
How to Detect Domain Hijacking Attacks?
What is a Domain Hijacking Attack?
Domain Hijacking (Domain Name Theft), the control of a domain name, a domain name to be changed without the permission of the original owner of the registration or domain name hosting, and a domain name is an abuse of privilege in the records system. Typically, a domain hijacking attack occurs by unauthorized access to a registrar, exploiting a vulnerability in the registrar through social engineering, or gaining access to the registrar’s email address and then resetting the registrar’s password.
As a result of domain hijacking attacks, companies face the following issues:
- Financial losses: Companies that rely on websites for business, such as e-commerce companies, can lose millions of dollars when they lose control of their domains, domains being one of their most valuable assets. Domain hijacking is one of the most significant cybersecurity risks online businesses can face.
- Reputation: Hackers can gain control of a domain’s email accounts and use the domain name to facilitate additional cyberattacks, such as malware installation or social engineering attacks.
- Personal data breach: By gaining access to a domain, hackers can replace the actual web page with an identical web page designed to capture sensitive data or PII (phishing). These attacks aim to capture account information, contact information (email addresses and phone numbers), social media accounts, IP addresses, or other personal information that can be used to gain unauthorized access to identity theft and customer accounts.
Recent Domain Hijacking Attacks
Perl.Com Domain Hijacking Attack
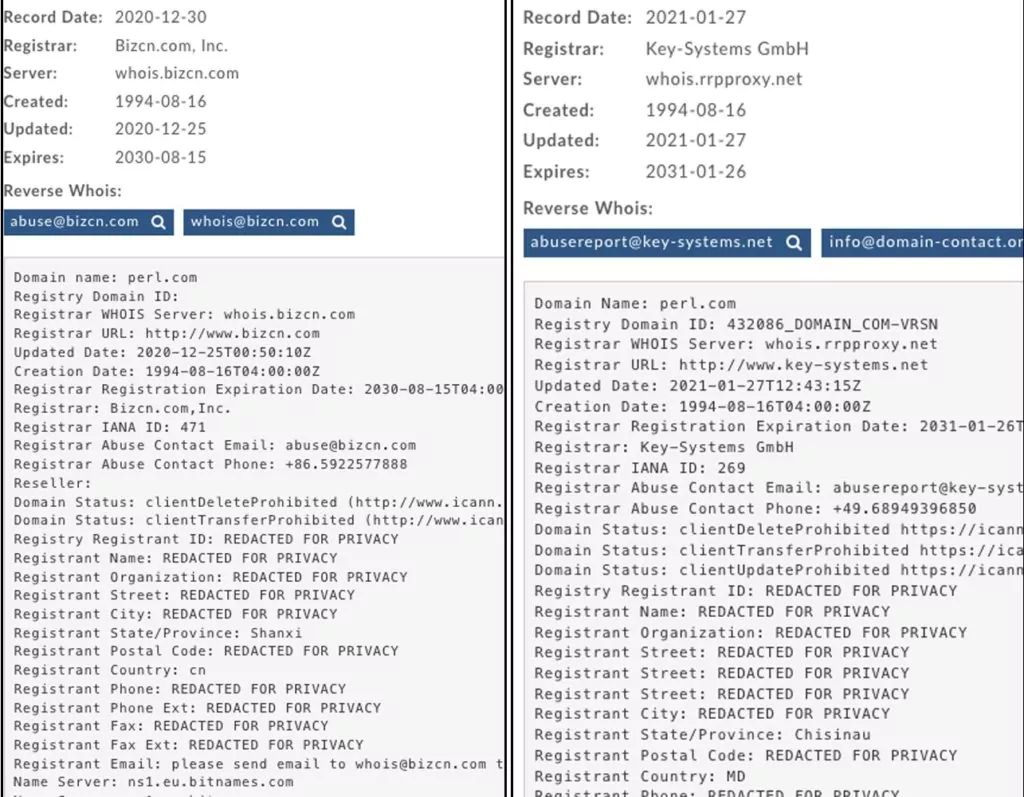
perl.com has been used since 1997 to post news and articles about the Perl programming language, which was highly attacked by Domain Hijacking on January 27, 2021. By the time the domain was stolen in September 2020, it was registered with Network Solutions. Subsequently, the domain name expiry date was extended for several years and was transferred to a registrar in China on December 25, 2020. Finally, the domain was transferred to the Key-Systems Registrar on January 27, 2021. Then the DNS address was changed.
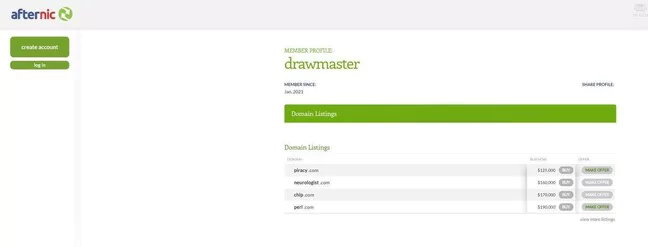
Shortly after threat actors stole the domain name, it was put up for sale on Afternic.com, a platform for selling domain names, for $190,000, but was soon removed.
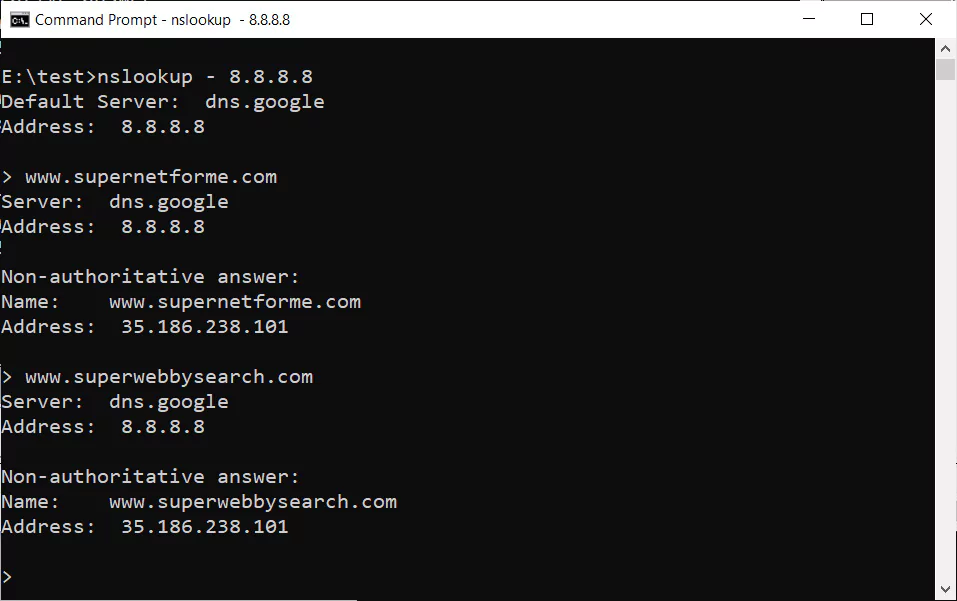
While the site could not serve over HTTPS, those who tried to access the site over HTTP encountered various malware scripts, tracking cookies, and a blank page. The 35[.]186[.]238[.]101 IP addresses to which the Perl.com domain was moved (Google Cloud IP address) were used for the distribution of malware, including Locky ransomware (2019) and finally as a command-and-control server (C2) (Virus Total). In addition, it has been determined that the threat actor waits 60 days to switch the domain name registration to a different company due to ICANN’s 60-day rule (the domain registrar can change 60 days after the registrar changes). After a week of work, the domain was taken back by its original owner and started to be used.
DNS Poisoning Attack Targeting Lenovo and Google’s Websites
China-based computer and smartphone manufacturer Lenovo’s home page and Google’s Vietnam site redirected users to a different website for a short time. Both companies were exposed to domain hijacking attacks against DNS.
In the Lenovo attack, the registration of domain names was transferred to Cloudflare by the threat actors and directed to two IP addresses of the Netherlands-based company called Digital Ocean. Users trying to access the real website were redirected to another website (the interface of the official published site above). When security researchers examined the source codes of the website, the names of Ryan King and Rory Andrew Godfrey, who were previously reported to be associated with the hacker group Lizard Squad, were found.
Users trying to access threat actors briefly redirected Google Vietnam’s site to another website. Like Lenovo, Google had the domain google.com.vn registered with Webnic.
How to Prevent Domain Hijacking?
To prevent a successful Domain Hijacking attack, ICANN imposes a 60-day waiting period between a change in the registration information and a registrar transfer. Retrieval of transferred domains is difficult to detect, and it is believed that the original domain owner will discover the changes and notify the registrar within 60 days.
It is recommended that companies take service from SOCRadar ASM or similar external attack surface management tools for themselves and their 3rd party companies (suppliers) to detect domain hijacking attacks. By providing early notification of Domain Hijacking attacks, it is possible to minimize or even eliminate data breaches that may occur. In addition, the following steps help prevent domain hijacking attacks:
- Work with a highly reputable domain name provider: Use an accredited registrar and avoid working with non-accredited (second-hand) registrars. Reputable domain registrars provide secure DNS management and 24/7 technical support.
- Activate the registrar-lock or Client Transfer Prohibited feature for domain names registered with the domain registrar: Domain name locking allows you to prevent unauthorized domain name transfers to another registrar.
- Ensure that the email and password information you used while registering with the domain registry firm is not used on other sites and activate the account lock feature: Data breaches may reveal common passwords between services. Do not use your username passwords on other sites to prevent credential stuffing attacks. Also, to avoid brute-force attacks, use a registrar that limits the number of invalid password attempts, locks the account, and notifies you by email when unusual activity is detected.
- Use the domain registrar’s 2-factor authentication mechanism and IP access feature: This should be enabled on all accounts that allow two-factor authentication. If someone can gain access to one of your accounts, the second layer of authentication can help protect you from unauthorized access.
- Activate the WHOIS privacy service, where you can prevent the receipt of detailed domain information: WHOIS protection reduces the amount of sensitive data you expose on the Internet, including address (street address, city, state, and country), phone number, and email address. WHOIS information can assist cyber criminals in social engineering attacks.
- Do not use the same company for domain provider and web hosting: To prevent an attacker from gaining access to your domain name and sensitive files that may be on your hosting provider, do not combine all risks in one basket.
- Remove DNS records of unused domains by inventing your digital assets: Remember that many attacks come from forgotten assets that remain in the blind spot.
- Use external attack surface management tools that actively monitor your DNS records, WHOIS information, and website changes and report the changing status: When you encounter a possible domain hijacking attack, the fastest way to get rid of this situation can be detected. Strengthen the detection mechanism.
- Use a product that actively tracks domain name expiration. Suppose you are going to stay with the same provider. In that case, enable automatic registration renewal for all your domains: Another method used in domain hijacking attacks is to take the expired domain registration by someone else.
- In the framework of increasing cyberattacks from third parties, monitor the companies you do business with and put your domain providers first on your checklist.
How Can You Use SOCRadar for Early Detection?
SOCRadar Extended Threat Intelligence service protects from domain hijacking attacks with the following methods.
SOCRadar Attack Surface Management prevents and quickly detects domain hijacking attacks by discovering and tracking your assets on the Internet, discovering the digital footprint where unused DNS records can be detected.
- Keeping track of domain NS (Name Server) registration changes,
- Keeping track of the domain’s A record change,
- Keeping track of the MX record change of the domain,
- Following the change of whois information,
- Following the change of the title and content information on the website
SOCRadar’s Brand Protection provides the detection of intelligence information about your assets and your company:
- By automatically tracking company domains in Dark and Deep web environments, it informs your company of every incident
- The HUMINT ability of SOCRadar dark web analysts provide your company to communicate with the threat actor for confirmation of the accuracy of up-to-date information and remove postings for increasing the company’s reputation when necessary
SOCRadar’s Cyber Threat Intelligence provides to detect intelligence on current cyber events:
- Through the determinations made based on country-specific and sector-specific domain hijacking attacks, the companies which can be affected by these attacks, are informed
- Actively informing security personnel about domain hijacking attacks




































