
Top 10 Best Free Cyber Threat Intelligence Sources and Tools in 2023
Keeping abreast of cybersecurity developments has become a challenge, given the constantly evolving landscape. This includes newly discovered vulnerabilities, new attack methodologies, and the tactics, techniques, and procedures (TTPs) used by emerging cyber attackers. Consequently, acquiring sources and tools to assist with these time-consuming tasks and obtain actionable information has become increasingly difficult.
For security professionals, possessing advanced knowledge is a crucial enabling factor. It may be necessary to experiment with free threat intelligence sources that provide verified and timely information before considering premium versions.
Numerous CTI (Cyber Threat Intelligence) tools can prove useful at different stages of the intelligence cycle. While these tools cannot be all-in-one solutions, in addition to facilitating automated data collection, storage, sharing, and analysis, together with the SR CTI solution can save a significant financial investment that many small or medium-sized companies cannot afford.
To address this issue, we have compiled a list of the top 10 best tools and sources that we find most helpful in incorporating CTI into your security operations. These options offer at least some of their functionalities for free.
1- AlienVault Open Threat Exchange
AlienVault Open Threat Exchange (OTX) offers open access to a global community of threat researchers and security experts. It provides community-generated threat data, fosters collaborative research, and automates the process of updating your security infrastructure with threat data from any source.
This platform serves as the original crowdsourced threat intelligence corpus and remains one of the best, processing over 19 million new Indicators of Compromise (IoC) records every day. The service is free to use and offers threat intelligence in various formats, including STIX, OpenIoC, MAEC, JSON, and CSV formats. Each feed sample is referred to as a “pulse”.
You have the flexibility to define your specific requirements by receiving certain pre-filtered data, and there is also the option to receive feeds tailored to device types, such as endpoints. If relevant data falls outside the parameters of your feed, this additional data is linked within the delivered records.
2- CTI4SOC
SOCRadar’s new standalone CTI solution, CTI4SOC, is a next-generation threat intelligence platform designed to facilitate the work of SOC analysts. It serves as a unique assistant to SOC teams with its 12 functional modules.
Unlike traditional threat intelligence platforms, CTI4SOC is powered by big data and presents all the data that analysts can obtain using various tools in an organized and contextual manner.
With CTI4SOC, SOC teams do not need to navigate through various information sources looking for true and useful information. The platform selects and filters information through the eyes of the analyst, providing you with the right hypothesis to begin your research.
The platform not only compiles useful information but also presents it in an actionable context. It offers one-click access to threat reports published by SOCRadar security analysts and other trusted sources.
In today’s ever-evolving threat landscape, some threat actors may only target specific sectors and have their own distinguishing characteristics. The SOC analyst’s understanding of these adversaries’ Tactics, Techniques, Procedures (TTPs), motivations, and behavioral patterns directly contributes to the investigation process by helping them form a well-informed point of view. With CTI4SOC, you can add active threat actors to watch lists to stay on top of their activities.
The SOCRadar Threat Hunting module is the SOC analyst’s most valuable tool after the investigation phase. From there, security personnel can extend their work by searching for critical information, such as command and control (C2) centers, malware, IP addresses, and domains. CTI4SOC is an API-ready solution that allows all this actionable data to be readily available in case of a possible attack.
3- DOCGuard
DOCGuard is a malware analysis service that integrates with Secure Email Gateways (SEGs) and SOAR solutions.
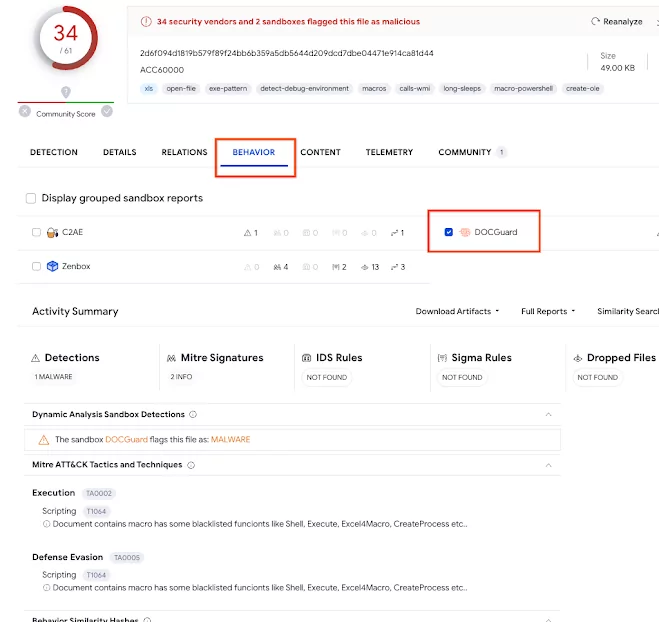
The service utilizes a new type of static analysis known as structural analysis. This method breaks malware into pieces and transfers them to core engines based on file structure components. By employing this approach, DOCGuard can unambiguously detect malware, extract F/P-free (false positive-free) Indicators of Compromise (IoCs), and identify obfuscation and encryption in the form of sequence encoding and document encryption.
Currently, the supported file types include Microsoft Office Files, PDFs, HTML, HTMs, LNKs, JScript, ISOs, IMGs, VHDs, VCFs, and archives (.zip, .rar, .7z, etc.). The detailed findings of the structural analysis are presented in an aggregated view in the GUI and can be downloaded as a JSON report. These findings can also be collected via the API.
DOCGuard’s groundbreaking analyzer engine allows it to analyze files in seconds and detect all known attack methods without missing any. Moreover, it performs this analysis with surprisingly low system resource usage. DOCGuard facilitates the automation of alert verification from various sources, such as SIEM and SOAR solutions, PhishMe, Cofense, etc. The service offers rapid sample analysis and seamlessly integrates with your cybersecurity ecosystem within minutes using its API interface. You can easily install DOCGuard by deploying the Docker container and integrating it into your cybersecurity infrastructure.
VirusTotal has recently announced that the document analysis cooperation integrated with DOCGuard will allow the community to take another view of scanned documents.
4- GreyNoise
GreyNoise provides visibility and deep context for Cyber Threat Intelligence (CTI) analysts and threat hunters. It collects and analyzes data on browsing activity across the Internet, helping to reduce false positives when analyzing threat intelligence information. GreyNoise gathers information on benign scanners like Shodan, as well as malicious actors like SSH and Telnet worms. Additionally, it identifies noise data that may be missed by a SOC analyst.
GreyNoise identifies internet browsers and general business activity in your security events, enabling faster and safer decision-making. Whether you use its Viewer, API, or integrate GreyNoise data into your security tools, you can find what matters in your security logs and get back to work.
GreyNoise integrations enable easy data enrichment in your Threat Intelligence Platform (TIP) and help eliminate the noise and false positives that CTI teams tend to encounter when ingesting different sources of intelligence. Threat hunters can enable GreyNoise to discover anomalous patterns in tactics, techniques, and procedures (TTPs), thereby uncovering enemy campaigns and infrastructure. They can also dive deep into Indicators of Compromise (IoCs) with the GreyNoise Analysis tool to accelerate their investigation timeline.
5- Intezer
Intezer is a platform designed to analyze and investigate alerts like an experienced security analyst and reverse engineer.
Over the years, Intezer has fine-tuned and extended the capabilities of its proprietary code analysis engine to automate increasingly time-consuming or repetitive tasks for SOC teams. It goes beyond automated playbooks, sandboxing, or alert enrichment to take action, make smart decisions, and provide recommendations to your team for incident response.
Intezer’s Self-Directed SOC platform prioritizes alerts and investigates threats for your team 24/7. By utilizing automated analysis, intelligent recommendations, and automated remediation, Intezer saves your team from wasting time on false positives, repetitive analysis tasks, and handling too many high-level and time-consuming alerts.
Intezer Analyze is an all-in-one malware analysis platform that can perform static, dynamic, and genetic code analysis on any type of file. It helps incident response and SOC teams streamline the investigation of any malware-related incident. Users can track malware families, extract IoCs/MITRE TTPs, and download YARA signatures. There is also a community version available to get started for free.
With Intezer Transformations, malware analysts and threat researchers can quickly get answers about any suspicious file or endpoint, classify suspicious files and machines in seconds, speed up response time, and combine multiple malware analysis tools into one.
Intezer enables timely, in-depth reporting and is considered a “must-have” to have a dedicated instance to upload potentially sensitive data and automatically prioritize and investigate every alert. The platform delivers only confirmed, serious threats. Easily connect your alerting systems, realizing immediate value without changing your daily operations.
6- MISP Threat Sharing
MISP, formerly called Malware Information Sharing Platform, is an open-source and free threat intelligence platform with open standards for sharing threat information. It was created by CIRCL and provides functions for collecting, storing, distributing, and sharing cybersecurity threats related to cybersecurity incidents and malware analysis.
MISP allows you to correlate Indicators of Compromise (IoCs) in the database with attributes and indicators from malware, attacks, or campaigns. It is designed by and for SOC analysts, security and ICT professionals, and malware reverse engineers to support their daily operations and efficiently share structured information.
As the MISP project expanded, it began covering not only malware indicators but also fraud and vulnerability information. The name is now MISP, which includes the core MISP software and a myriad of tools (PyMISP) and formats (core format, MISP taxonomies, warning lists) to support MISP. MISP is now a community project led by a team of volunteers.
The purpose of MISP is to promote the sharing of structured information within the security community and beyond. MISP provides functionalities to support the exchange of information as well as the consumption of information by Network Intrusion Detection Systems (NIDS), LIDS, and log analysis tools, SIEMs.
Key functionalities of MISP, Malware Information Sharing Platform, and Threat Sharing include:
- An efficient IoC and indicator database that allows storing technical and non-technical information about malware samples, incidents, attackers, and intelligence.
- Automated correlation to find relationships between attributes and indicators from malware, attack campaigns, or analyses.
- A flexible data model where complex objects can be expressed and linked together to express threat intelligence, events, or linked items.
- Built-in sharing functionality to facilitate data sharing using different distribution models.
- An intuitive user interface for end-users to create, update, and collaborate on events and attributes/indicators.
- A flexible API to integrate MISP with your own solutions. MISP comes with PyMISP, a flexible Python library to access MISP platforms via their REST API that allows you to fetch events, add or update events/attributes, add or update malware samples or search for attributes.
- Adjustable taxonomy to classify and tag events according to your classification schemes or existing taxonomy.
- Intelligence dictionaries called the MISP galaxy, which includes existing threat actors, malware, RAT, ransomware, or MITRE ATT&CK, can be easily associated with events and attributes in MISP.
7- OpenCTI – Open Cyber Threat Intelligence Platform
The OpenCTI project, a unified platform for all levels of Open Cyber Threat Intelligence, is a tool designed to facilitate the processing and sharing of information for cyber threat intelligence purposes. It is the product of collaboration between the Computer Emergency Response Team (CERT-EU) and the French National Cyber Security Agency (ANSSI).
OpenCTI is an open-source platform that enables organizations to manage their cyber threat intelligence information (CTI) and observables. It was created to store, organize, and visualize technical and non-technical information about cyber threats.
Data structuring is performed using an information schema based on STIX2 standards. It is designed as a modern web application that includes a GraphQL API and a user experience (UX)-oriented front-end. It can also be integrated with other tools and applications such as MISP, TheHive, MITRE ATT&CK, etc.
Some of the key elements included in this threat intelligence platform are as follows:
- OpenCTI delivers linked operational and strategic intelligence information through a uniform data model based on STIX2 standards.
- Automated workflows: The engine automatically draws logical conclusions to provide insights and real-time connections.
- Integration with the information technology ecosystem: Its open-source design enables simple integration with any native or third-party system.
- Intelligent data visualization allows analysts to visually represent entities and their connections, including nested relationships, using various display options.
- Analysis tools: Each piece of information and indicator is linked to the primary source it came from to facilitate analysis, scoring, and correction.
OpenCTI is a framework that includes Python or Go API interfaces and a powerful web interface.
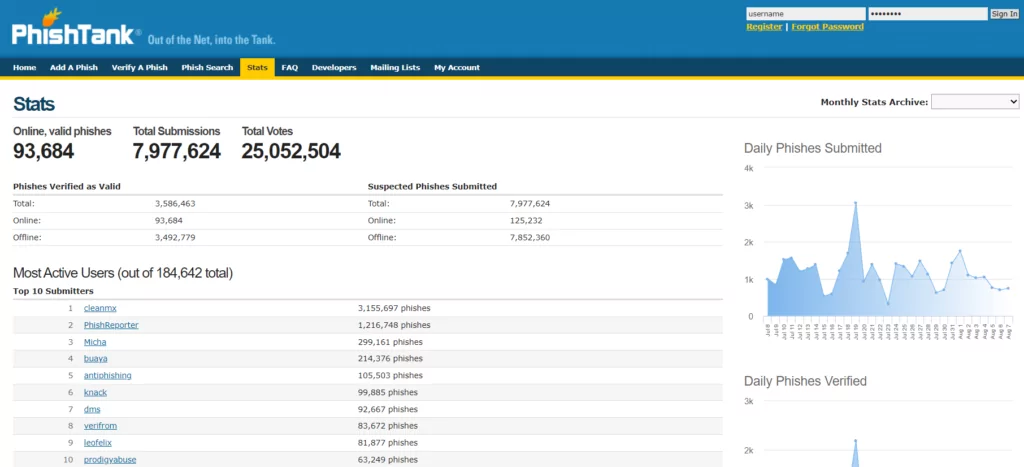
8- PhishTank
PhishTank is a free community site and collaborative platform where anyone can submit, verify, track, and share phishing data. It offers a comprehensive stream of verified phishing URLs that can be utilized to protect organizations against phishing attacks. PhishTank operates as a phishing verification system, enabling users to submit or rate suspicious sites and providing an open API.
The platform provides a list of suspicious phishing URLs sourced from human reports, and it also incorporates external feeds when available. While PhishTank is a free service, signing up for an API key may be necessary at times.
9- Pulsedive
Pulsedive is a free community threat intelligence platform that utilizes open-source feeds, enriches Indicators of Compromise (IoCs), and runs them through a risk-scoring algorithm to improve the quality of the data. It allows users to submit, search, scan, and enrich IPs, URLs, and domains. Furthermore, it enables users to correlate and update IoCs derived from threat intelligence feeds and lists risk factors explaining why certain IoCs are considered higher risk. The platform provides a high-level view of threats and threat activity.
Users can search for indicators based on any combination of the following criteria: Value, Type, Risk, Last seen timestamp, Threat Feed, Attribute, and Property. Additionally, they have the capability to search for threats based on any combination of the following criteria: Threat name, Alias, Category, Risk, Last seen timestamp, Feed, and Threat attribute.
10- VirusTotal
VirusTotal checks items with over 70 antivirus scanners and URL/domain blocking services, along with numerous tools to extract signals from the analyzed content. Any user can utilize their browser to select a file from their computer and send it to VirusTotal. The platform offers several file submission methods, including a primary public web interface, desktop installers, browser extensions, and a programmatic API. The web interface holds the highest screening priority among public submission methods. Submissions can be made in any programming language using the HTTP-based public API. Similarly, URLs can be submitted in various ways, including the VirusTotal web page, browser extensions, and the API.
When a file or URL is submitted, the underlying results are shared with the sender, as well as with review partners who use the results to improve their own security posture. Therefore, by submitting files, URLs, domains to VirusTotal, you contribute to raising the global security level.
This basic analysis also serves as the foundation for many other features, including a network that permits users to comment on files and URLs and share notes with each other. VirusTotal proves useful in detecting malicious content and identifying false positives. Furthermore, VirusTotal notifies users when an antivirus solution identifies a submitted file as malicious and displays the detection label. Additionally, most URL scanners will distinguish between types of websites, including malware, phishing, and suspicious.



































