
What Do You Need To Know About Cloud Web Application Firewall (WAF)
A cloud Web Application Firewall (WAF) is a security application running on the cloud that tracks the traffic between the user and the web servers to filter and block malicious packages traveling back and forth between the user and the web.
Operating in the seventh layer of the OSI model, the application layer, cloud WAFs are the preferred choice for protecting internet-facing services, including web applications and APIs, from cyber threats coming directly from web traffic.
Cloud web application firewalls offer protection against known zero-day vulnerabilities, DDoS (distributed denial-of-service) attacks, Cross-site scripting (XSS) attacks, and other vulnerabilities and threats coming through the web.

Why Are Cloud WAFs Important?
WAFs are primarily used by e-commerce and finance companies with online banking services. This security solution protects enterprises against web-based cyber attacks such as DDoS attacks or credential stuffing attacks.
Without a WAF, enterprises are vulnerable to these types of attacks; and as a result, they may face serious consequences damaging their organization.
How Do Cloud WAFs Work?
The attack surface of enterprises grows each day using new APIs and applications. The cloud WAF adds an extra layer of security to the enterprise’s expanding attack surface to protect users against upcoming cyber threats.
The cloud web application firewall monitors and analyzes the HTTP requests between the user and the webserver and decides whether the request is malicious or not by applying predefined rules. The analyzed HTTP requests are mainly GET and POST requests.
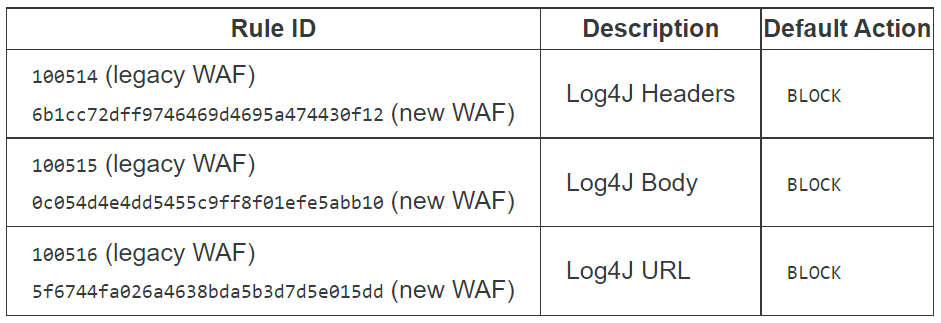
Cloud WAF Security Solution Against Recent Critical Log4J Vulnerability
In particular, popular cloud WAF vendors such as Cloudflare or Akamai have stated that they updated their security solutions to protect their users from the recently discovered zero-day exploit CVE-2021-44228, popularly known as Apache Log4j RCE vulnerability. This situation shows that WAFs continuously evolve and are updated against new cyber threats.
What are Different Types of WAFs?
As opposed to cloud WAFs, there are two other types of web application firewalls, known as host-based WAFs and network-based WAFs; however, they are not as efficient as the cloud web application firewall.
First, host-based WAFs are wholly integrated with the source code, making them difficult to manage and update. In addition, host-based WAFs need to use the resources of the center server to operate, so they require additional memory allocation within the server.
Secondly, network-based WAFs are generally hardware-based solutions, and they are placed within the company while also being connected to the company’s network. The downside of network-based WAFs is that they are not cost-efficient, requiring maintenance periodically.
Cloud WAF solutions are efficient and optimized because they operate in the cloud. They do not need additional memory allocation or periodic maintenance. In addition, the distribution and development of cloud WAFs are straightforward compared to other solutions.
Evolution of Web Application Firewalls
The scope of WAF capabilities is expanding to protect against API attacks, and currently, the market definition is evolving from WAF to WAAP (Web Application and API Protection).
According to Gartner, by 2026, 40% of organizations will select their WAAP provider based on advanced API protections, as well as web application security features — up from less than 10% in 2021. It is also faster to deploy and more manageable for organizations to maintain.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Try for free

































