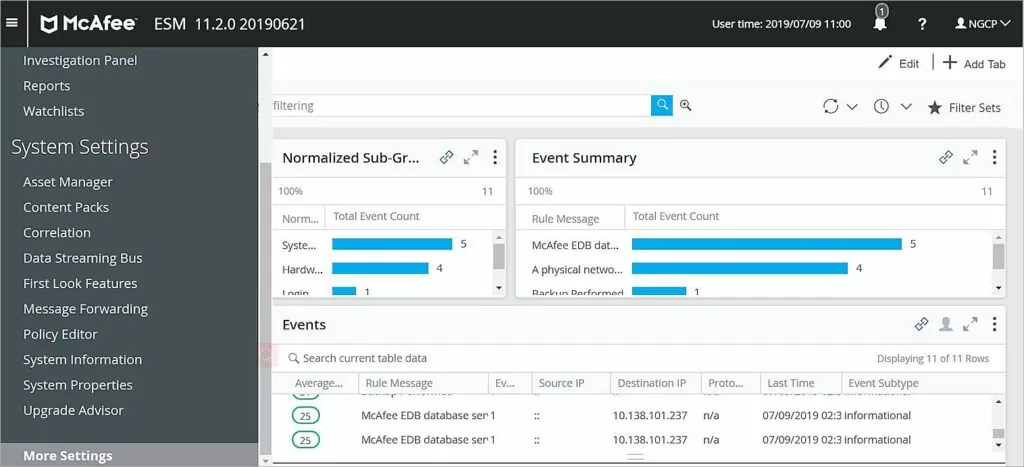
McAfee is an essential participant in SIEM and threat intelligence research. Their Enterprise Security Manager (ESM) consolidates, correlates, evaluates, and prioritizes security events for Intel Security and third-party solutions.
McAfee also offers integrated configuration and change management solutions, case management, and centralized policy management to enhance workflow and productivity. McAfee’s Advanced Correlation Engine is intended for risk- and behavior-based correlation and specialized correlation. Additionally, it has parsed events, databases, and reporting capabilities.
7- Sumo Logic
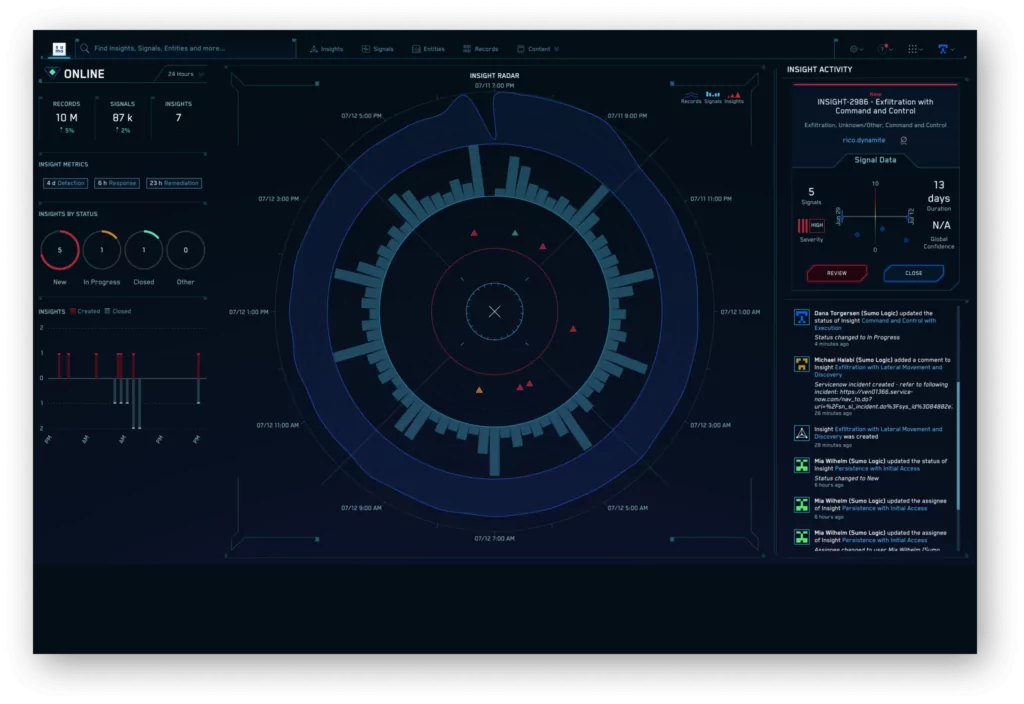
This cloud-based platform is suitable for SMBs in terms of cost and functionality. Since the product is new, there isn’t much of a community in place. However, Sumo Logic asserts that its solution solves holes in IT security that other companies have left unfilled, particularly in cloud installations.
This tool seems to be designed with a more technical user in mind. Hence the design aspects are less inviting.
8- Rapid7

Rapid7 provides its InsightIDR platform, a cloud-based SIEM solution for contemporary threat detection and response. Rapid7’s InsightIDR aims to consolidate your security data via cloud-based log and event management. Rapid7 intends to aid business compliance, identify the underlying behavior breaches, and track lateral movement.
Rapid7 specifically watches for lateral movement using stolen credentials by manipulating traffic and extracting hashes, and it helps the search and visualizes your security data.
9- Tenable
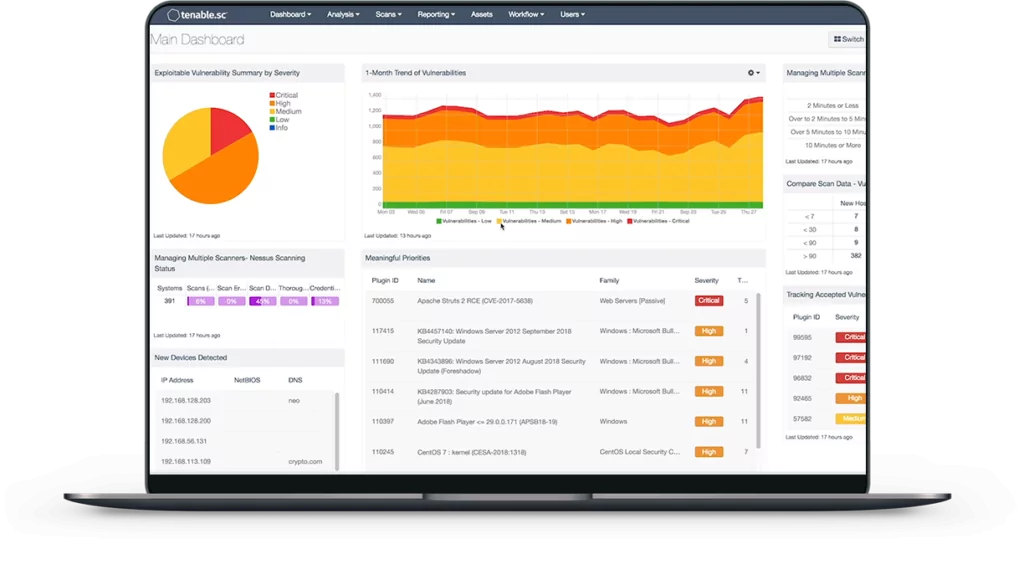
Tenable provides SIEM, which utilizes the log management capabilities of their Log Correlation Engine (LCE) to gather all logs, software activity, user events, and network traffic across the whole IT environment. Tenable analyzes data for correlations between events and their effects on the security and compliance posture.
Tenable Nessus vulnerability and configuration scans and real-time monitoring with the Tenable Passive Vulnerability Scanner give event context and threat-list knowledge about any system (PVS).
10- Trustwave
Trustwave’s Managed SIEM services provide threat intelligence, efficiency, and automation to businesses of all sizes. Its service is appropriate for consumer-facing organizations, including the Payment Card Industry Data Security Quality (PCI DSS) — a stringent compliance capability and a high standard.
Trustwave collaborates with POS suppliers to create logging functionality for in-store payment systems. Its equipment provides enhanced correlation, reporting, and ad hoc analytic capabilities locally on the device and via its Security Operations Centers.