
Microsoft Fixes Exploited Zero-Days in March Patch Tuesday (CVE-2023-23397 & CVE-2023-24880)
[Update] December 5, 2023: Microsoft has officially attributed the exploitation of CVE-2023-23397 to APT28.*
Microsoft has released its Patch Tuesday update for March 2023, which includes fixes for 80 security vulnerabilities. Eight vulnerabilities have critical severity ratings, and two zero-day vulnerabilities are under active exploitation.
The types of vulnerabilities fixed in March 2023 Patch Tuesday are listed below:
- 21 Elevation of Privilege Vulnerabilities
- 2 Security Feature Bypass Vulnerabilities
- 27 Remote Code Execution Vulnerabilities
- 15 Information Disclosure Vulnerabilities
- 4 Denial of Service Vulnerabilities
- 10 Spoofing Vulnerabilities
- 1 Edge – Chromium Vulnerability
Microsoft Patches Exploited Zero-Days
The first zero-day vulnerability tracked as CVE-2023-23397 (CVSS score: 9.8), also included in critical vulnerabilities, exists in Microsoft Outlook and allows privilege escalation.
Between April and December 2022, the state-sponsored Russian hacking group APT28 (also known as STRONTIUM, Sednit, Sofacy, and Fancy Bear) actively exploited CVE-2023-23397 to breach the networks of government, military, energy, and transportation organizations.
The group sent malicious Outlook notes and tasks to exploit the SMB protocol, forcing target devices to authenticate to SMB shares under their control to steal NTLM hashes. APT28 used stolen credentials to move laterally within the victims’ networks and change Outlook mailbox folder permissions for email exfiltration.
Mitigations for CVE-2023-23397 include adding users to the Protected Users group in Active Directory and blocking outbound SMB (TCP port 445). A dedicated PowerShell script has also been released to help admins check for users targeted using this Outlook vulnerability.
The second zero-day vulnerability, CVE-2023-24880 (CVSS score: 5.4), is a security feature bypass found in Windows SmartScreen, which allows to create executables that can bypass Windows Mark of the Web (MotW) security warnings. Although it has a CVSS score of 5.4, it is under active exploitation.
Attackers exploited the vulnerability using malicious MSI files with a crafted Authenticode signature. The signature was invalid but successfully bypassed SmartScreen.
The vulnerability was made possible because Microsoft released a narrow patch for CVE-2022-44698 that only fixed a single aspect of the bug rather than the root cause, which allowed the attackers to quickly identify a different variant of the original bug.
Critical Vulnerabilities
The remaining critical vulnerabilities covered in the patch are detailed below:
- CVE-2023-23415 (CVSS score: 9.8): An attacker could obtain remote code execution on the target system by sending a protocol error containing a fragmented IP packet within an ICMP packet header.
- CVE-2023-23404 (CVSS score: 8.1): This Windows Point-to-Point Tunneling Protocol vulnerability enables remote code execution. An unauthenticated attacker can exploit this by sending a specially crafted connection request to a RAS server.
- CVE-2023-23416 (CVSS score: 8.4): To execute code remotely, an attacker can upload a malicious certificate to a certificate processing service or persuade an authenticated user to do so. The attack is performed on the local machine.
- CVE-2023-23392 (CVSS score: 9.8): An unauthenticated attacker can exploit a target server that uses the HTTP Protocol Stack (http.sys) to process packets by sending a specially crafted packet, resulting in remote code execution.
- CVE-2023-21708 (CVSS score: 9.8): This vulnerability affects the Remote Procedure Call Runtime. An unauthenticated attacker can achieve server-side remote code execution by sending a specially crafted RPC call to an RPC host.
- CVE-2023-1017 (CVSS score: 7.8): In TPM2.0’s Module Library, an out-of-bounds write vulnerability exists that can result in denial of service (DoS) or remote code execution.
- CVE-2023-1018 (CVSS score: 7.7): TPM2.0’s Module Library also contains an out-of-bounds read vulnerability that could allow attackers to read or access sensitive data stored in the TPM.
Proof-of-Concept Available for the Zero-Day CVE-2023-23397
Security researchers have disclosed technical details about one of the zero-day vulnerabilities, CVE-2023-23397, in Microsoft Outlook for Windows that allows hackers to remotely steal hashed passwords by sending a malicious email.
Microsoft has released a patch for this privilege escalation flaw, which affects all versions of Outlook on Windows. However, the vulnerability has already been exploited as a zero-day flaw in NTLM-relay attacks since mid-April 2022.
The vulnerability can be triggered without user interaction by simply opening Outlook or reminders. The stolen hashed passwords can be used to perform NTLM relay attacks to gain access to corporate networks.
In addition, MDSec has shared a video demonstrating how the vulnerability in Microsoft Outlook can be exploited, serving as a proof-of-concept (PoC) for how easy it is for threat actors to leverage the bug.
Microsoft Warns of New Attack Exploits CVE-2023-23397
Microsoft has released guidance that provides details of the attacks that have taken place using CVE-2023-23397.
It has been suggested that a nation-state actor may be responsible for the exploitation. According to researchers, a cyberespionage campaign exploiting the vulnerability has been observed, carried out by a threat actor known as UNC4697, which is believed to be associated with the APT28 group.
*Microsoft has officially attributed the exploitation of CVE-2023-23397 to APT28, a Russian-based nation-state threat actor also known as Forest Blizzard (STRONTIUM, FANCYBEAR). The company has collaborated with the Polish Cyber Command (DKWOC) to counteract the threat, identifying and mitigating the actor’s techniques. For more details on this collaborative effort, check out the article.
Attackers have been able to gain initial access through a Net-NTLMv2 Relay attack, maintain persistence by modifying mailbox folder permissions, and move laterally by sending additional malicious messages.
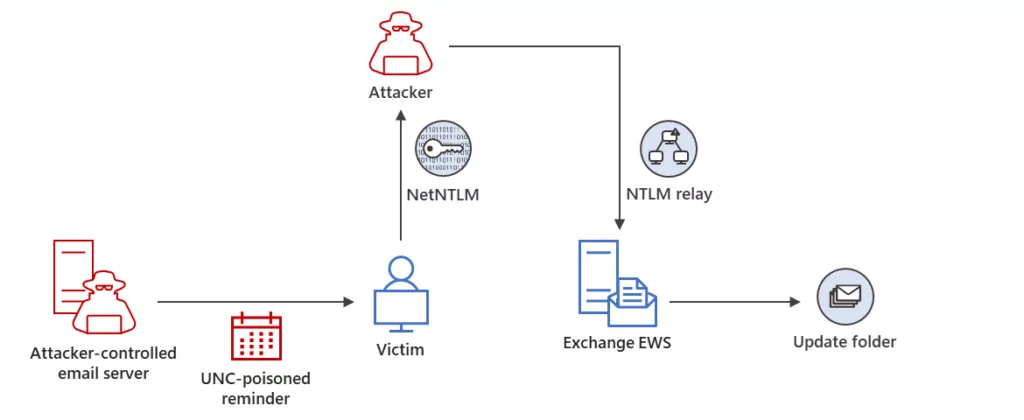
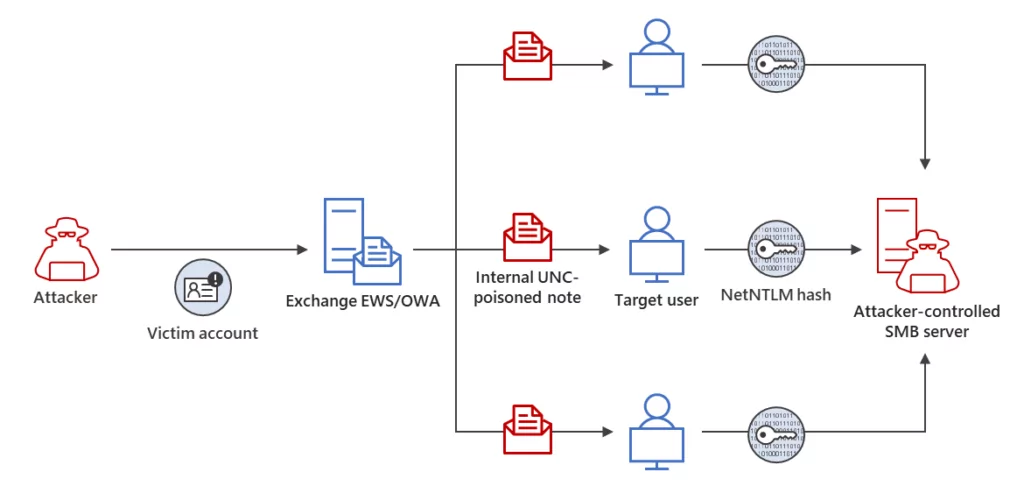
Threat actors have also been observed extending their access within the compromised environment by targeting other members of the same organization using a compromised email account.
Cybersecurity researchers consider the exploitation of CVE-2023-23397 novel and stealthy, as it does not require user interaction. Users in targeted organizations may have received harmful messages with the PidLidReminderFileParameter value set.
Even when users reported suspicious reminders on tasks, the initial security review of the messages, tasks, or calendar items did not reveal any evidence of malicious activity.
Microsoft suggests using threat hunting methods to identify any unusual user behavior that could indicate a compromised credential. Additionally, Microsoft has given indicators of attack for this campaign:
- 101.255.119[.]42
- 213.32.252[.]221
- 168.205.200[.]55
- 185.132.17[.]160
- 69.162.253[.]21
- 113.160.234[.]229
- 181.209.99[.]204
- 82.196.113[.]102
- 85.195.206[.]7
- 61.14.68[.]33
Prioritize Patches with SOCRadar
Security researchers recommended applying the patches according to Microsoft’s security update guide for March 2023 to safeguard your systems and products against mentioned vulnerabilities.
SOCRadar can protect your assets by identifying and monitoring potential security concerns like vulnerabilities. The platform offers actionable intelligence that can enhance security measures and assist with patch prioritization.
Get a demo now and experience SOCRadar’s Vulnerability Intelligence for more information and updates on the vulnerabilities.



































