
CEO Fraud: Investigating A Gift Card Scam
On March 8, 2023, SOCRadar announced that it received a $5 million Series A investment from 212, a leading equity fund investing in B2B technology start-ups. Then it has become the target of cyber fraudsters. As experienced in similar investment events, the attackers used this situation as an opportunity in the posts that were the subject of the news in the global sense. Since the name of Huzeyfe Onal (CEO) was included in the investment news, the attackers attempted to phish SOCRadar employees by impersonating Huzeyfe Onal. In the observed attacks, we detected that threat actors performed phishing attacks on three of the institution’s employees. We thought that employees’ email addresses had been compromised via LinkedIn.
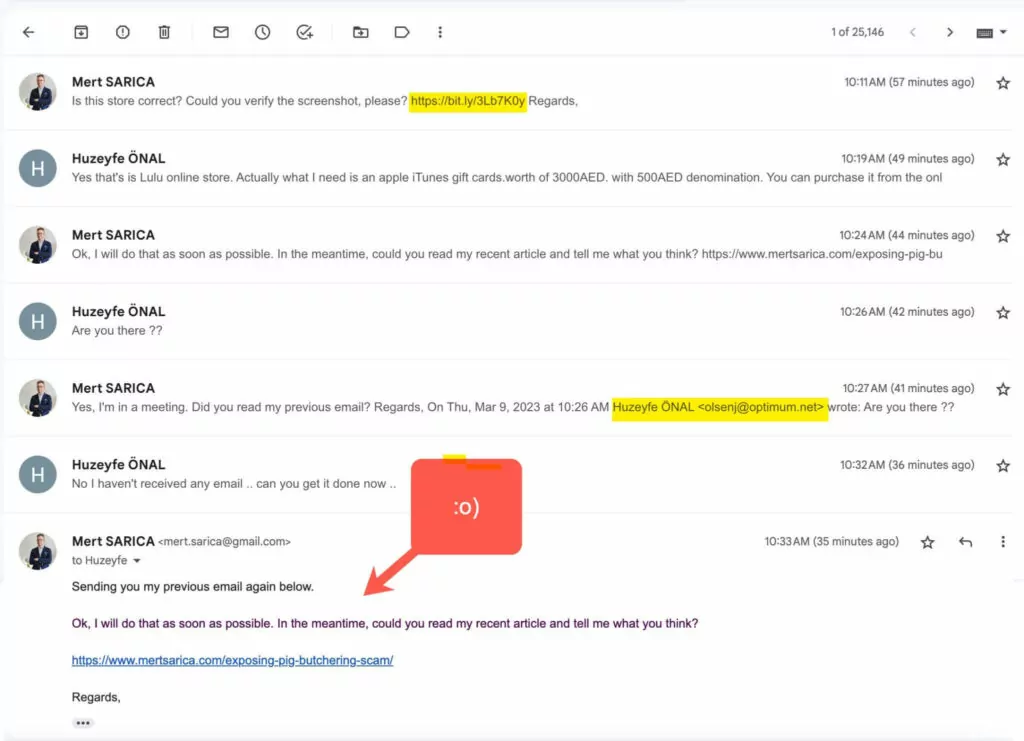
One of the targeted employees was Mert Sarıca (Head of Strategy). After realizing the situation, Mert Sarıca tried to contact the fraudster and reveal his identity. On March 8, 2023, after the investment news was published on Yahoo Finance, the attackers started to send phishing emails to the company’s employees on the same day. We detected that the phishing emails came from the address [email protected], impersonating the name of Huzeyfe Önal. A screenshot of the content of the relevant email sent by the fraudster is given in the images below.
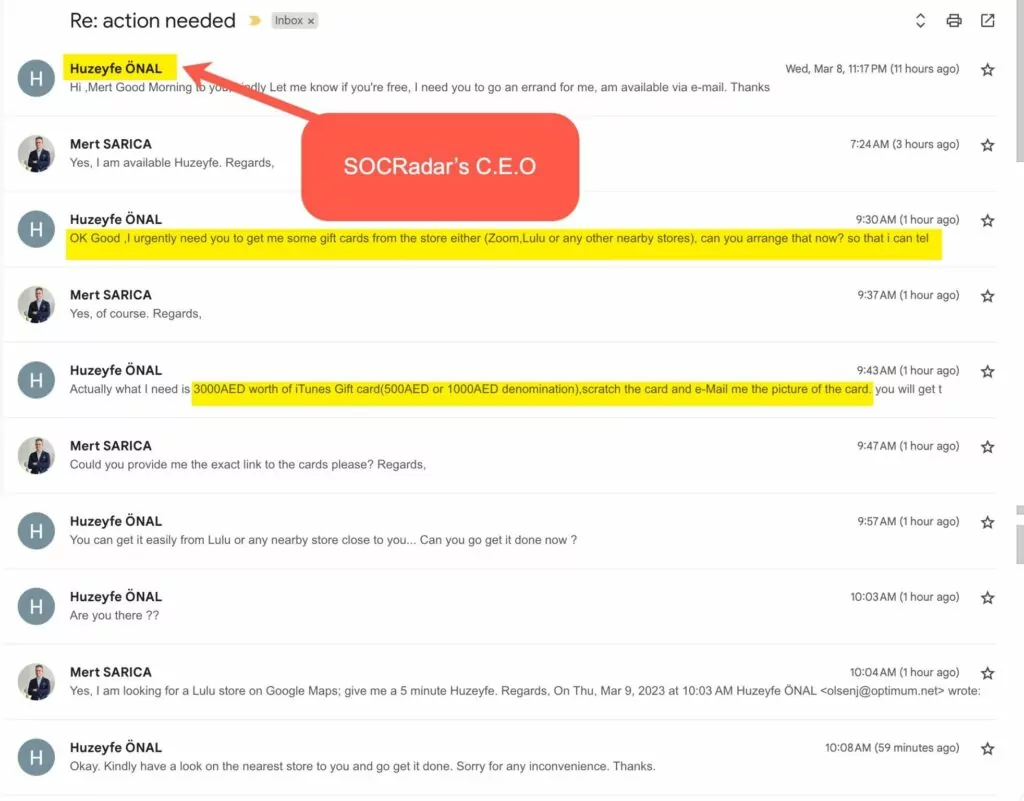
In the email, attacker states that they urgently request a gift voucher from the store on behalf of Huzeyfe Onal. The fraudster wants employees to think that after the investment in SOCRadar, gift cards will be distributed to the company personnel. As stated in the content of the email in the screenshot, they ask for a certain number of iTunes Gift cards to be provided and the area with the code on the card to be engraved and forwarded to them. After this action, the fraudster aims to collect the iTunes Gift cards and put them up for sale on underground forum sites.
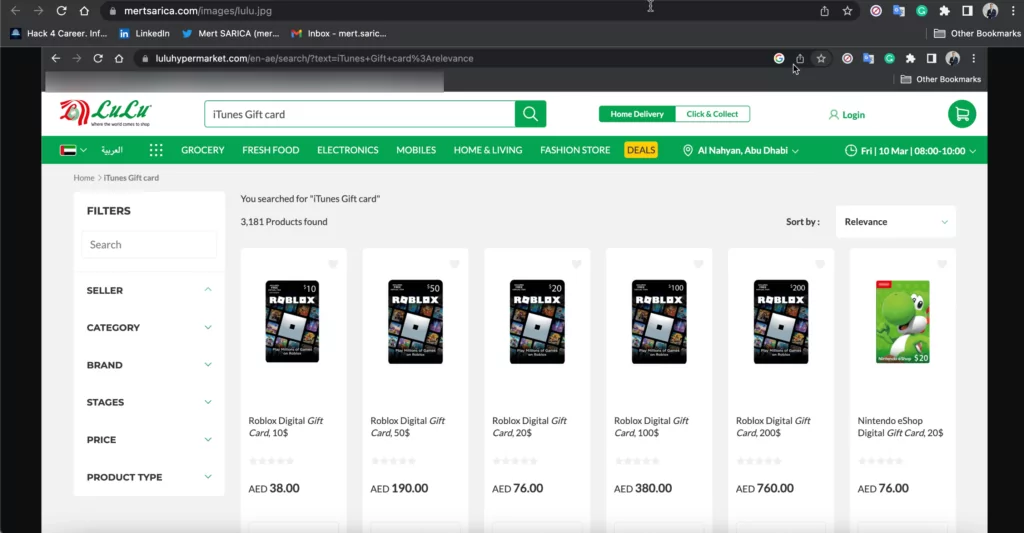
For the gift card requested by the fraudster in the email, a screenshot was taken by searching for “iTunes Gift Card” on Lulu HyperMarket. Bitly URL shortening service was used to obtain a shortened link for the screenshot and forwarded it to the fraudster. This process aims to detect the IP address of the fraudster by making the fraudster click on the shortened URL.
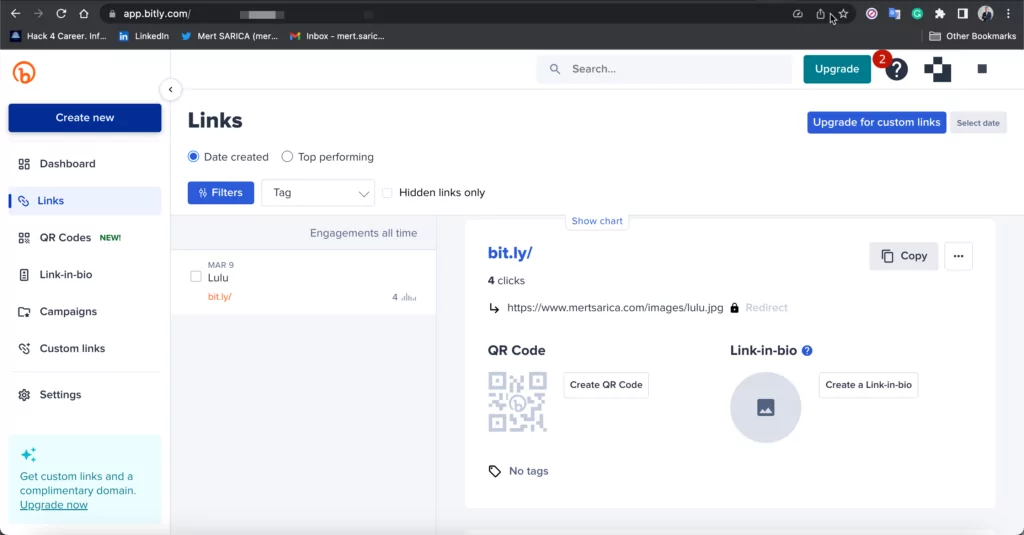
With this shortened URL we have created, the IP addresses visiting the link can be detected. By sending the relevant shortened URL via email, it was intended for the threat actor to visit the address.
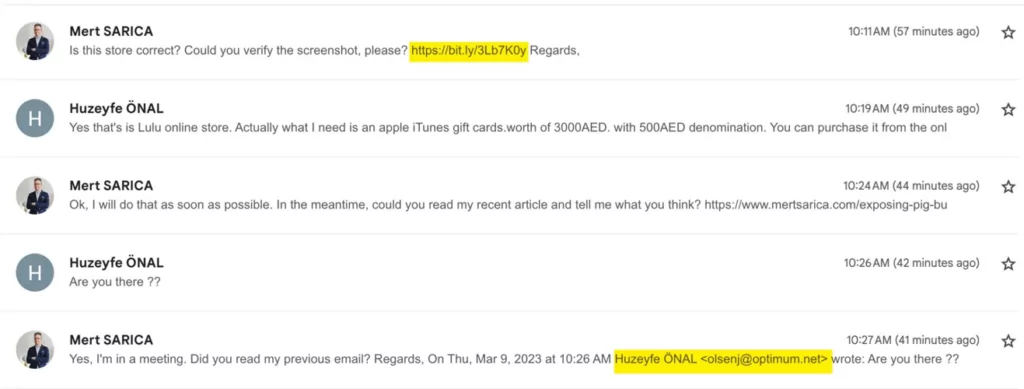
The scammer revealed his IP address by visiting the shortened URL in the first email in the screenshot above. Later in the conversation, Mert Sarıca, realizing the scammer’s intentions, sent him a blog post titled Pig Butchering about a scam attempt as a cautionary reply. After reading this post, the scammer ended the correspondence as expected.
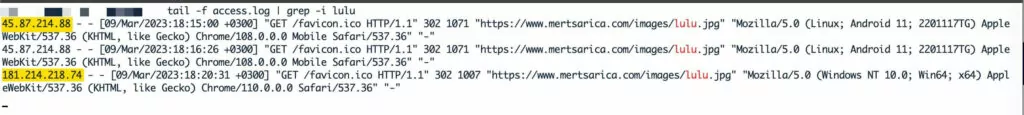
Two different IP addresses belonging to the fraudster who attempted to carry out the phishing attack via the shortened URL service have been identified.
- 45.87.214.88 (Android OS)
- 181.214.218.74 (Windows OS)
IOCRadar & SOCRadar Threat Hunting
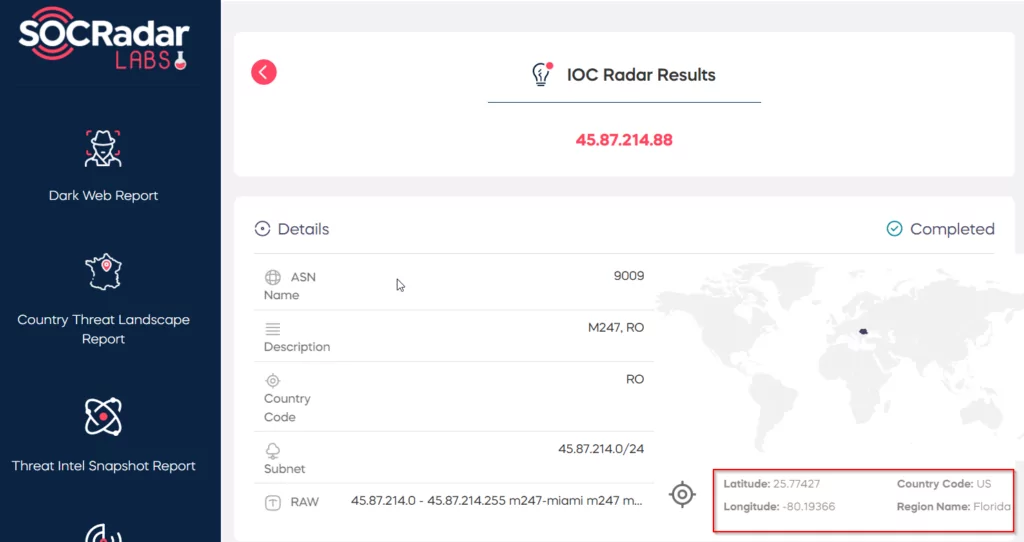
As a result of the research conducted on IOCRadar and SOCRadar, more detailed information was obtained on the IP addresses and email addresses of the fraudster.
- 45.87.214.88
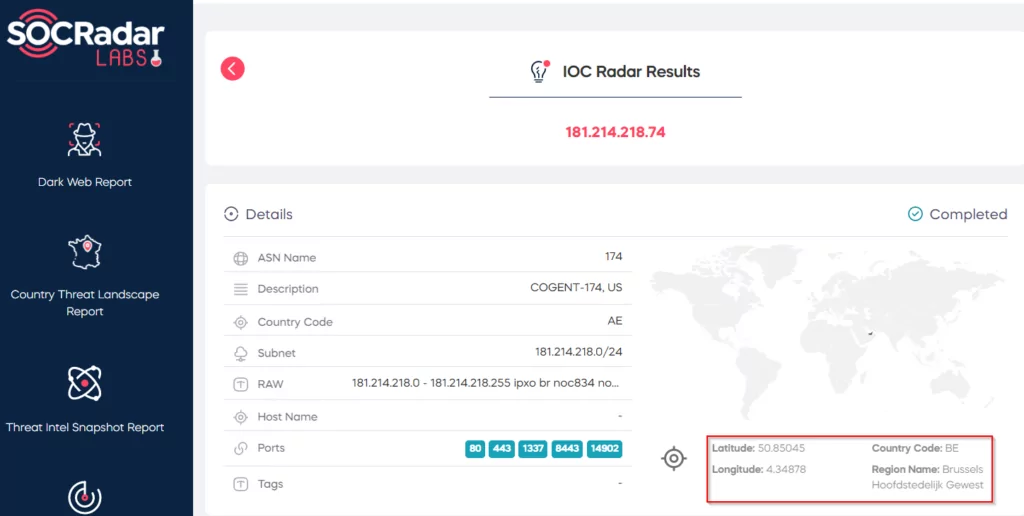
- 181.214.218.74
You can access detailed information about other indicators used by the fraudster by visiting IOCRadar. As SOCRadar, we proactively follow all kinds of cases that may pose a threat and add them to our platform for detection to support your cybersecurity posture.
Apart from IP addresses, we detected that the fraudster used the email address “[email protected]” to communicate. Examples of research that can be done in light of this information using the Threat Hunting page on the SOCRadar Platform are given in the images below.
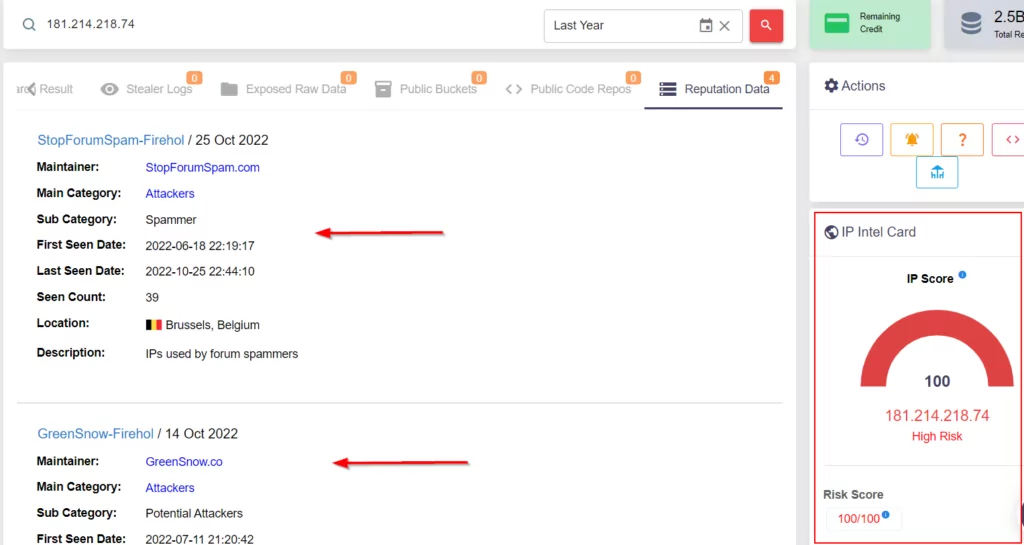
As a result of our research on different sources for the IP addresses of the fraudster, we saw that one of the IP addresses was a VPN address. The findings obtained on IP addresses are given in the images below.
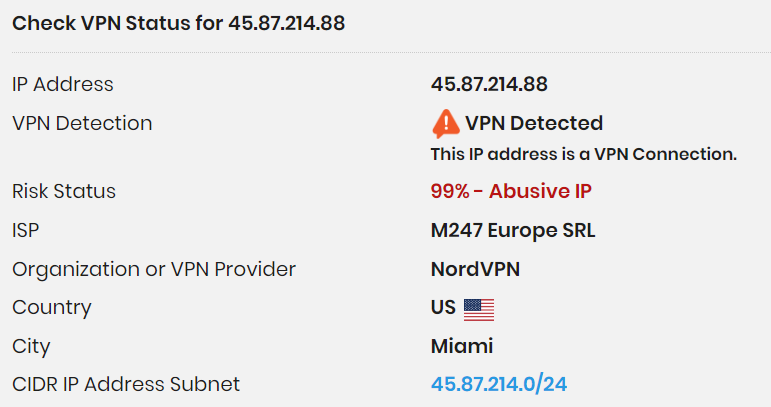
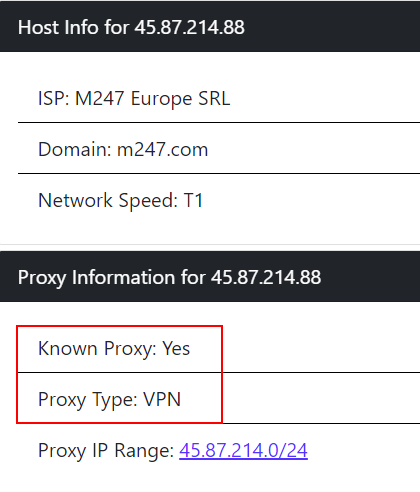
In the later stages of the investigation, we noticed that the IP address “45[.]87[.]214[.]88” visited the connection via a mobile device. The IP address “181[.]214[.]218[.]74” visited the connection via a Windows device. It is estimated that the IP address used on the mobile device belongs to the NordVPN VPN company, while the connection made from the Windows device is the fraudster’s own IP address.
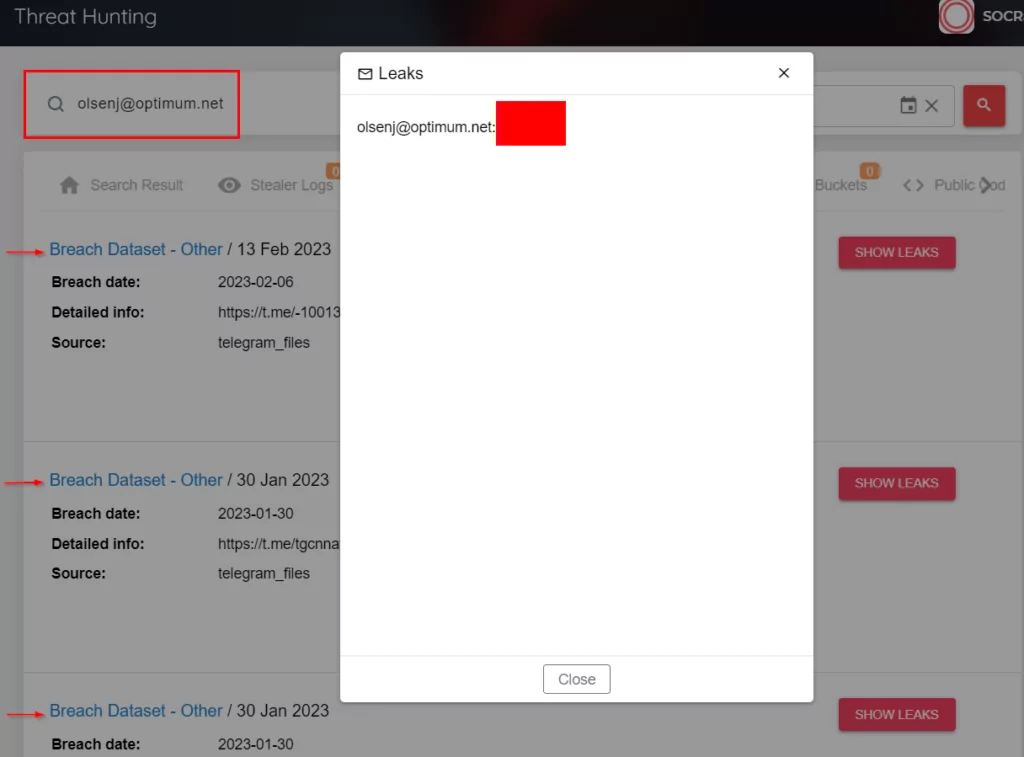
As a result of the queries made on the SOCRadar Threat Hunting page, it is seen in the “Breach Dataset” results that the email address used under the name “OlsenJ” was shared in past leaks. More detailed results can be obtained on behalf of the threat actor by doing more research on the Platform with IP and email addresses. You can also benefit from the Threat Hunting step on the SOCRadar platform to analyze similar fraud attempts.
The screenshot of the Telegram channel where threat actors shared the relevant leak is available in the image above. The fraudster carried out this attack using the stolen email address shared on the Telegram data leak channels.
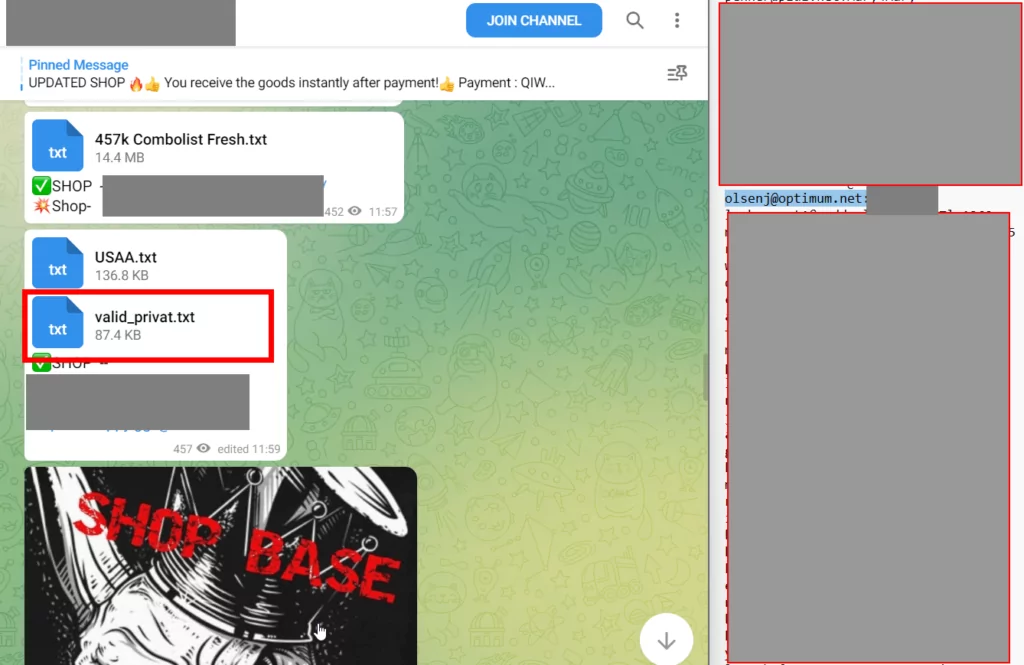
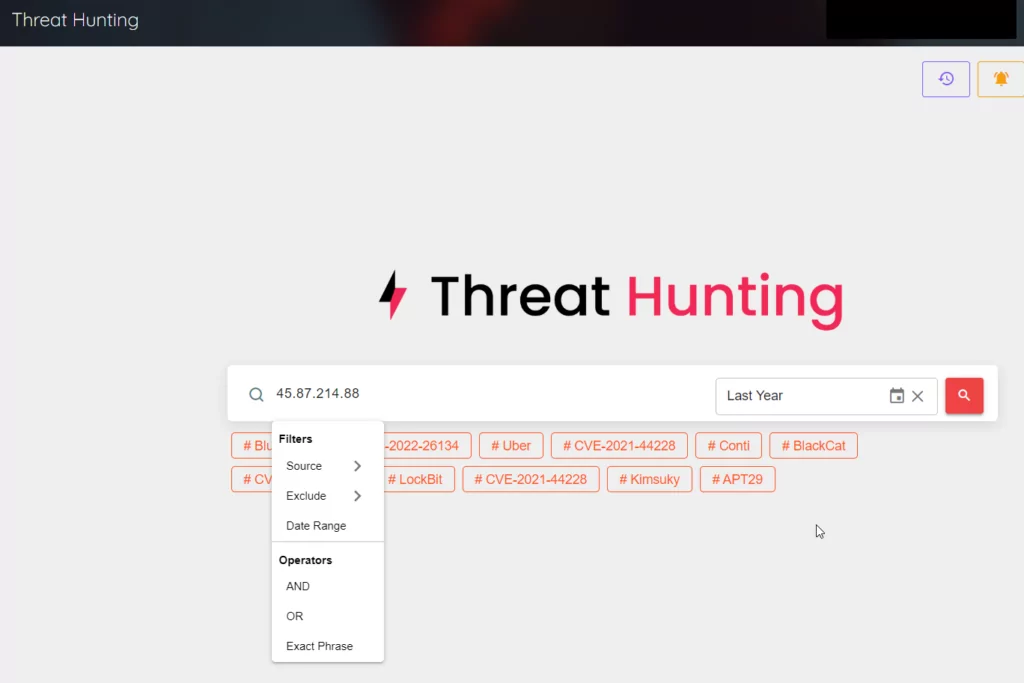
SOCRadar Threat Hunting page offers a wide range of filters to enable more detailed and faster research on these types of fraudsters and threat actors.
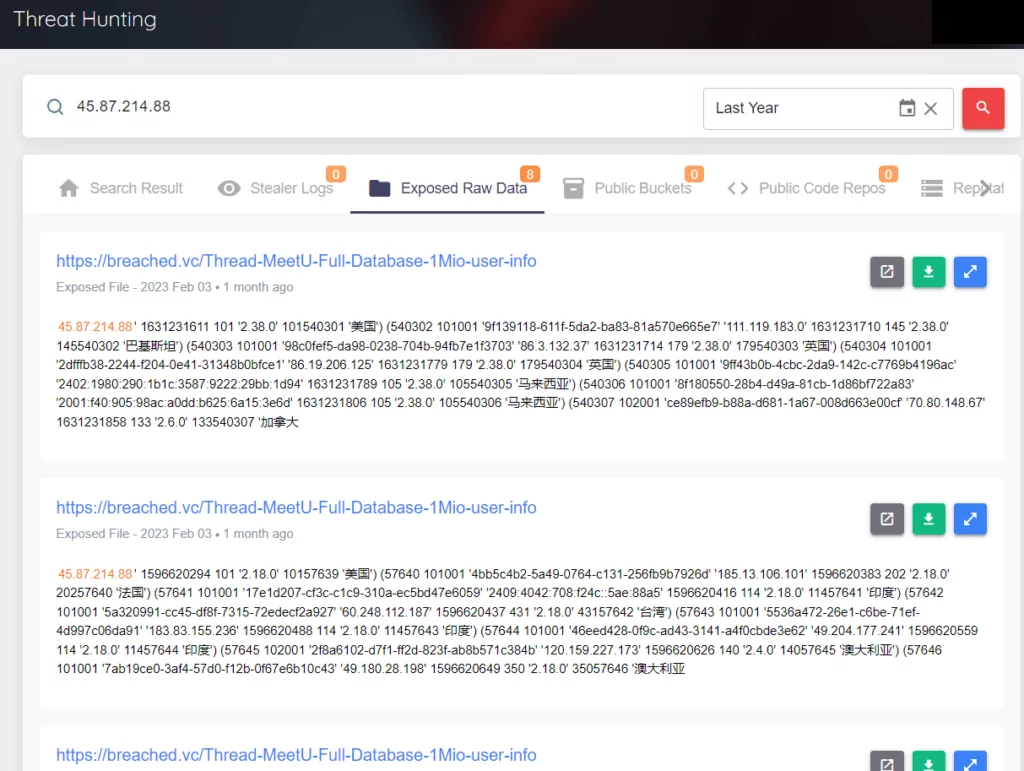
In the research conducted on the SOCRadar Threat Hunting page, it is possible to obtain many matches for the IP address “45[.]87[.]214[.]88.” Similar results are also valid for the IP address “181[.]214[.]218[.]74,” and the details are given in the screenshot below.
Conclusion
This report is based on the detection and analysis of a cyber fraud attack in which attackers targeted organizations and individuals with impersonation methods and attempted to harm them by soliciting requests such as gift cards. In this attack method, attackers usually aim to steal the financial resources of businesses and organizations. This attack method, which threat actors usually carry out to convince the victim to make a payment by sending a fake invoice to the victim, can sometimes include incidents such as gift card requests.
This report includes the detection and analysis of a cyber fraud attack on SOCRadar after it attracted the attention of cyber fraudsters following the investment news. To protect against this attack method called cyber fraud, organizations should build cybersecurity awareness, and employees must verify incoming email addresses and contents. Additional verifications should be made to ensure that requests, especially from managers, are actually sent by managers. Various security measures should be taken with email filters and security solutions to provide security controls for the accounts of company employees. In this way, suspicious emails can be blocked. In addition, necessary checks should be made to regularly identify and fix security vulnerabilities, and system updates should be continuously monitored.
Thanks to SOCRadar Extended Threat Intelligence, you can benefit from the early warning system about the threat actors detected in such attacks and their methods. You can also get detailed information about the attack, the threat actor, and its motivation by using our platform in such cyberattack attempts.




































